Attacking Storage Services : the Lynchpin of Cloud Services
A presentation at HITB CyberWeek 2020 Red Team Village by Anant Shrivastava
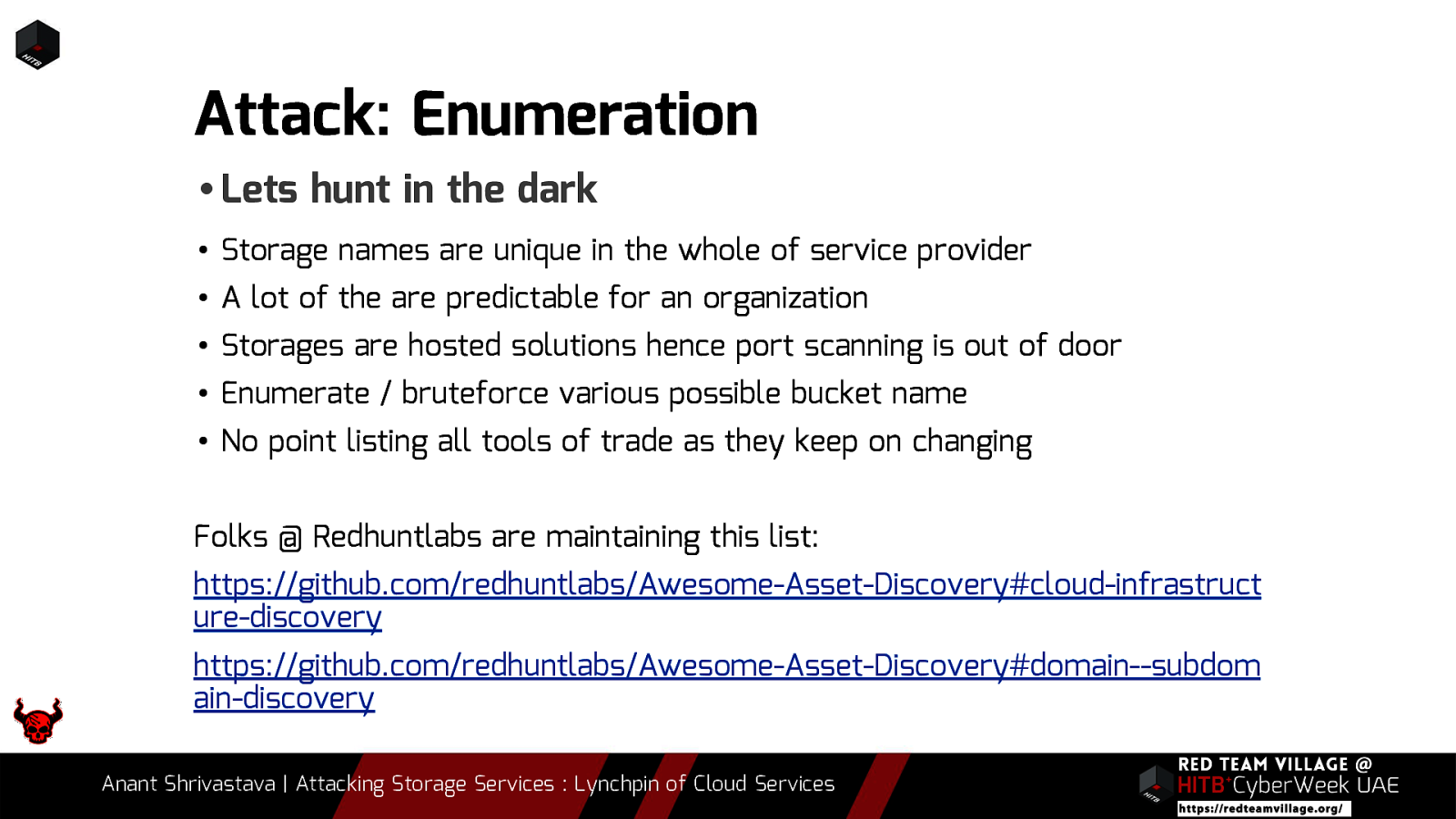
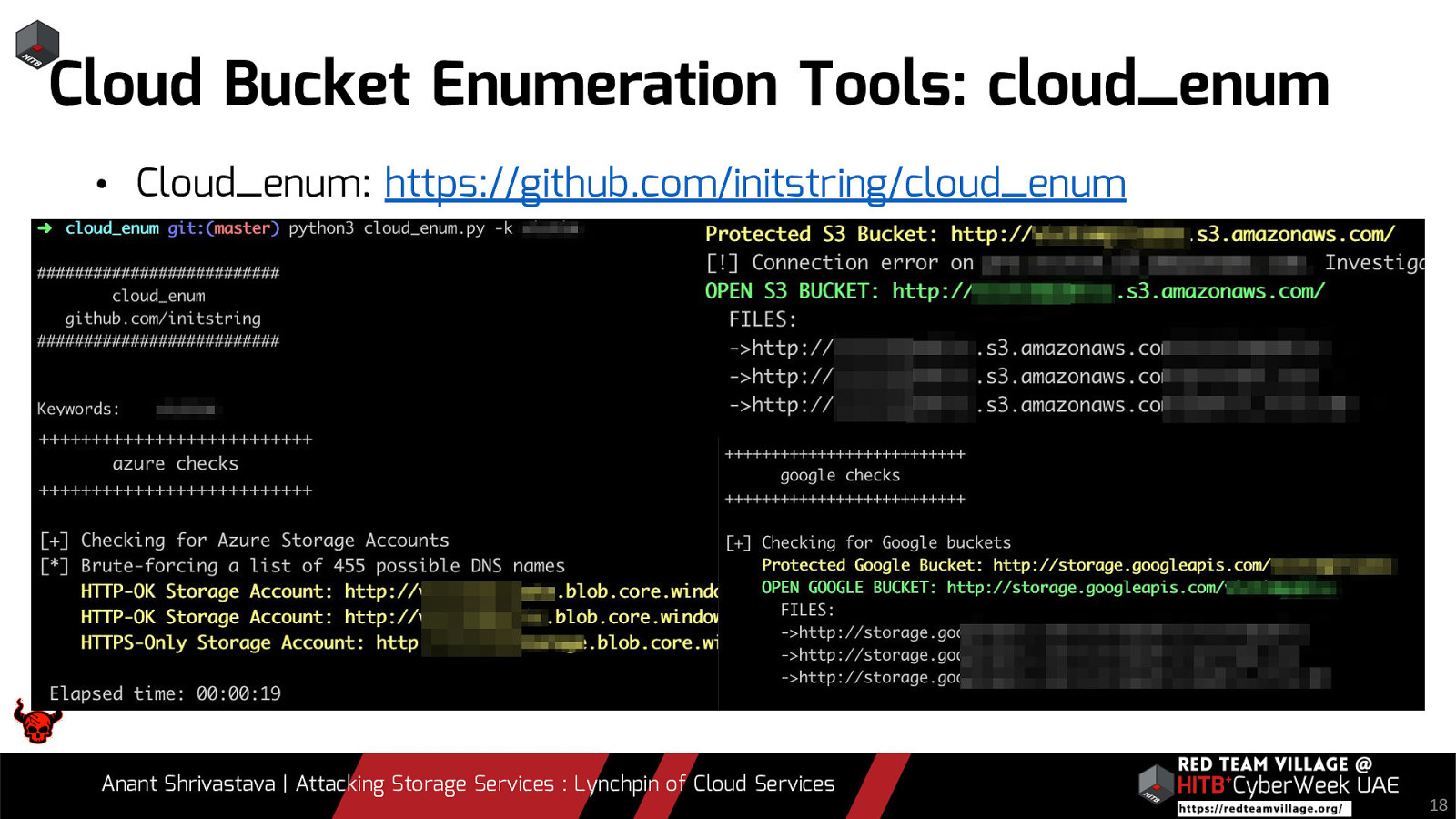
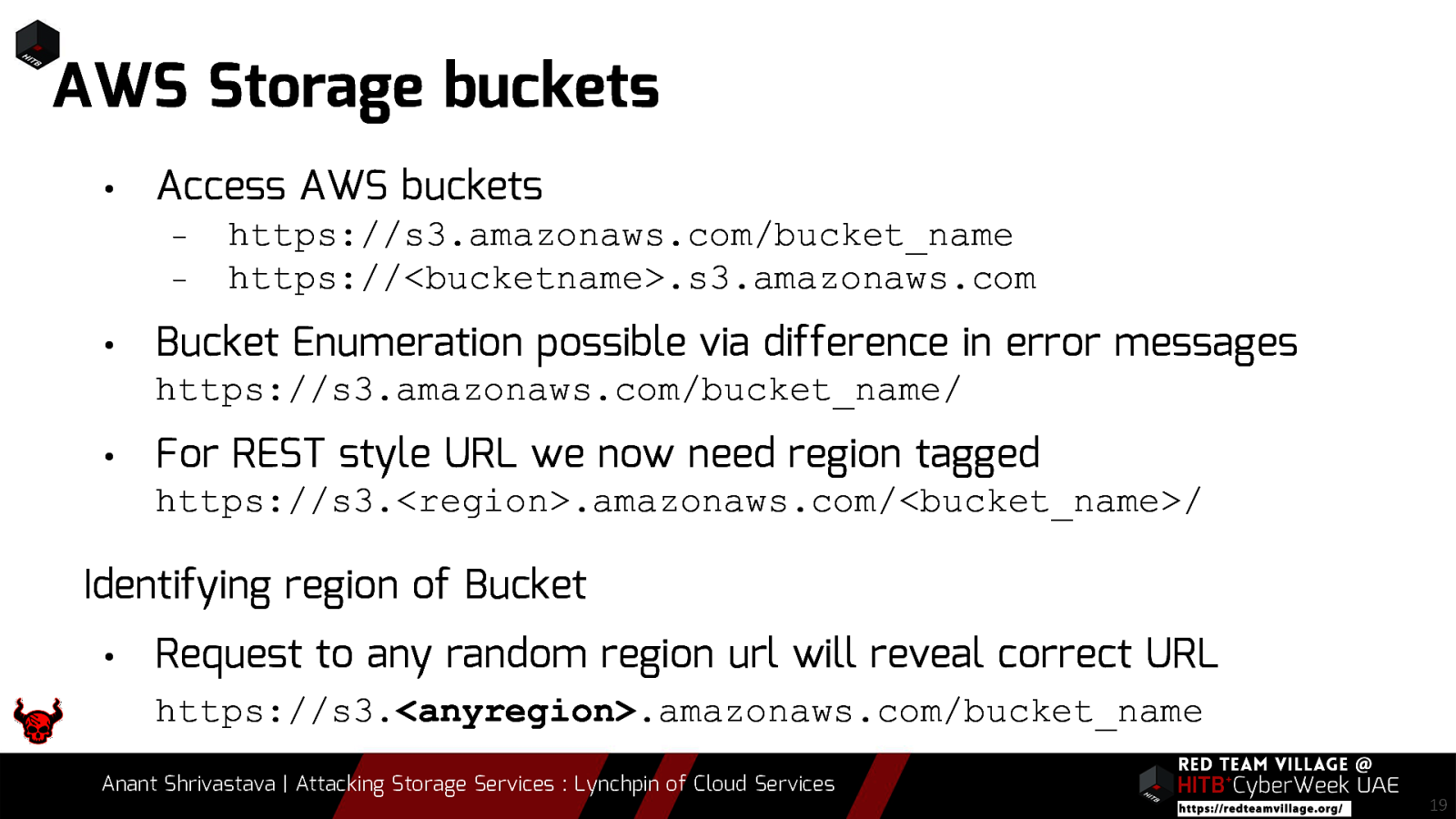
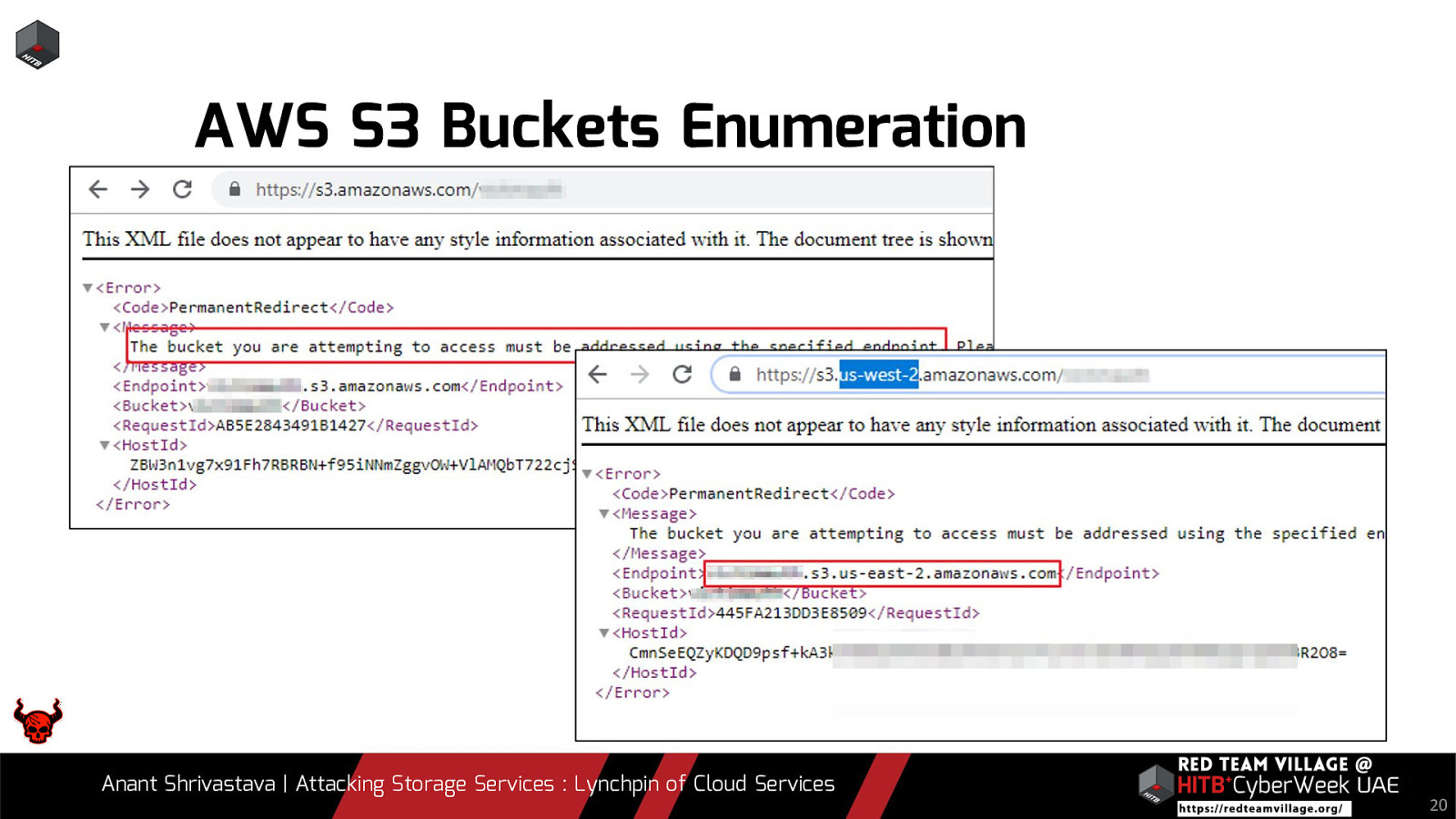
We all agree that most organizations have some or the other service leveraged over cloud