SSL PINNING AND BYPASSES (ANDROID & IOS) BY ANANT SHRIVASTAVA
Slide 1

Slide 2
ANANT SHRIVASTAVA Information Security Consultant Admin - Dev - Security null + OWASP + G4H http://anantshri.info and @anantshri Trainer : Blackhat, RuxCon, NullCon, g0s, c0c0n Speaker : Nullcon, c0c0n, ClubHack, RootConf Android Tamer Code Vigilant
Slide 3

SSL PINNING Another layer to achieve secure communication specially protection against MiTM
Slide 4
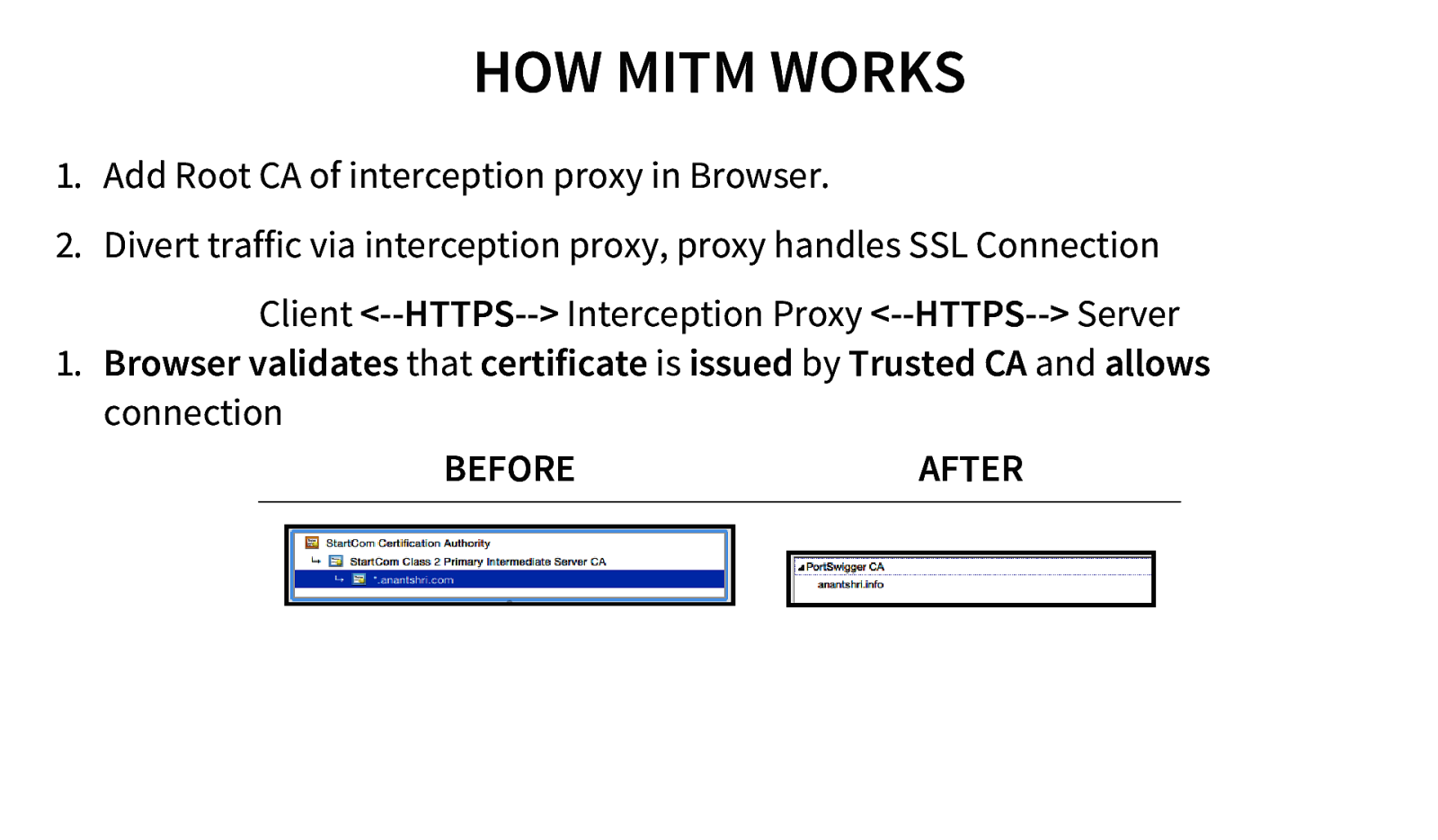
HOW MITM WORKS 1. Add Root CA of interception proxy in Browser. 2. Divert traffic via interception proxy, proxy handles SSL Connection Client <—HTTPS—> Interception Proxy <—HTTPS—> Server 1. Browser validates that certificate is issued by Trusted CA and allows connection BEFORE AFTER
Slide 5

