Nessus Reporting Karma By Anant Shrivastava http://anantshri.info anant@anantshri.info
Slide 1

Slide 2
Its not a Talk • First thing’s first – This is not a talk. – This should be an interactive session. • I am here presenting what I have worked so far to give back what I learned from community. • Need your opinion / suggestion / comments on how I can improve on it.
Slide 3

Points to Discuss • • • • • Nessus Reporting : Various formats How to customize Understanding Nessus XML format PHP code as PoC for parsing logic. Analysis : the real pain – Reclassification – False positives
Slide 4

Nessus • Do we need an introduction
Slide 5
Nessus Reporting formats • • • • HTML NBE Dot nessus v1 Dot nessus v2
Slide 6
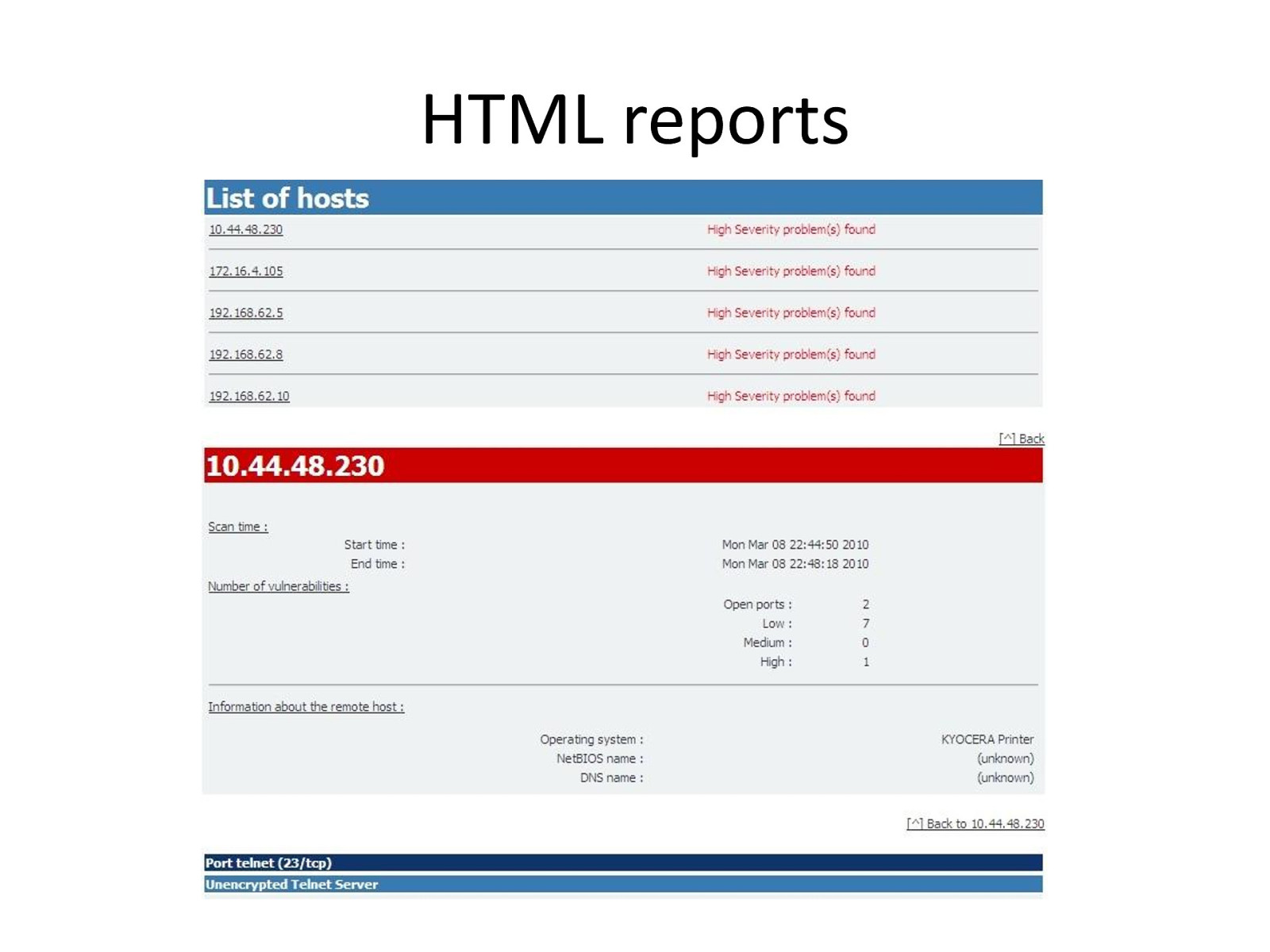
HTML reports
Slide 7
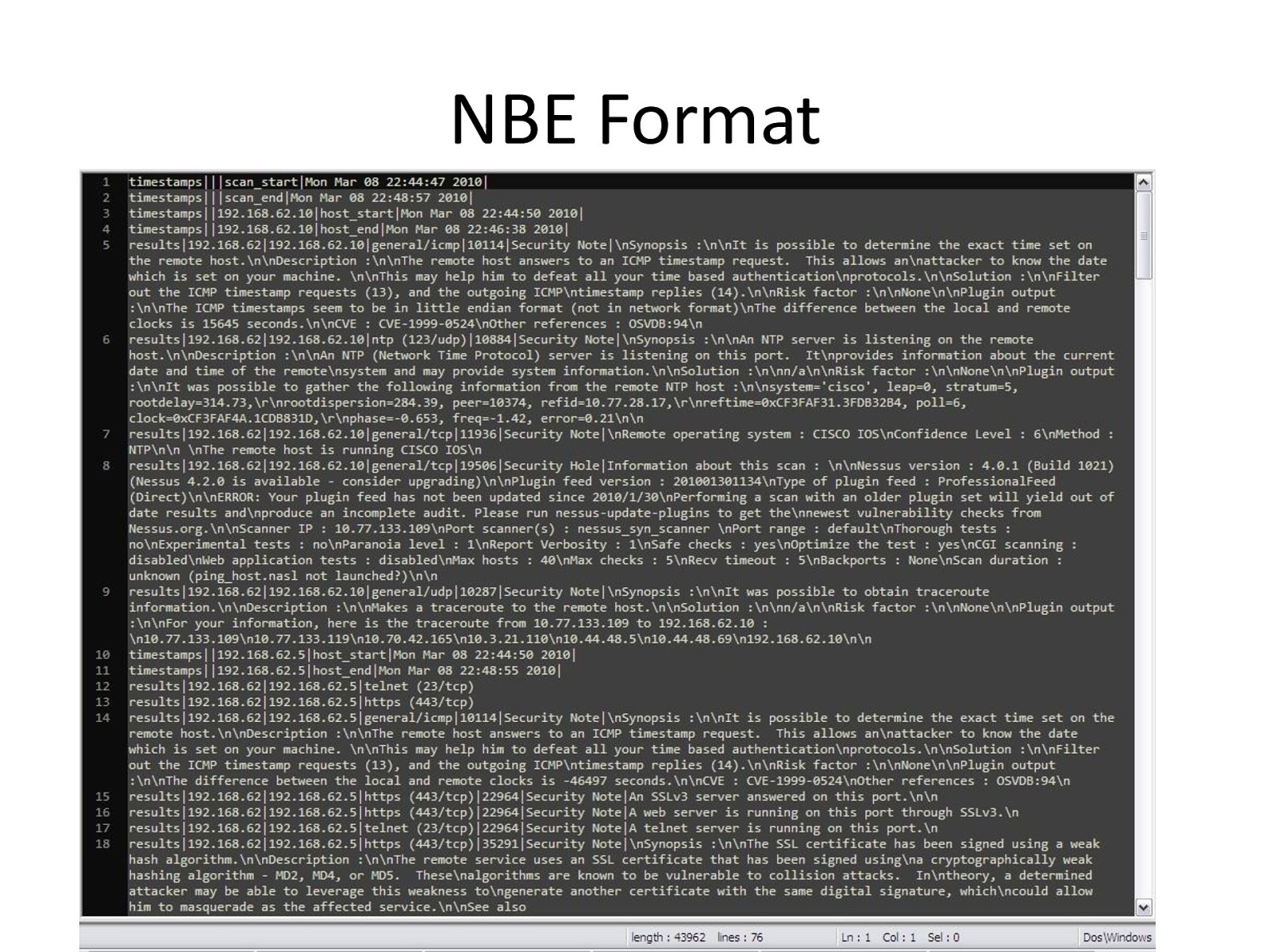
NBE Format
Slide 8
Understanding dot Nessus format • We have two nessus format. • .nessus • .nessus (v2)