environments. To add to it, there are assets that are not linked directly to the public and not easily spotted. When it comes to Red Team Engagements it boils down to a simple statement. “Are you able to find something that wasn’t supposed to be visible in the first place ?”. Storage services by the cloud providers are usually not visible directly to the end user and are often overlooked by pentesters and Red Teamers. In this talk we will be leveraging the possibility of Storage Services of different cloud vendors and how if not properly configured could lead to a lot of Damage to the organization.
Storage services are almost always the second service started by cloud vendors after IaaS, it is done in that order for a reason. Cloud Storage irrespective of how simple it looks, is a complex deeply integrated component for cloud services. The primary purpose of storage services is to hold data of all kinds, besides its primary function it also performs multiple other actions. Storage allows building higher abstraction services on top of the it such as:
Static file hosting,FaaS or PaaS code hosting and Log storage
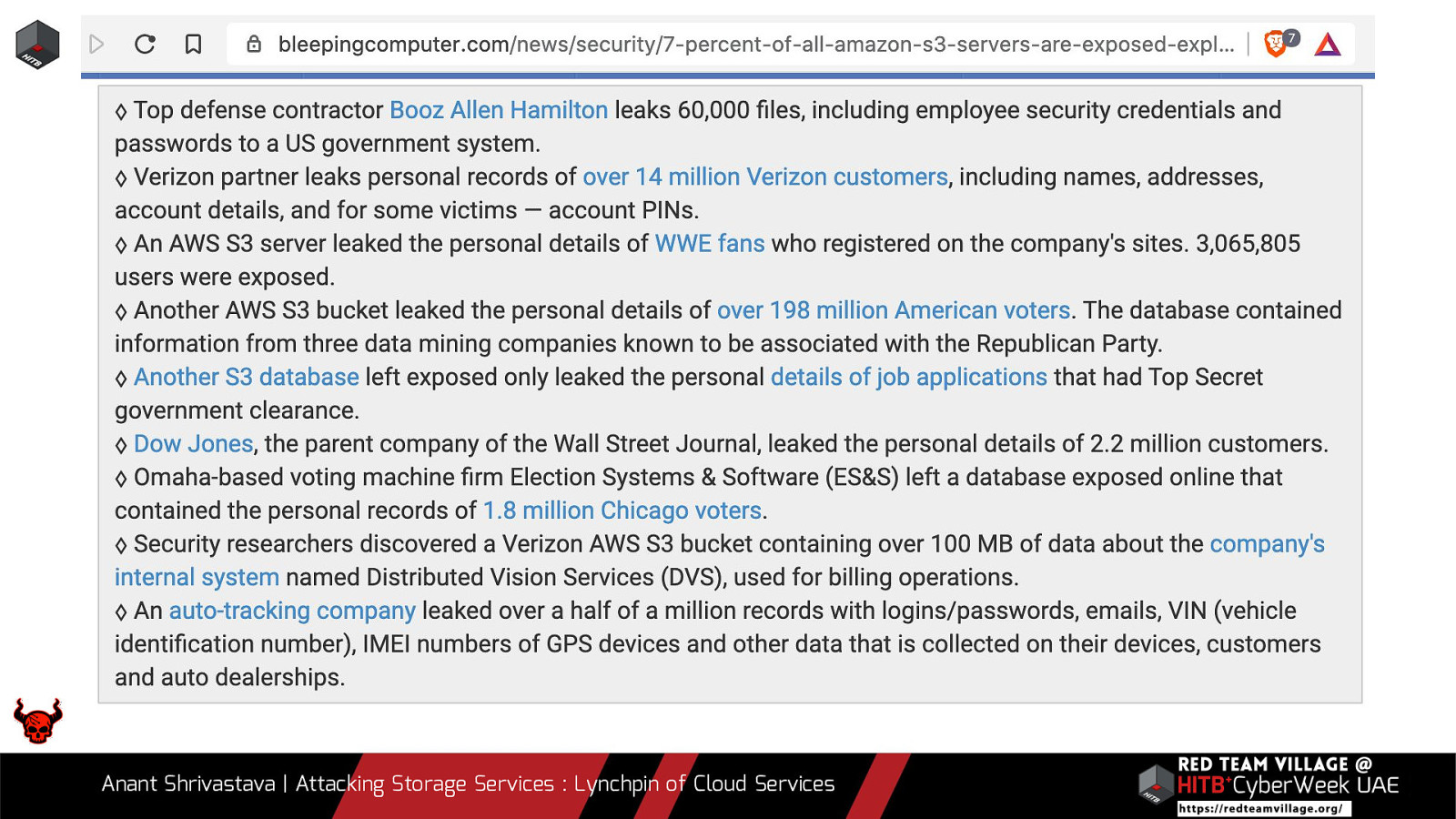
