SBoM The Fad, The Future, and In-Between Anant Shrivastava
Slide 1
Slide 2

Anant Shrivastava ● Chief researcher @ Cyfinoid Research ● 15+ yrs of industry exposure ● Speaker / Trainer: BlackHat, c0c0n, nullcon, RootConf, RuxCon ● Project Lead: ● ○ Code Vigilant (Code Review Project) ○ Hacking Archives of India, ○ TamerPlatform (Android Security) (@anantshri on social platforms) https://anantshri.info (C) Cyfinoid Research 2
Slide 3
Software Bill of Material • Itemized list of all the ingredients in the software • Ingredients means mostly third-party components • • • • • Software name Version Checksum License information Dependencies list if possible • SBoM’s are mostly for one level depth only with other levels plugged in each other. (C) Cyfinoid Research 3
Slide 4
Every standard starts with competition • SPDX • ISO Standard • Github provides default export in this format • CycloneDX • OWASP Supported • SWID • Alternative ISO specification https://www.ntia.gov/files/ntia/publications/sbom_formats_survey-version-2021.pdf (C) Cyfinoid Research 4
Slide 5
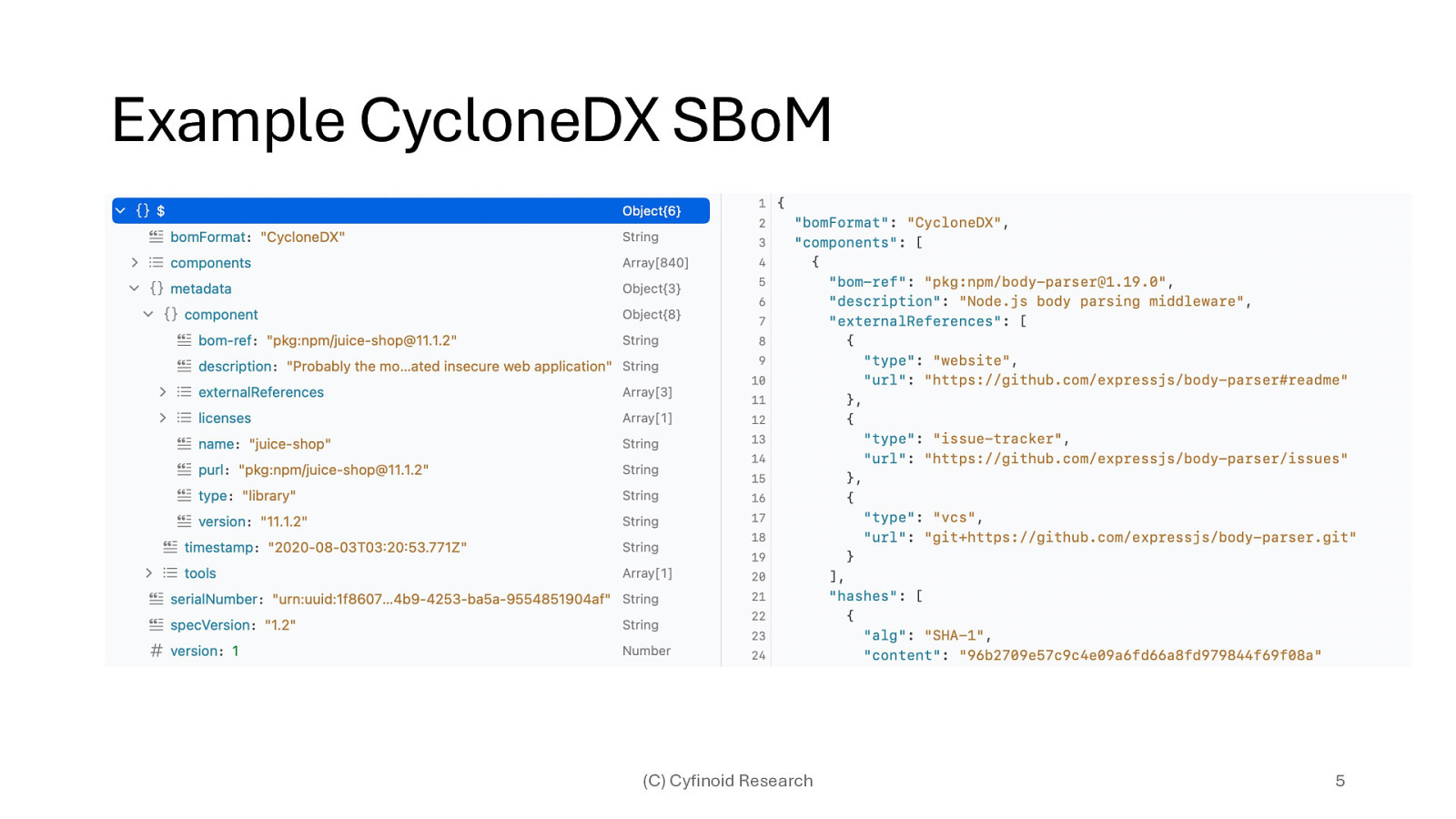
Example CycloneDX SBoM (C) Cyfinoid Research 5
Slide 6
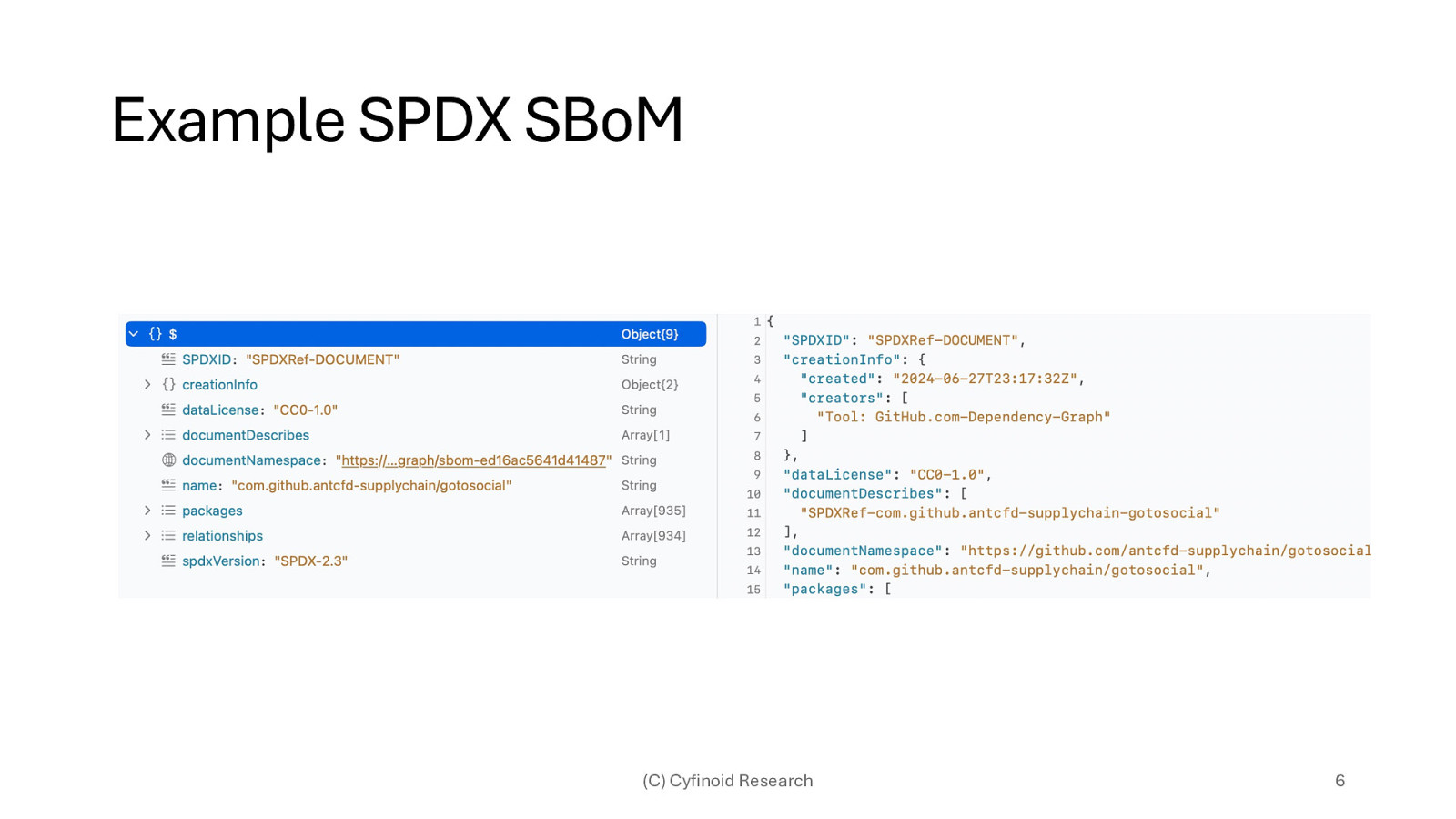
Example SPDX SBoM (C) Cyfinoid Research 6
Slide 7