PKI IS BROKEN 1. System Trust all CA in Trust Store (PortSwigger CA) 2. System Trust’s ROOT CA not certification chain 3. Any CA can issue certificate to any website (Diginotar, Trustwave, NIC and many more) 4. Certificate Stolen: Welcome to Revocation hell and CRL Nightmare 5. OCSP to the rescue over port 80 6. and many more
Slide 6

SO WHAT SHOULD WE DO Pin Trust on our own certification chain and validate it at Client Side
Slide 7

Slide 8

WHAT’S THE CATCH 1. 2. 3. 4. 5. 6. What if you get new certificate from a different service provider What if your certificate chain changes What if certificate is revoked What if certificate is stolen What is Client is malacious What if ….. Answer: You need to update the code everytime certificate changes ITS EASY PUSH AN UPDATE
Slide 9

SO WHY SHOULD I BOTHER 1. Developers : This hinders attacker from traffic interception. Adds another layer for Attacker to look for. Without Rooting devices its nearly imposible to bypass it so far. 2. Pentesters : This hinders you from inspecting application (be ready for bypasses section)
Slide 10

SSL PINNING IN ANDROID & BYPASS
Slide 11

HOW TO IMPLEMENT SSL PINNING Multiple ways 1. Store Certificate in sqlite and use it directly 2. Store sha1 hashes and compare 3. Store sha1 hash of one element in chain and compare
Slide 12
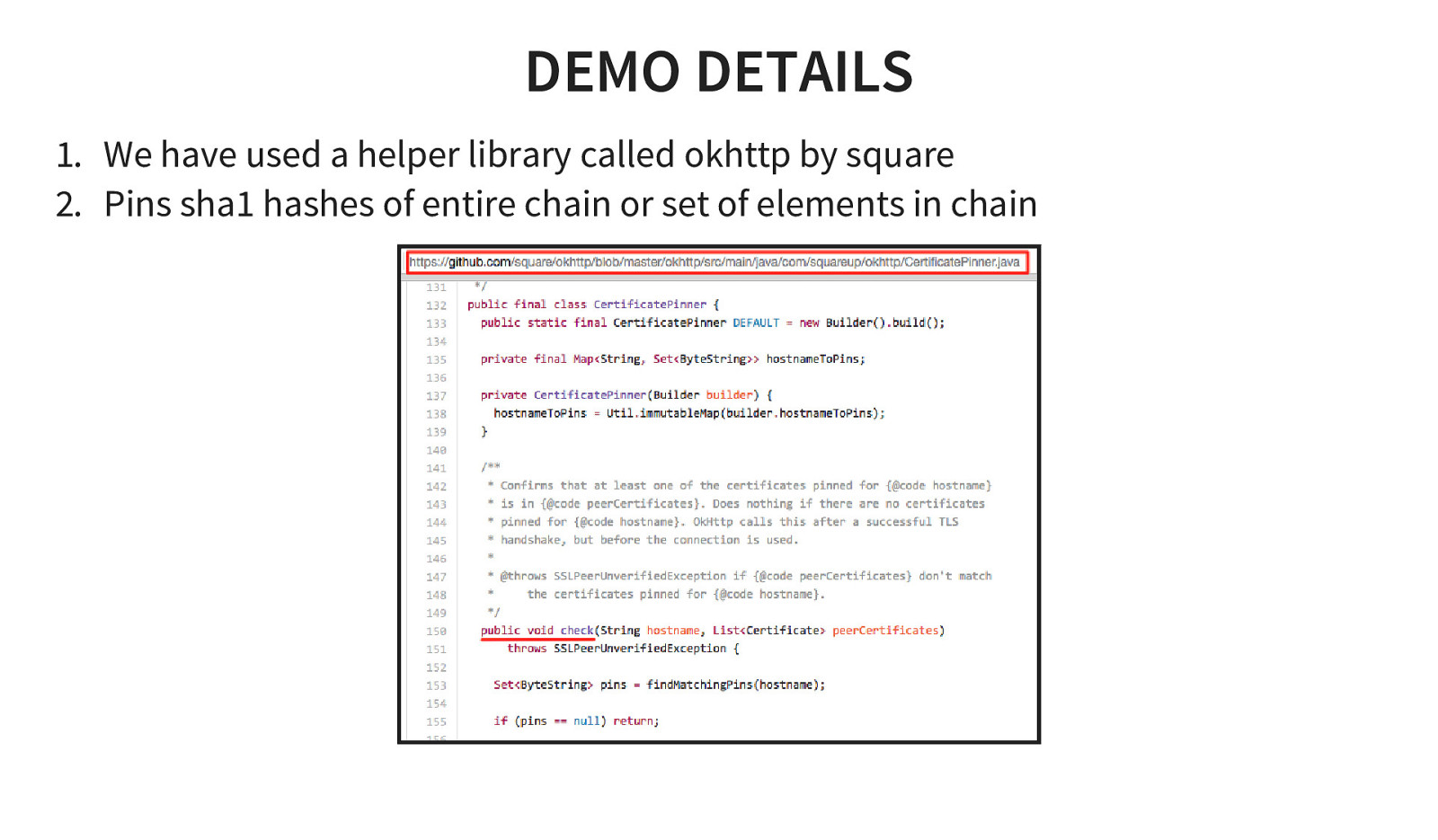
DEMO DETAILS 1. We have used a helper library called okhttp by square 2. Pins sha1 hashes of entire chain or set of elements in chain
Slide 13

