DevSecOps What, Why and How Anant Shrivastava NotSoSecure Global Services @anantshri
Slide 1

Slide 2

About Anant Shrivastava • Director NotSoSecure Global Services • Sysadmin / Development / Security • Project Owner: AndroidTamer, Codevigilant • Contributor : OWASP, null, G4H and more • https://anantshri.info (@anantshri on social platforms) NotSoSecure Global Services (a Claranet group company) • Boutique Consulting firm specialized in training and consulting
Slide 3

Agenda ● What is DevSecOps ● Why do we need DevSecOps ● How do we do DevSecOps ● Integrate Security in Pipeline ● Tools of Trade ● Sample Implementation ● Case Studies
Slide 4

Disclaimer ● I will be listing a lot of tools, It’s not an exhaustive list. ● I don’t endorse or recommend any specific tool / vendor ● Every environment is different: Test and validate before implementing any ideas.
Slide 5
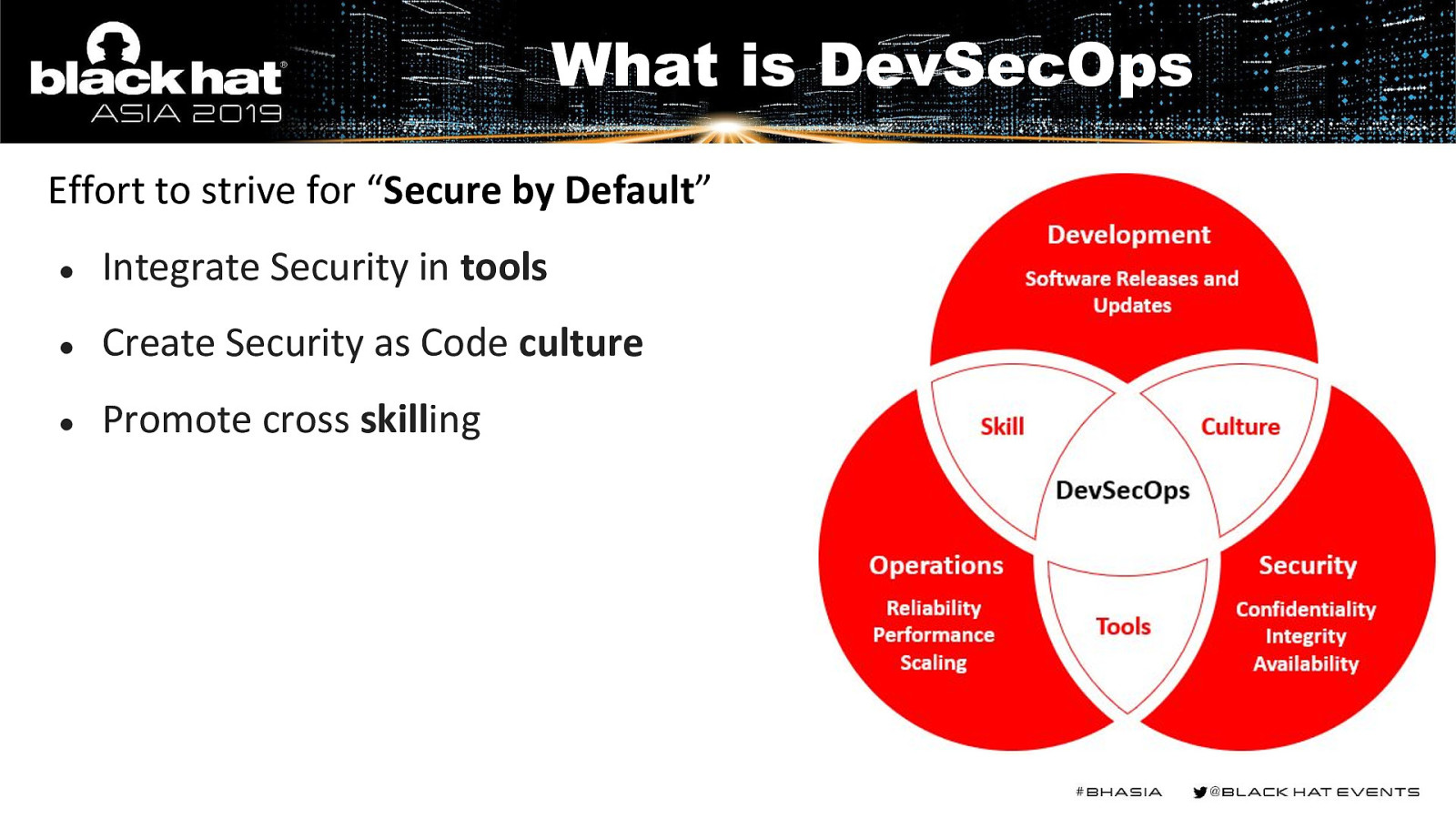
What is DevSecOps Effort to strive for “Secure by Default” ● Integrate Security in tools ● Create Security as Code culture ● Promote cross skilling
Slide 6
Why do we need DevSecOps ● DevOps moves at rapid pace, traditional security just can’t keep up ● Security as part of process is the only way to ensure safety
Slide 7
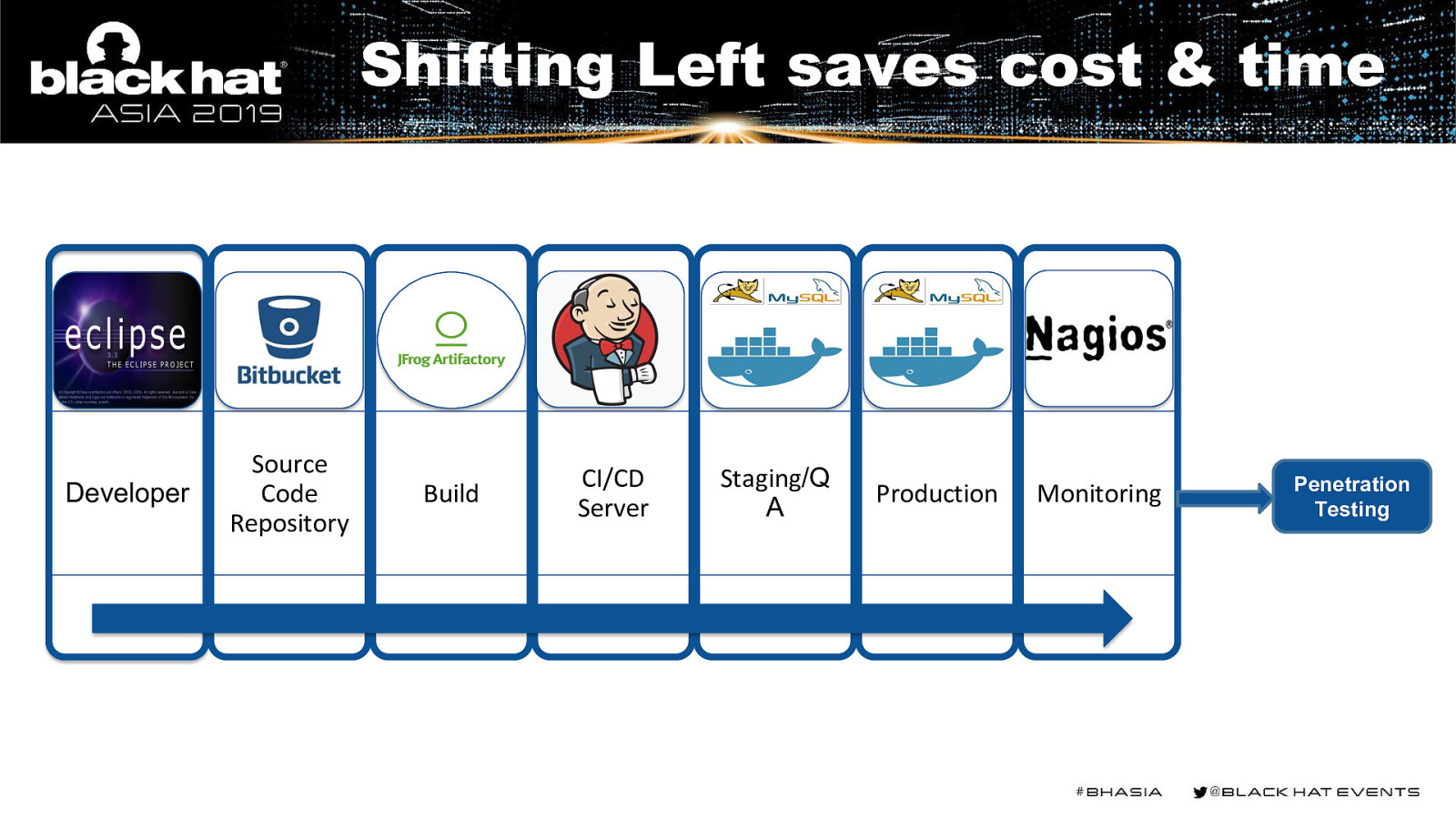
Shifting Left saves cost & time Developer Source Code Repository Build CI/CD Server Staging/Q A Production Monitoring Penetration Testing
Slide 8
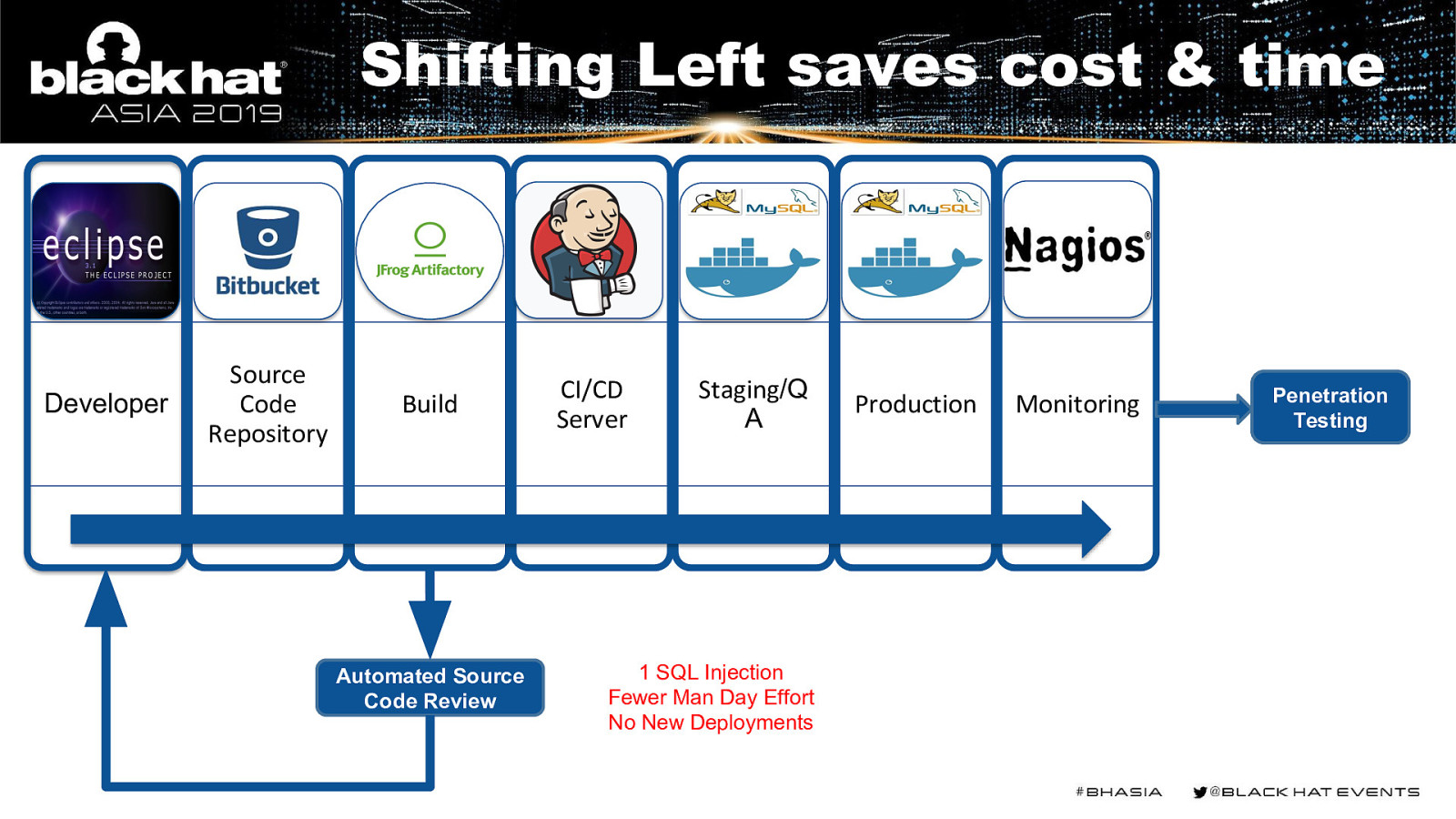