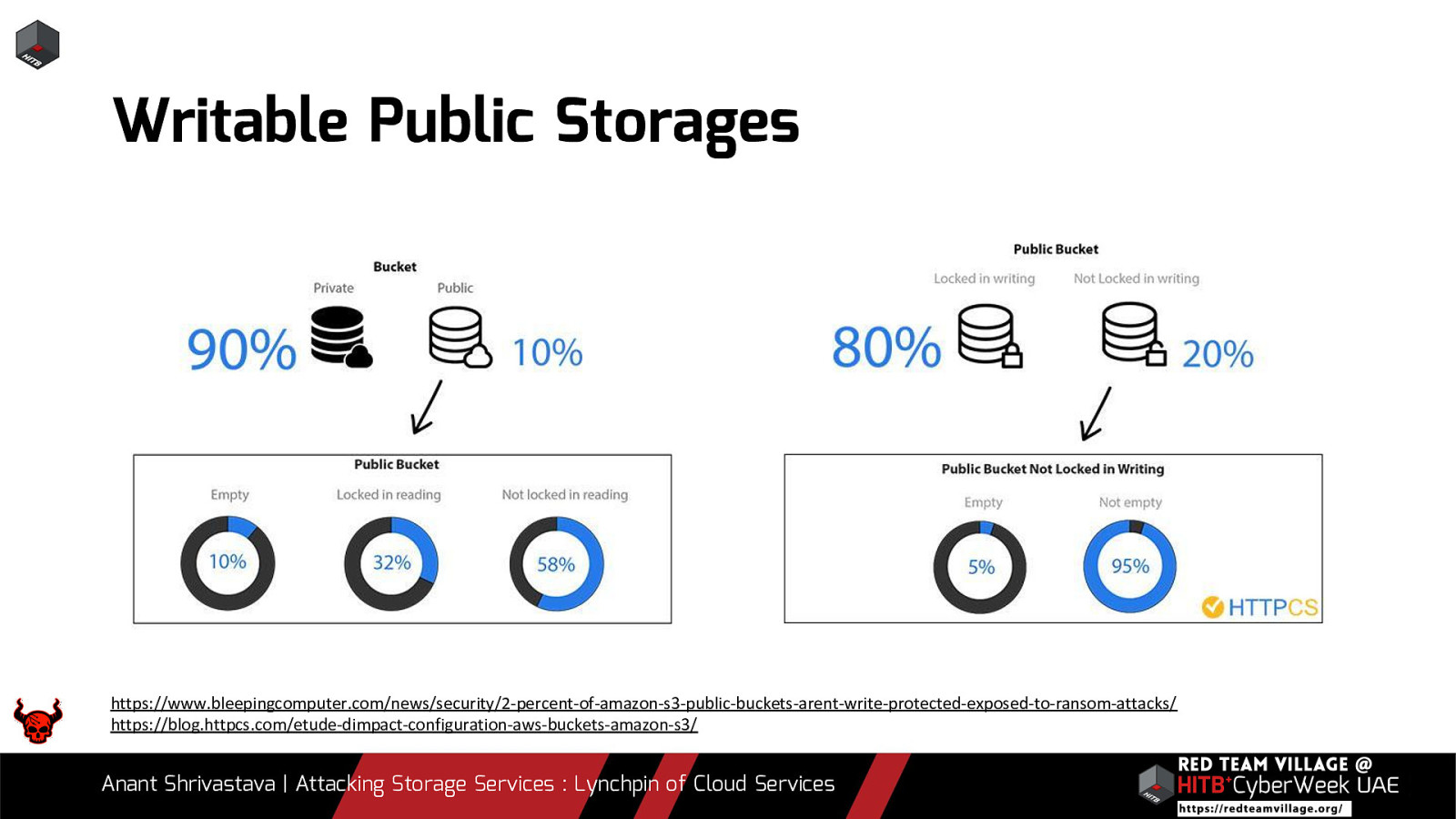
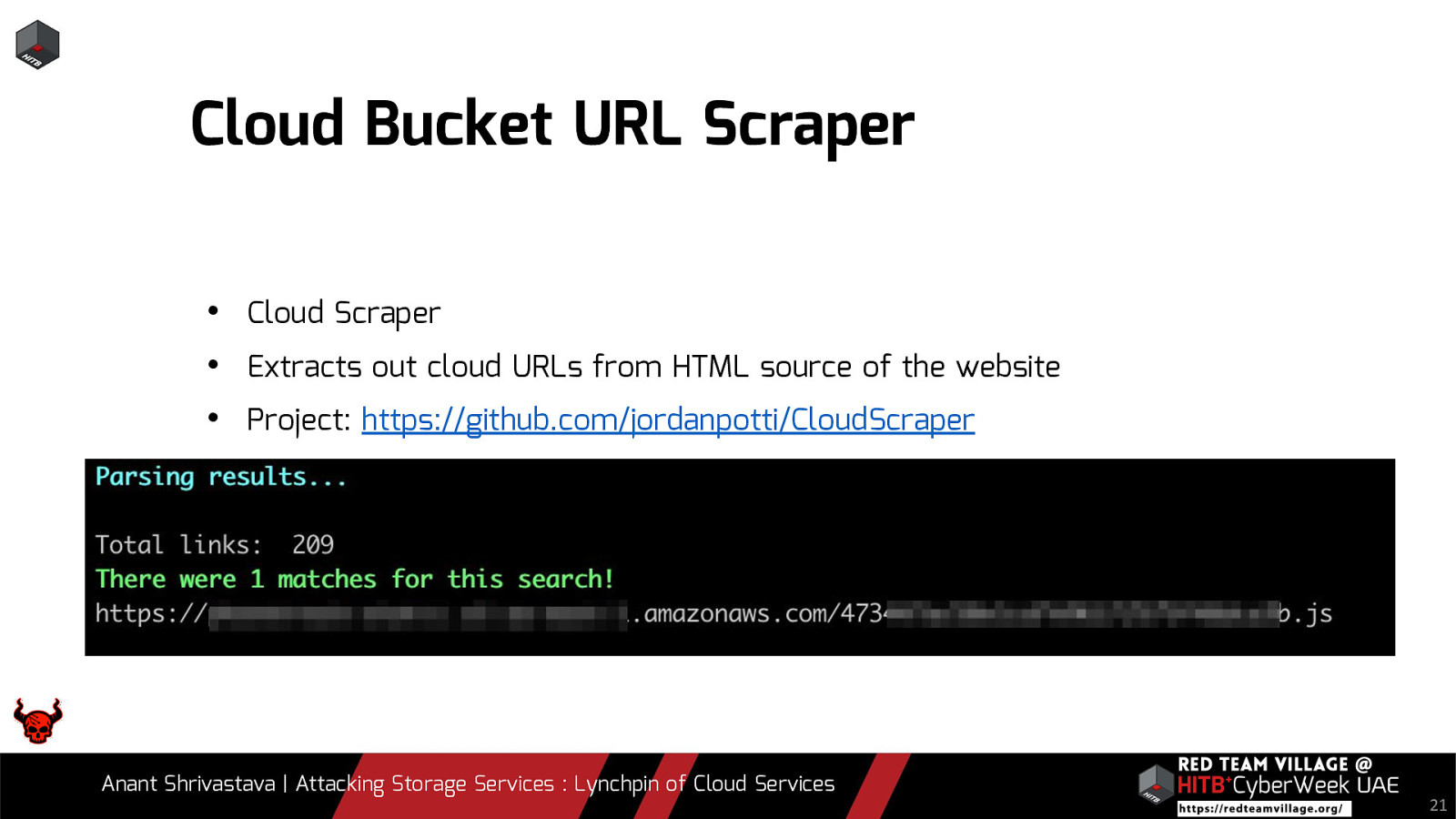
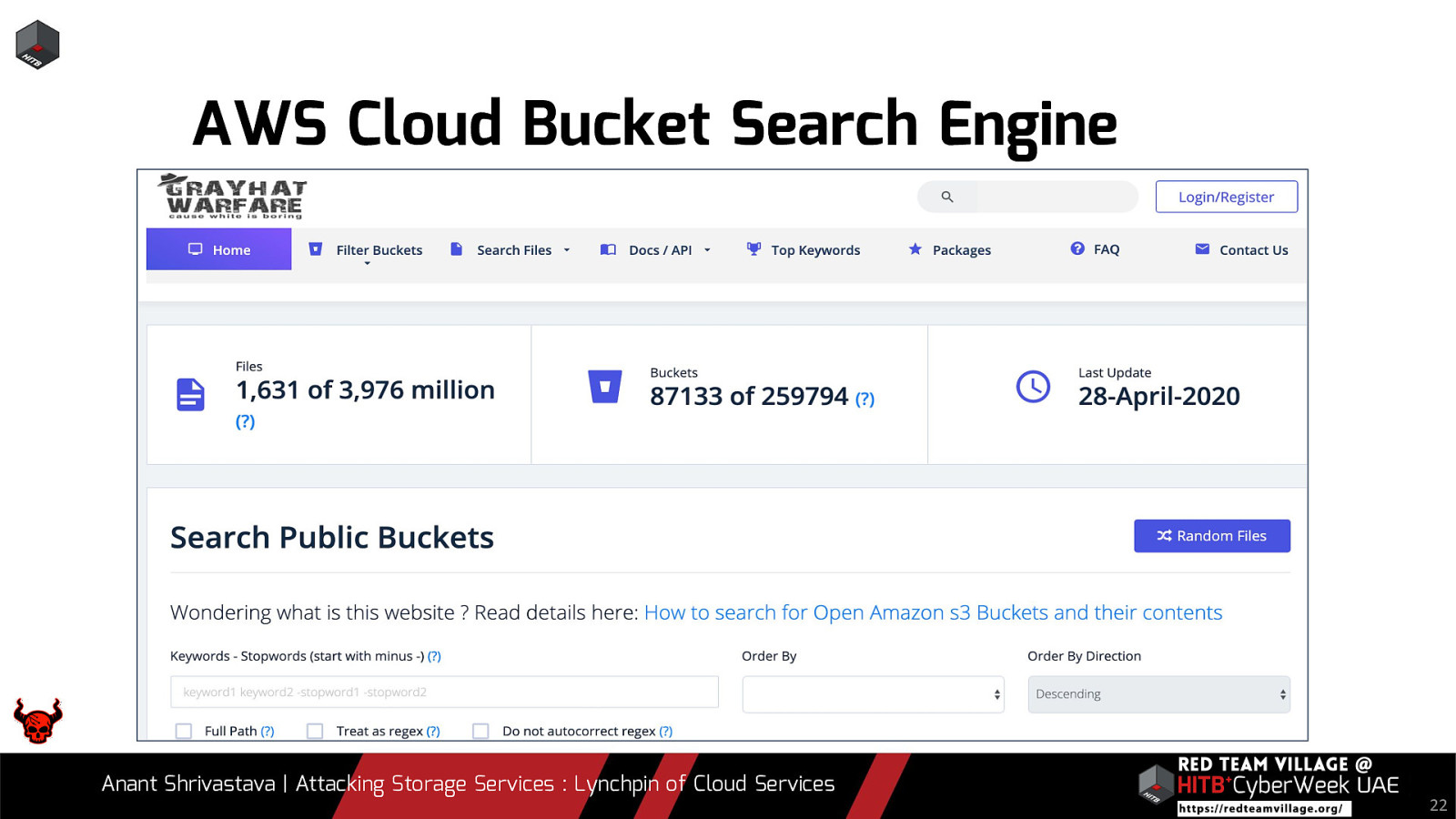
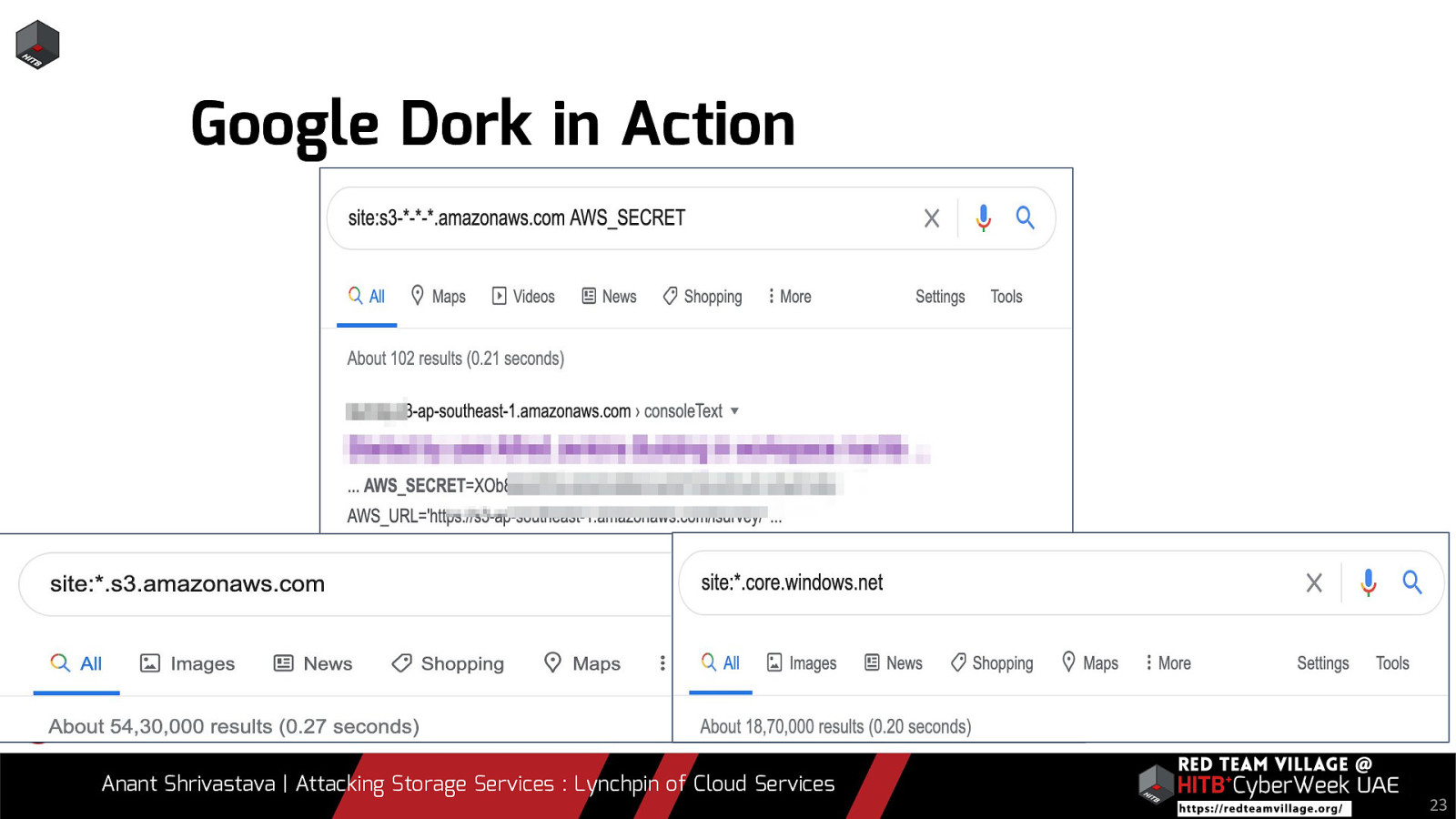
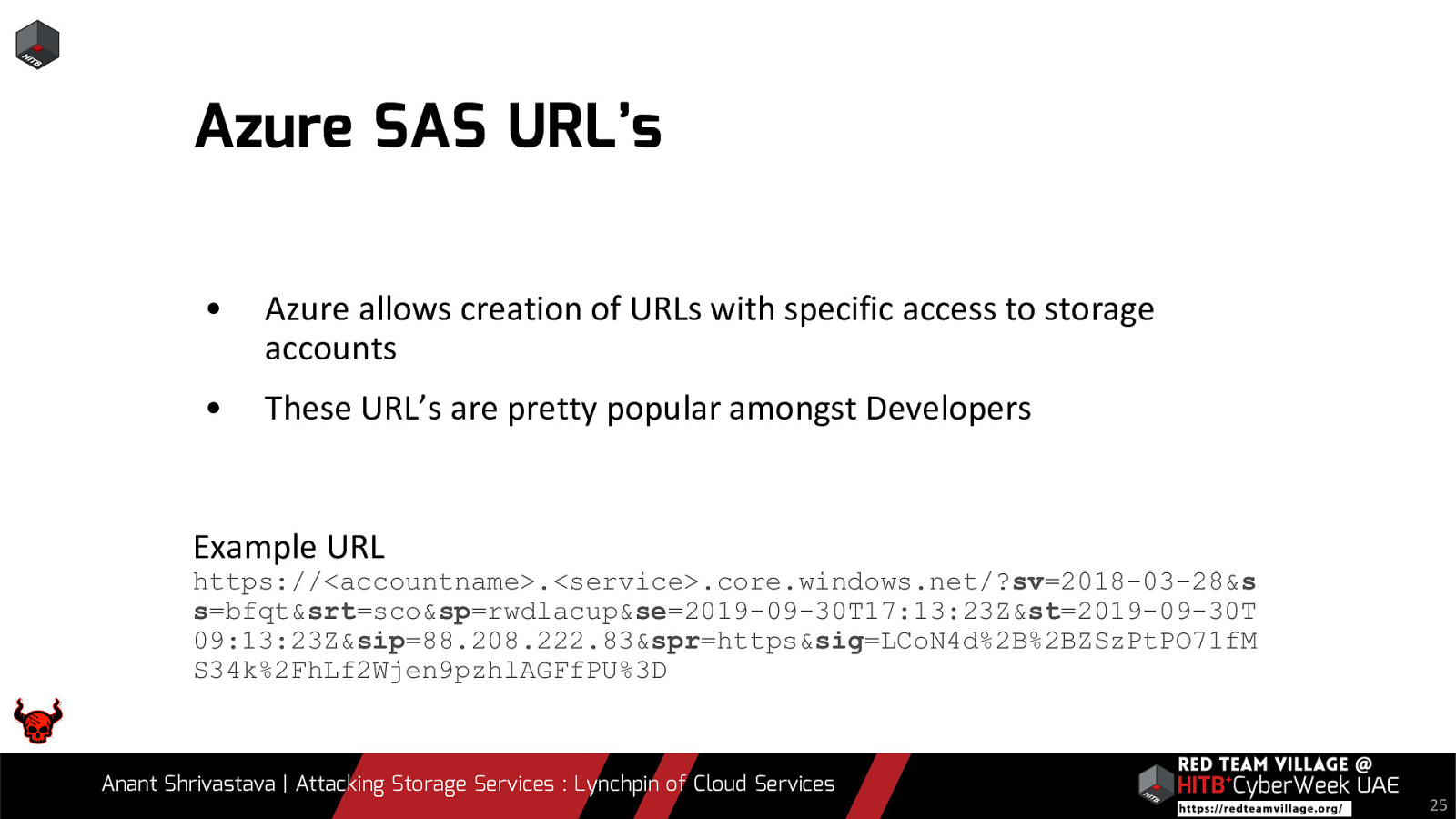
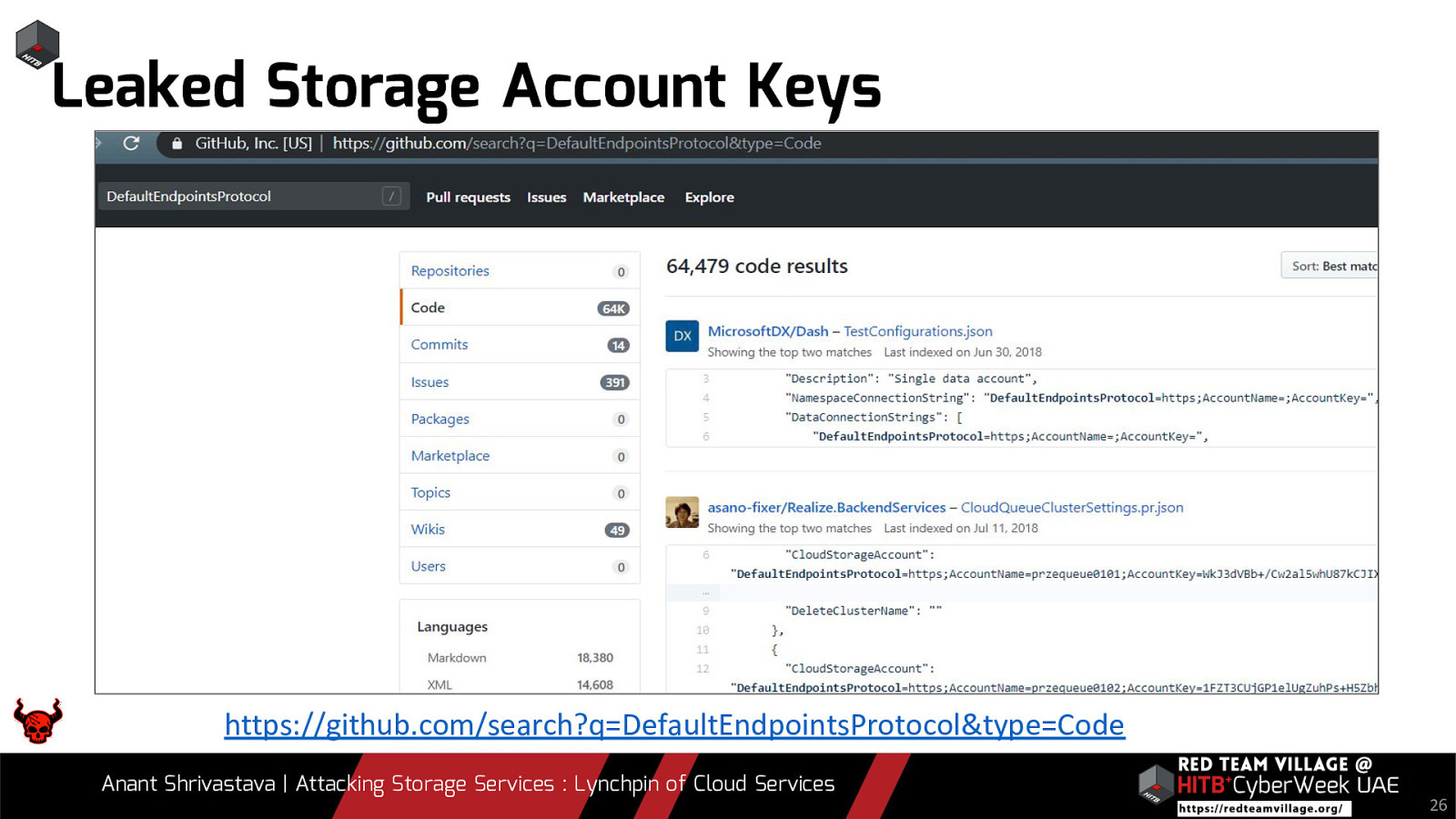
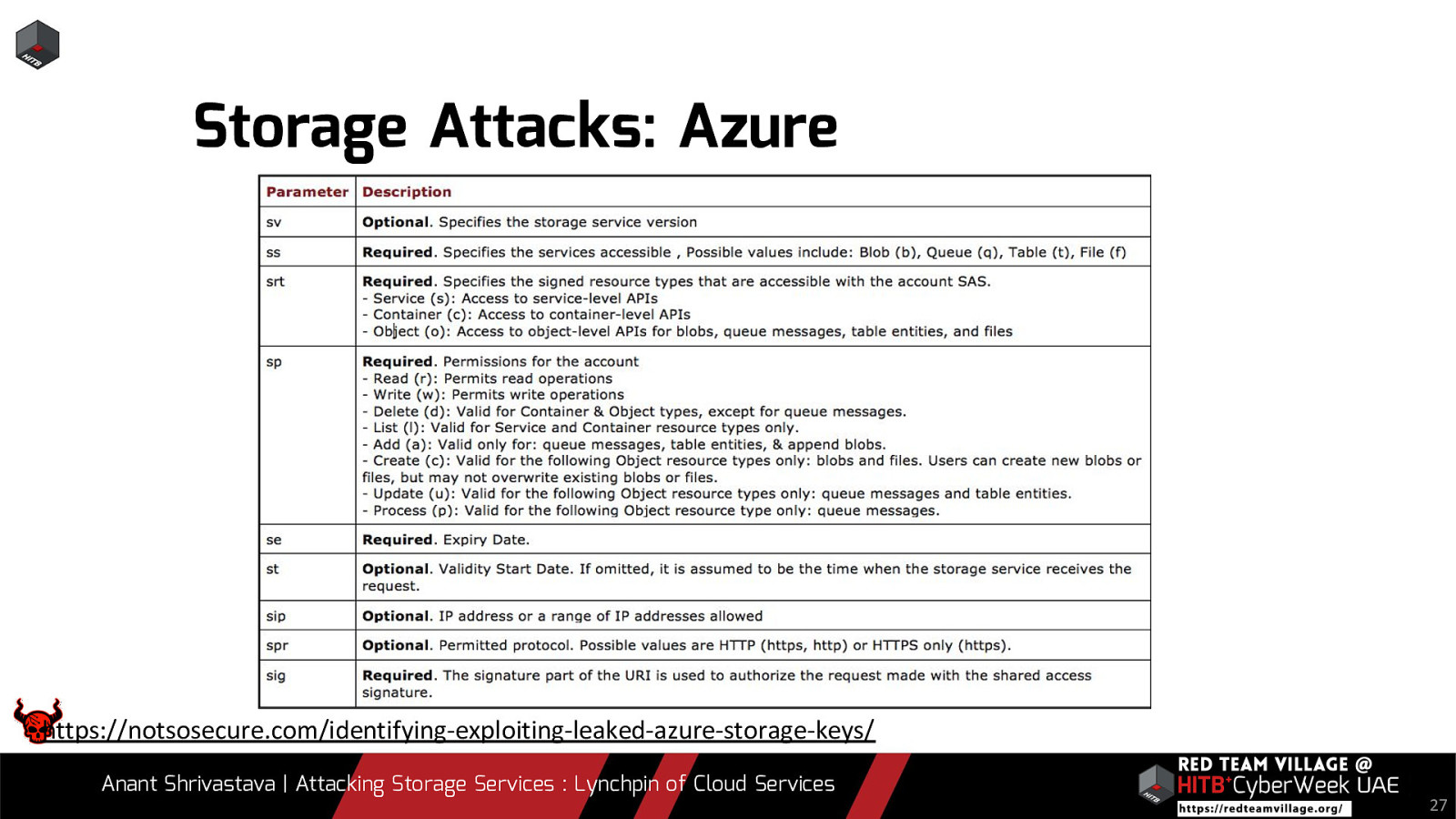
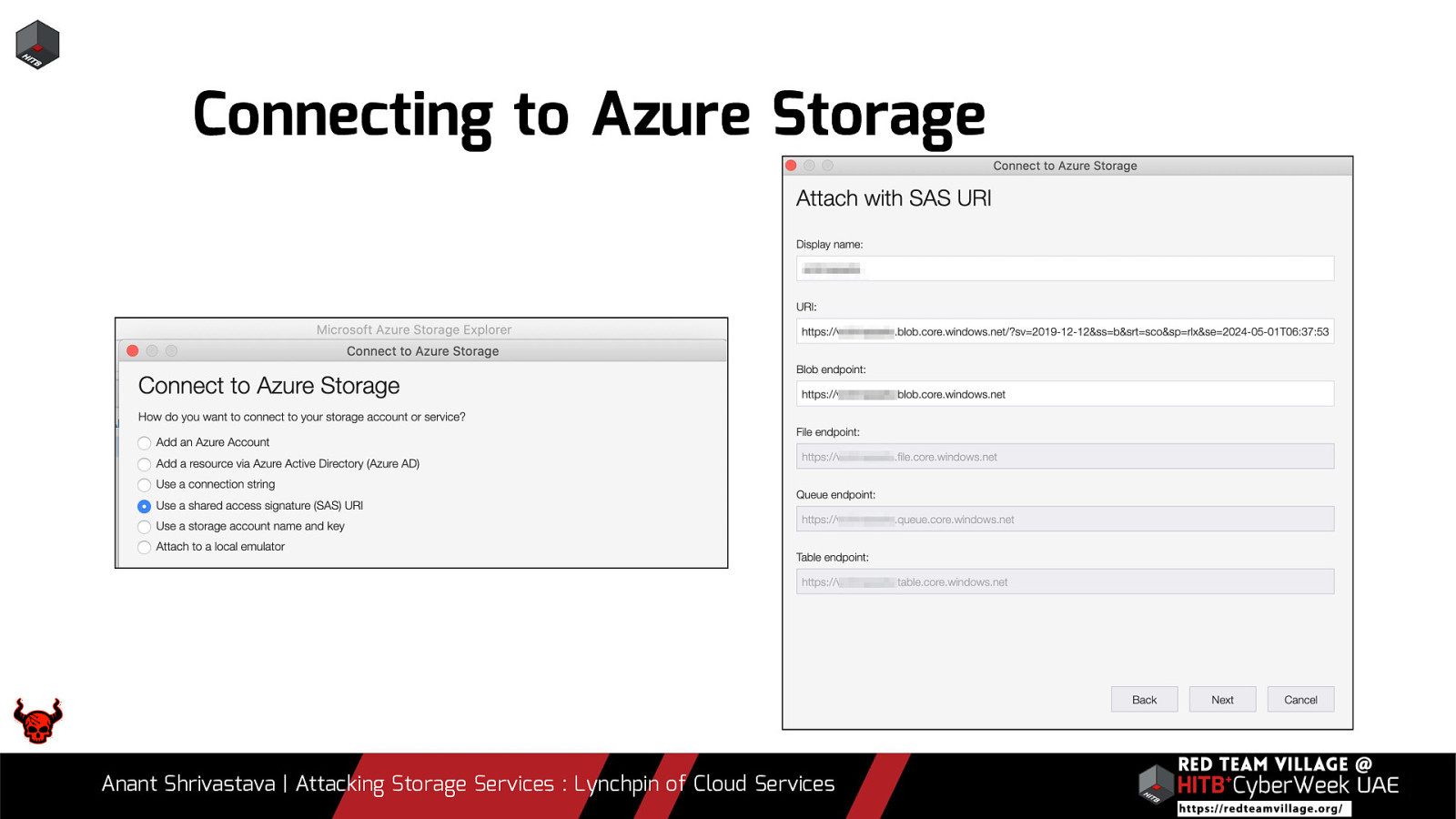
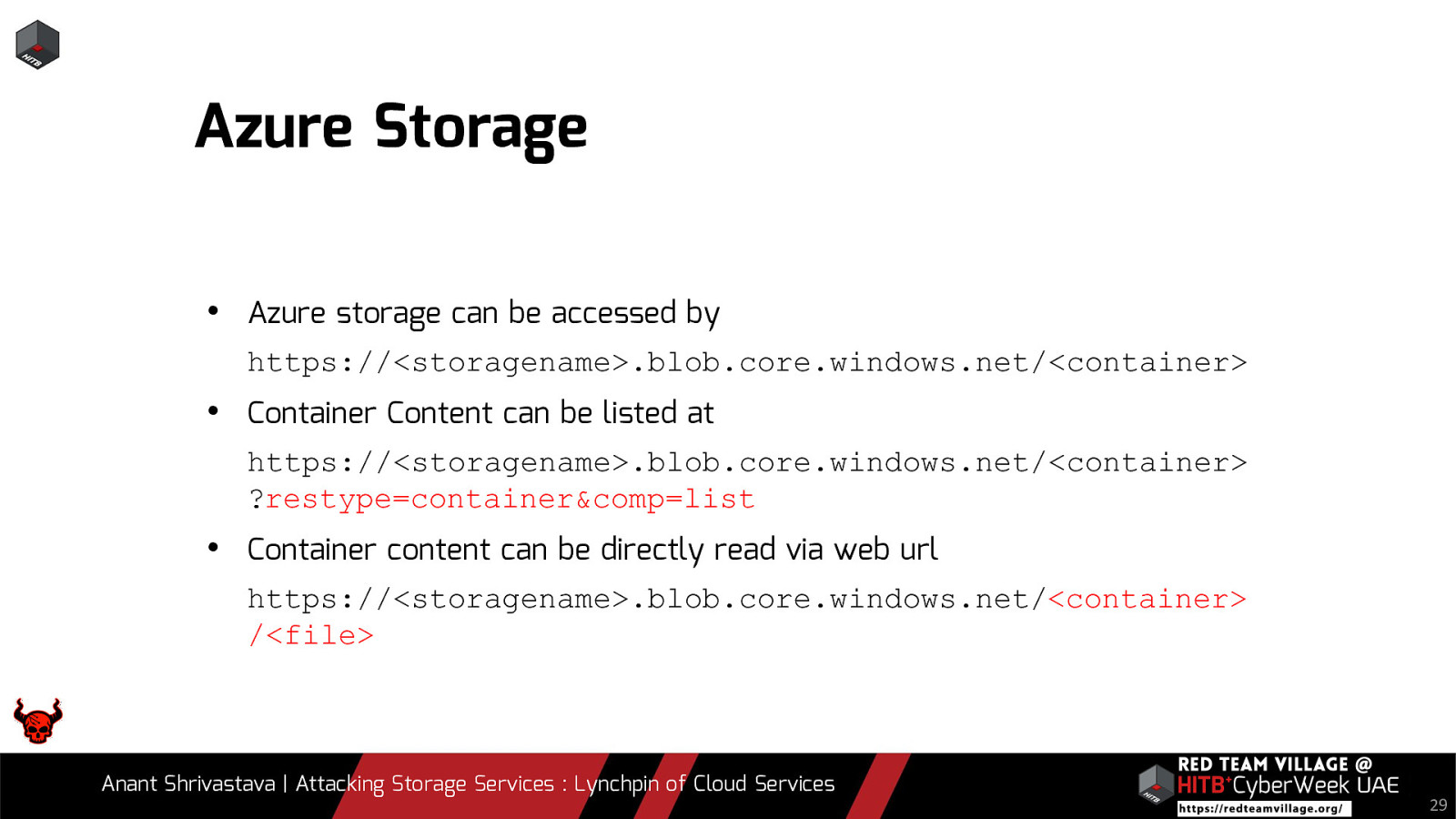
