Developers and Security My 2 paisa’s based on decade and half of my experience Anant Shrivastava Geek | Researcher
Slide 1

Slide 2
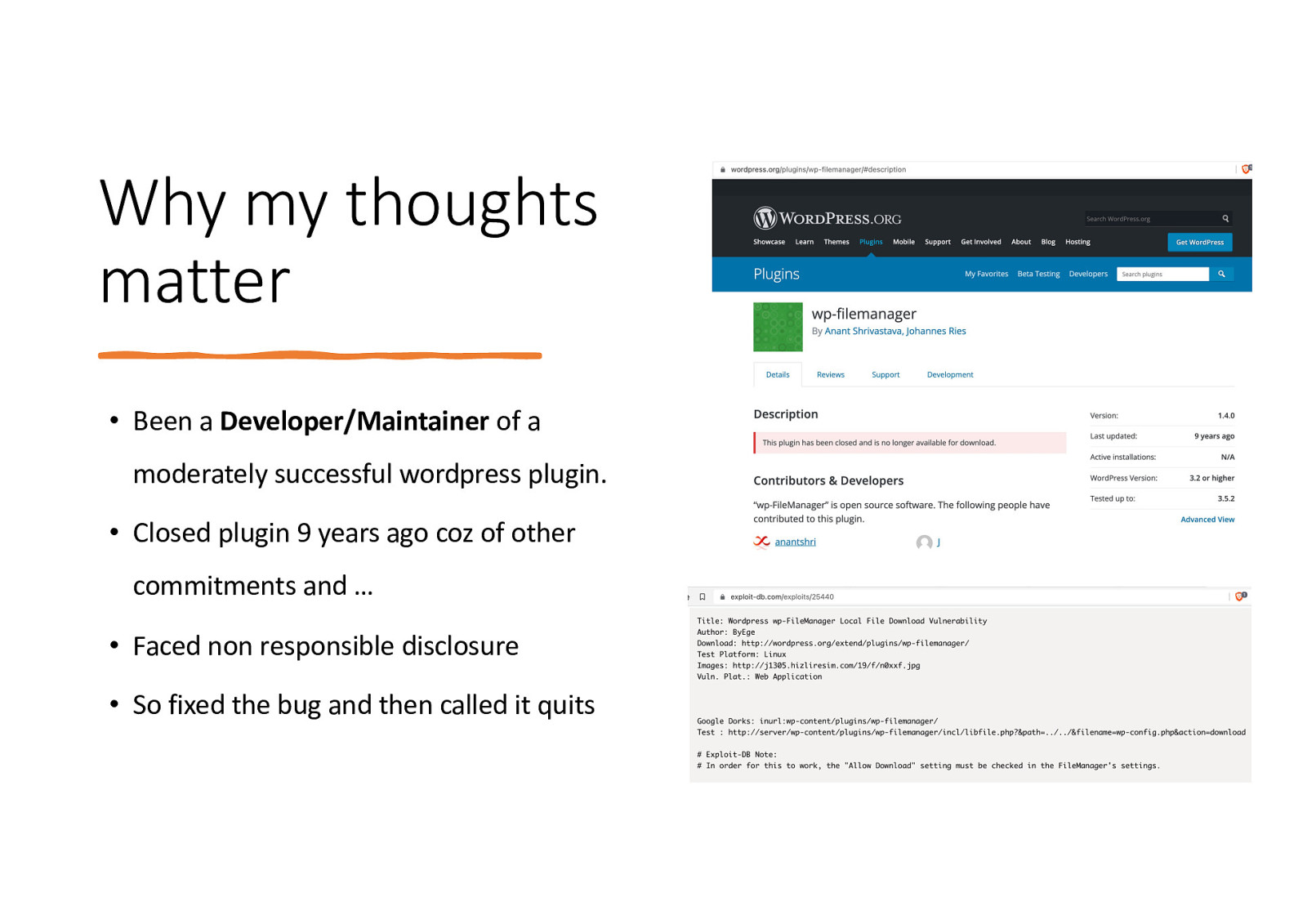
Why my thoughts matter • Been a Developer/Maintainer of a moderately successful wordpress plugin. • Closed plugin 9 years ago coz of other commitments and … • Faced non responsible disclosure • So fixed the bug and then called it quits
Slide 3
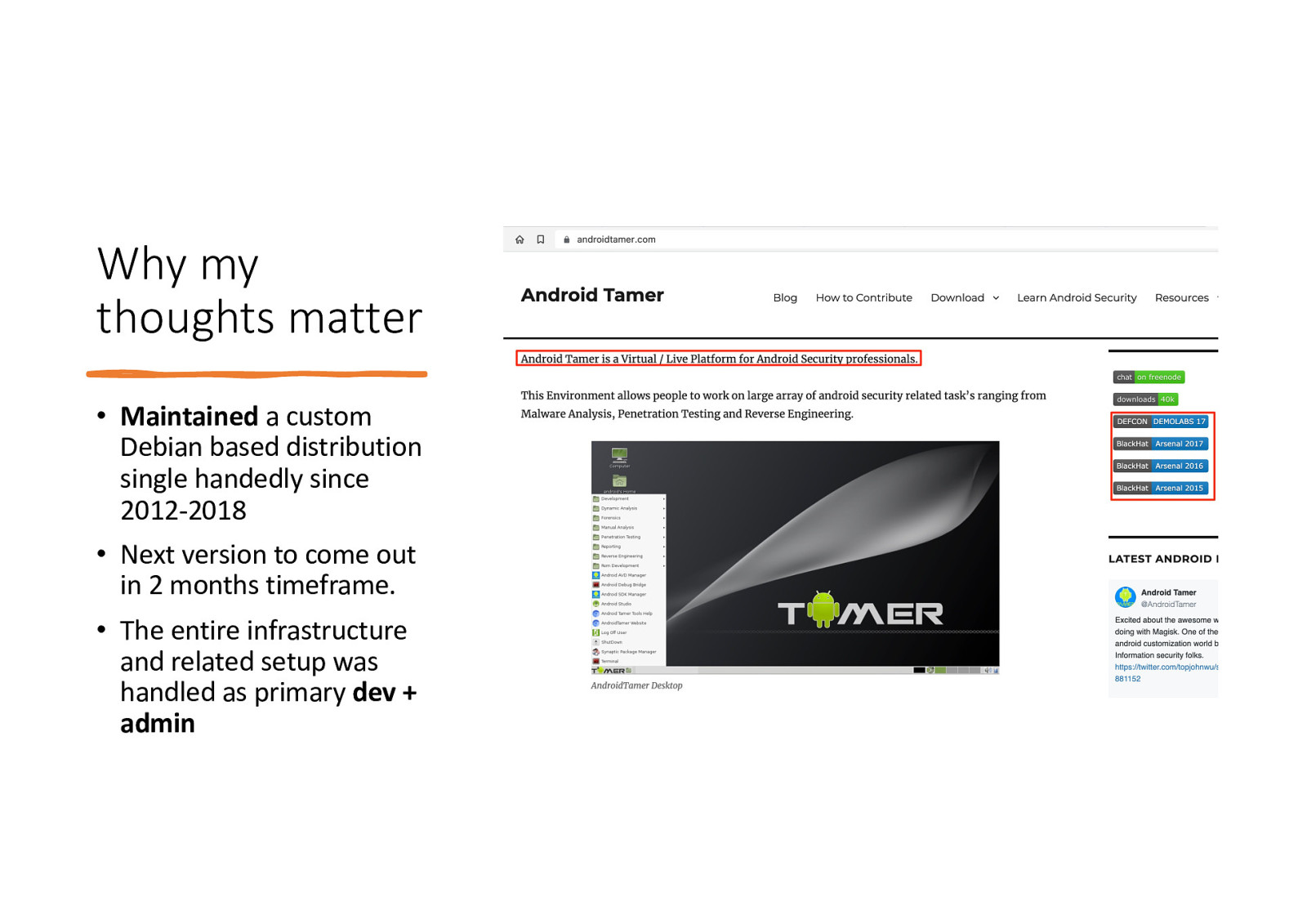
Why my thoughts matter • Maintained a custom Debian based distribution single handedly since 2012-2018 • Next version to come out in 2 months timeframe. • The entire infrastructure and related setup was handled as primary dev + admin
Slide 4
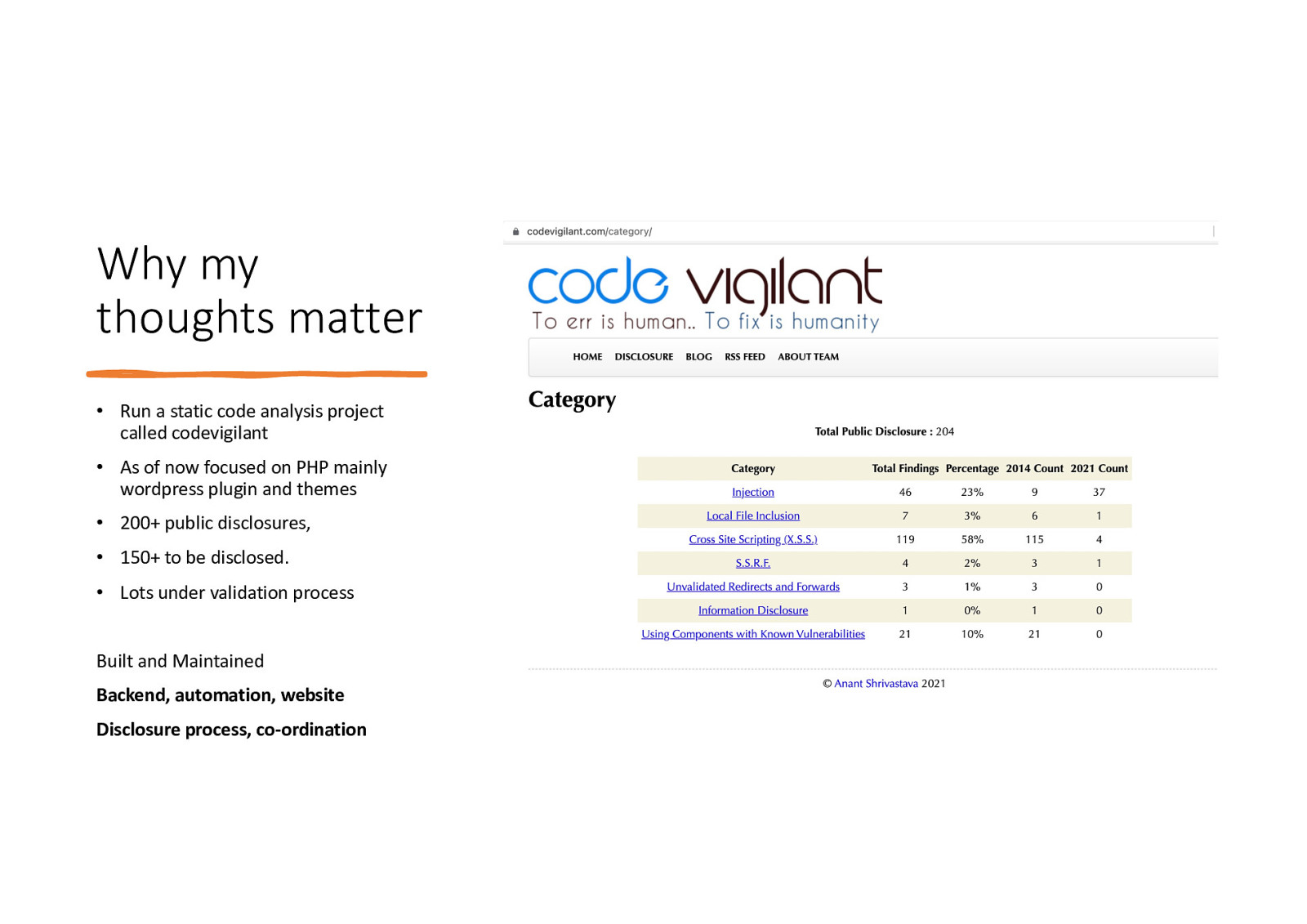