Shifting Left saves cost & time Developer Source Code Repository Build Automated Source Code Review CI/CD Server Staging/Q A 1 SQL Injection Fewer Man Day Effort No New Deployments Production Monitoring Penetration Testing
Slide 9
How do we do DevSecOps • DevSecOps is Automation + Cultural Changes • Integrate security into your DevOps Pipeline • Enable cultural changes to embrace DevSecOps
Slide 10
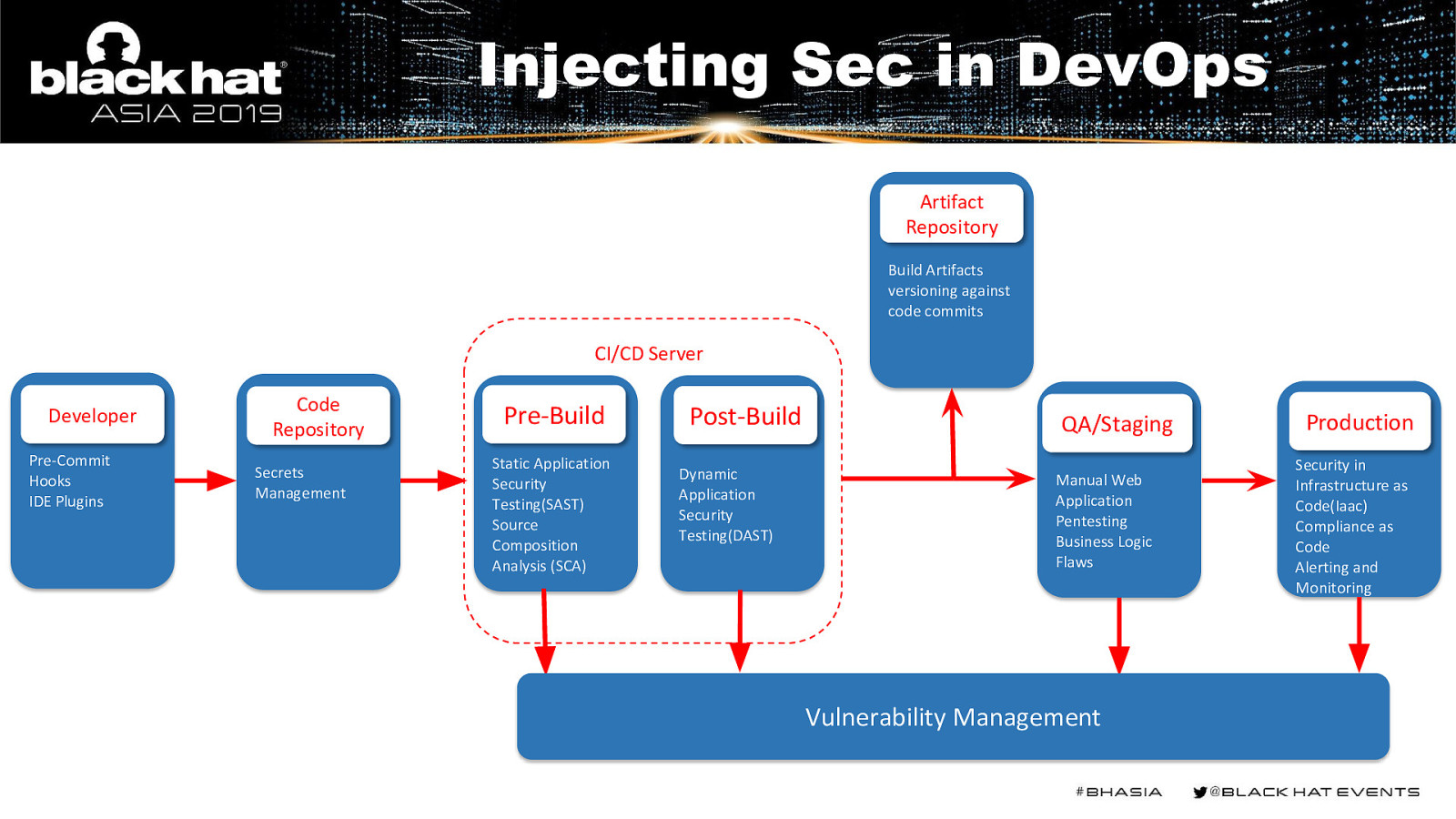
Injecting Sec in DevOps Artifact Repository Build Artifacts versioning against code commits CI/CD Server Developer Pre-Commit Hooks IDE Plugins Code Repository Secrets Management Pre-Build Static Application Security Testing(SAST) Source Composition Analysis (SCA) Post-Build Dynamic Application Security Testing(DAST) QA/Staging Manual