Slide 9
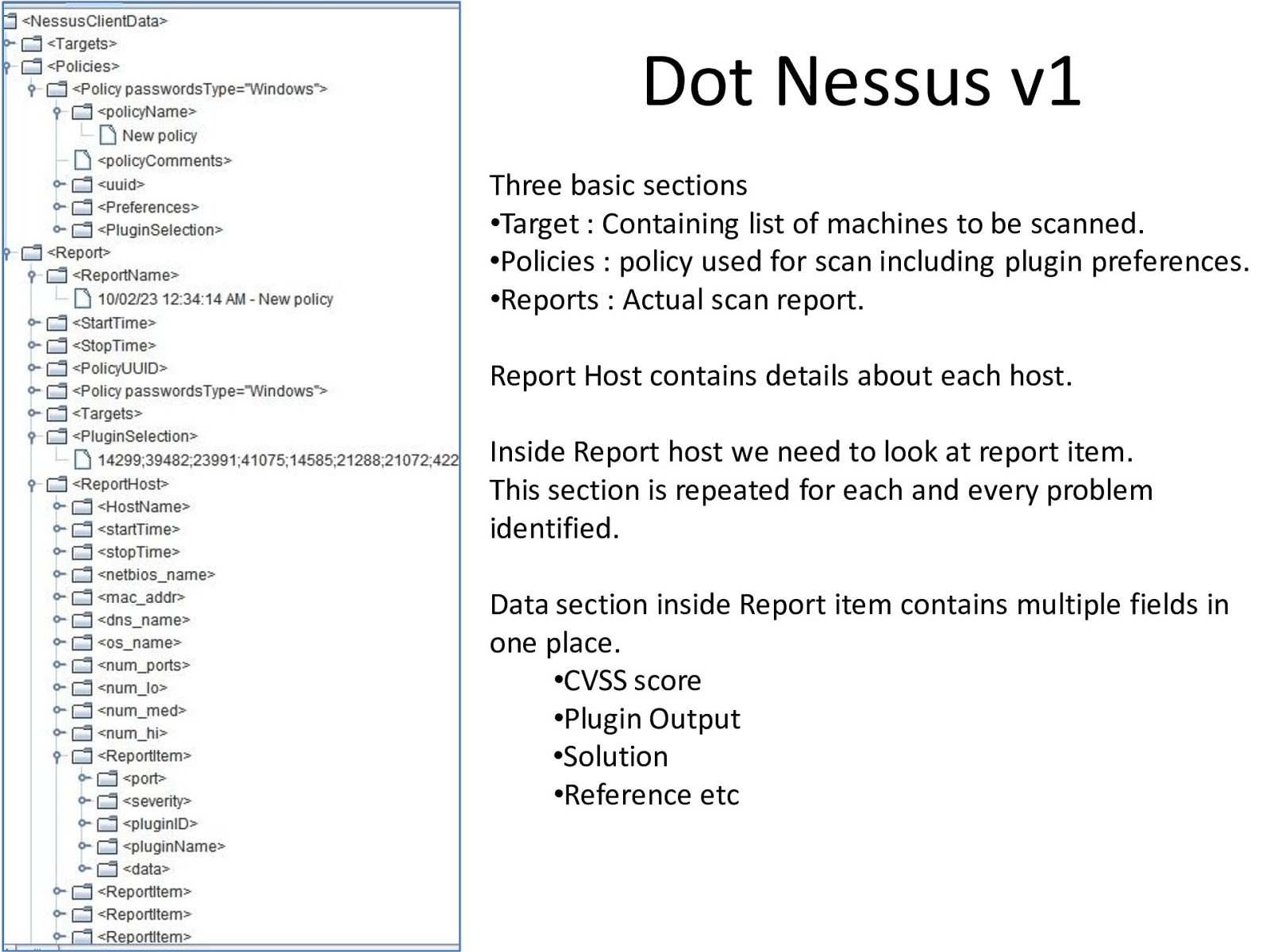
Dot Nessus v1 Three basic sections •Target : Containing list of machines to be scanned. •Policies : policy used for scan including plugin preferences. •Reports : Actual scan report. Report Host contains details about each host. Inside Report host we need to look at report item. This section is repeated for each and every problem identified. Data section inside Report item contains multiple fields in one place. •CVSS score •Plugin Output •Solution •Reference etc
Slide 10
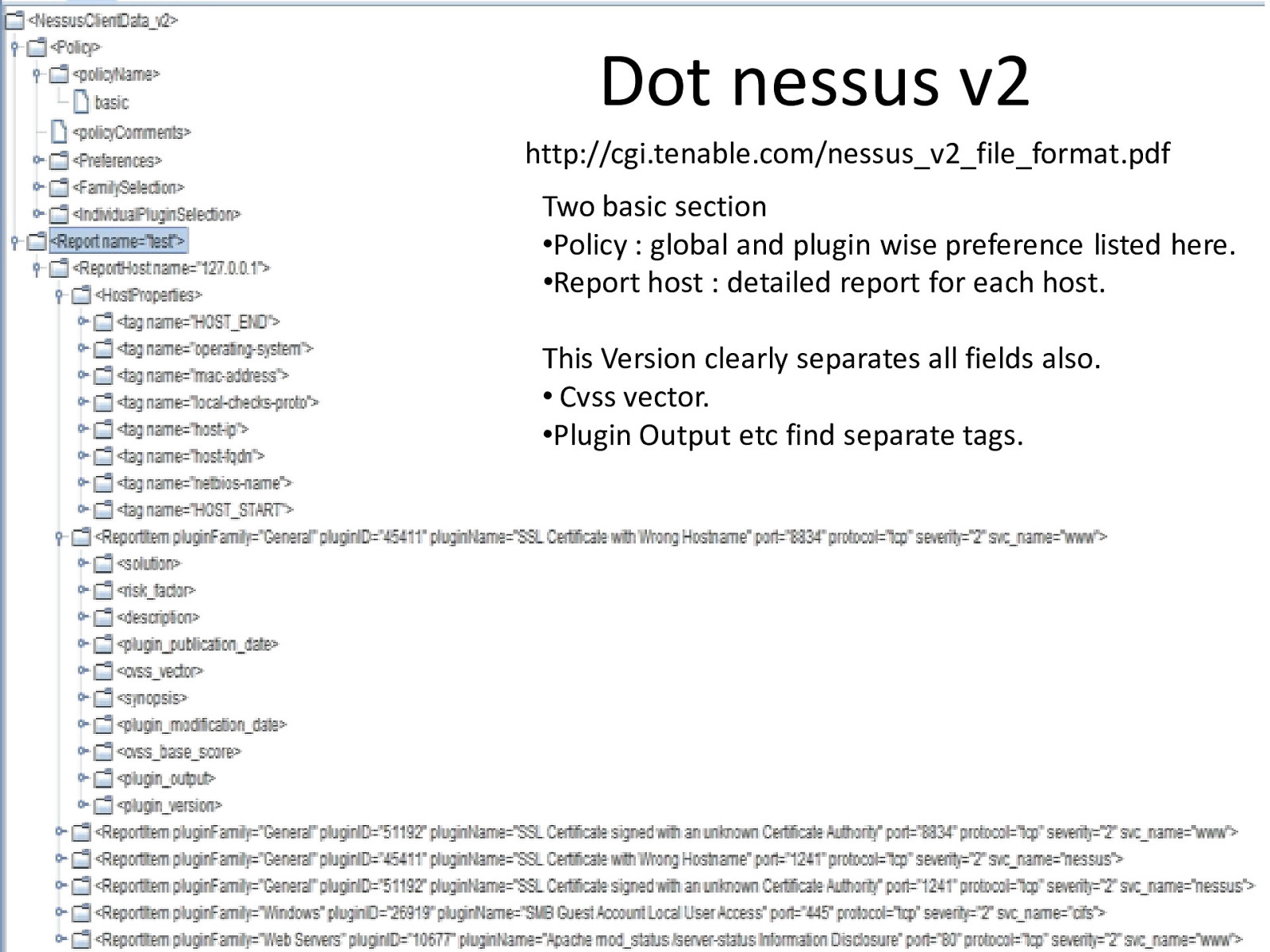
Dot nessus v2 http://cgi.tenable.com/nessus_v2_file_format.pdf Two basic section •Policy : global and plugin wise preference listed here. •Report host : detailed report for each host. This Version clearly separates all fields also. • Cvss vector. •Plugin Output etc find separate tags.