How to create SBoM • Github provides dependency Graph in “Insights” • SBoM generation tools • Cdxgen • https://github.com/CycloneDX/cdxgen • SPDX Generator • https://github.com/spdx/tools • /dev/hand if all else fails (Its XML) (C) Cyfinoid Research 7
Slide 8
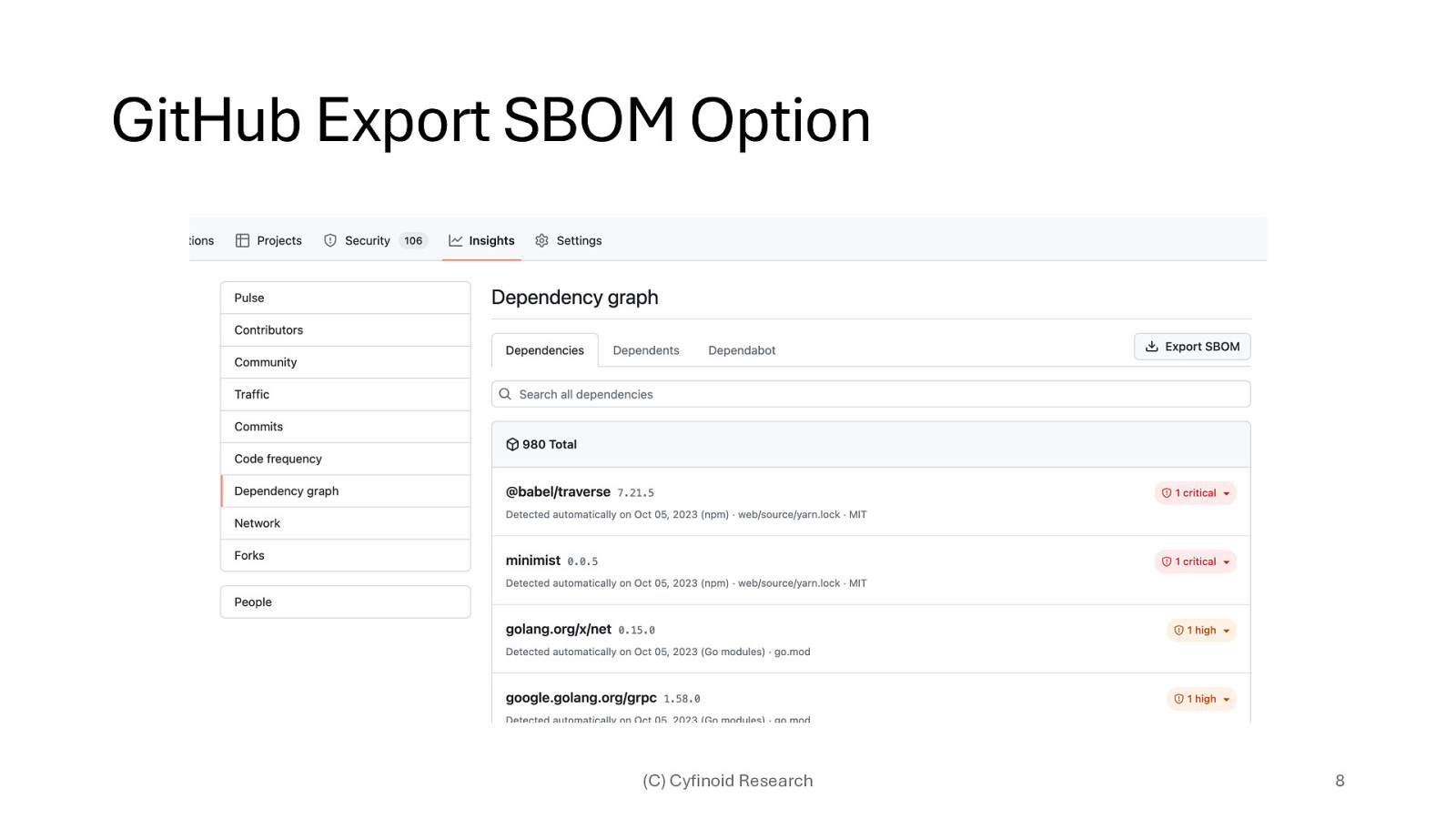
GitHub Export SBOM Option (C) Cyfinoid Research 8
Slide 9