Web Application Pentesting Business Logic Flaws Vulnerability Management Production Security in Infrastructure as Code(Iaac) Compliance as Code Alerting and Monitoring
Slide 11
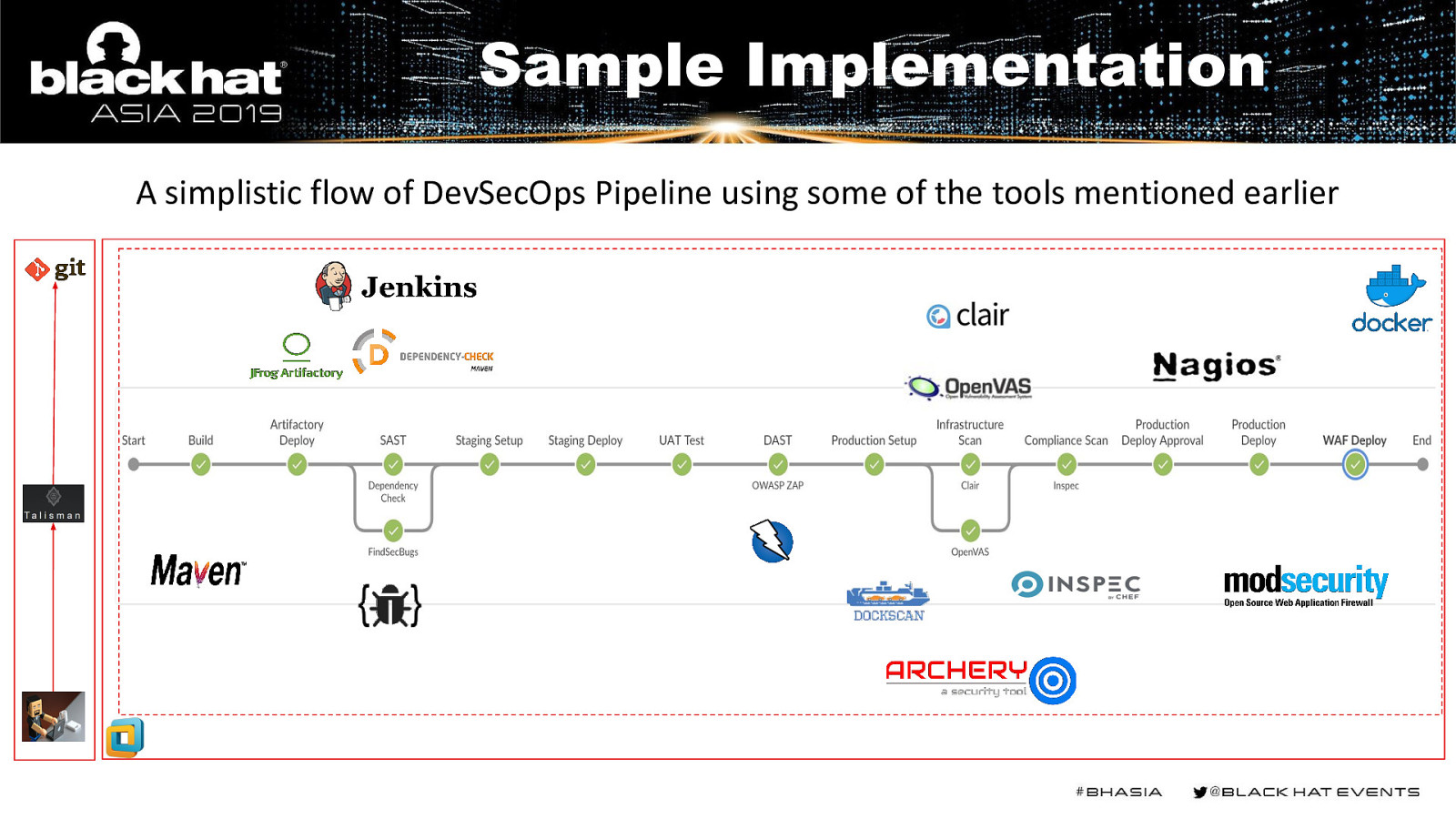
Sample Implementation A simplistic flow of DevSecOps Pipeline using some of the tools mentioned earlier
Slide 12

Tools of trade ThreatSpec. Threat Modelling Tools truffleHog Pre-Commit Hooks Software Composition Analysis Secret Management Git Hound Retire.js Static Analysis Security Testing (SAST) IDE Plugins Microsoft Threat Modeling Tool CAT.net Keywhiz Preference Given to opensource tools; we don’t endorse any tool
Slide 13