DEMO SSL PINNING
Slide 14

BYPASS DEMO
Slide 15
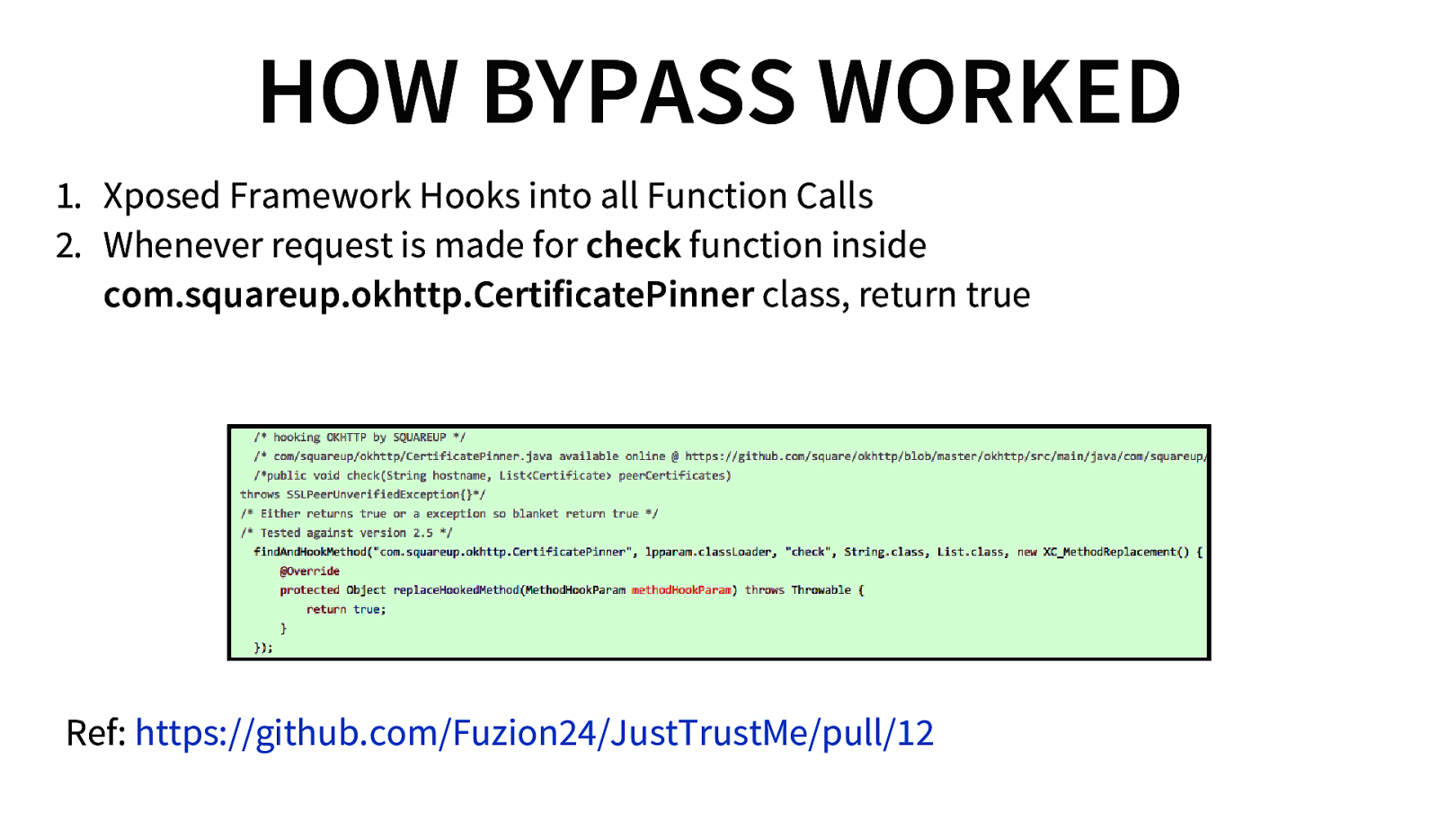
HOW BYPASS WORKED 1. Xposed Framework Hooks into all Function Calls 2. Whenever request is made for check function inside com.squareup.okhttp.CertificatePinner class, return true Ref: https://github.com/Fuzion24/JustTrustMe/pull/12
Slide 16
ANDROID DEMO END
Slide 17