Why my thoughts matter • Run a static code analysis project called codevigilant • As of now focused on PHP mainly wordpress plugin and themes • 200+ public disclosures, • 150+ to be disclosed. • Lots under validation process Built and Maintained Backend, automation, website Disclosure process, co-ordination
Slide 5
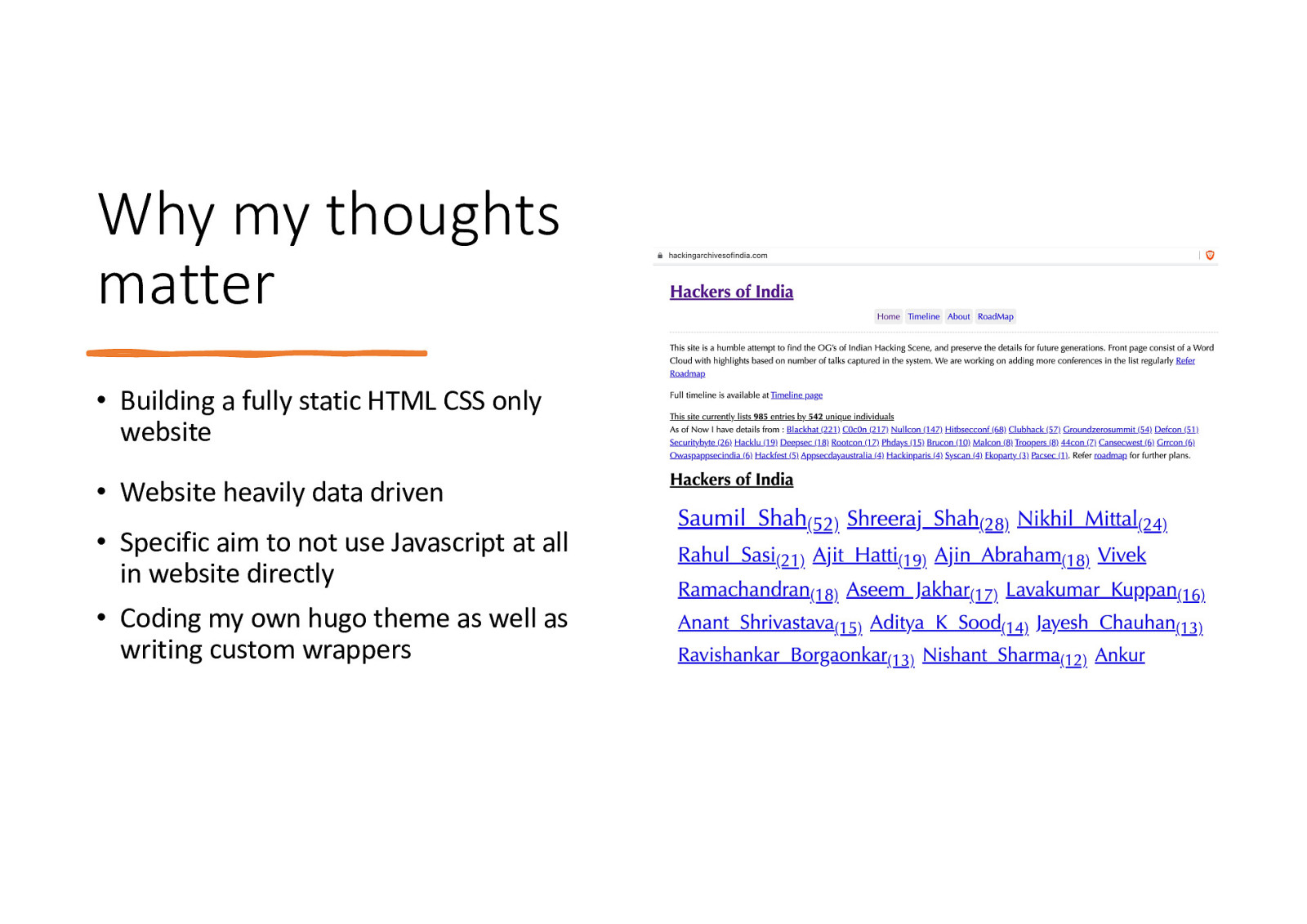
Why my thoughts matter • Building a fully static HTML CSS only website • Website heavily data driven • Specific aim to not use Javascript at all in website directly • Coding my own hugo theme as well as writing custom wrappers
Slide 6
Why my thoughts matter • Running my own collection of websites (~10+) on Wordpress self hosted since 2007 • Maintained entire offensive, defensive and operations network for an infosec company for 5+ years single handedly • Build automations and supporting various opensource projects via time, effort, money, documentation etc
