Attacking Storage Services: Lynchpin of Cloud Services Anant Shrivastava Technical Director, NotSoSecure Global Services
Slide 1

Slide 2
Agenda How I am going to bore you for next 30 minutes • Quick Overview of Cloud Storage (so we all know what I am talking about) • Examples of real world attack scenario (coz I don’t want a demo fail) • Attack methodology that we can follow (rehash of all things cloud storage attack) • How to prevent (coz giving out gyaan is what this talk is all about) • Question and Answer (As if I have not bored you enough) Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 3

About Myself: Anant Shrivastava a.k.a Why should you listen to me • Director NotSoSecure Global Services • Sysadmin / Development / Security : all shades of IT • Project Owner: HackingArchivesofIndia, AndroidTamer, CodeVigilant • Contributor : null, G4H and many more • @anantshri on social platforms Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 4

Cloud Storage What are we going to talk about • Storage service examples are: • AWS S3 buckets • Azure Storage • GCP Storage • Digital Ocean Spaces • Sharepoint • One Drive • Dropbox • Google Drive Storage • Code commit • Code repositories: github, bitbucket Generally used for storage of objects: • Files • Documents • Source Code • Transient objects • Keys • Secrets Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 5
Why Cloud Storage Why target the storage • Cloud Storage is a Lynchpin for cloud services Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 6

Cloud Storage: Why Attack Why target the storage • Consider it like an external disk keeping data in it • A big part of cloud is able to operate as the data is decoupled from it. • Such services rely heavily on the Cloud Storage to provide the data backend. • Besides the data almost all cloud offerings need storage services for: • Platform as a Service: Source code for Application • Function as a Service: Source code for Function • Secret Storage: unbelievable number of people assume storage is good to store passwords or keys or api secrets or confidential data • to name a few…. Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 7
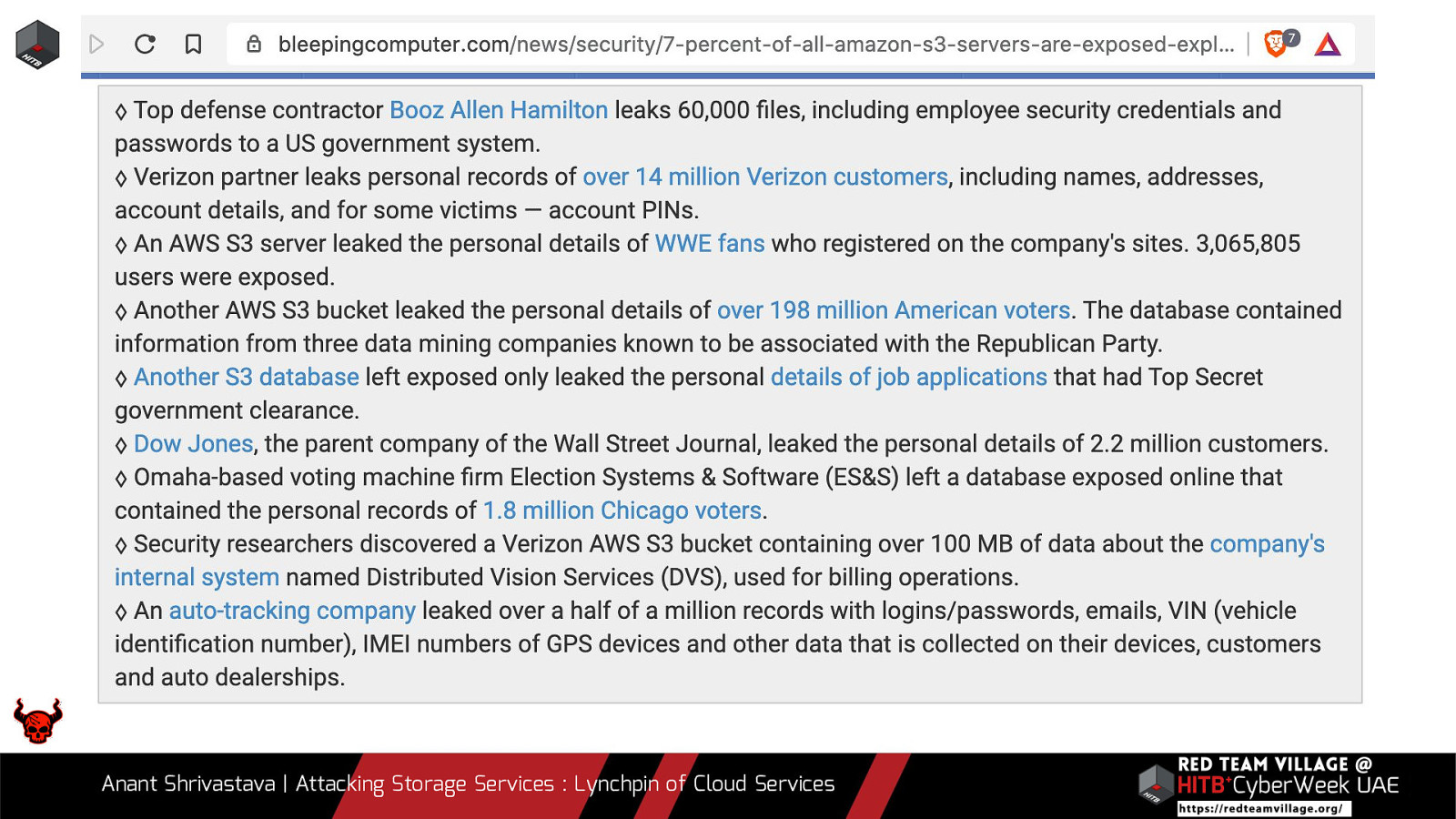
Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 8
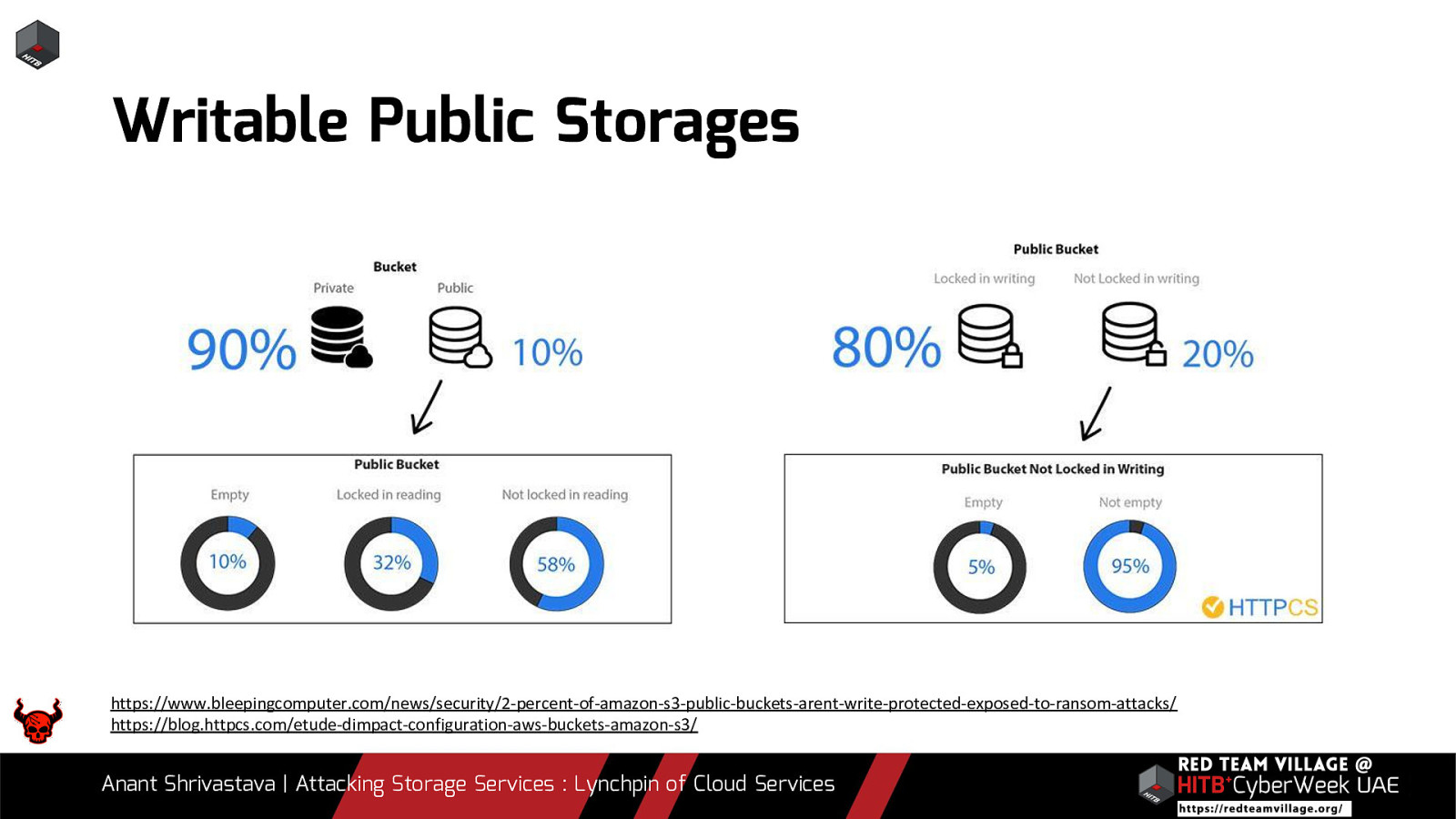
Writable Public Storages https://www.bleepingcomputer.com/news/security/2-percent-of-amazon-s3-public-buckets-arent-write-protected-exposed-to-ransom-attacks/ https://blog.httpcs.com/etude-dimpact-configuration-aws-buckets-amazon-s3/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 9

Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 10

Case Studies (best way to show impact) Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 11
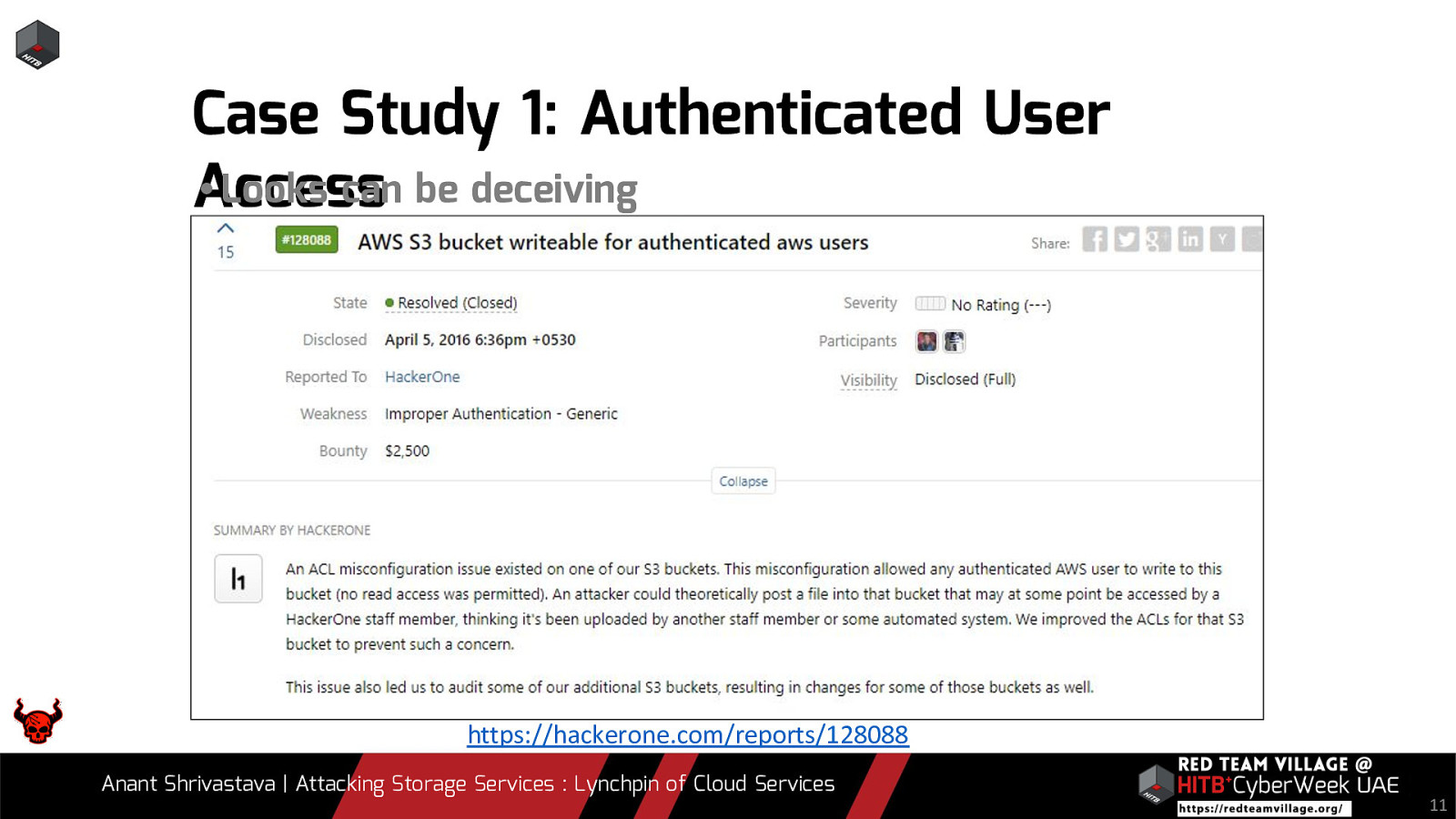
Case Study 1: Authenticated User • Looks can be deceiving Access https://hackerone.com/reports/128088 Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 11
Slide 12
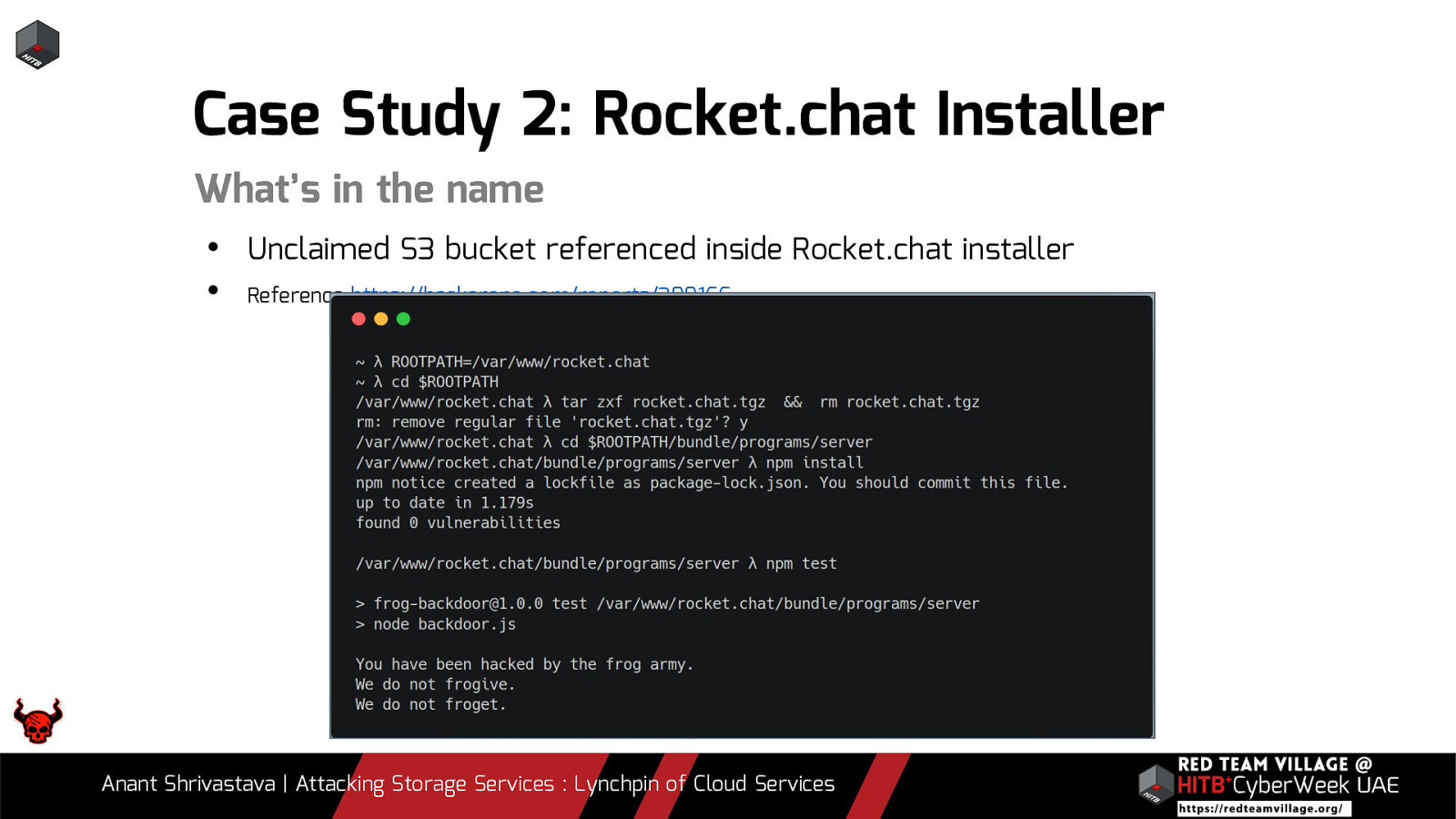
Case Study 2: Rocket.chat Installer What’s in the name • Unclaimed S3 bucket referenced inside Rocket.chat installer • Reference https://hackerone.com/reports/399166 Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 13
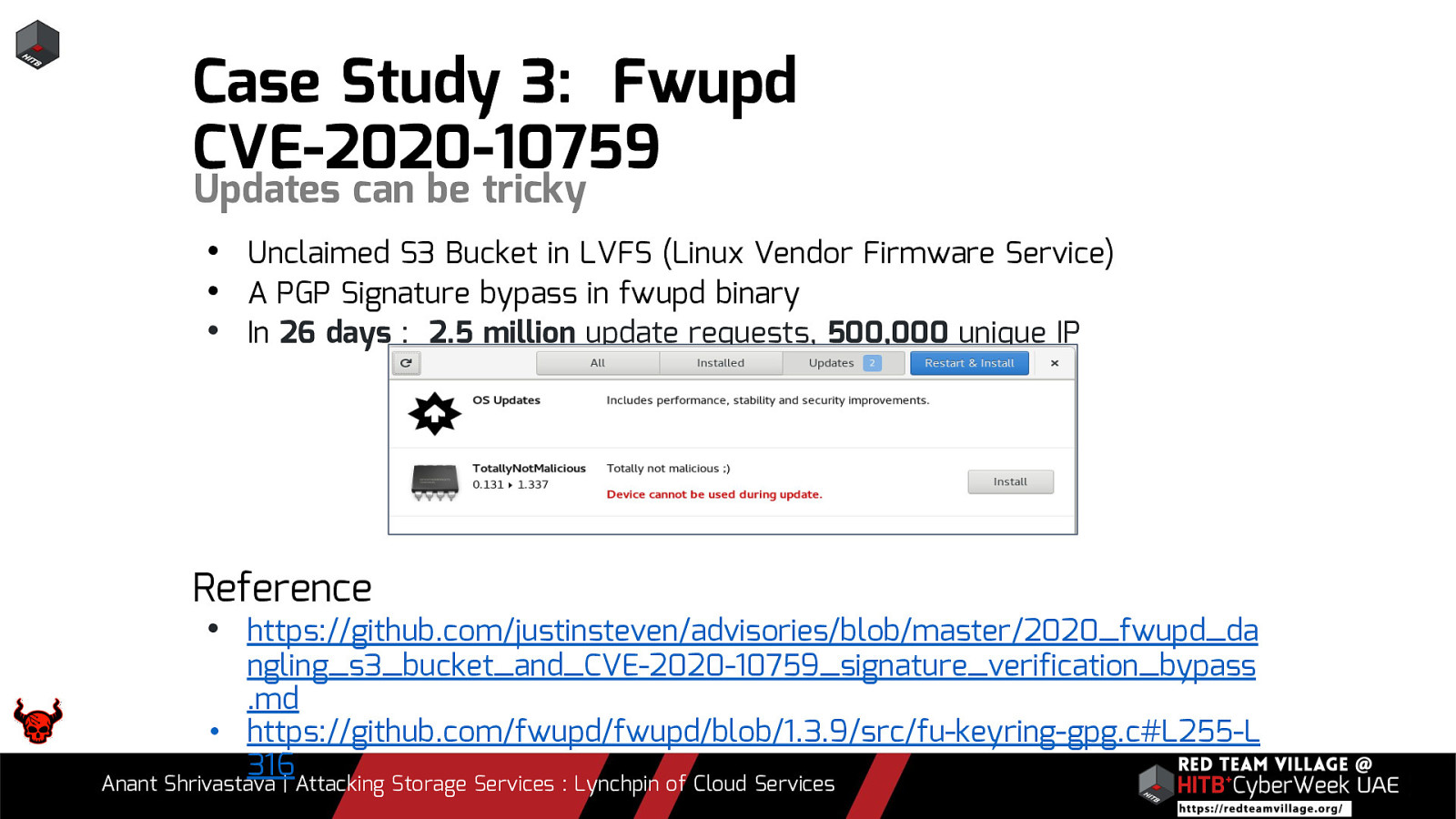
Case Study 3: Fwupd CVE-2020-10759 Updates can be tricky • Unclaimed S3 Bucket in LVFS (Linux Vendor Firmware Service) • A PGP Signature bypass in fwupd binary • In 26 days : 2.5 million update requests, 500,000 unique IP Reference • https://github.com/justinsteven/advisories/blob/master/2020_fwupd_da ngling_s3_bucket_and_CVE-2020-10759_signature_verification_bypass .md • https://github.com/fwupd/fwupd/blob/1.3.9/src/fu-keyring-gpg.c#L255-L 316 Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 14

Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 15
Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 16