SSL PINNING IN IOS & BYPASS
Slide 18

HOW TO IMPLEMENT SSL PINNING 1. Use Third Party helper like 1. SwiftHTTP 2. TrustKit 2. Or Use SecTrustEvaluate via NSURLConnectionDelegate (third party helper basicly are wrapper to do this)
Slide 19

DEMO SSL PINNING
Slide 20

HOW TO BYPASS 1. https://github.com/iSECPartners/ios-ssl-kill-switch 2. https://github.com/nabla-c0d3/ssl-kill-switch2 (superseeds ios-ssl-kill-switch works on 9.0.2 also, doesn’t work with itunes/appstore by default)
Slide 21

BYPASS DEMO
Slide 22
HOW IT WORKS 1. Leverages Cydia substrate 2. Uses MobileSubstrate to inject on process 3. Hooks on Secure Trasport API instead of SecTrustEvaluate or NSURL* as The Secure Transport API is “the lowest-level TLS implementation on iOS” 1. Patch SSLCreateContext(): Disable the built-in certificate validation in all SSL contexts 2. Patch SSLSetSessionOption(): Remove the ability to re-enable the built-in certificate validation 3. Patch SSLHandshake(): Force a trust-all custom certificate validation Reference: https://nabla-c0d3.github.io/blog/2013/08/20/ios-ssl-kill-switch-v0dot-5-released/
Slide 23
IOS DEMO END
Slide 24

ANY QUESTIONS
Slide 25
ANANT SHRIVASTAVA Information Security Consultant Admin - Dev - Security null + OWASP + G4H http://anantshri.info and @anantshri Trainer : Blackhat, RuxCon, NullCon, g0s, c0c0n Speaker : Nullcon, c0c0n, ClubHack, RootConf Android Tamer Code Vigilant
Slide 26

REFERENCES Generic 1. https://www.owasp.org/index.php/Certificate_and_Public_Key_Pinning Android 1. https://github.com/square/okhttp 2. https://github.com/Fuzion24/JustTrustMe iOS 1. 2. 3. 4. https://github.com/daltoniam/SwiftHTTP https://github.com/datatheorem/TrustKit https://github.com/iSECPartners/ios-ssl-kill-switch https://github.com/nabla-c0d3/ssl-kill-switch2/