Mobile Top 10 2014-M2 Insecure Data Storage by Anant Shrivastava
Slide 1

Slide 2

About Me ● Anant Shrivastava ● http://anantshri.info ● Independent Information Security Consultant ● Interest Areas : Web, Mobile, Linux ● Project Lead – Android Tamer ● – Live ISO environment for Android Security. Used by multiple professionals and trainers across the globe. CodeVigilant ● A initiative to find flaws in opensource softwares. Holds 160+ responsibly disclosed web vulnerabilities at this point in time.
Slide 3

Agenda ● Understand Insecure Data Storage ● Effects on overall Security ● Examples of Insecure Data Storage ● How to Find Insecure Data Storage ● How to prevent it
Slide 4
Understand mobile Storage ● Android – /data/data/<app> ● – /sdcard/ ● ● Application specific data section, only application has access. Root has access to this partition also External memory generally FAT32 hence no ACL applies. Data can be read by all applications and externally read by card reader. IOS – <Application_Home>/Documents/ : Accessible only to app and root user. – No Sdcard for iOS devices
Slide 5
Insecure Data Storage ● ● ● It occurs when development teams assume that users or malware will not have access to a mobile device’s filesystem. And sensitive information such as PII(Personally Identifiable Information) is stored in the data-stores on the device in insecure format. Insecure format – Plain text – Reversable trivial encoding (double ROT-13 or ROT-n, base64/32/128 etc)
Slide 6