Attacking Cloud Storage : Methodology a.k.a Why more then half of you are here • In all the case studies storage played an important part • So now we have established that storage attacks can be catastrophic • Methodology we will follow 1. 2. 3. 4. 5. Enumerate and Gather information Identify vulnerabilities Exploit vulnerabilities Post exploitation and pivoting Circle back to step 1 Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 17
Attack: Enumeration • Lets hunt in the dark • Storage names are unique in the whole of service provider • A lot of the are predictable for an organization • Storages are hosted solutions hence port scanning is out of door • Enumerate / bruteforce various possible bucket name • No point listing all tools of trade as they keep on changing Folks @ Redhuntlabs are maintaining this list: https://github.com/redhuntlabs/Awesome-Asset-Discovery#cloud-infrastruct ure-discovery https://github.com/redhuntlabs/Awesome-Asset-Discovery#domain—subdom ain-discovery Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 18
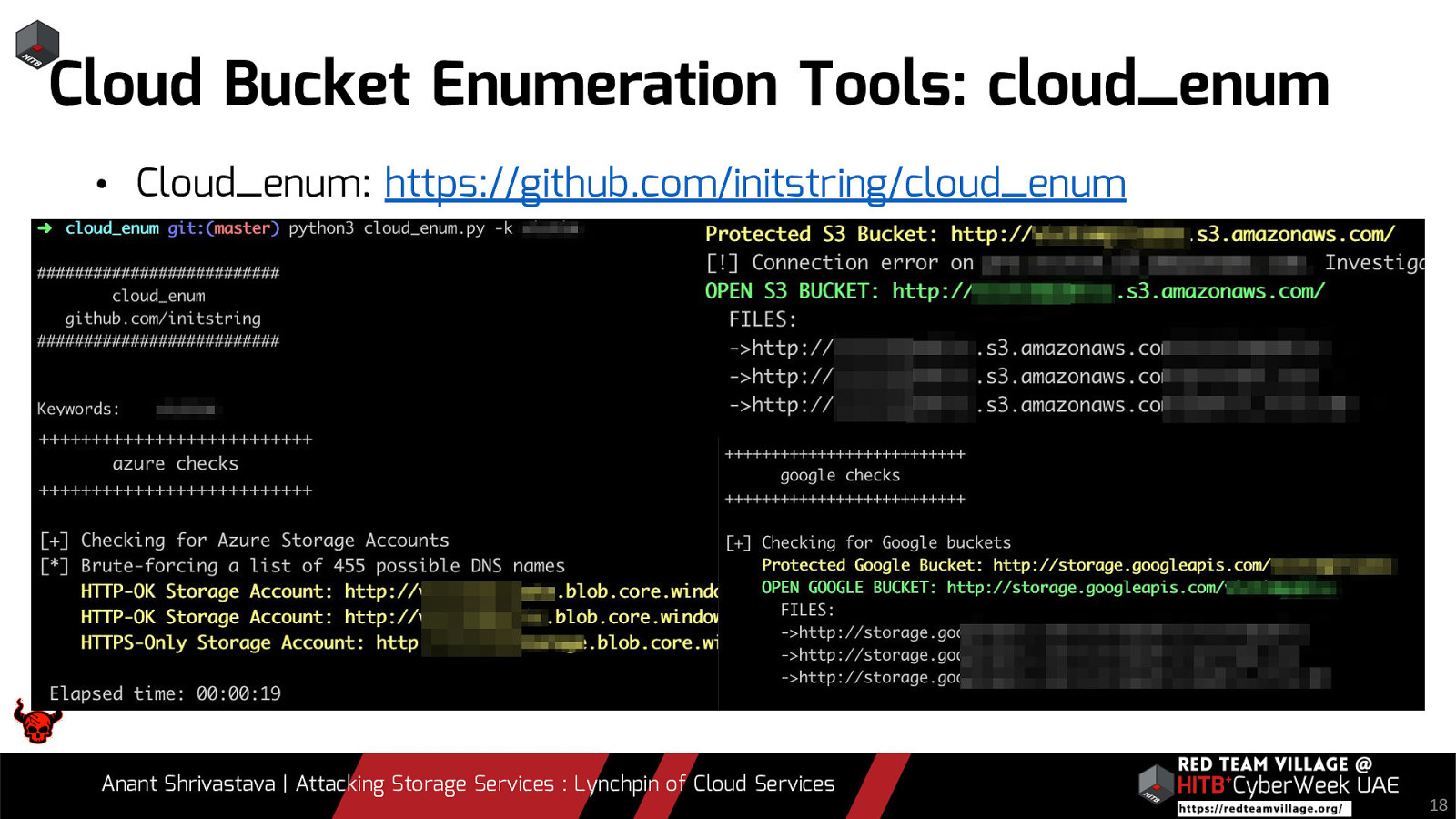
Cloud Bucket Enumeration Tools: cloud_enum • Cloud_enum: https://github.com/initstring/cloud_enum Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 18
Slide 19
AWS Storage buckets • Access AWS buckets – – • https://s3.amazonaws.com/bucket_name https://<bucketname>.s3.amazonaws.com Bucket Enumeration possible via difference in error messages https://s3.amazonaws.com/bucket_name/ • For REST style URL we now need region tagged https://s3.<region>.amazonaws.com/<bucket_name>/ Identifying region of Bucket • Request to any random region url will reveal correct URL https://s3.<anyregion>.amazonaws.com/bucket_name Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 19
Slide 20
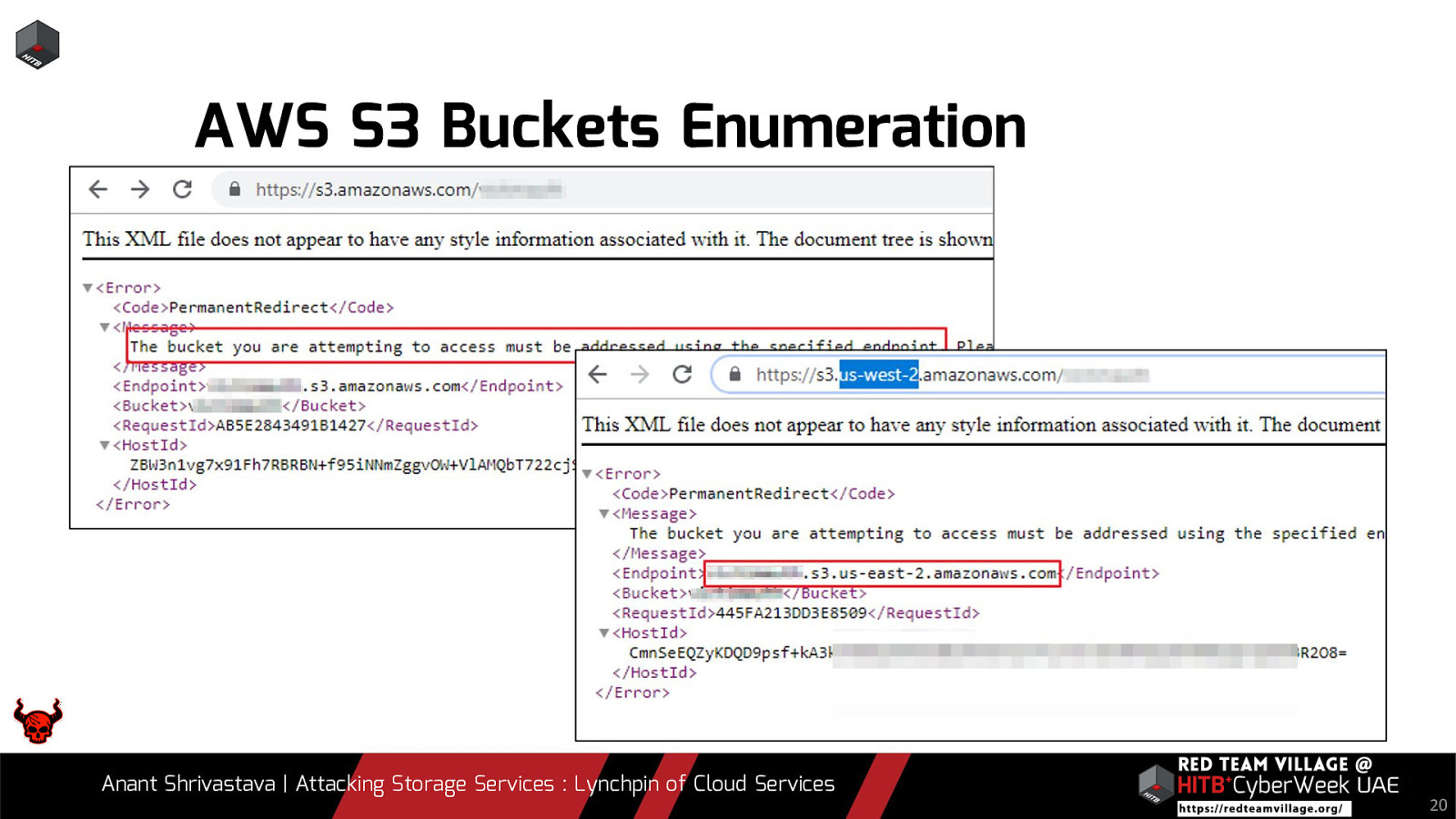
AWS S3 Buckets Enumeration Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 20
Slide 21
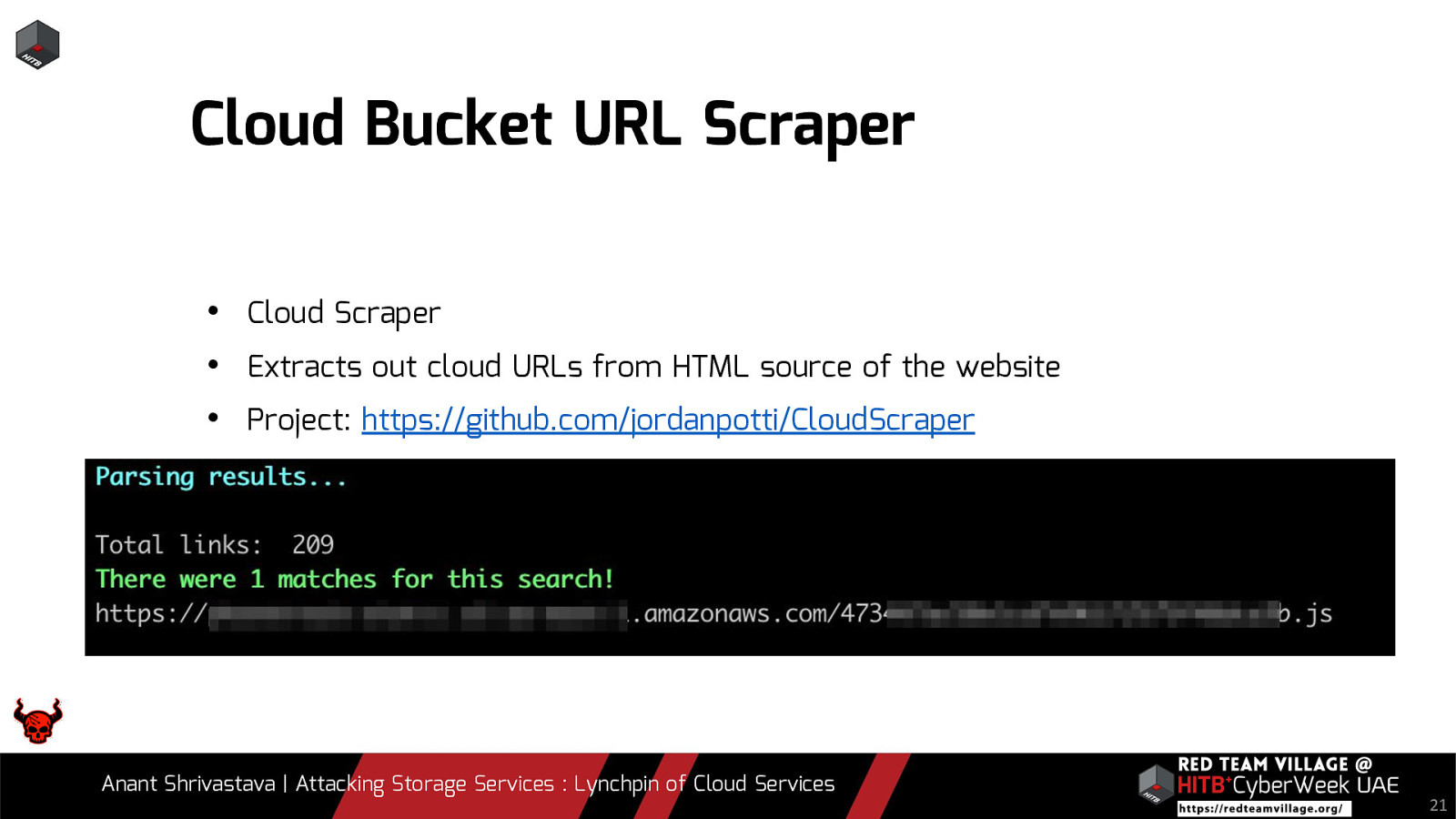
Cloud Bucket URL Scraper • Cloud Scraper • Extracts out cloud URLs from HTML source of the website • Project: https://github.com/jordanpotti/CloudScraper Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 21
Slide 22
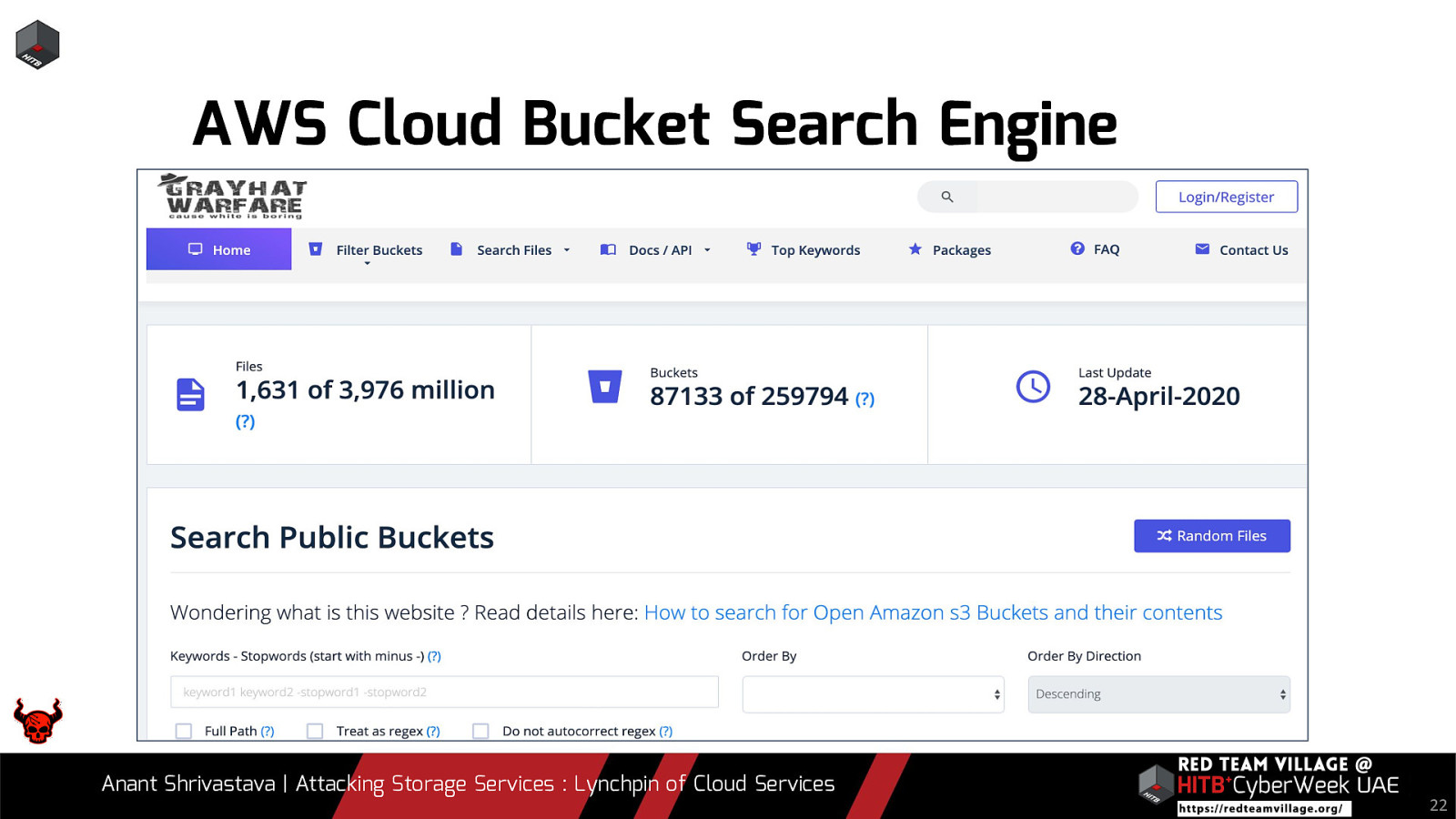
AWS Cloud Bucket Search Engine Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 22
Slide 23
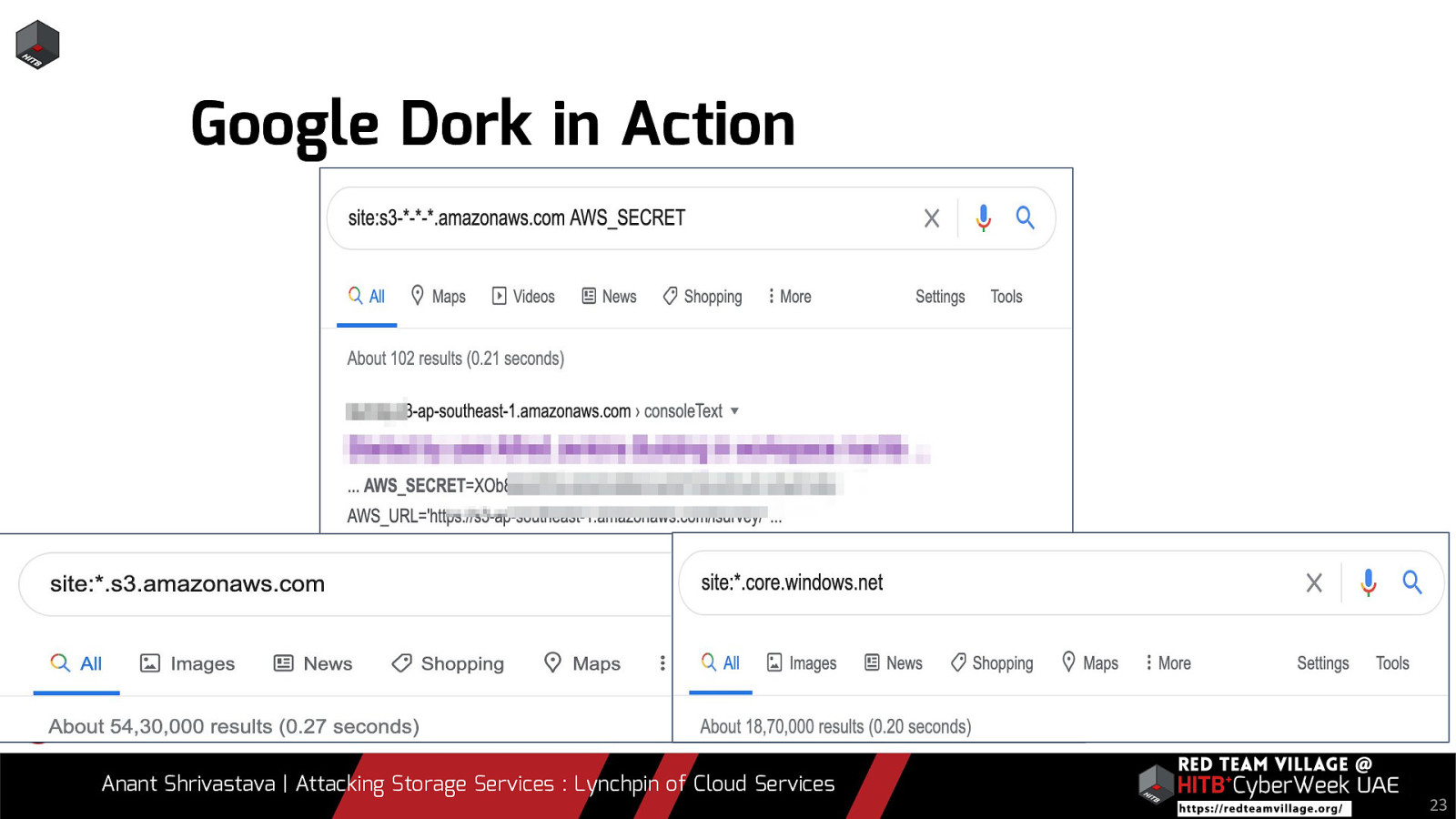
Google Dork in Action Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 23
Slide 24