Due to its versatility storage is an area which should be looked at with a fine tooth comb. However the situation is far worse than what we can imagine. From exposing buckets to public, to leaking api keys or ssh keys in public. Things go from bad to worse when buckets also are leaking write access to source code leading to full account takeover scenarios. This talk will cover the following aspects around Cloud Storage Services.
- 1. Basics of Cloud Storage Services and why to target them
- 2. Attack Methodology to be followed
- 3. Various attack scenarios from real and bug bounty world
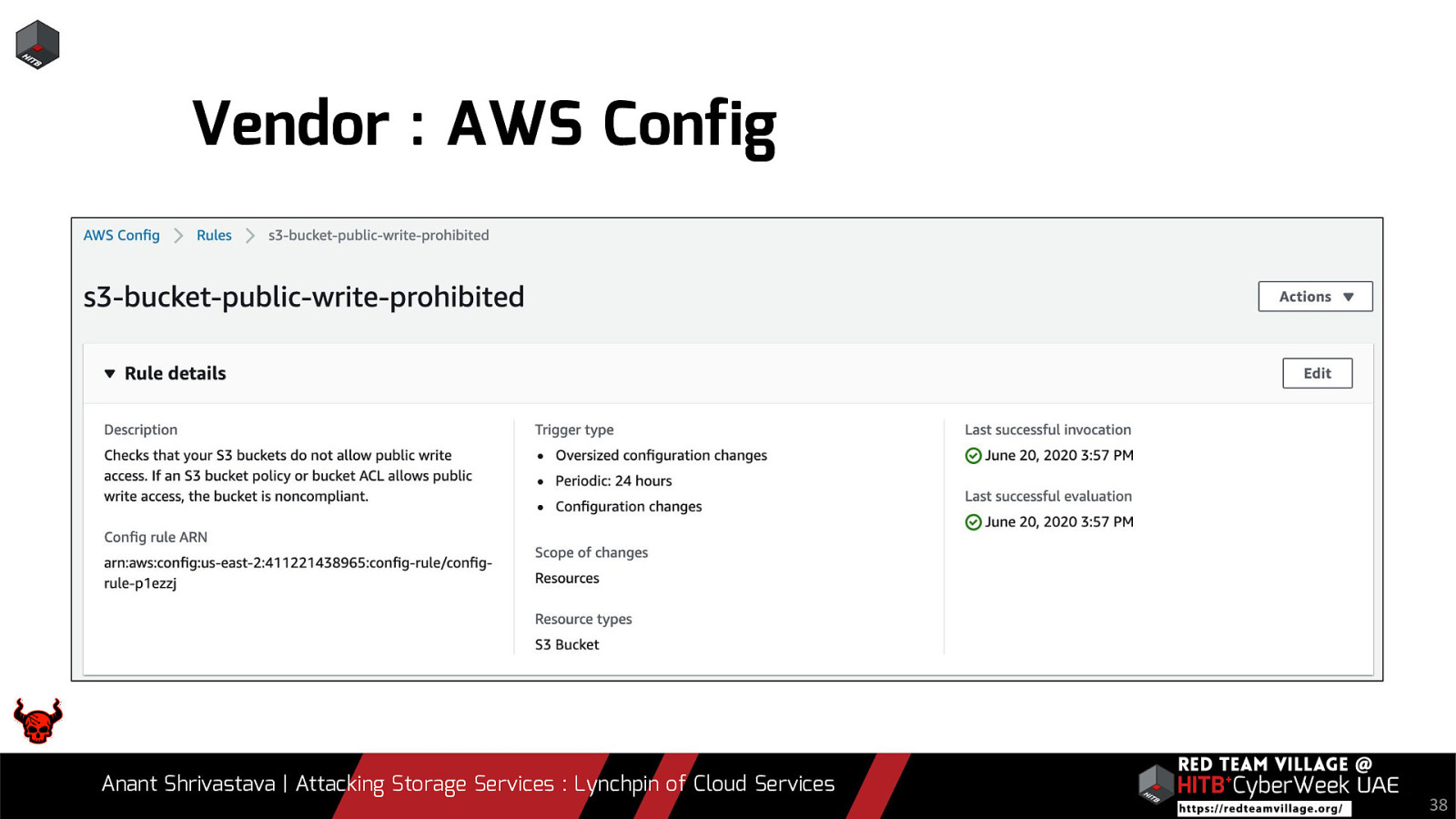
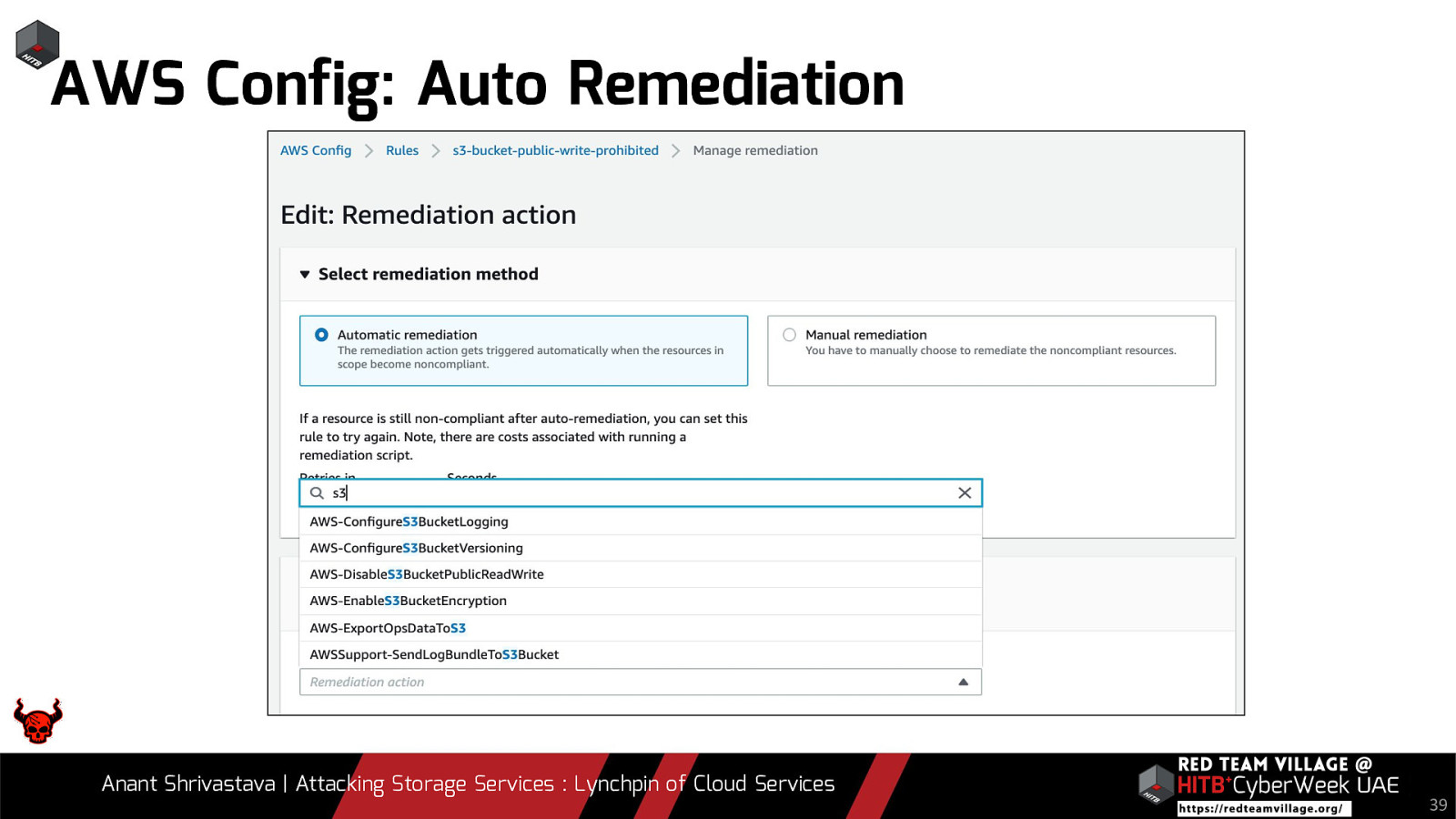
- 4. What are cloud vendors doing to protect this
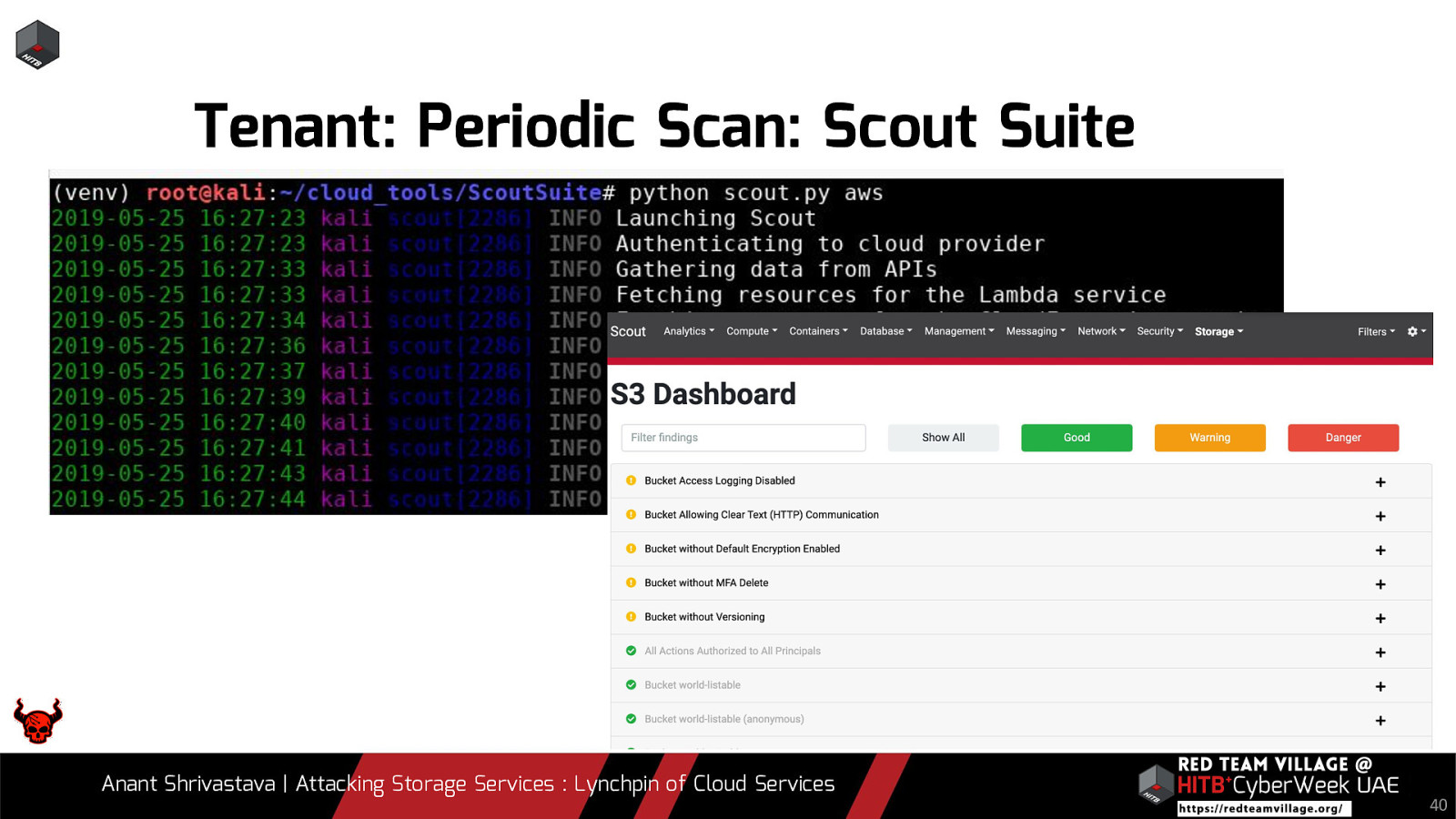
- 5. What the developers or admins have to keep in mind