Effect of Insecure Data Storage ● This could lead to – Identity Theft – Fraud – Reputation Damage – External Policy Violation (PCI) – or Material Loss.
Slide 7
Demo Time
Slide 8
Demo’s ● Approtect ● Google Authenticator
Slide 9
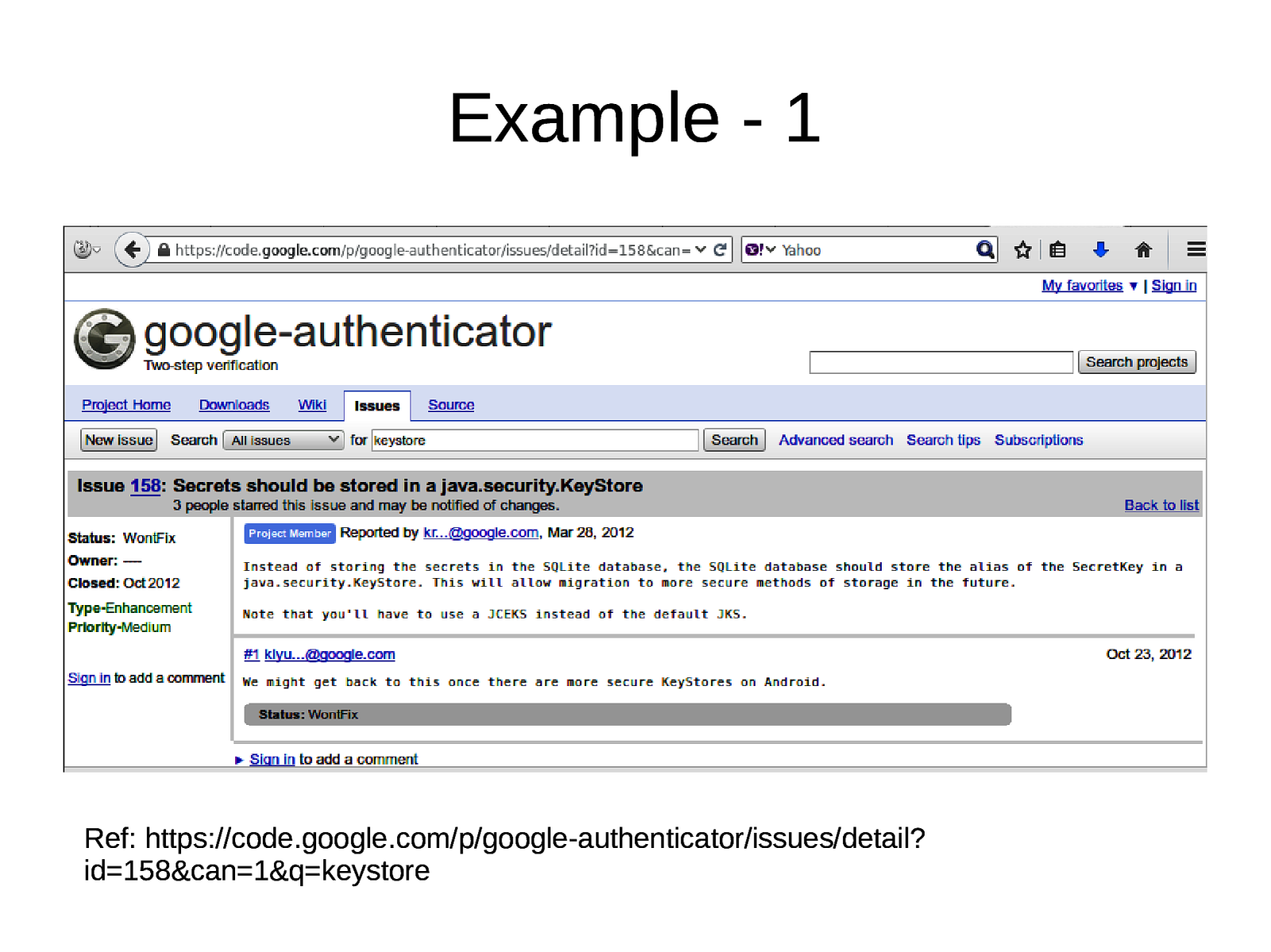
Example - 1 Ref: https://code.google.com/p/google-authenticator/issues/detail? id=158&can=1&q=keystore
Slide 10
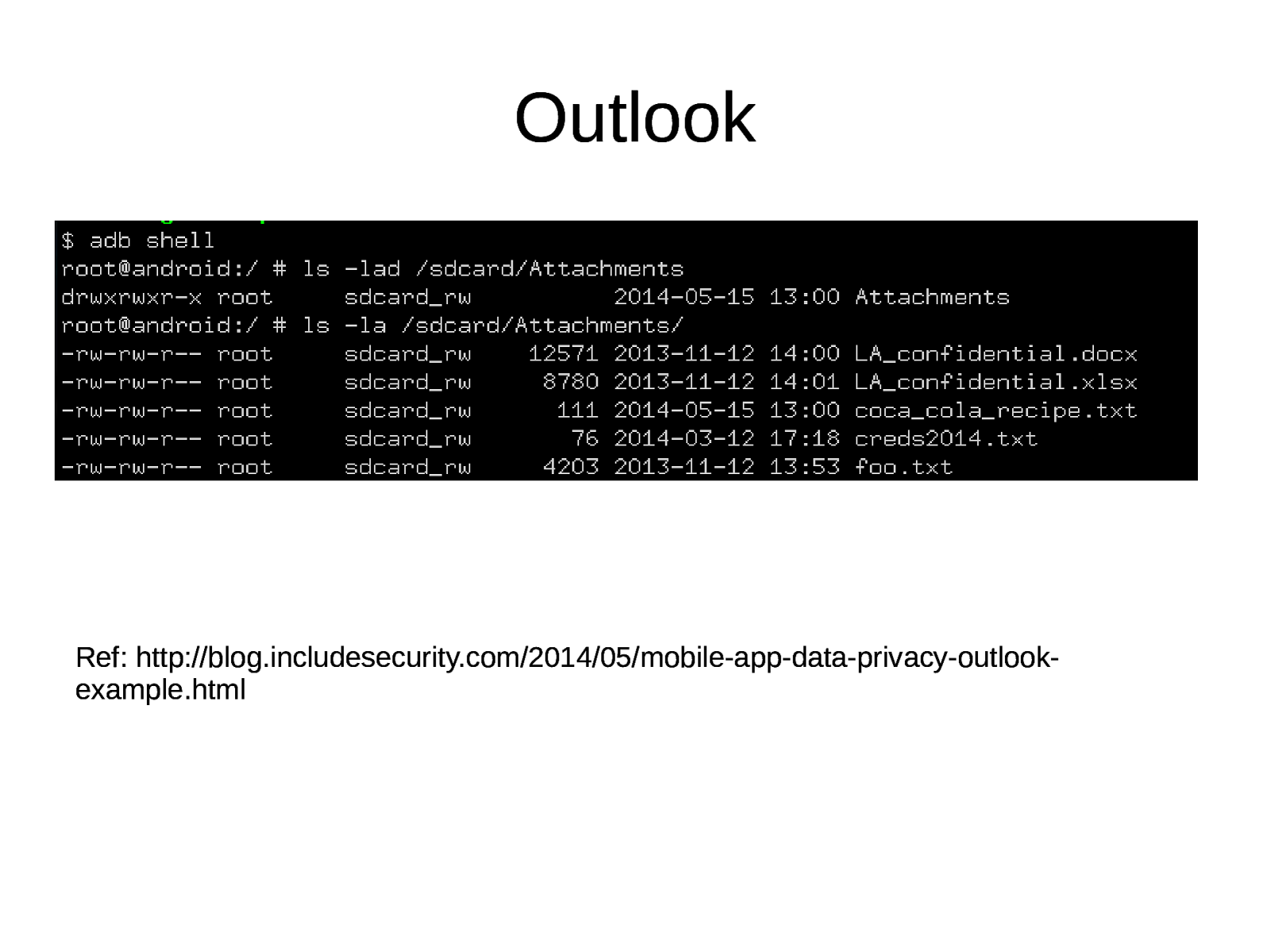
Outlook Ref: http://blog.includesecurity.com/2014/05/mobile-app-data-privacy-outlookexample.html
Slide 11
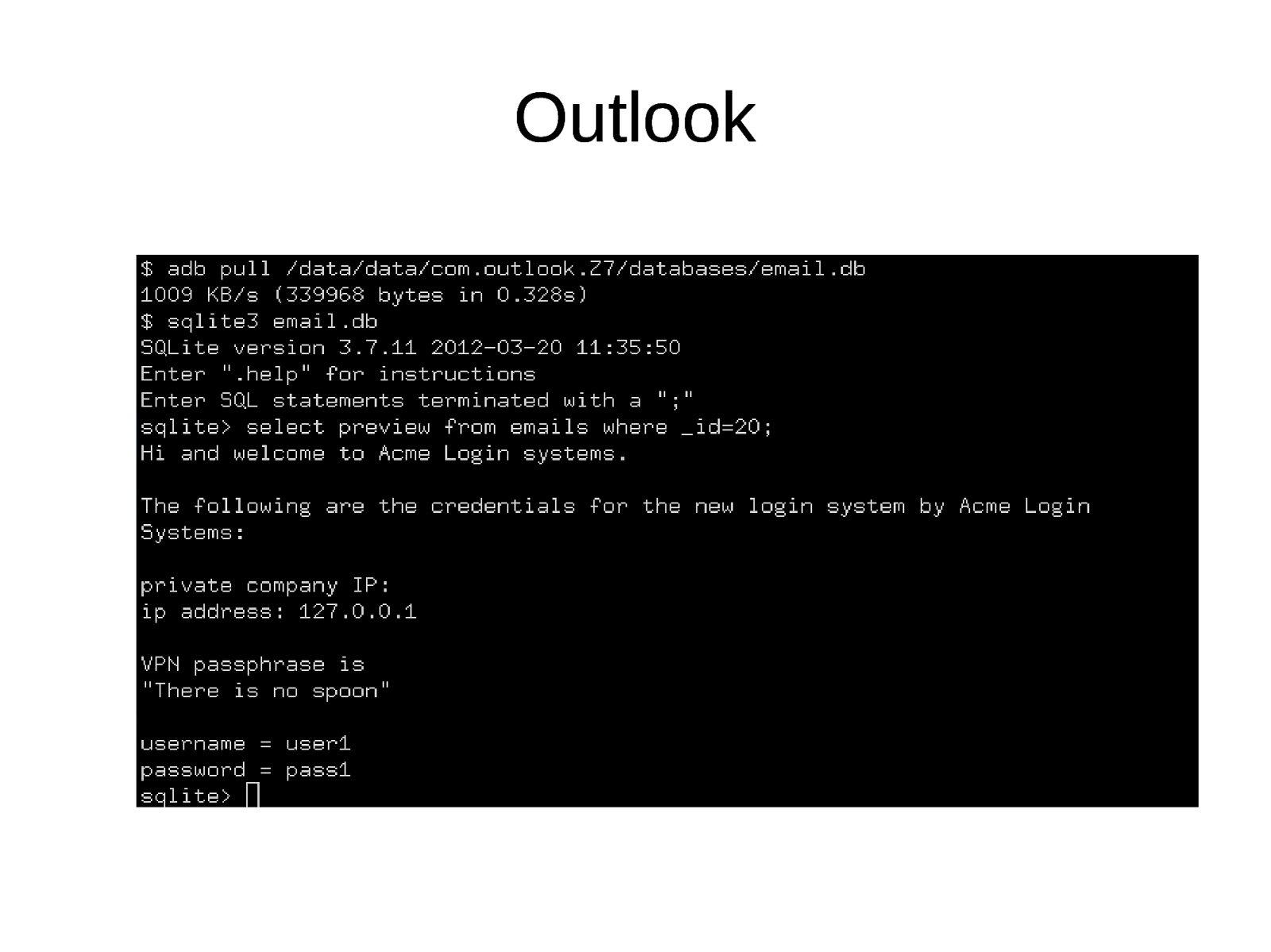
Outlook
Slide 12