Attack: Identification and Exploitation Primary Focus on permissions: • • • • Anonymous access granted on bucket Misconfigured write access for a resource Restricted to auth user (any authenticated user) Lax IAM Rules/Policies giving access to data Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 25
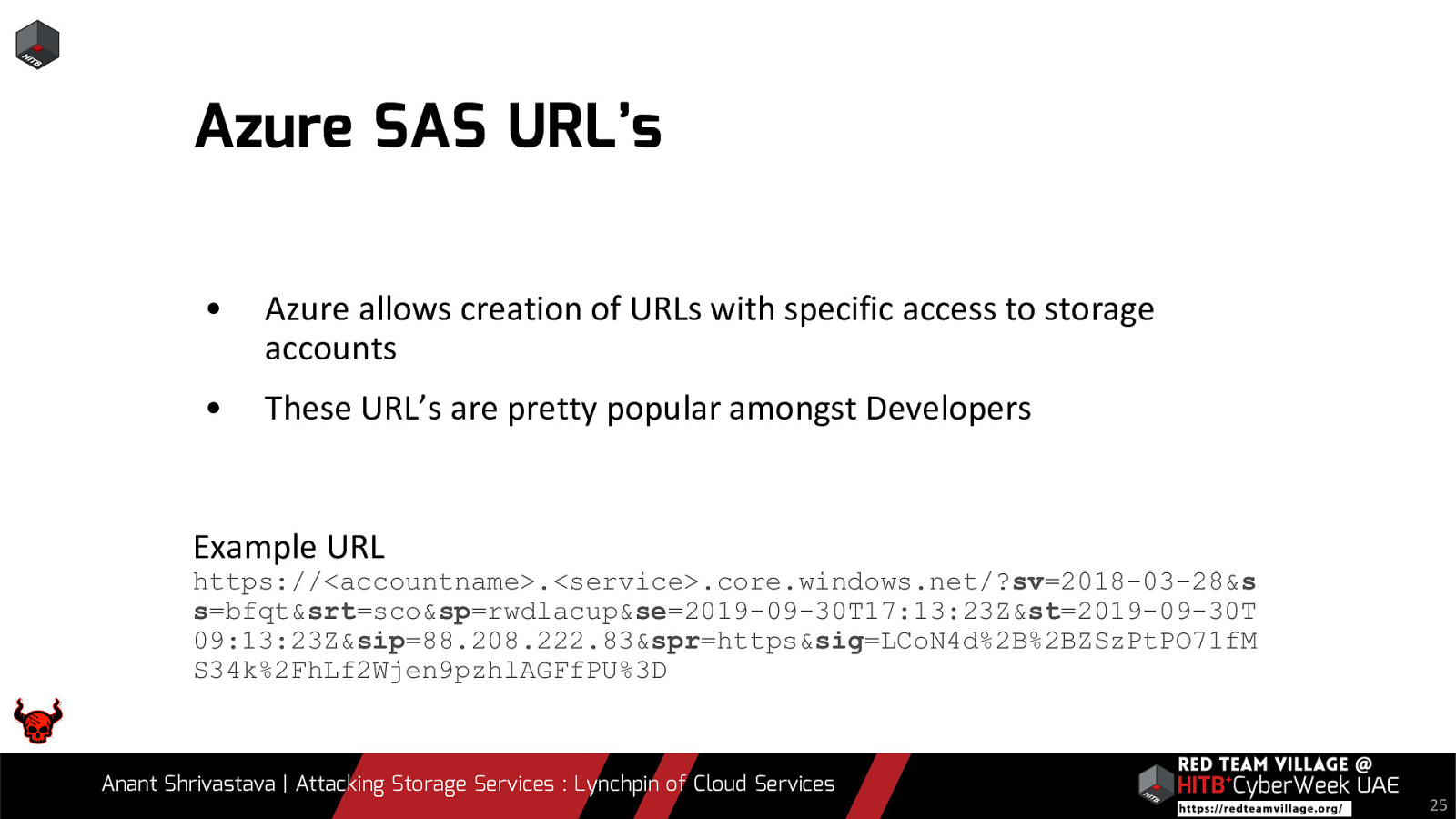
Azure SAS URL’s • Azure allows creation of URLs with specific access to storage accounts • These URL’s are pretty popular amongst Developers Example URL https://<accountname>.<service>.core.windows.net/?sv=2018-03-28&s s=bfqt&srt=sco&sp=rwdlacup&se=2019-09-30T17:13:23Z&st=2019-09-30T 09:13:23Z&sip=88.208.222.83&spr=https&sig=LCoN4d%2B%2BZSzPtPO71fM S34k%2FhLf2Wjen9pzhlAGFfPU%3D Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 25
Slide 26
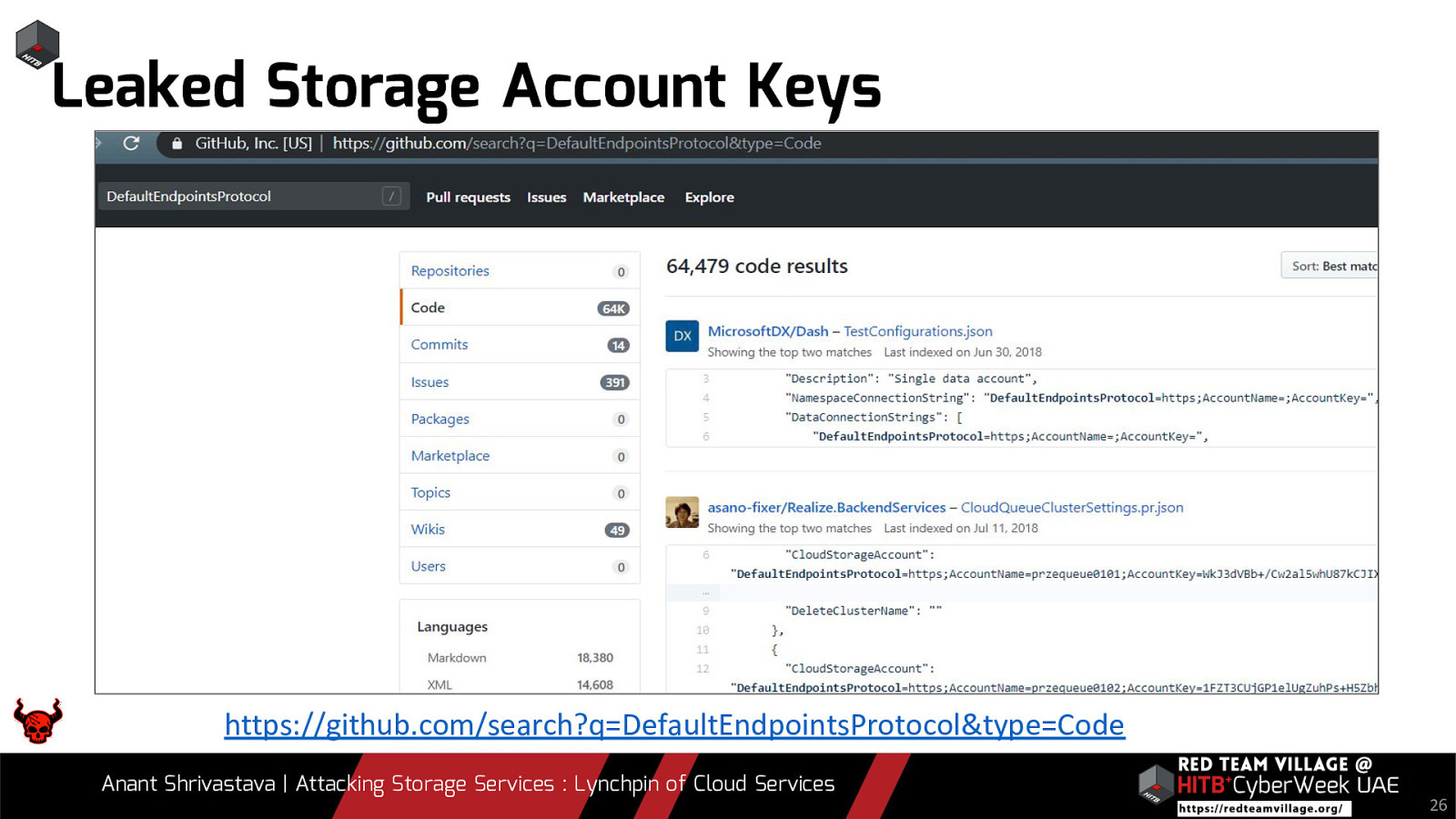
Leaked Storage Account Keys https://github.com/search?q=DefaultEndpointsProtocol&type=Code Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 26
Slide 27
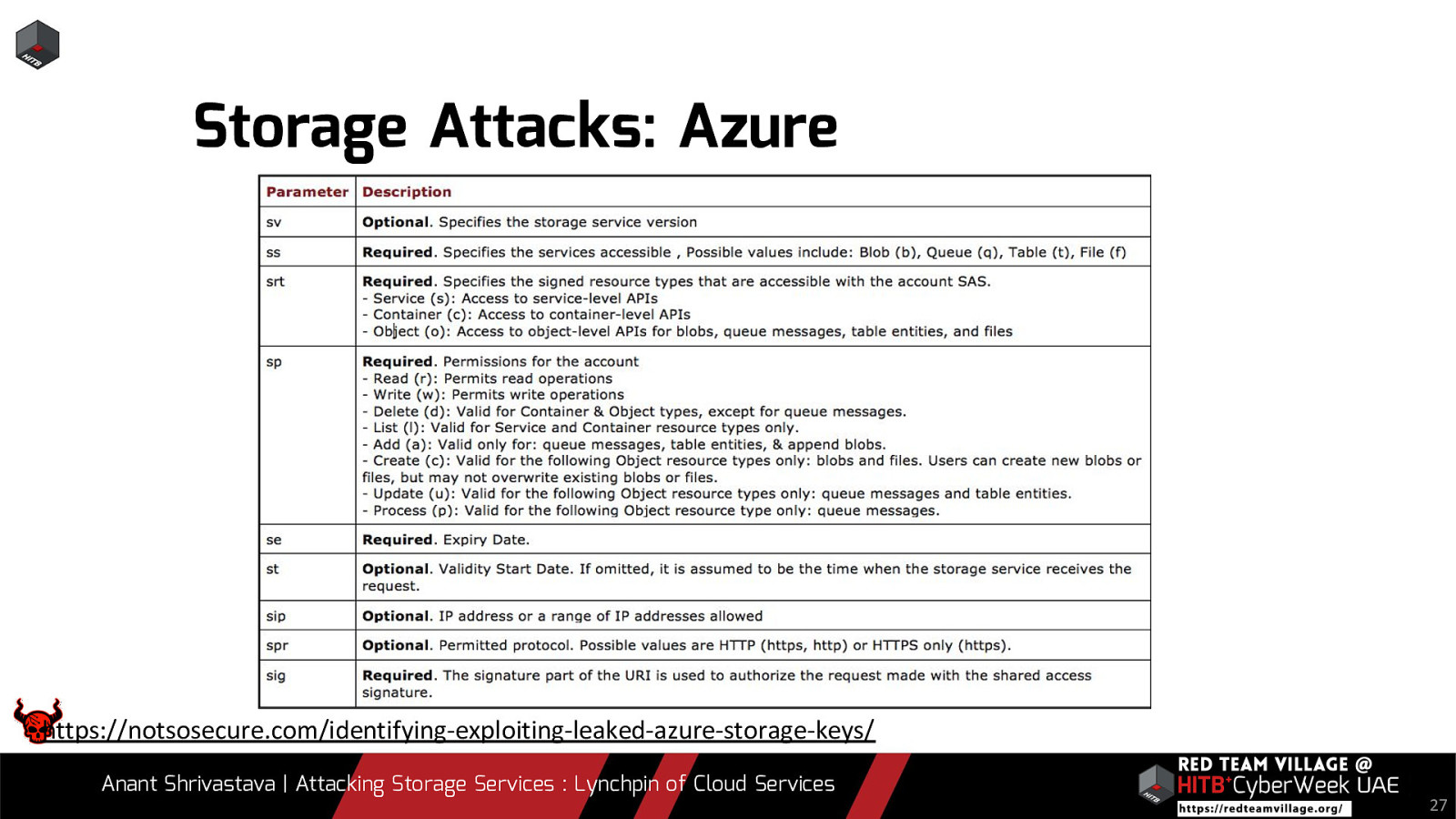
Storage Attacks: Azure https://notsosecure.com/identifying-exploiting-leaked-azure-storage-keys/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 27