- 6. Question and Answer
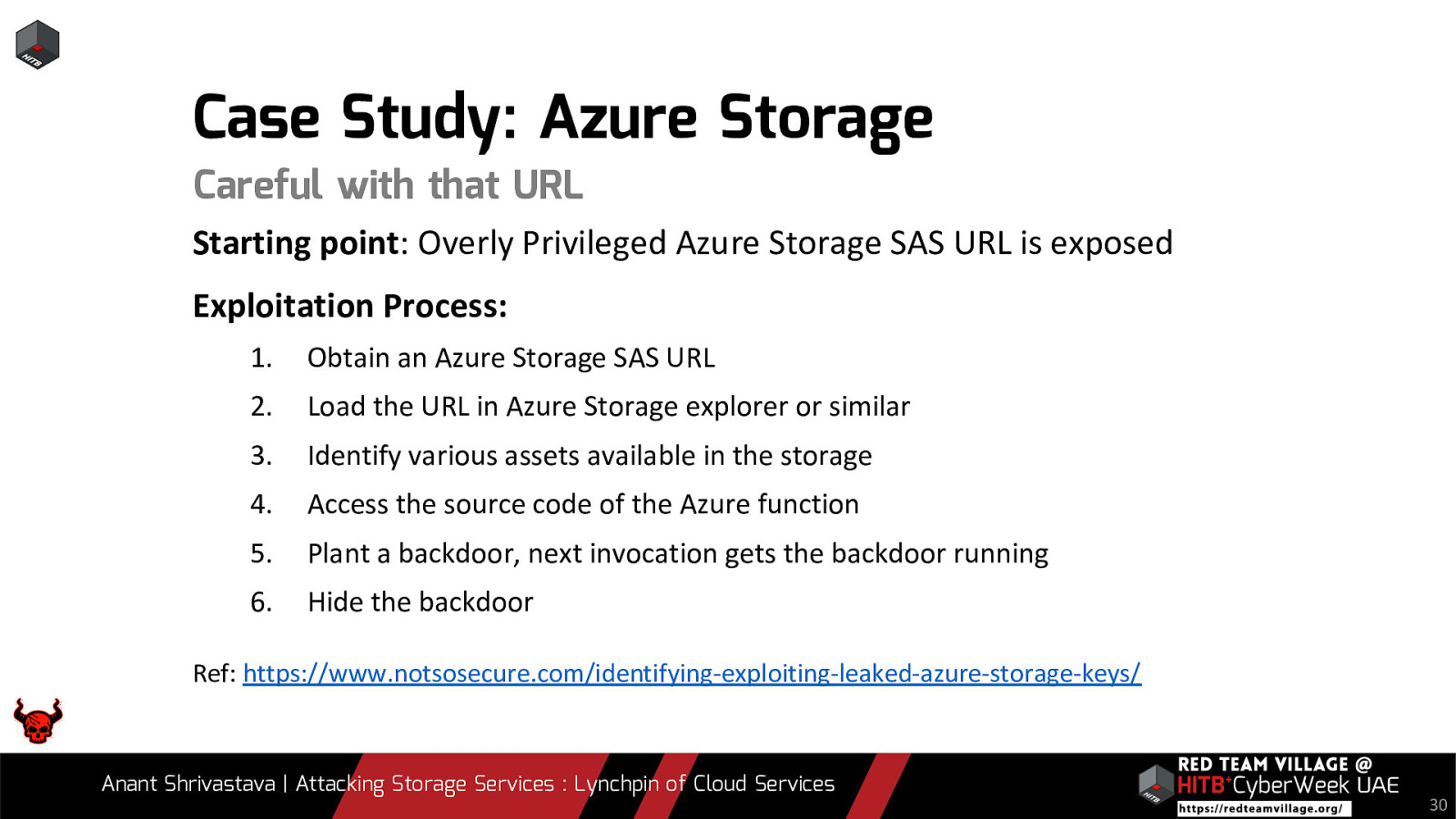
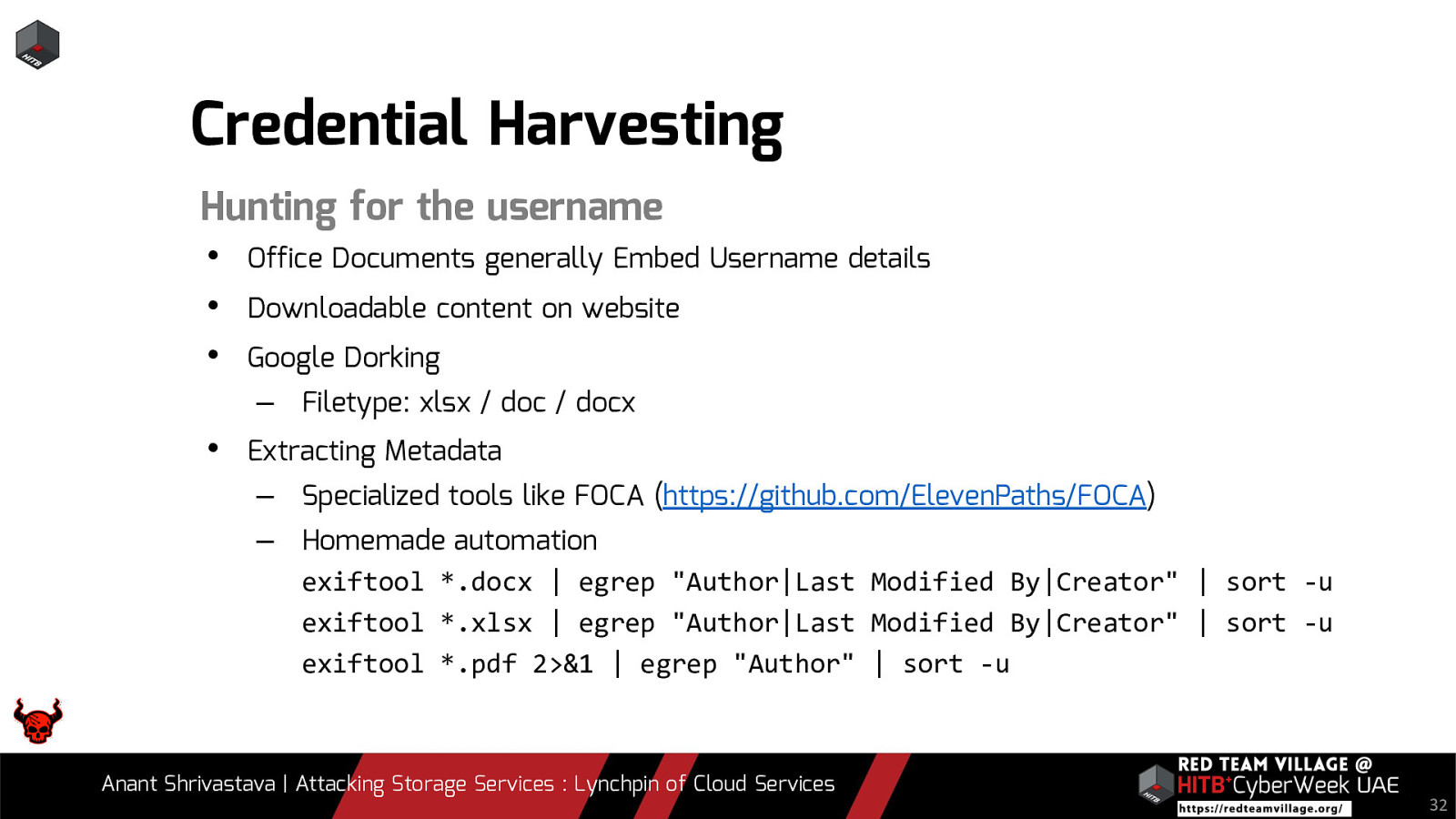
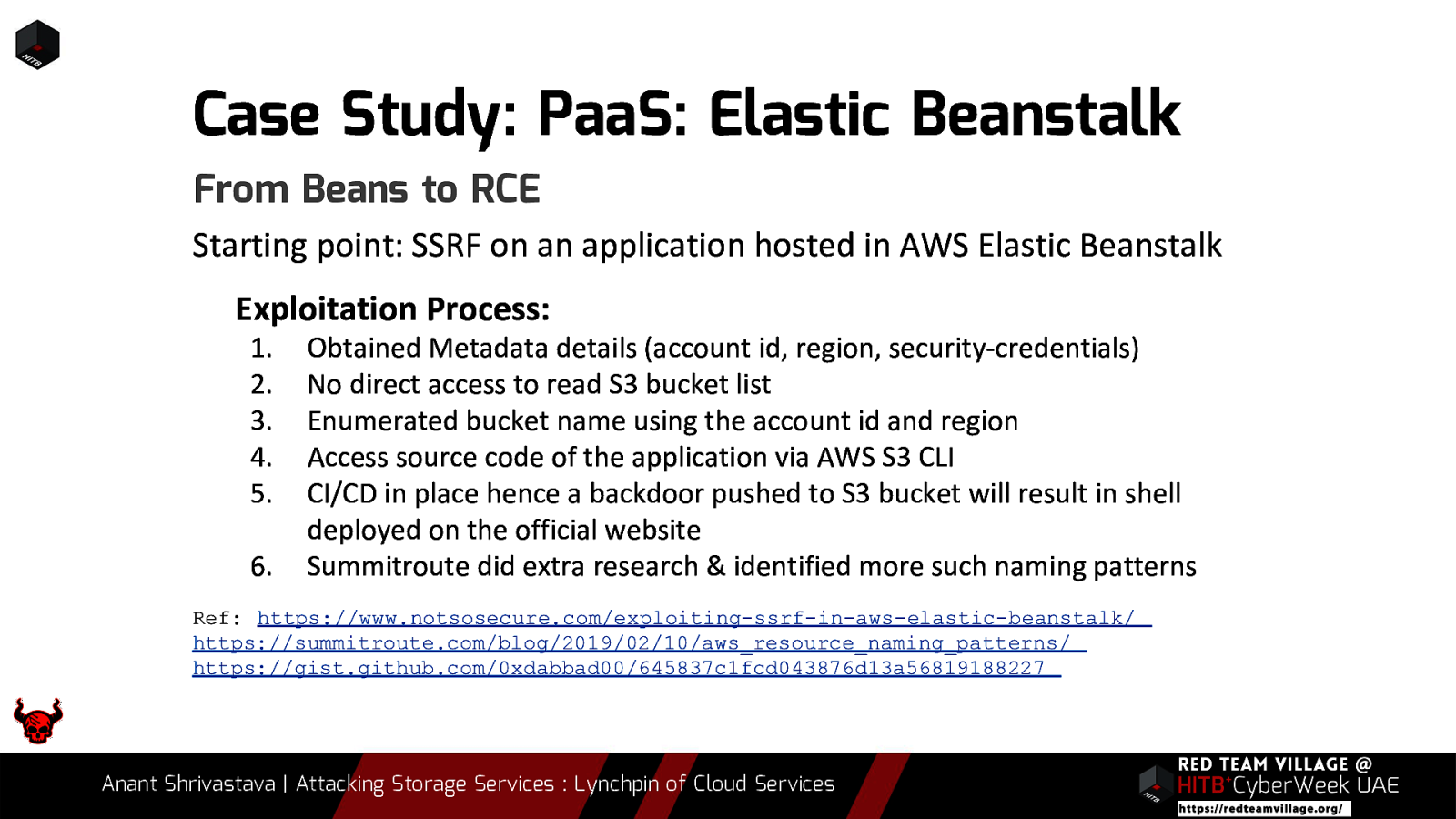
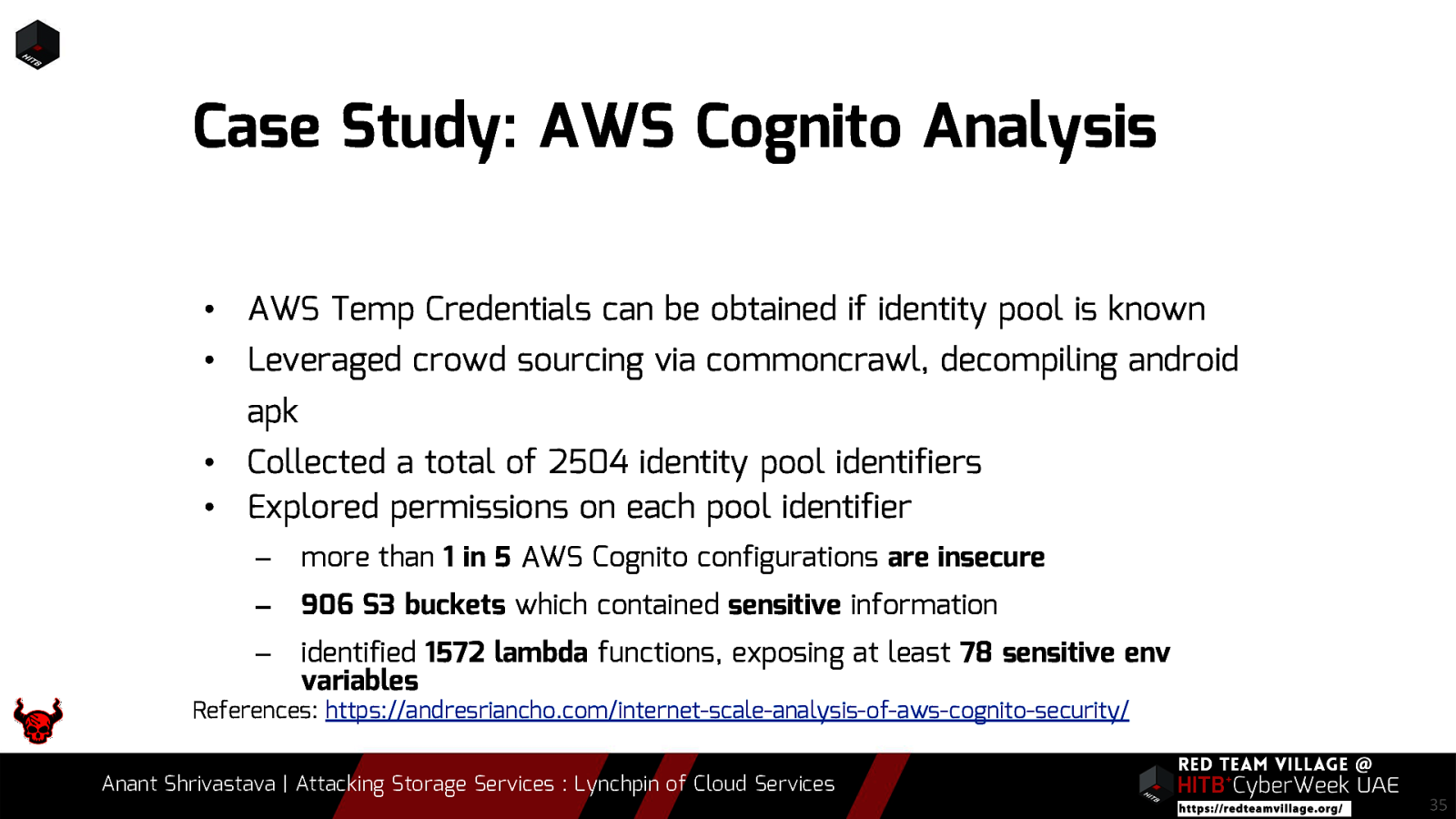
Note: Case studies will be interspersed throughout the slides
Video
Resources
The following resources were mentioned during the presentation or are useful additional information.