Slide 11
Continuous Evolving format (v2) • Recently added tags – exploit_available - boolean – exploit_framework_canvas - boolean – canvas_package - name – exploit_framework_metasploit - boolean – metasploit_name - name
Slide 12
Customized HTML reports • Frankly I am not good at that • However per my basic search its good option for those who don’t want to mess with the output’s too much
Slide 13
Customization
Slide 14
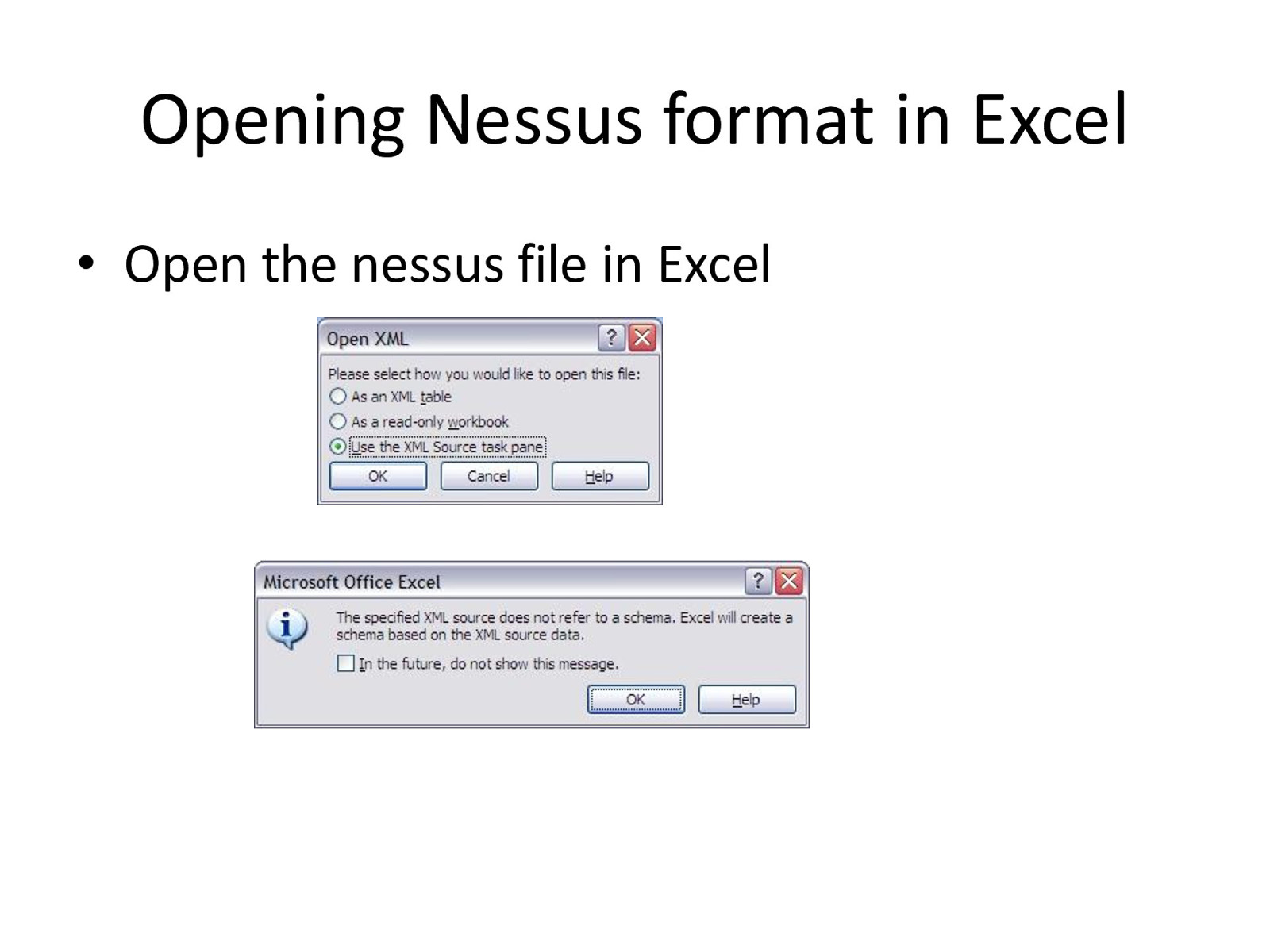
Opening Nessus format in Excel • Open the nessus file in Excel