(C) Cyfinoid Research 9
Slide 10
Is SBoM really useful • SBoM rose to prominence coz of exec order by US President. • Requirement is to create SBoM • No directions around usage, consumption etc • SBoM Tells you software composition nothing else • Industry representatives have started asking Questions? • Should we focus on building SBOM or fix issues in that time? (C) Cyfinoid Research 10
Slide 11
Thoughts from Industry around SBoM • Why should I disclose my composition to the world • I will only share the SBoM to NDA covered entities • I don’t need SBoM coz I don’t sell to USA • Better to spend time in fixing bugs then making SBoM (C) Cyfinoid Research 11
Slide 12
Food for thought software industry is mostly fixing problems created by software industry (C) Cyfinoid Research 12
Slide 13
What problems have we created • Software build automation == quicker release cycle • Automated release cycle == less wait for features • Faster feature release == less inclination to upgrade dependencies • Too much focus on OSS Codebase without helping the maintainers • Impossible segregation of features and bug fixes • Automated notification of vulnerability (hedonic hamster wheel) (C) Cyfinoid Research 13
Slide 14
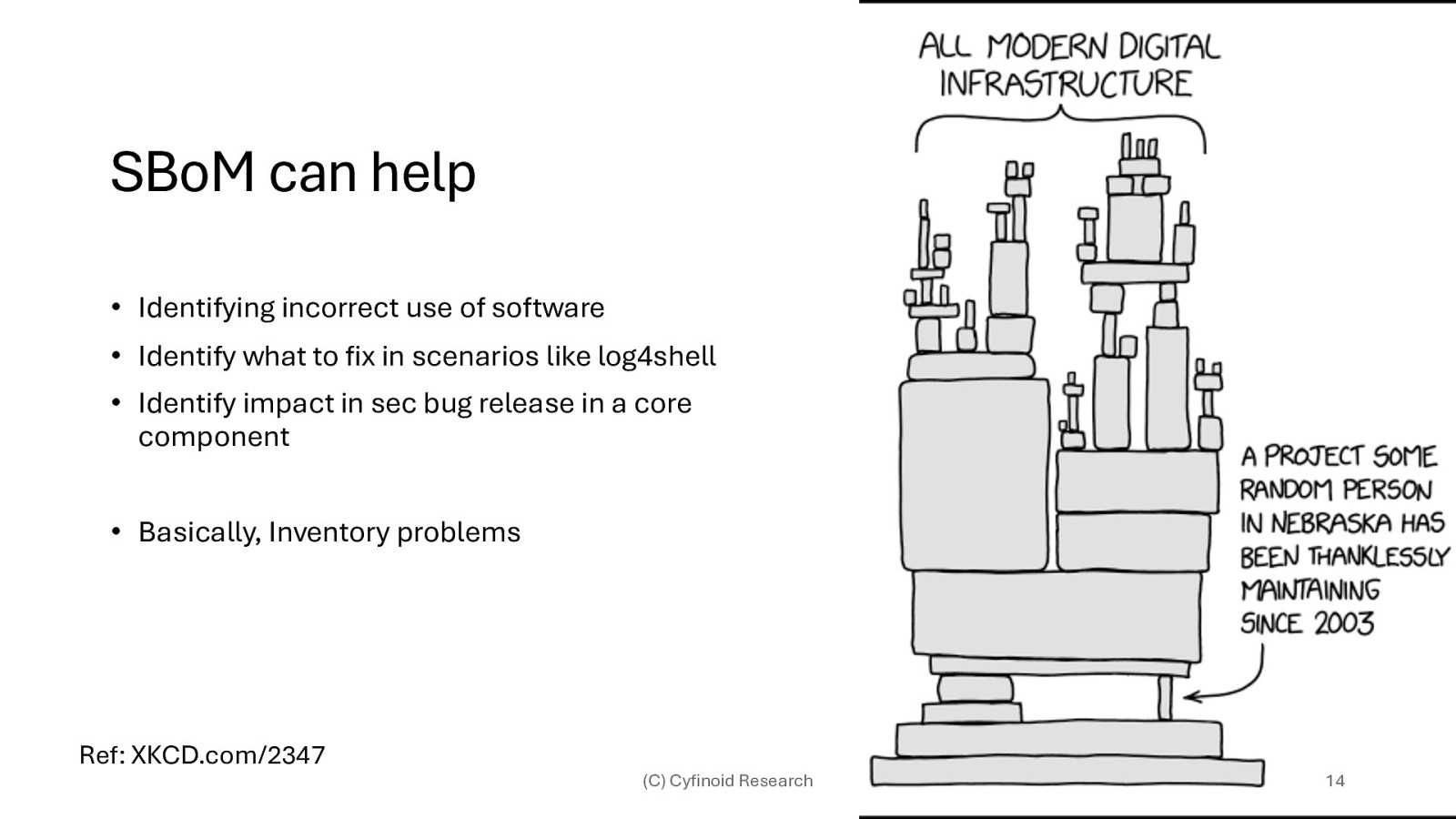
SBoM can help • Identifying incorrect use of software • Identify what to fix in scenarios like log4shell • Identify impact in sec bug release in a core component • Basically, Inventory problems Ref: XKCD.com/2347 (C) Cyfinoid Research 14
Slide 15