How to find ● Data storage in mobile is generally in following formats – XML – Plist – SQLite – Plain text config files – Log Files – Cookies in webview
Slide 13

How to Find? Android Apps ● Install the app ● Configure and run it for some time ● Extract the /data/data/<app_name> ● ● Also before installing and after installing application observe change in /sdcard also Identify files and content
Slide 14

Mitigation ● don’t store data unless absolutely necessary ● Never store credentials on the phone file system ● ● ● Force the user to authenticate using a standard web or API login scheme (over HTTPS) to the application upon each opening and ensure session timeouts are set at the bare minimum to meet the user experience requirements. For databases consider using SQLcipher for Sqlite data encryption Be aware that all data/entities using NSManagedObects will be stored in an unencrypted database file.
Slide 15

Mitigation ● ● ● ● Ensure any shared preferences properties are NOT MODE_WORLD_READABLE unless explicitly required for information sharing between apps. Ensure SDCARD storage is not used for PII or sensitive information of any sorts Avoid using NSUserDefaults to store senstitve pieces of information Apple or android keychains can be used but once jailbroken or rooted it can be easily read.
Slide 16

References ● ● ● ● www.owasp.org/index.php/Mobile_Top_10_2014-M2 h30499.www3.hp.com/t5/Fortify-ApplicationSecurity/Exploring-The-OWASP-Mobile-Top-10-M1Insecure-Data-Storage/bap/5904609#.VAEKztYvC00 developer.android.com/training/articles/securitytips.html www.owasp.org/index.php/IOS_Developer_Cheat_S heet
Slide 17

Questions