Slide 7

Why my thoughts matter Worked at Spoken / Trained at
Slide 8
Developers and Security My 2 Paisa’s based on decade and half of my experience of Development / Administration / Infosec
Slide 9
Software eating the world
Slide 10
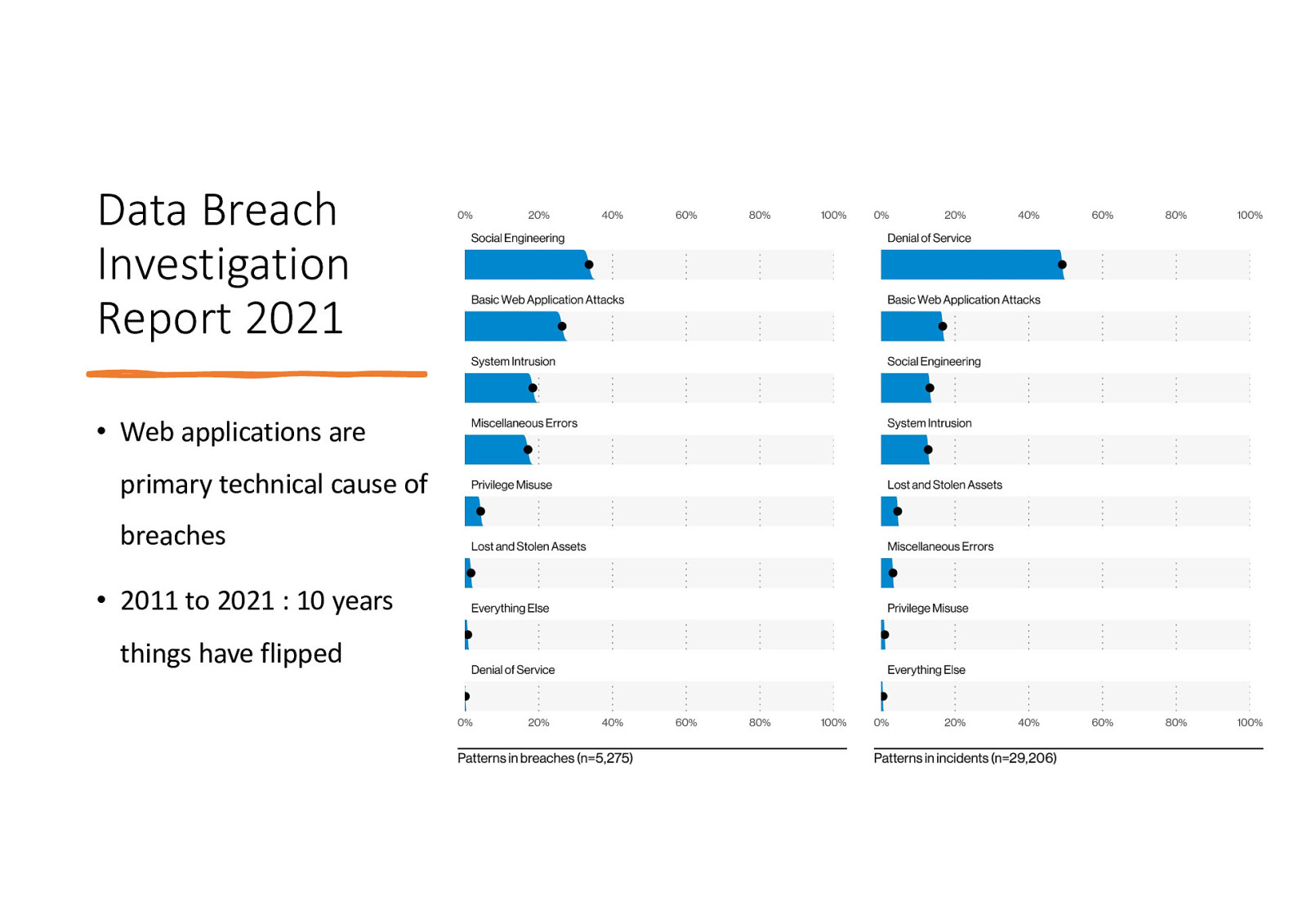
Data Breach Investigation Report 2021 • Web applications are primary technical cause of breaches • 2011 to 2021 : 10 years things have flipped
Slide 11

The mess of misunderstanding
Slide 12

How to move forward https://www.slideshare.net/notsosecure/devsecops-what-why-and-how-blackhat-2019
Slide 13

Collaboration is the key https://www.slideshare.net/anantshri/diverseccon-keynote-my-2-paisas-on-infosec-world