Another thought • Infosec has never had the luxury of well-maintained inventory • SBoM can help with it • we never had inventory; we don’t even know what to do with it when its created (C) Cyfinoid Research 15
Slide 16
Consequences for Infosec For Practitioners both infosec and Devops • We have been asking for better visibility, this is it For Industry entities • This is like “opening the kimono” moment (C) Cyfinoid Research 16
Slide 17

If security practitioners want to preserve this facility they need to act now (C) Cyfinoid Research 17
Slide 18

(C) Cyfinoid Research 18
Slide 19
Existing tooling • OWASP Cyclone DX : https://cyclonedx.org/ • Google SLSA dev : https://slsa.dev/ • SPDX : https://spdx.dev/ • SafeDep : https://safedep.io/ • Dependency Tracker: https://dependencytrack.org/ • SYFT : https://github.com/anchore/syft (C) Cyfinoid Research 19
Slide 20
Security efforts already in progress • VDR : Vulnerability Disclosure Report • VEX : Vulnerability Exploitability eXchange • xBoM’s • • • • • • Software-as-a-Service Bill of Materials (SaaSBOM) Hardware Bill of Materials (HBOM) Machine Learning Bill of Materials (ML-BOM) Cryptography Bill of Materials (CBOM) Manufacturing Bill of Materials (MBOM) Operations Bill of Materials (OBOM) • Attestations (C) Cyfinoid Research 20
Slide 21
What can we do • Security is largely considered a cost center and any incentive that is solely useful for security is a cost. • Inventory allows organization to make data driven decisions • Make SBoM’s usefulness visible for other departments • If more people especially profit centers and business requirements (HR, Finance) need it, its hard to kill (C) Cyfinoid Research 21
Slide 22
SBoM Usage beyond security teams Use each SBoM as part of inventory, Consolidate then and then draw inferences from it • Development • Acquisitions and mergers • Compliance (adjunct security) • Risk Management (C) Cyfinoid Research 22
Slide 23
SBoM usage for Developers • Manage technical Debt • Reduce dependency scatter • Consolidate efforts for usage • Simplified package selection in case of newer project (C) Cyfinoid Research 23
Slide 24

SBoM usage for Acquisitions & Mergers Use SBoM as an indicator for future cost and decision • Too many outdated / EOL / unmaintained software in use leads to high cost of ownership after acquisitions • If the toolset / techstack is vastly different than existing, then extra talent cost • If too many techstacks in picture, shows non cohesive teams (C) Cyfinoid Research 24
Slide 25

SBoM usage for Compliance • Licensing policy spread not just at product but at input component level • Possible cost of rework due to non-compliance with company policy • Possible repercussions if my code touches this code (GPL restrictions to name as one) (C) Cyfinoid Research 25
Slide 26
SBoM usage for Risk Management Interesting questions that can be answered • Do I want to include X amount of risk by purchasing this vendor’s software? • If risk is low but product will be highly visible, can I still afford it. • Even with high risk, in a self-contained environment is it okey • Do I really want my SSO auth token going into this software (C) Cyfinoid Research 26
Slide 27
What is needed • Better tooling (tech and UX) • Current tools are not easy to use even for practitioners • Collaboration and seeking feedback from other parties • Don’t make tooling for yourself make it for others • Focus on usage not on glamorizing tech • We technologists focus too much of technical side. (C) Cyfinoid Research 27
Slide 28

To Conclude • I believe SBoM is a Boon for overall IT Industry to move in better directions. • Newton’s first law of motion stands : Inertia can only be countered by greater force • There is a bright future ahead if we can muster the courage for it (C) Cyfinoid Research 28
Slide 29
Thanks for listening & open to Questions? NAME WEBSITE anant@cyfinoid.com EMAIL (C) Cyfinoid Research 29
Slide 30
References • What if we spent all the time it took to make SBOMs fixing bugs instead? #appsec #sbom : https://www.youtube.com/watch?v=jdNtUK8kpJE • SBoM Guidance by Kymberlee Price: https://www.youtube.com/watch?v=_yWRQ6XM6pQ (C) Cyfinoid Research 30