Slide 28
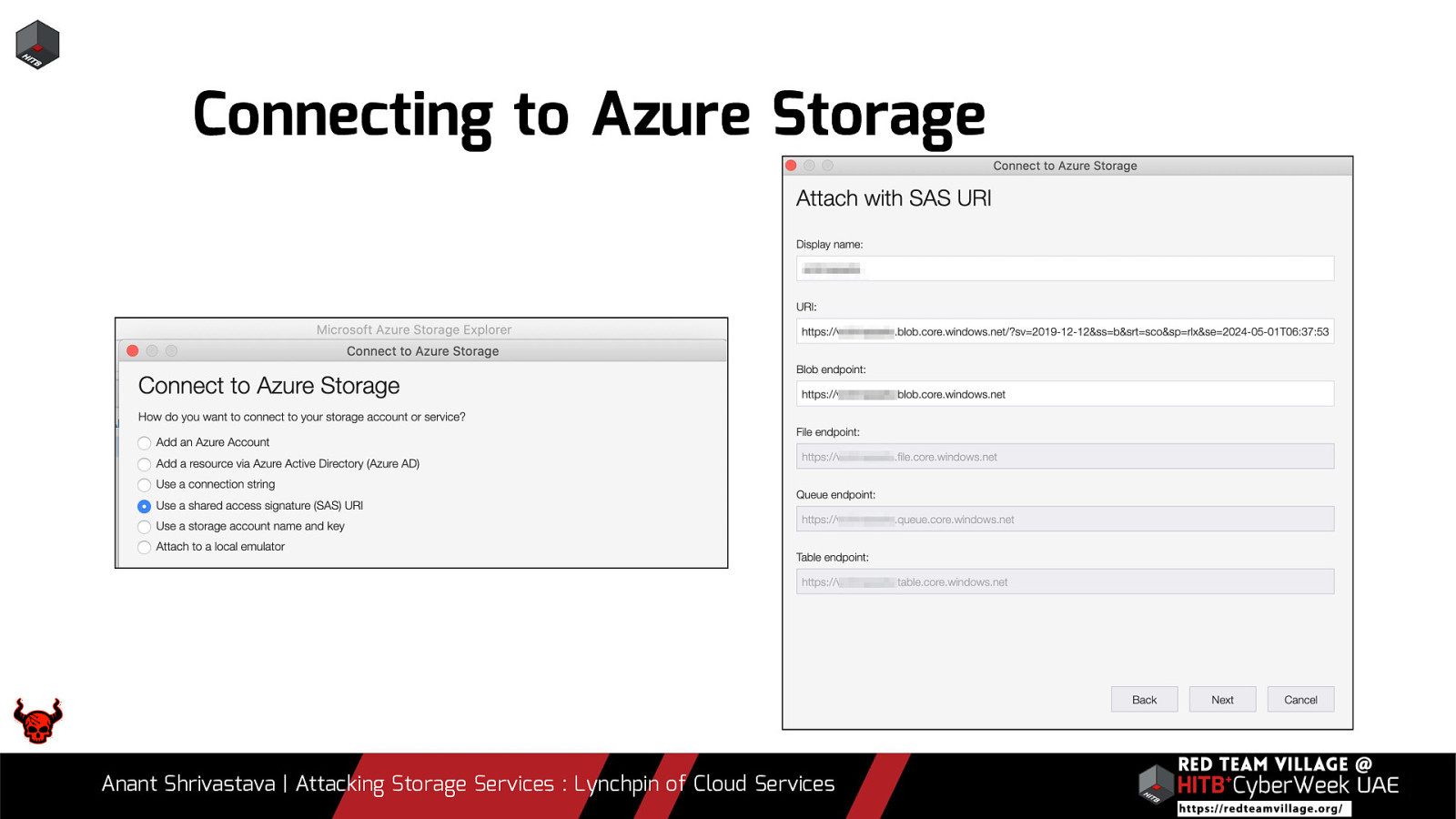
Connecting to Azure Storage Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 29
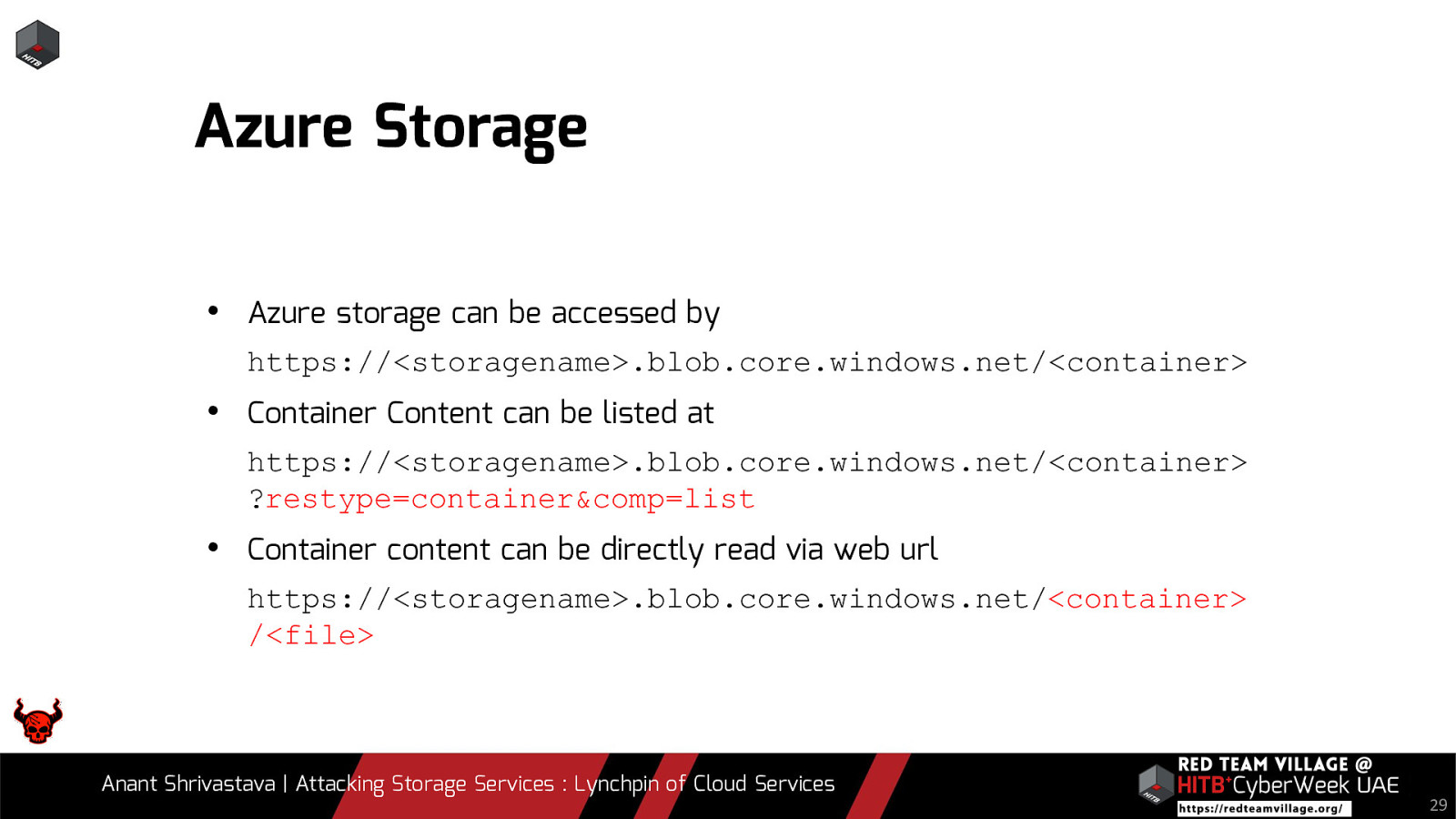
Azure Storage • Azure storage can be accessed by https://<storagename>.blob.core.windows.net/<container> • Container Content can be listed at https://<storagename>.blob.core.windows.net/<container> ?restype=container&comp=list • Container content can be directly read via web url https://<storagename>.blob.core.windows.net/<container> /<file> Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 29
Slide 30
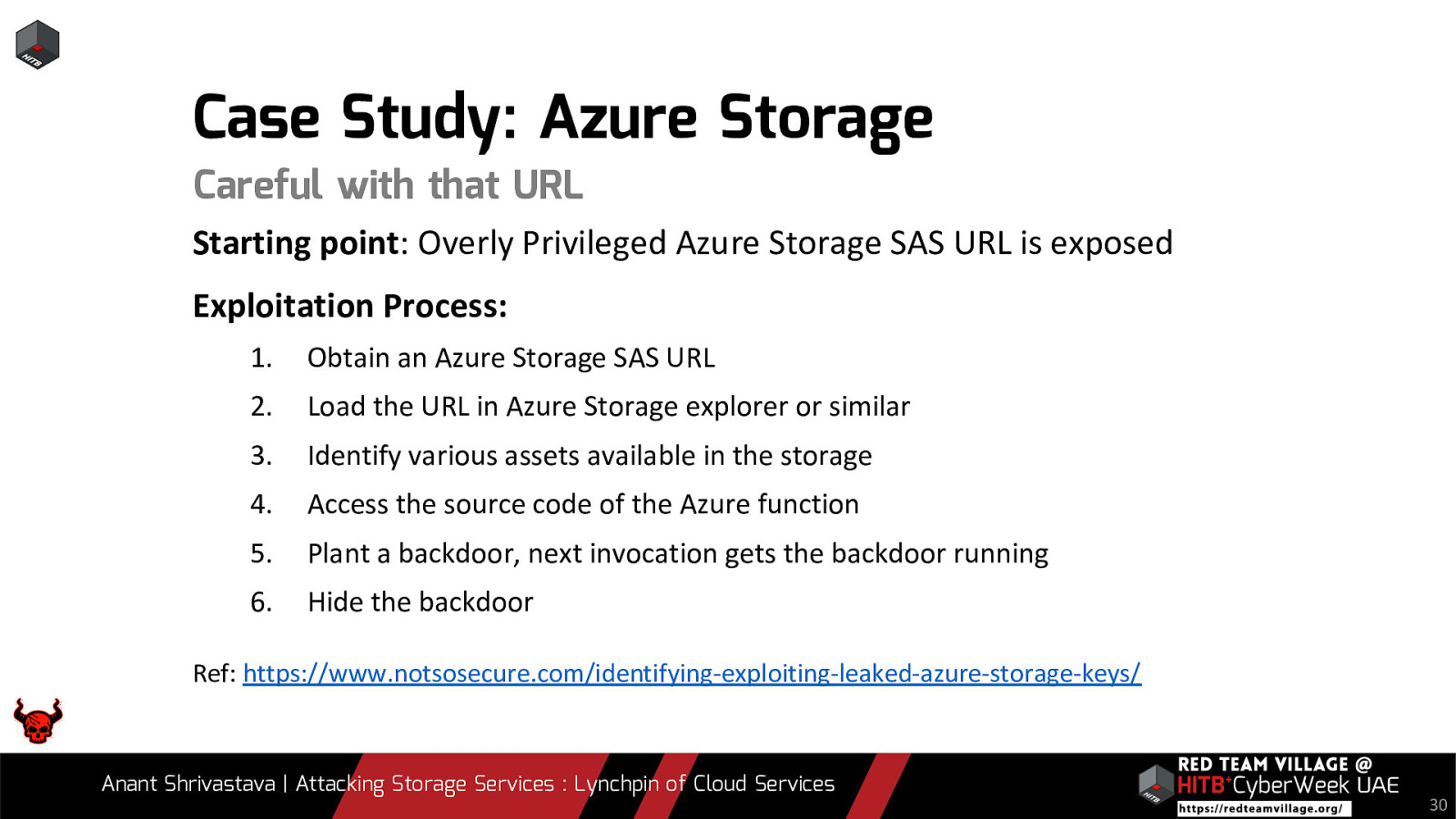
Case Study: Azure Storage Careful with that URL Starting point: Overly Privileged Azure Storage SAS URL is exposed Exploitation Process: 1. Obtain an Azure Storage SAS URL 2. Load the URL in Azure Storage explorer or similar 3. Identify various assets available in the storage 4. Access the source code of the Azure function 5. Plant a backdoor, next invocation gets the backdoor running 6. Hide the backdoor Ref: https://www.notsosecure.com/identifying-exploiting-leaked-azure-storage-keys/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 30
Slide 31