Slide 15
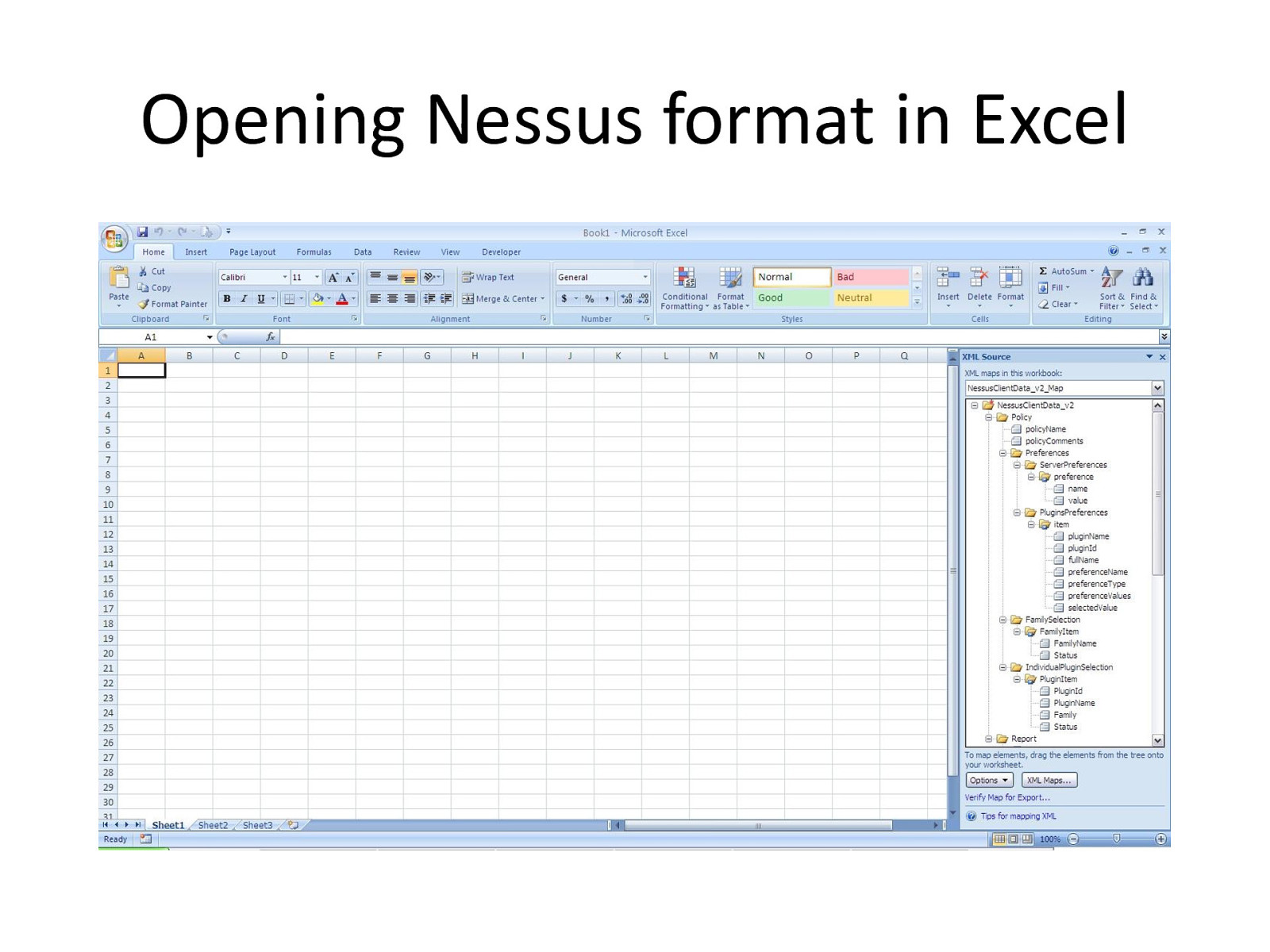
Opening Nessus format in Excel
Slide 16
Opening Nessus format in Excel
Slide 17
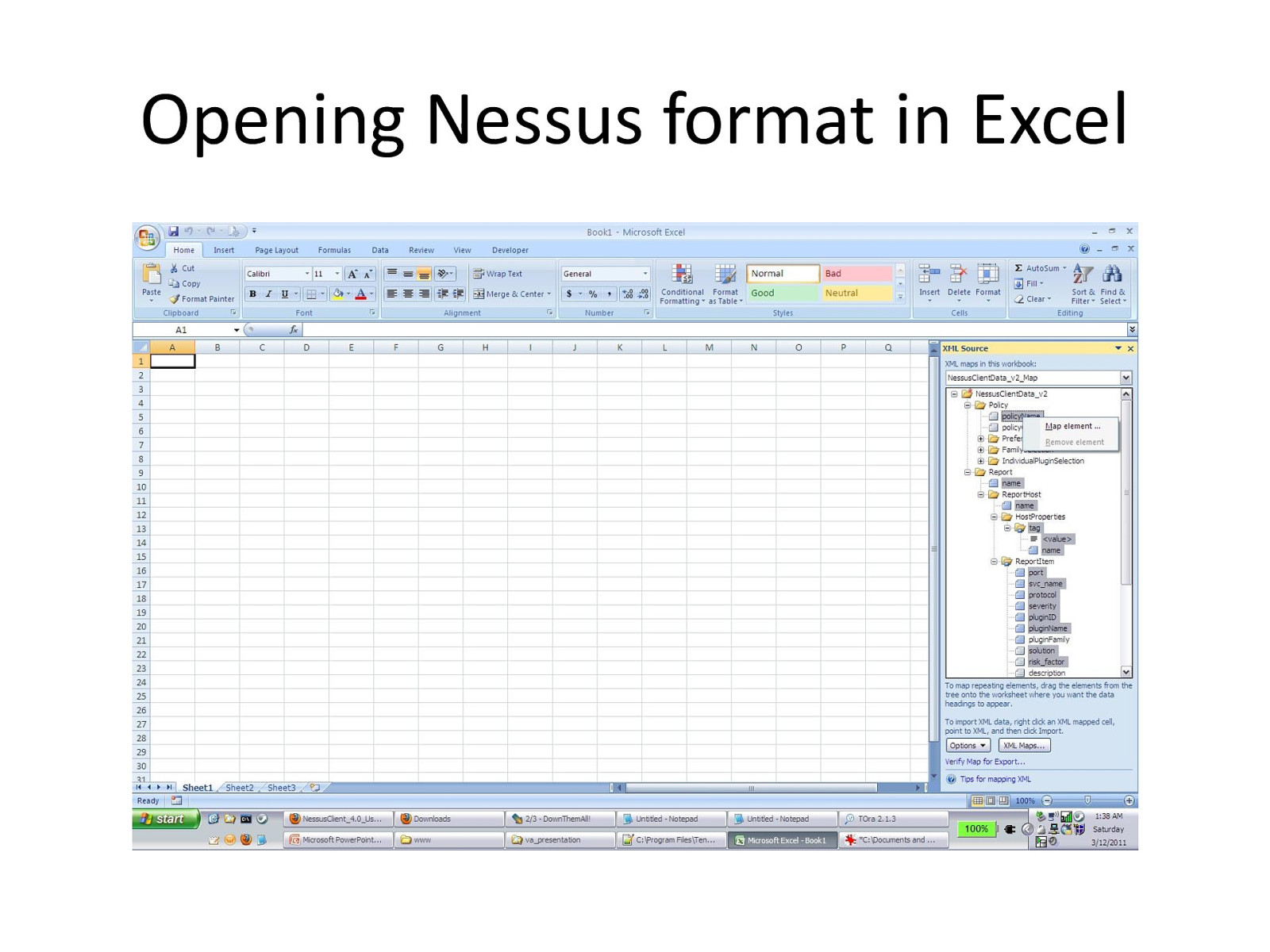
Opening Nessus format in Excel
Slide 18
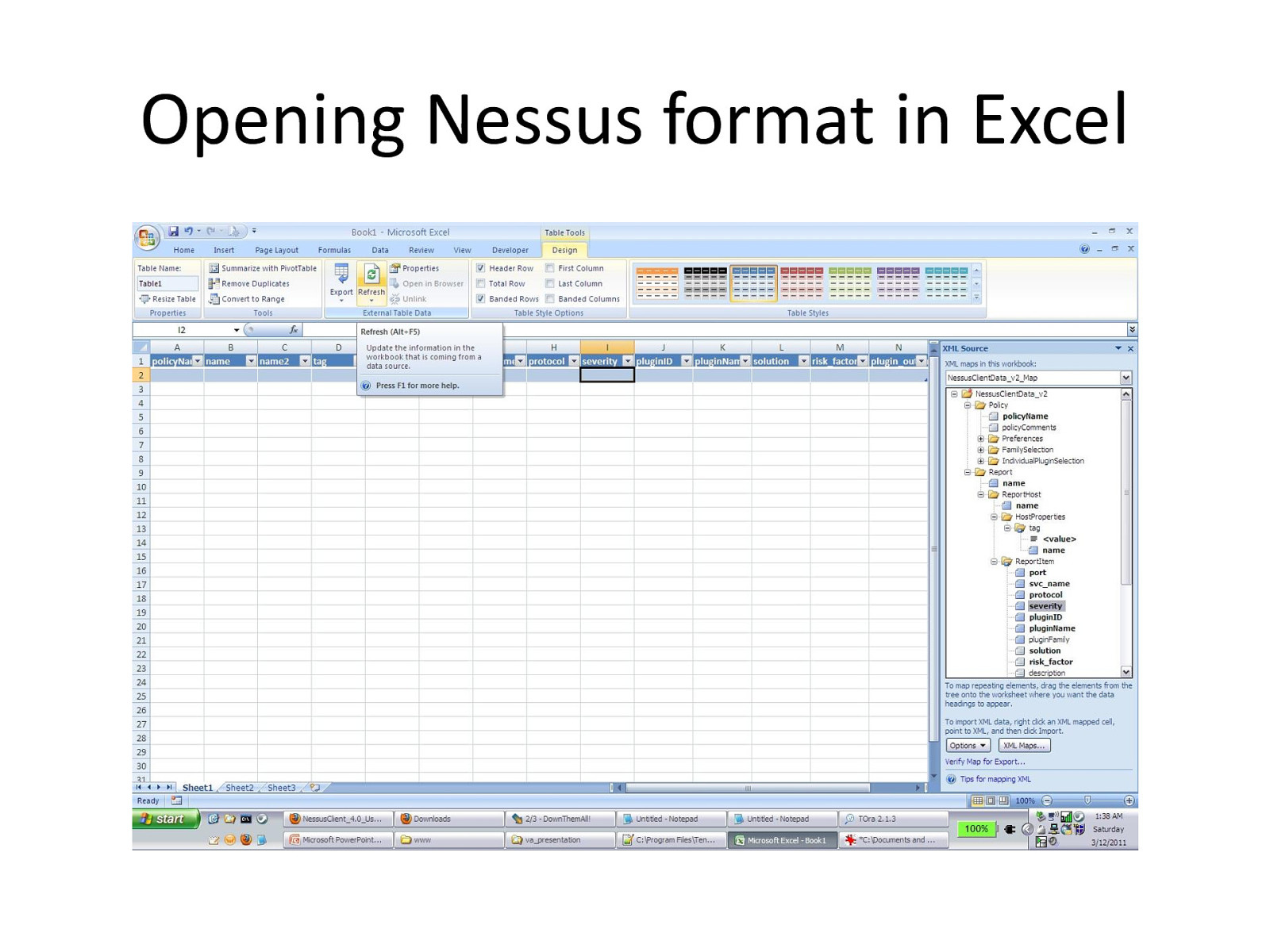
Opening Nessus format in Excel
Slide 19
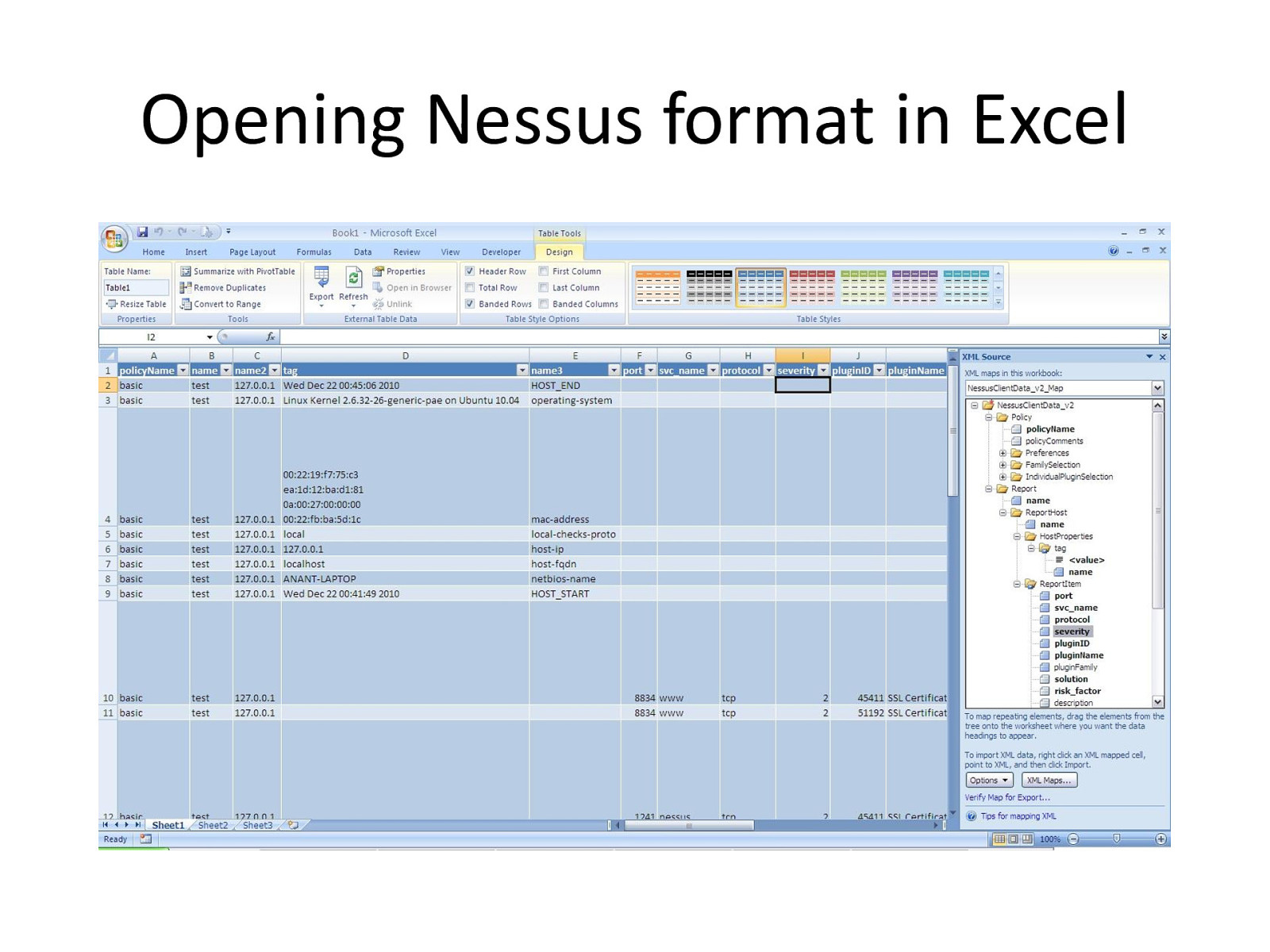
Opening Nessus format in Excel
Slide 20
Better Option • Use some parsing logic. • Some existing options – http://seccubus.com/ : very good option • Provides periodic scan option with report comparision. – http://enterprise.bidmc.harvard.edu/pub/nessusphp/ • Good php interface. – Also number of options in Python, perl for the same
Slide 21
If options exist why write again • Custom Parser writing will only be required for – Integrating with existing infra tools. • Inventory management system • Security checking tools. – More level of customization required then provided. – Better control over frequency and scan granularities.