Tools of trade Vulnerability Management Jackhammer Dynamic Security Analysis Infrastructure Scan Compliance as Code Docker Bench for Security WAF Preference Given to opensource tools; we don’t endorse any tool
Slide 14

To be or not to be in Pipeline ● API / command line access ● Execution start to final output should be 15 minutes max ● Containerized / scriptable ● Minimal licensing limitations (parallel scans or threads) ● Output format parsable / machine readable (no stdout, yes to json /xml) ● Configurable to counter false negatives / false positives
Slide 15
What about Cloud • The Threat Landscape changes • Identity and Access Management • Billing Attacks • Infrastructure as Code allows quick audit / linting • Focus more on: • Security groups • Permissions to resources • Rouge /shadow admins • Forgotten resources (compromises / billing)
Slide 16

Cultural Aspect ● Automation alone will not solve the problems ● Focus on collaboration and inclusive culture ● Encourage security mindset specially if it’s outside sec team ● Build allies (security champions) in company ● Avoid Blame Game This is just the tip of the iceberg (Details out of scope for this session)
Slide 17

Security Champion • Bridge between Dev, Sec and Ops teams • Build Security Champions • Single Person per team • Everyone provided with similar cross skilling opportunities • Incentivize other teams to collaborate with Sec team • Internal Bug bounties • Sponsor Interactions (Parties / get-togethers) • Sponsor cross skilling trainings for other teams
Slide 18
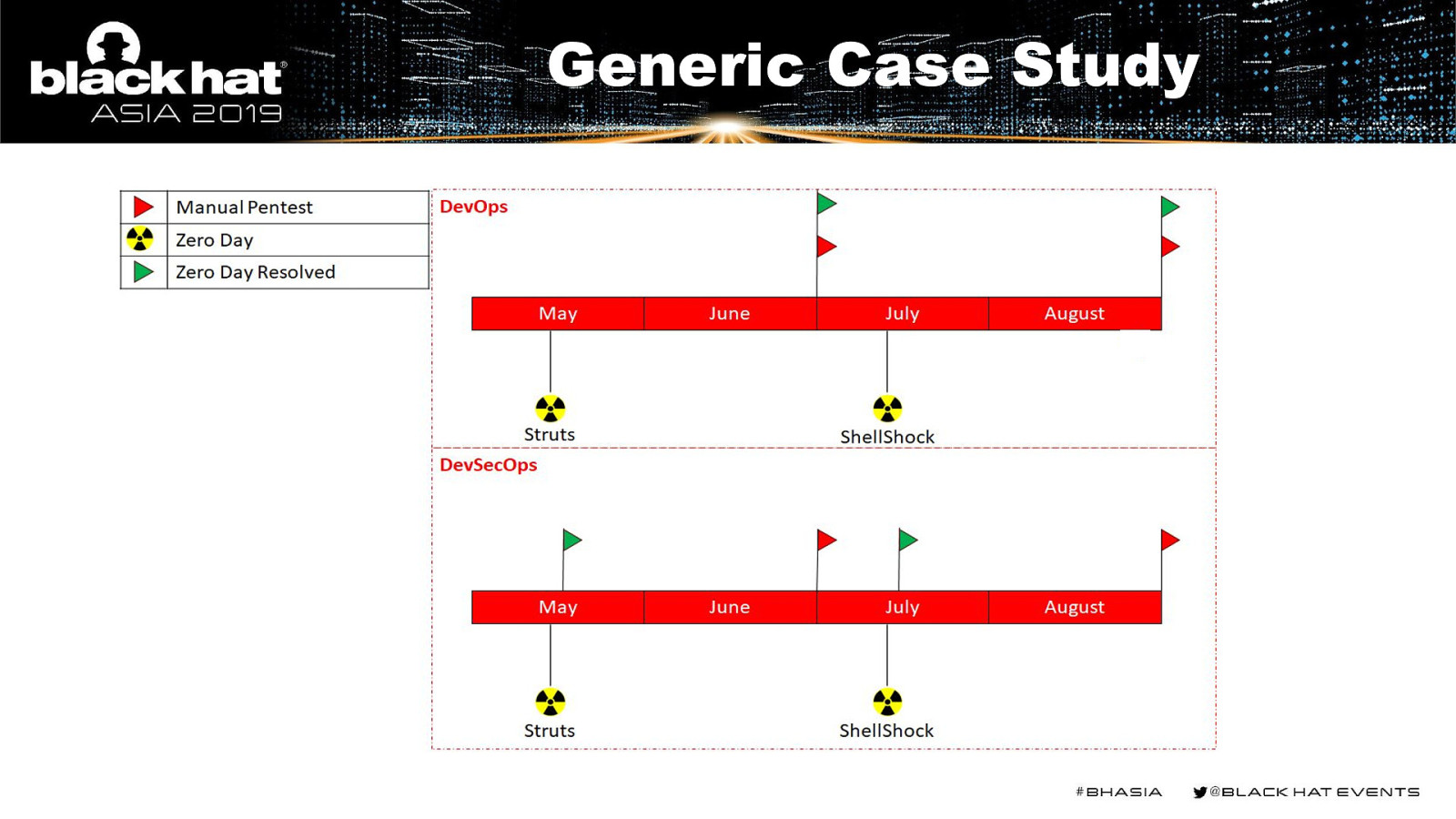