Attack: Post Exploitation • Once access to storage accounts is obtained it opens various path • Example: • Files such as office documents can reveal softwares and usernames • FaaS / PaaS code can lead to RCE in application allowing post exploitation and pivot • Sensitive data in buckets can be worth many times over the company valuation • Secrets such as passwords or keys can lead to pivot in the network Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 32
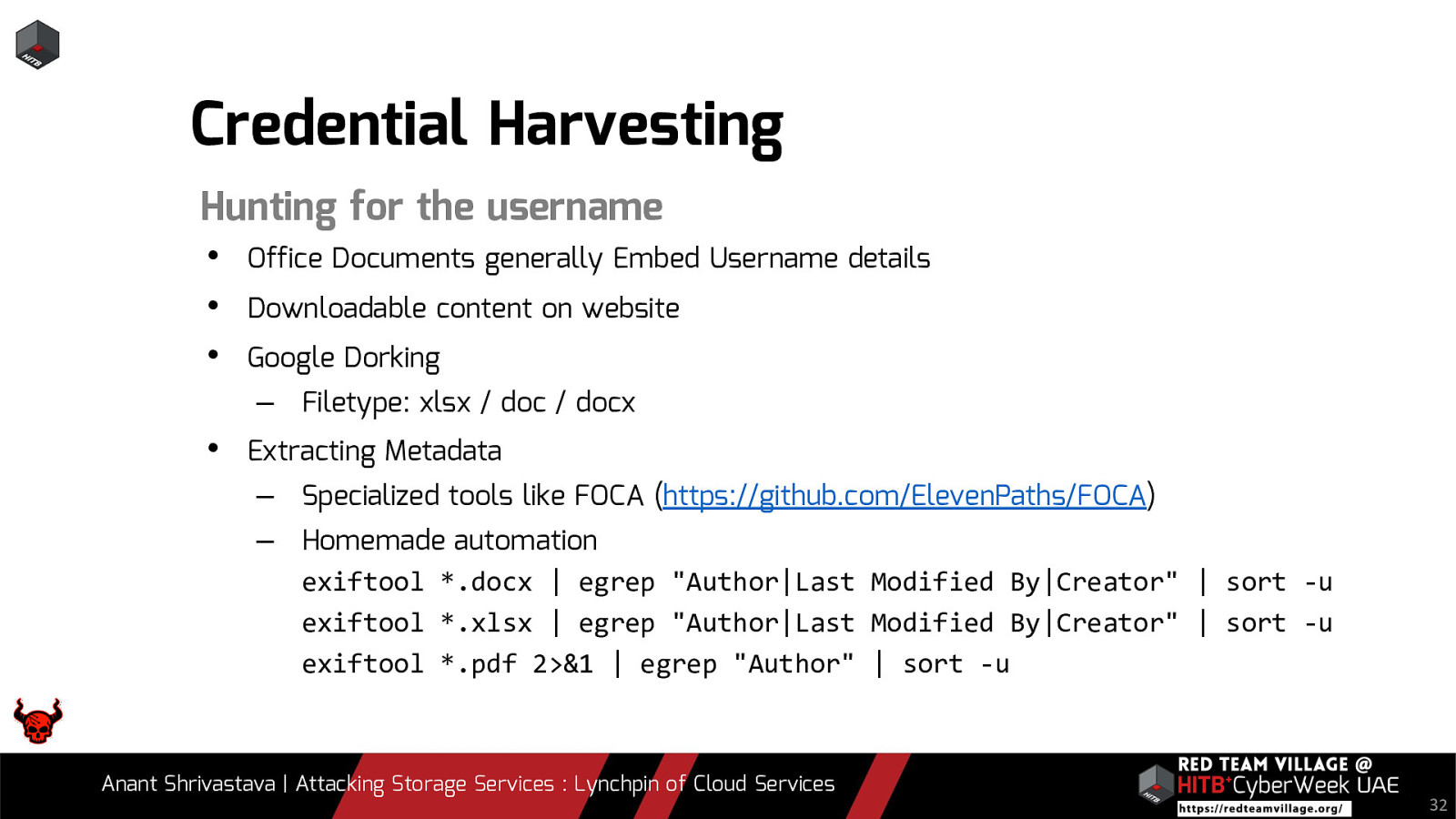
Credential Harvesting Hunting for the username • • • Office Documents generally Embed Username details Downloadable content on website Google Dorking – Filetype: xlsx / doc / docx • Extracting Metadata – Specialized tools like FOCA (https://github.com/ElevenPaths/FOCA) – Homemade automation exiftool *.docx | egrep “Author|Last Modified By|Creator” | sort -u exiftool *.xlsx | egrep “Author|Last Modified By|Creator” | sort -u exiftool *.pdf 2>&1 | egrep “Author” | sort -u Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 32
Slide 33