Slide 22

PHP PoC : Shareable
<?php function read_max_nessus($file_name) { $xml = simplexml_load_file($file_name); $Policy = $xml->Policy; $report = $xml->Report; echo “Policy Name : ” . $Policy->policyName; foreach( $report->ReportHost as $hst){ $ip_address = $hst[“name”]; echo “<ol><li>IP ADDRESS : ” . $ip_address . “</li>”; $circle=”“; $server_type = $hst->HostProperties->tag[1]; $end_date = $hst->HostProperties->tag[0]; echo “<li> Server Type : ” . $server_type . “</li><li><ol>”; foreach ($hst->HostProperties->tag as $tg){ echo “<li>”. htmlentities($tg[“name”]) . ” :” . htmlentities($tg[0]) . “</li>”; } echo “</ol></li><li><ol>”; foreach ($hst->ReportItem as $rh){ if ($rh[“pluginName”]== “”){ continue; } else{ echo “<li><ul><li>Port : ” . htmlentities($rh[“port”]) . “</li>”; echo “<li>Protocol : ” . htmlentities($rh[“protocol”]) . “</li>”; echo “<li>Service Name : ” . htmlentities($rh[“svc_name”]) . “</li>”; echo “<li>Plugin ID : ” . htmlentities($rh[“pluginID”]) .”</li>”; echo “<li>Plugin Name : ” . htmlentities($rh[“pluginName”]) .”</li>”; echo “<li>Plugin Family : ” . htmlentities($rh[“pluginFamily”]) .”</li>”; echo “<li>Severity : ” . htmlentities($rh[“severity”]) . “</li>”; echo “<li>Risk Factor : “.nl2br(htmlentities($rh->risk_factor)) . “</li>”; echo “<li>Synopsis : “. nl2br(htmlentities($rh->synopsis)) . “</li>”; echo “<li>Description : “. nl2br(htmlentities($rh->description)) . “</li>”; echo “<li>Solution : “. nl2br(htmlentities($rh->solution)) . “</li>”; echo “<li>Reference CVE : ” . htmlentities($rh->cve) . “</li>”; echo “<li>CVSS Base Score : ” . htmlentities($rh->cvss_base_score) . “</li>”; echo “<li>CVSS Vector : ” . htmlentities($rh->cvss_vector) . “</li>”; echo “<li>X ref : ” . htmlentities($rh->xfref) . “</li>”; echo “<li>Bug Track Id : ” . htmlentities($rh->bid) . “</li>”; echo “<li>Plugin Output : ” . nl2br(htmlentities($rh->plugin_output)) . “</li>”; echo “<li>Exploit Available : ” . $rh->exploit_available . “</li>”; echo “<li>Exploit Available in MetaSpolit : ” . $rh->exploit_framework_metasploit . “</li>”; echo “<li>MetaExploit Name : ” . $rh->metasploit_name . “</li>”; echo “<li>Exploit Available in CANVAS : ” . $rh->exploit_framework_canvas . “</li>”; echo “<li>CANVAS Package Name : ” . $rh->canvas_package . “</li>”; echo “<li>See Also : ” . nl2br(htmlentities($rh->see_also)) . “</li></ul></li>”; } } echo “</ol></li></ol>”; } } ?>Slide 23

Actual Work • • • • PHP front end for Report uploading to DB DB used : Oracle Integration with Inventory Management Tool Analysis – Known False positive identification by plugin id. – Grouping common vulnerabilities in group – Classification on Network and Server devices • Excel based report extraction
Slide 24
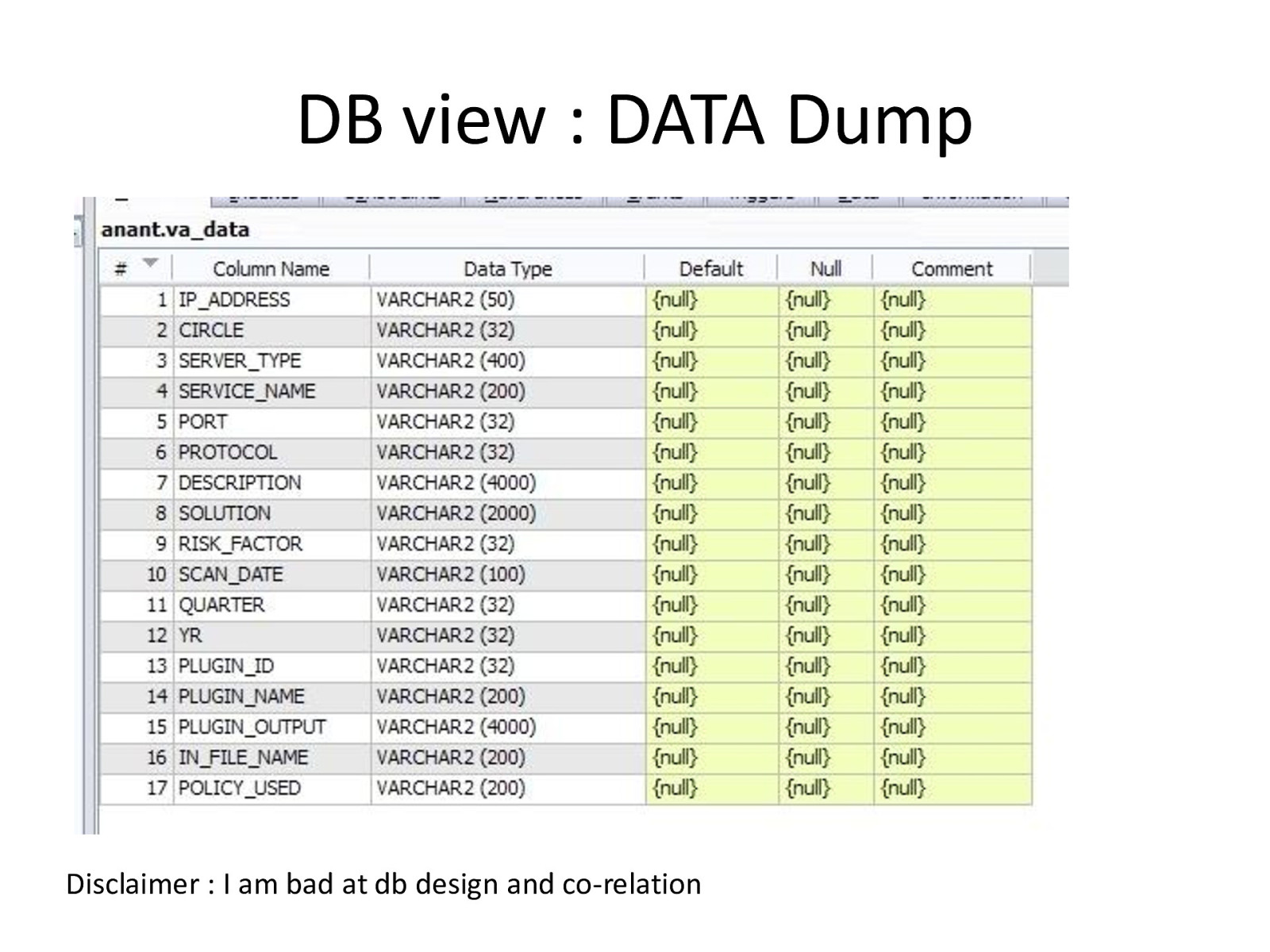
DB view : DATA Dump Disclaimer : I am bad at db design and co-relation
Slide 25

Front End
Slide 26