Generic Case Study
Slide 19

Case Study o nm r o t i n Un d e t n u o c c a u d an s t sse A ed Prevention: Recurring Asset Inventory and Automated Assessments
Slide 20
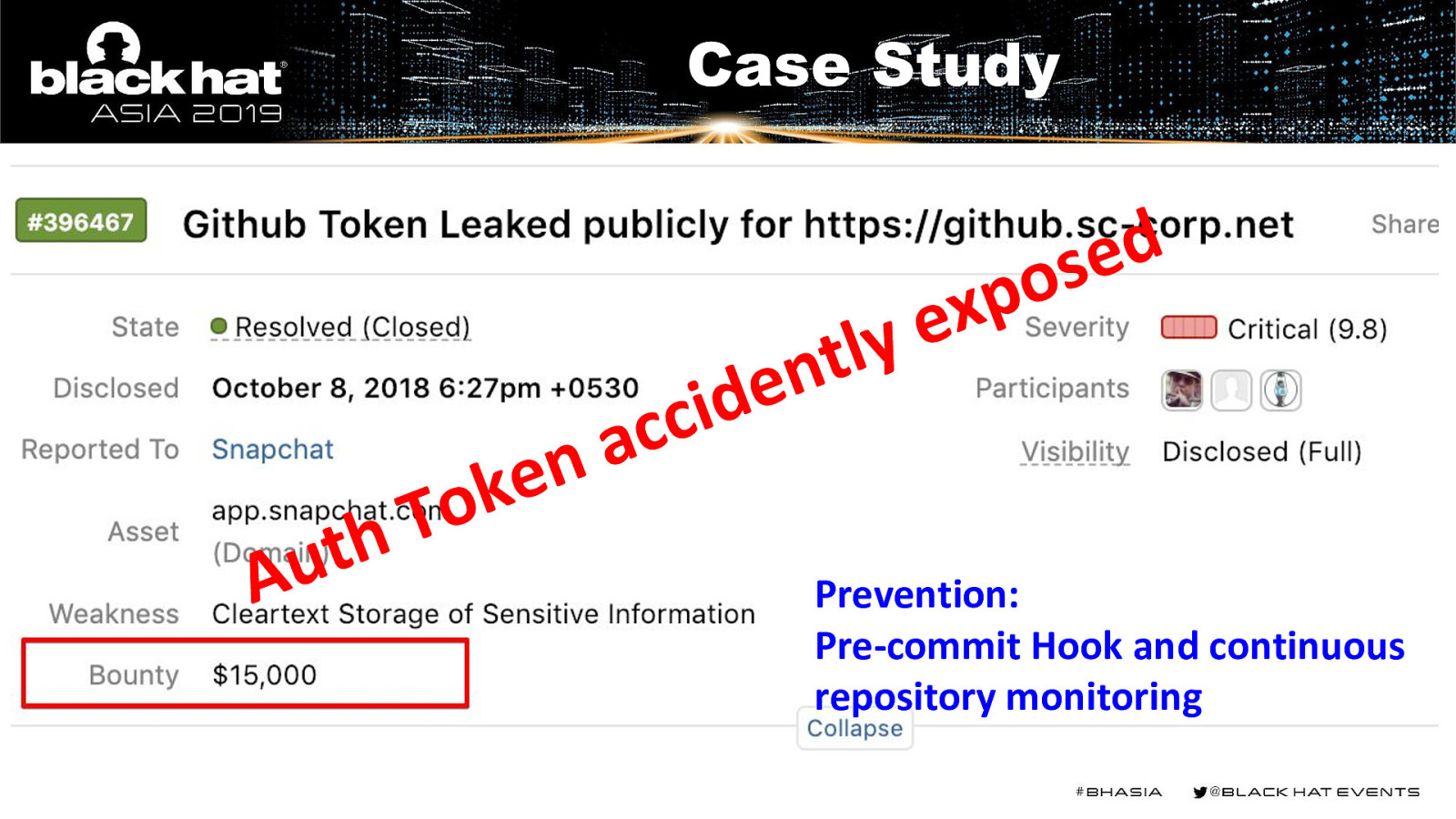
Case Study p x ye l t en Au n e k o T h t d i c ac d e os Prevention: Pre-commit Hook and continuous repository monitoring
Slide 21

More Case Studies n o i t a r s t sse u g i f n o c s i M A d u o l C Prevention: Continuous monitoring and review of cloud assets and config
Slide 22
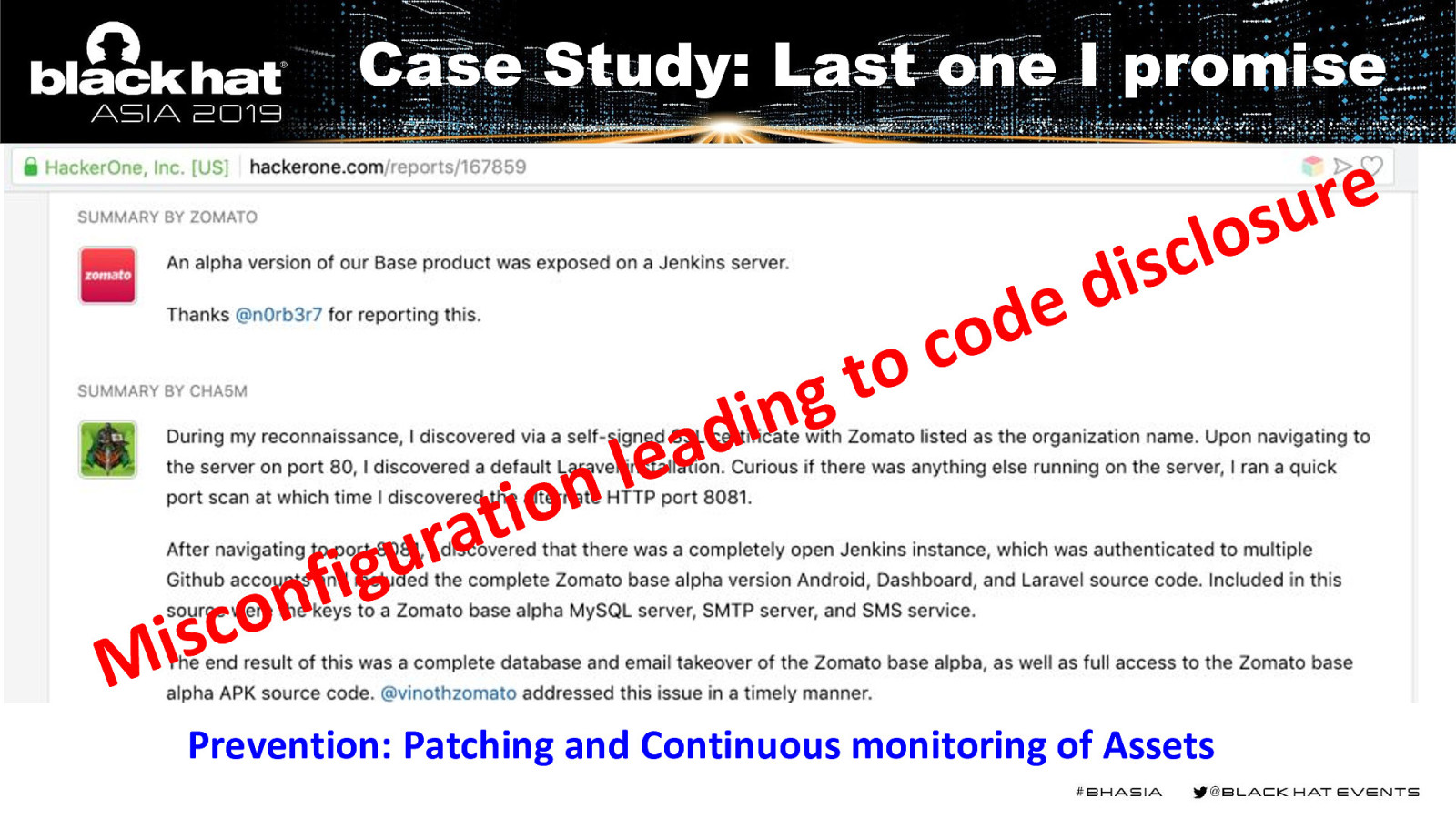
Case Study: Last one I promise n o i t a r i d lea o t ng e d co e r u s o l c s i d u g i f n o c s i M Prevention: Patching and Continuous monitoring of Assets
Slide 23
Is it Enough • Rite of passage by periodic pen test and continuous bug bounty • It’s not just important to get feedback but to also action on them • Risk Acceptance Documentation should be the worst case scenario not your first bet
Slide 24
References • https://www.blackhat.com/docs/us-17/thursday/us-17-Lackey-Practical%20 Tips-for-Defending-Web-Applications-in-the-Age-of-DevOps.pdf • https://www.sonatype.com/hubfs/2018%20State%20of%20the%20Softwar e%20Supply%20Chain%20Report.pdf • https://snyk.io/opensourcesecurity-2019/ • https://www.veracode.com/state-of-software-security-report
Slide 25

Key Takeaways • Security is everyone responsibility • Embrace security as an integral part of the process, use feedback to refine the process • DevSecOps is not a one size fit all: your mileage will vary