Case Study: SSRF to EC2 takeover • Starting point: SSRF on a Web Application • Obtained Metadata details (account id, region, security-credentials) • Using credentials enumerate all s3 buckets • One s3 bucket contained pem files for all ec2 boxes • Enumerate instances to identify higher power roles • Obtained access to those instances via pem files • Backdooring the AWS account by creating new id with iam:* capabilities • Reference: https://www.threatstack.com/cloud-attack (not exact but similar) Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 34
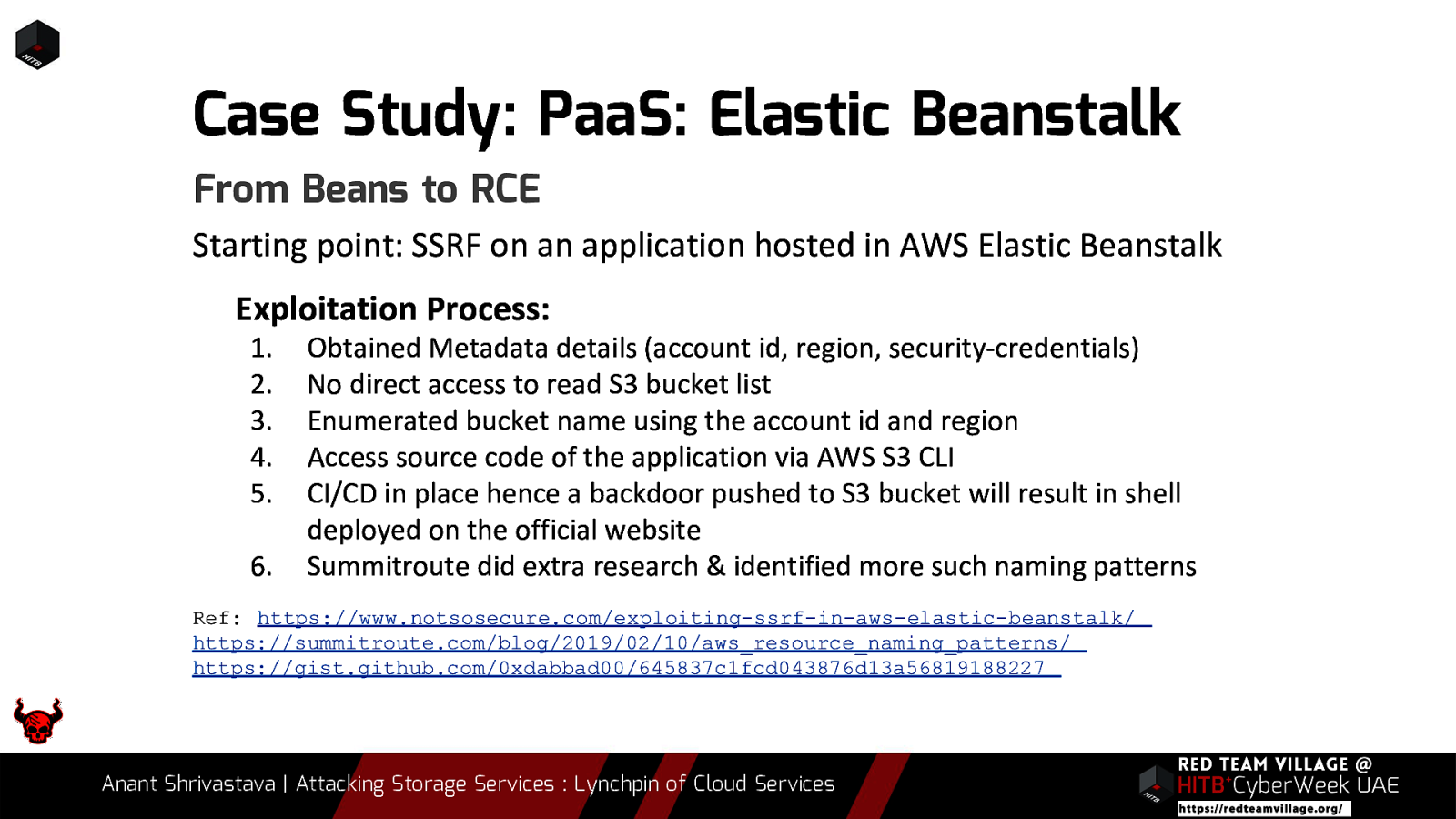
Case Study: PaaS: Elastic Beanstalk From Beans to RCE Starting point: SSRF on an application hosted in AWS Elastic Beanstalk Exploitation Process: 1. 2. 3. 4. 5. 6. Obtained Metadata details (account id, region, security-credentials) No direct access to read S3 bucket list Enumerated bucket name using the account id and region Access source code of the application via AWS S3 CLI CI/CD in place hence a backdoor pushed to S3 bucket will result in shell deployed on the official website Summitroute did extra research & identified more such naming patterns Ref: https://www.notsosecure.com/exploiting-ssrf-in-aws-elastic-beanstalk/ https://summitroute.com/blog/2019/02/10/aws_resource_naming_patterns/ https://gist.github.com/0xdabbad00/645837c1fcd043876d13a56819188227 Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 35
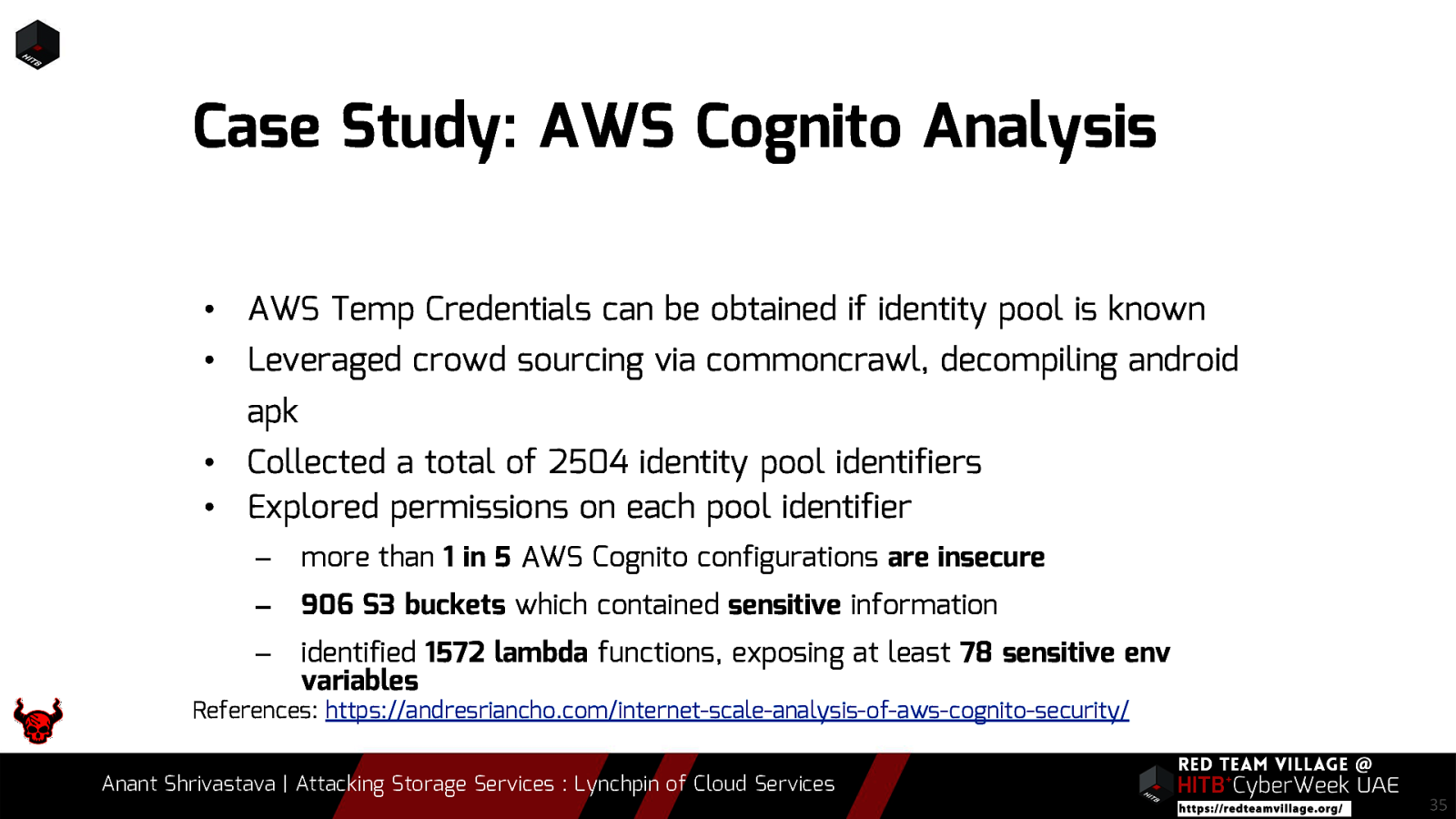
Case Study: AWS Cognito Analysis • AWS Temp Credentials can be obtained if identity pool is known • Leveraged crowd sourcing via commoncrawl, decompiling android apk • Collected a total of 2504 identity pool identifiers • Explored permissions on each pool identifier – more than 1 in 5 AWS Cognito configurations are insecure – 906 S3 buckets which contained sensitive information – identified 1572 lambda functions, exposing at least 78 sensitive env variables References: https://andresriancho.com/internet-scale-analysis-of-aws-cognito-security/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 35
Slide 36