Slide 14

Developers have a more ingrained role to play • Security is considered an art and not a science • Security needs to be commoditized and converted to science • How do you do it • Exactly how dev’s have done this with infrastructure • From manual and long drawn process we have reached to • All codified near instantaneous infrastructure deployments
Slide 15
DevOps needs to eat security • DevSecOps as a term should not have existed but its here and people use it. • Eat security art side and make it security science • Automatable • Documented • Testable • Repeatable It may not be 100% possible but it is achievable in high 90’s
Slide 16

Developers to take full ownership • No one and I repeat no one other then dev knows code better • Leverage security team and support function: • Take inputs from them as early and as often as possible • Take final ownership of product in your hand • If security team acts as bottleneck they are doing it wrong
Slide 17
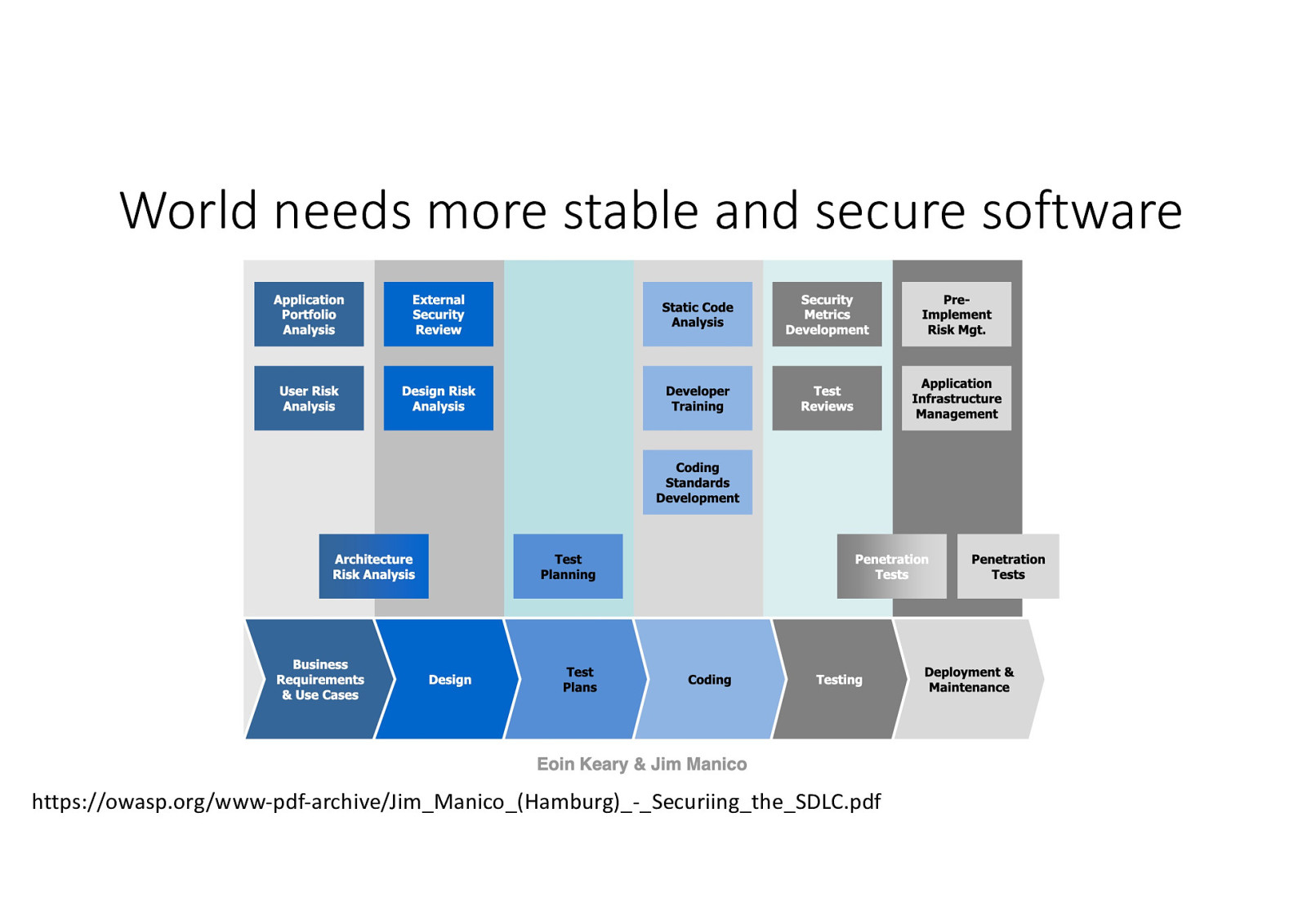
World needs more stable and secure software https://owasp.org/www-pdf-archive/Jim_Manico_(Hamburg)_-_Securiing_the_SDLC.pdf
Slide 18
Collaboration in action https://twitter.com/anantshri/status/1483031251439464448
Slide 19

Mix bag of responses • Some responses specifically asking devs to do this or that • Lots of suggestions to follow secure early or put security in early stages. • Unsurprisingly lots spooked with third party dependencies • But a common theme emerged in all these tweets especially from veterans of this field.