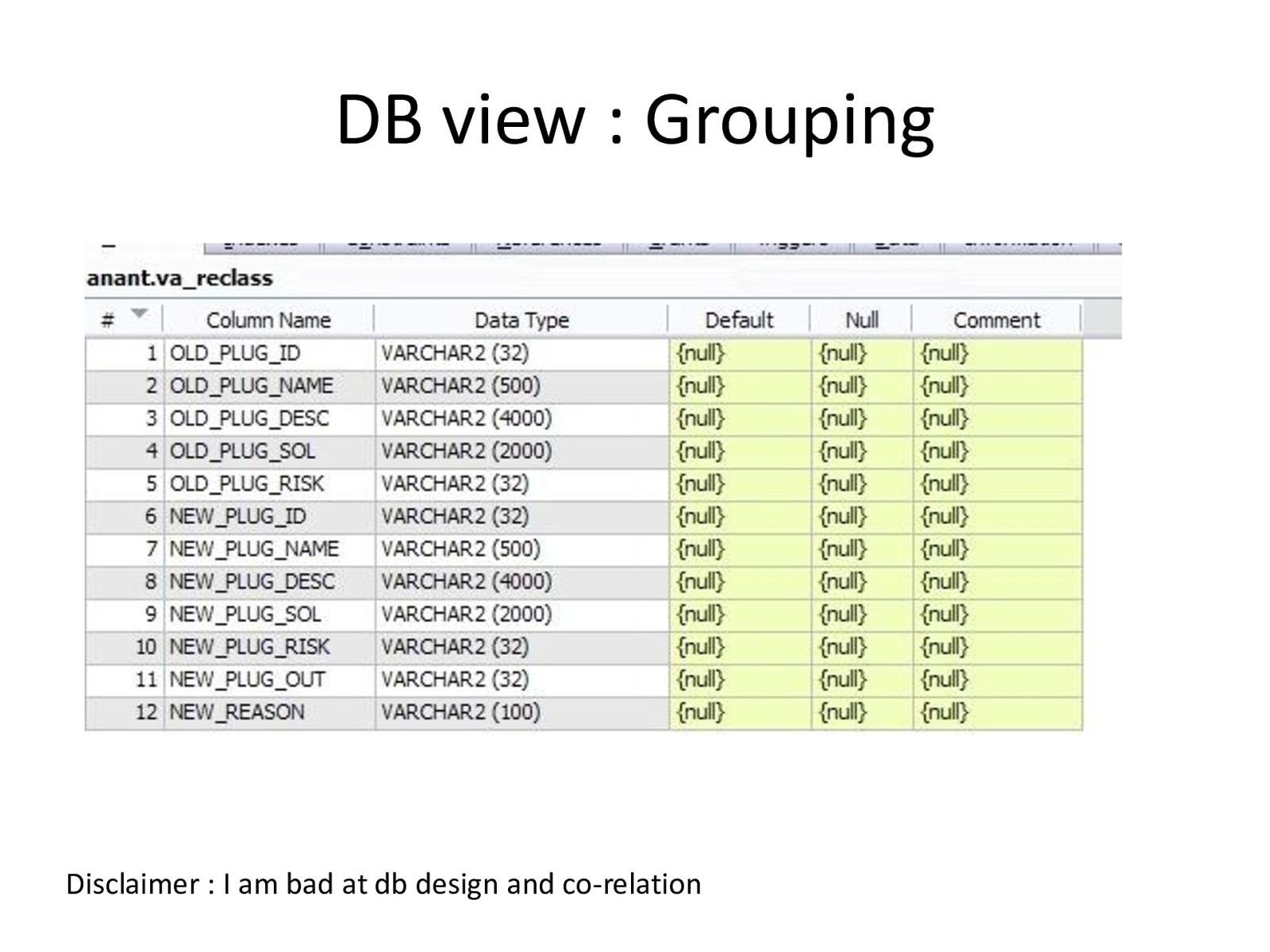
DB view : Grouping Disclaimer : I am bad at db design and co-relation
Slide 27
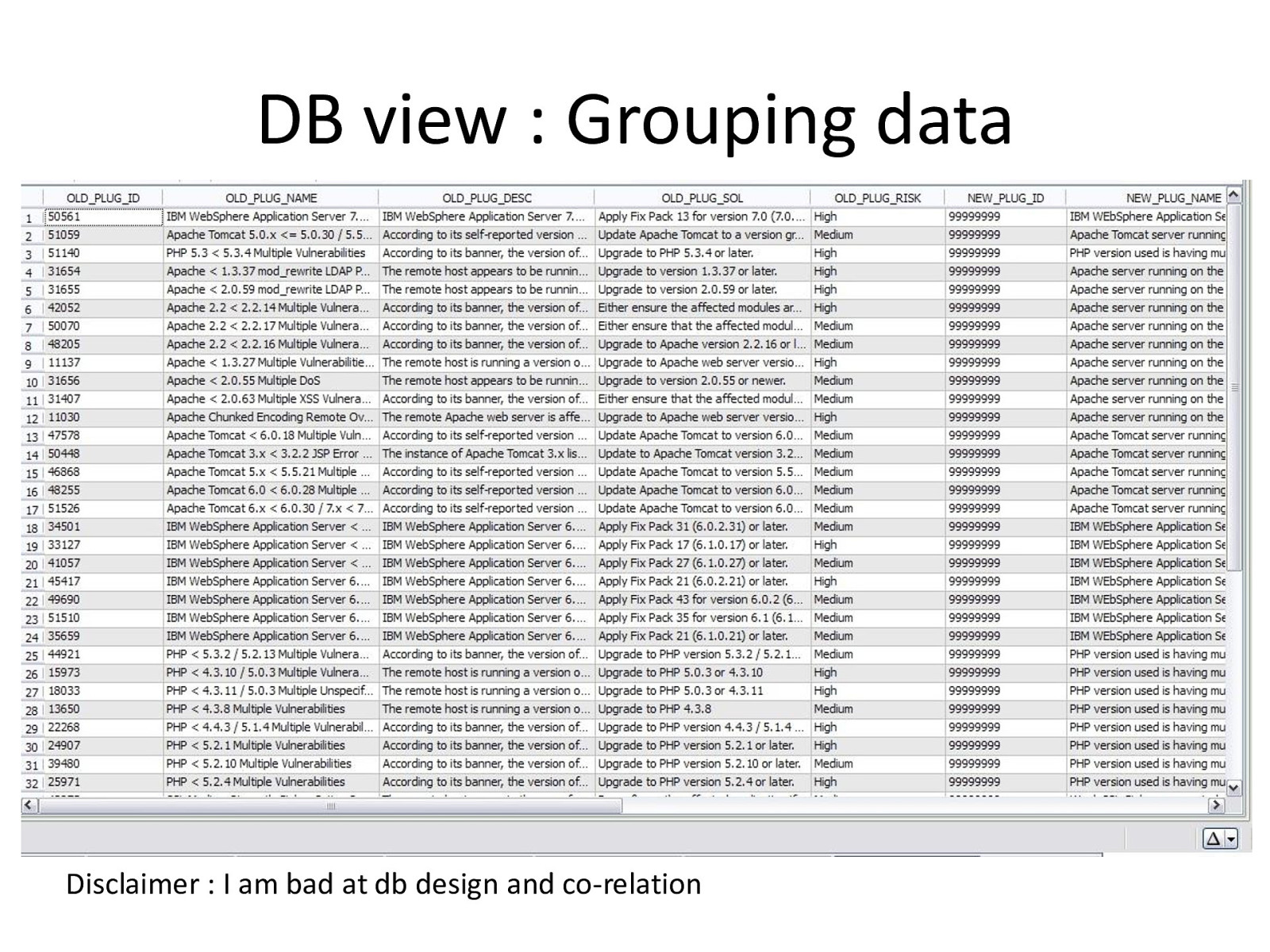
DB view : Grouping data Disclaimer : I am bad at db design and co-relation
Slide 28
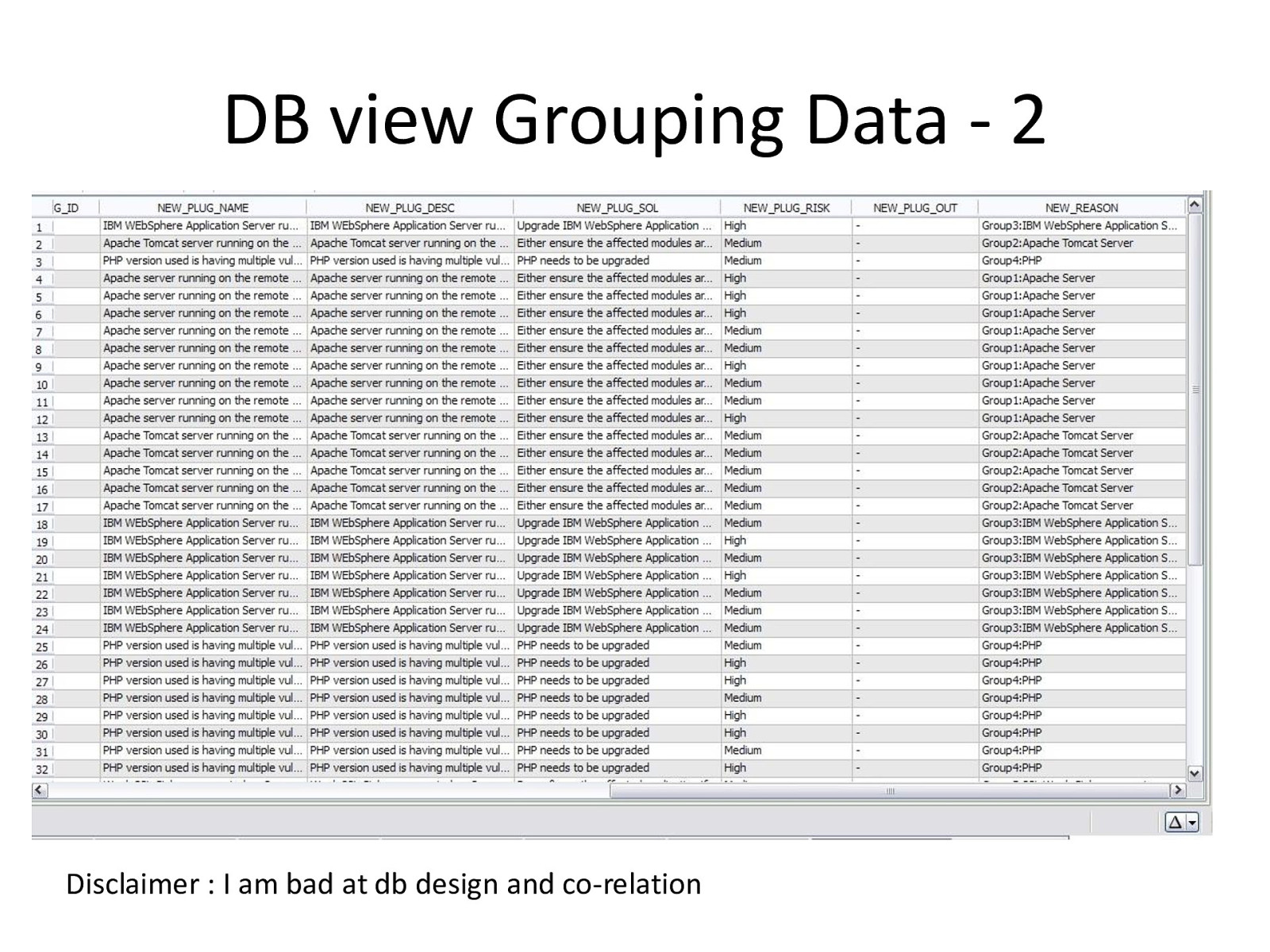
DB view Grouping Data - 2 Disclaimer : I am bad at db design and co-relation
Slide 29
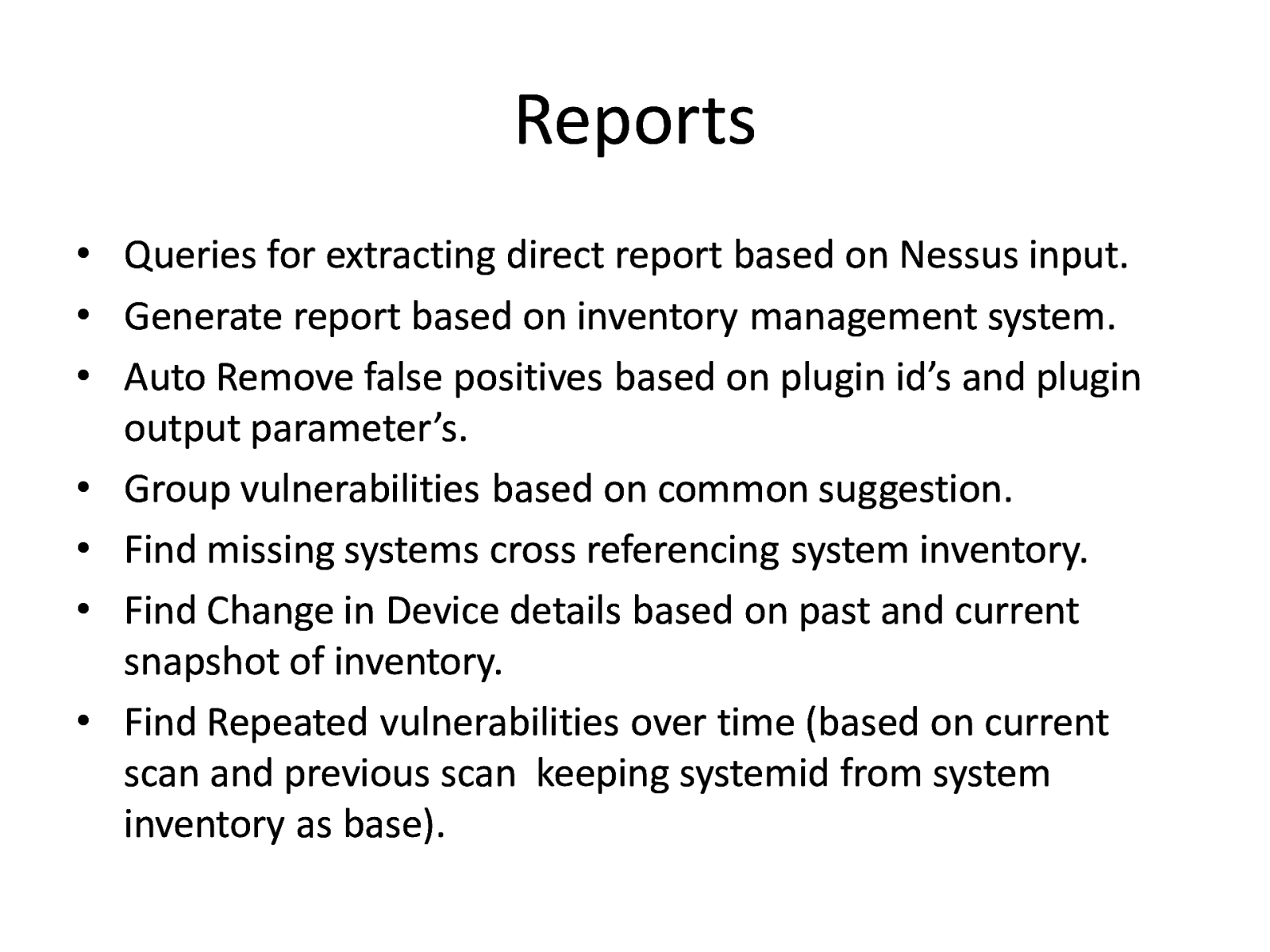
Reports • Queries for extracting direct report based on Nessus input. • Generate report based on inventory management system. • Auto Remove false positives based on plugin id’s and plugin output parameter’s. • Group vulnerabilities based on common suggestion. • Find missing systems cross referencing system inventory. • Find Change in Device details based on past and current snapshot of inventory. • Find Repeated vulnerabilities over time (based on current scan and previous scan keeping systemid from system inventory as base).
Slide 30
Extract all plugin details • Till Nessus 4.2 version – Nessus –Spq localhost 1241 <user> <pass> • Above 4.2 – XML RPC interface
Slide 31

Road Ahead • This is what I have planned so far – Creating similar interface for OpenVAS. – Use XMLRPC for remote initialization and control. – Keep MySQL as an alternative option
Slide 32
Thanks • Thanks for still being seated. • I hope this presentation might help you in any way. • Please come forward if you have any comment or suggestion.