Defenses a.k.a things everyone should do but no one cares • Cloud Vendors • Provide warnings on possible problematic scenario’s • Automation for common problem detection and solution • Tenant • Identity and Access management is key • No unauth /public access unless required • Authenticated user is most definitely not the setting you want • Periodically run scans to identify variations • Ensure you are aware of your own setup limitations Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 37

Vendor Warnings Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 38
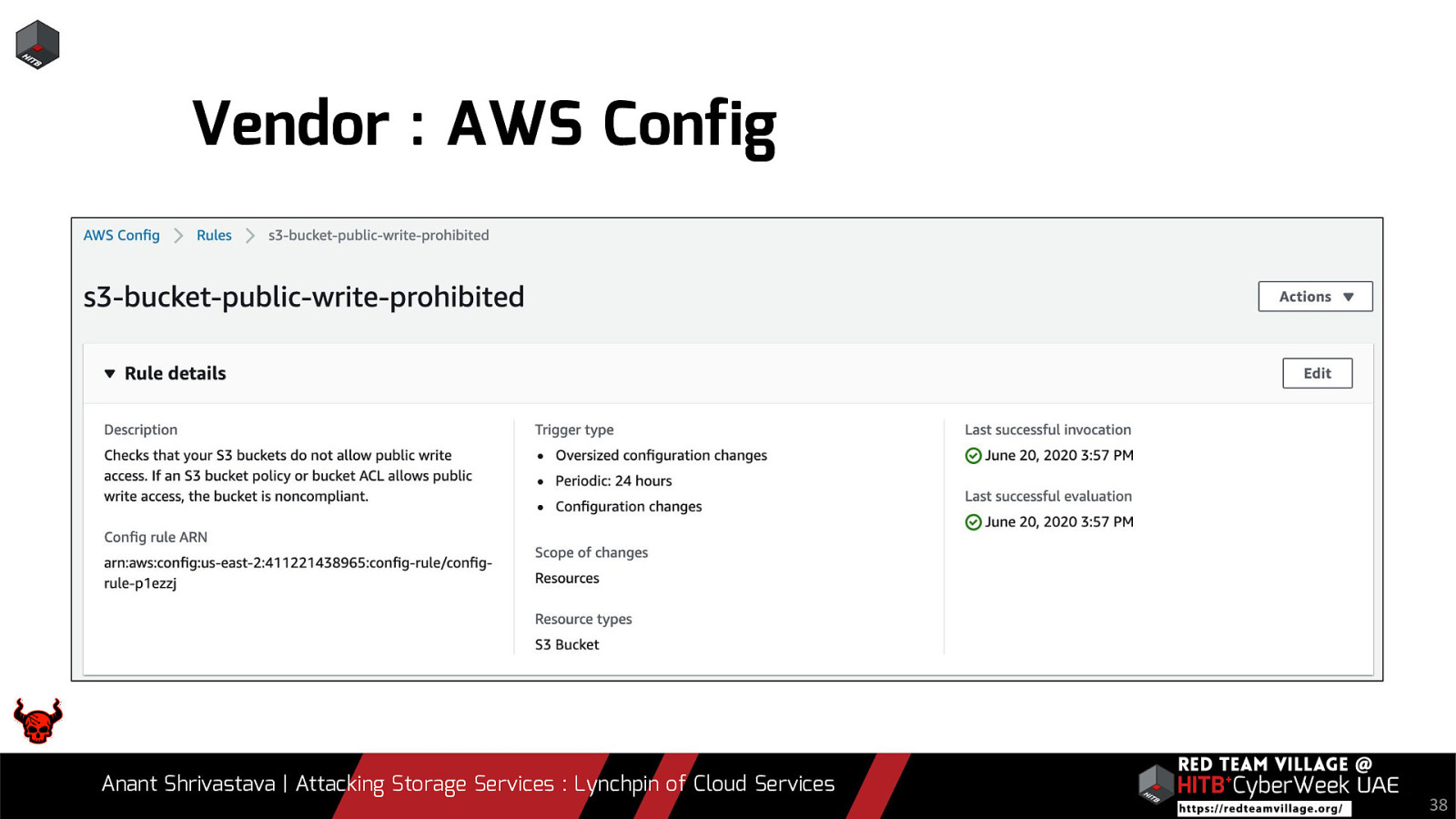
Vendor : AWS Config Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 38
Slide 39
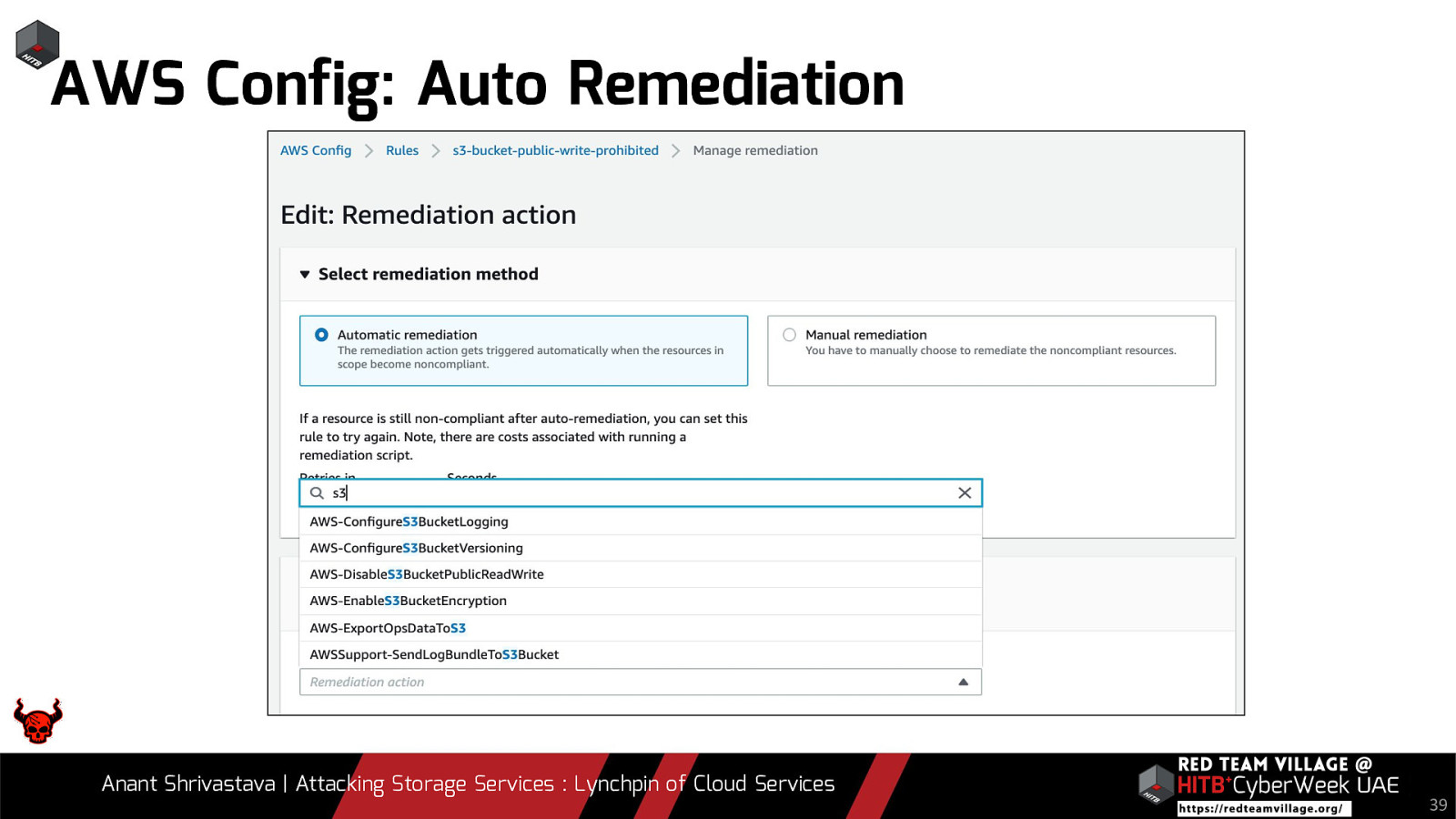
AWS Config: Auto Remediation Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 39
Slide 40
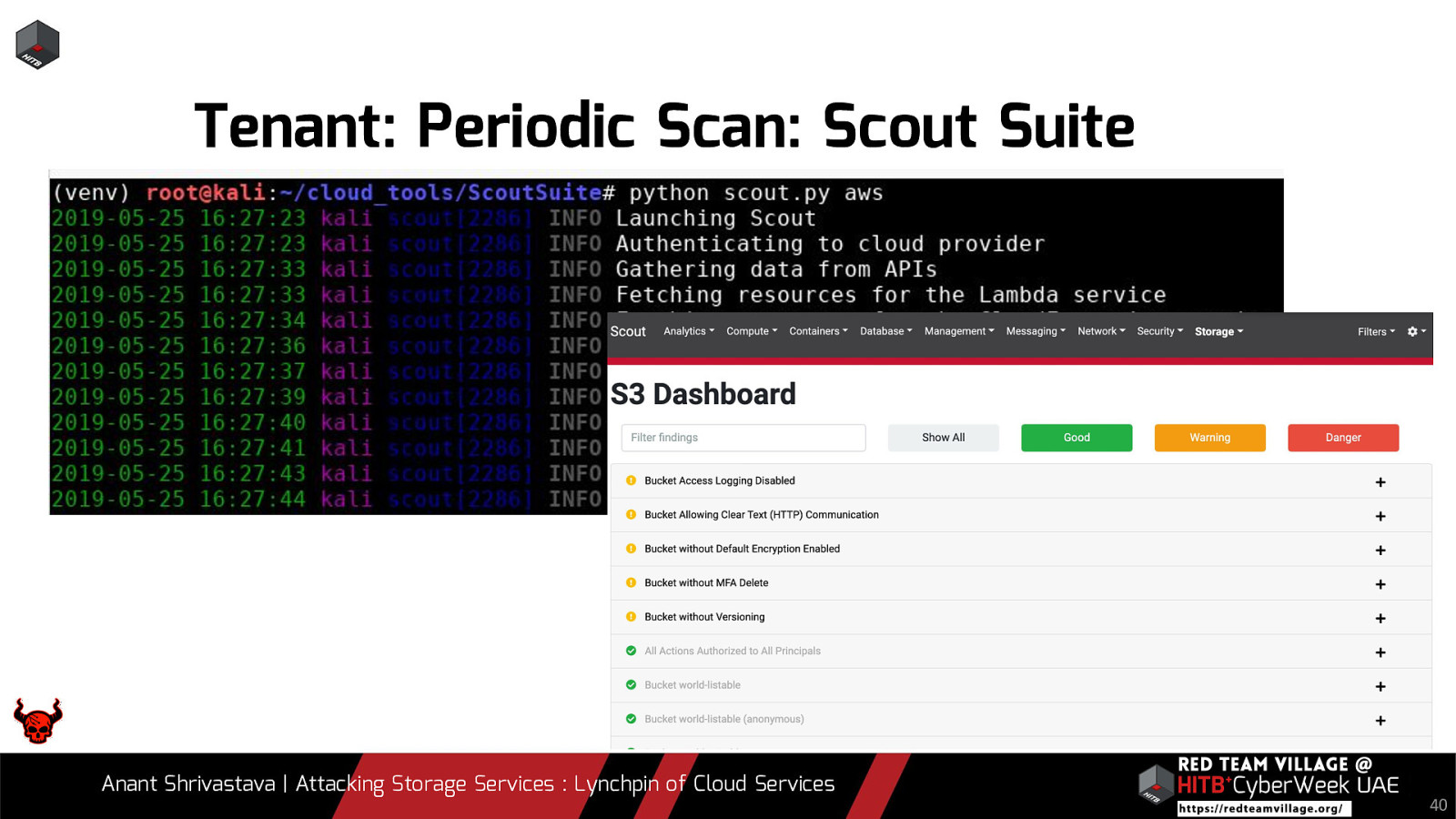
Tenant: Periodic Scan: Scout Suite Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 40
Slide 41
Tenant: Prepare for Disaster • Be prepared for the inevitable • Validate your Setup – – – – Simulate hacks Observe reactions Finetune reactions Revalidate Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 41
Slide 42

Question and Answers I will now look at the chat and answer questions. https://xkcd.com/246/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services 42
Slide 43

Additional Reference Material • Jason Haddix’s awesome The bug hunter’s Methodology Series • https://github.com/jhaddix/tbhm • https://cloudsecwiki.com/ Anant Shrivastava | Attacking Storage Services : Lynchpin of Cloud Services
Slide 44

Thank You Anant Shrivastava, anant@anantshri.info See you at HITB’s Discord channel for questions & answers!