Slide 20
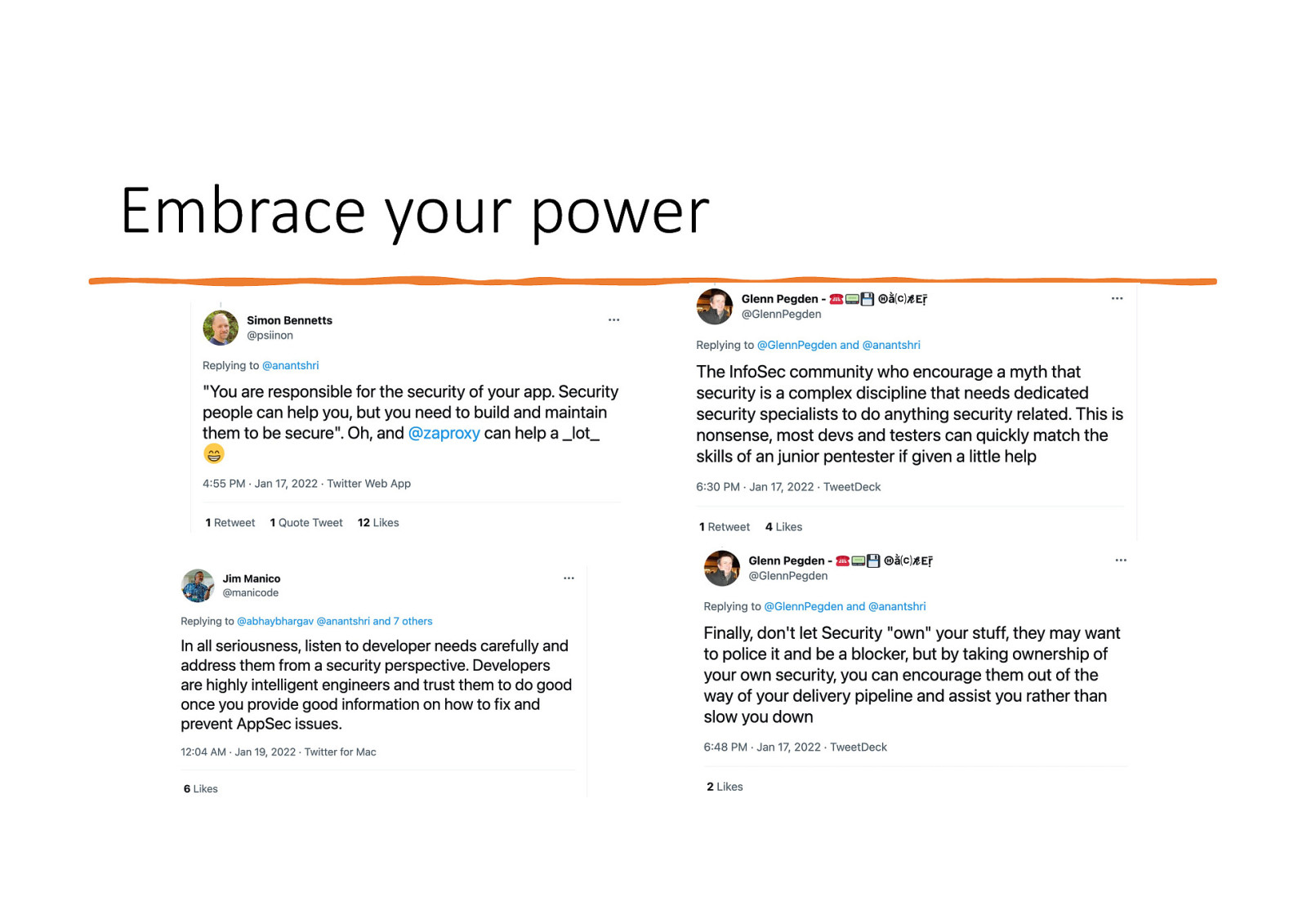
Embrace your power
Slide 21
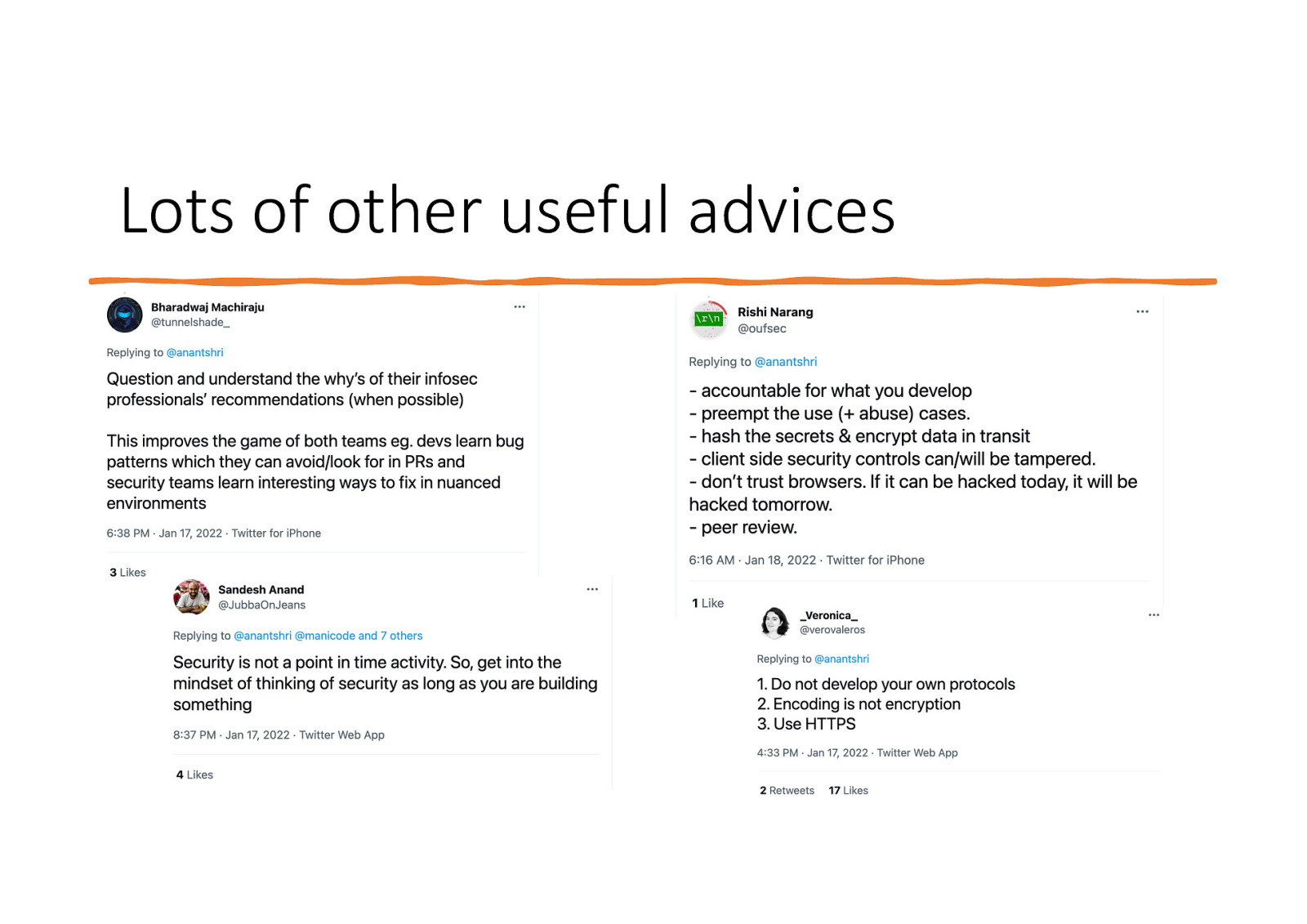
Lots of other useful advices
Slide 22
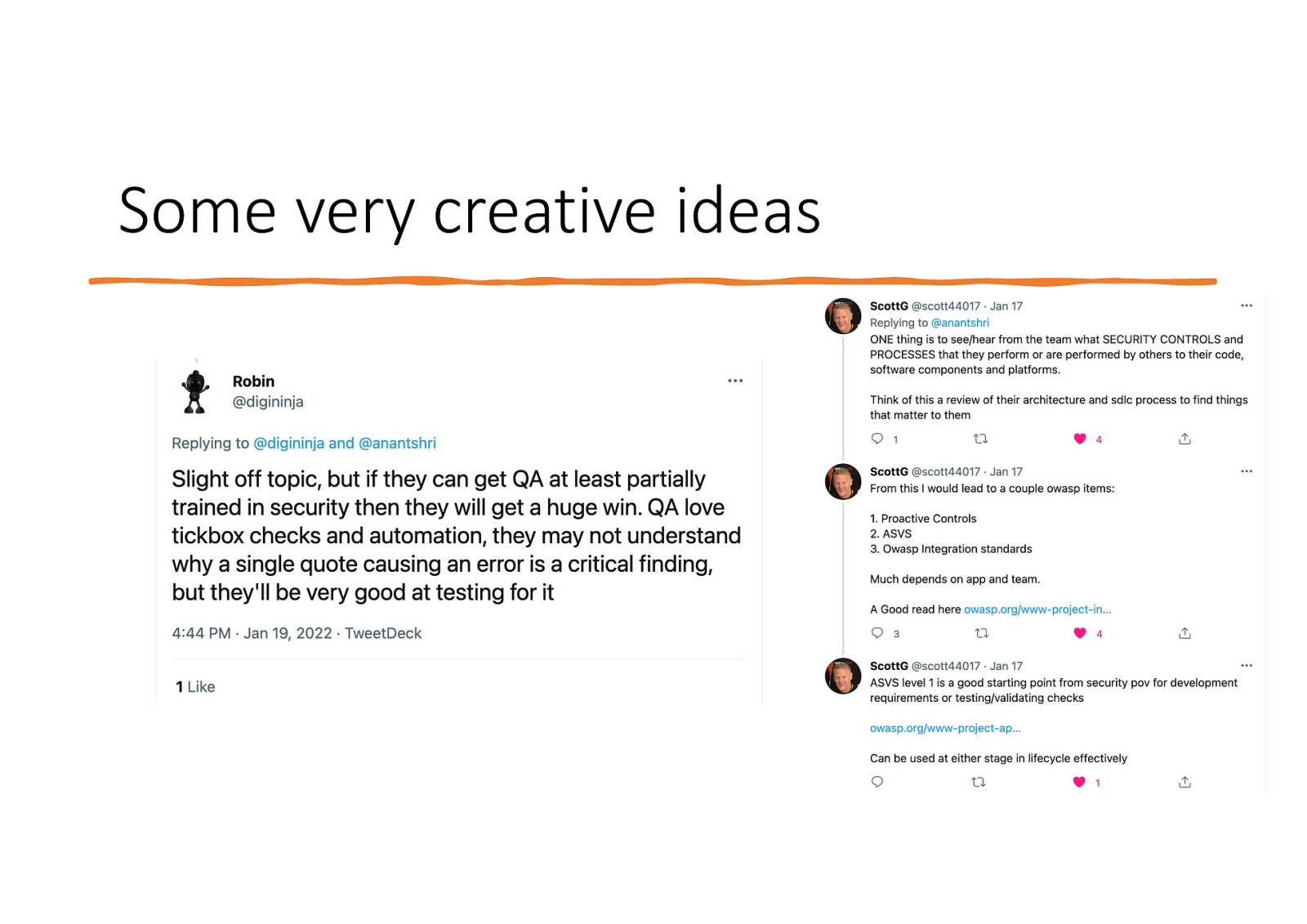
Some very creative ideas
Slide 23
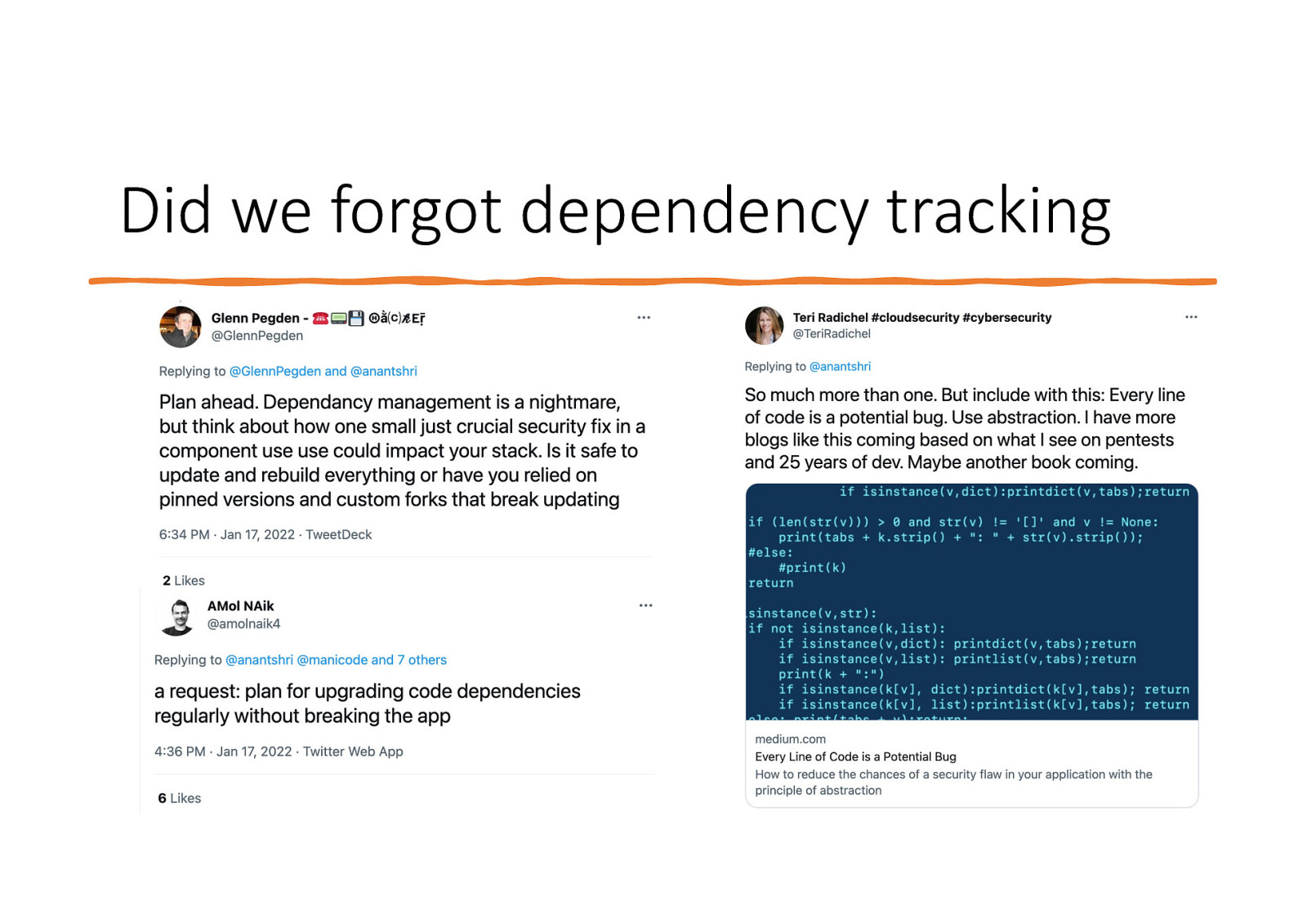
Did we forgot dependency tracking
Slide 24
Some basic ideas to kickstart the brain • Use customizable tools like semgrep • Learn how to test the vulnerabilities • Try to find bug as close to writing code as you can IDE Plugin > git commit hook > CI tool
Slide 25
Quick References • https://owasp.org/www-project-application-security-verification-standard/ • https://owasp.org/www-project-proactive-controls/ • https://owasp.org/www-project-integration-standards/ • https://owasp.org/www-project-spotlight-series/
Slide 26
Important points recap • Developers are the best judge of how the code gets changed • Security teams can help but they can’t take ownership • Pick tools that work for you and automate sec stuff
Slide 27
Thanks, and open to questions