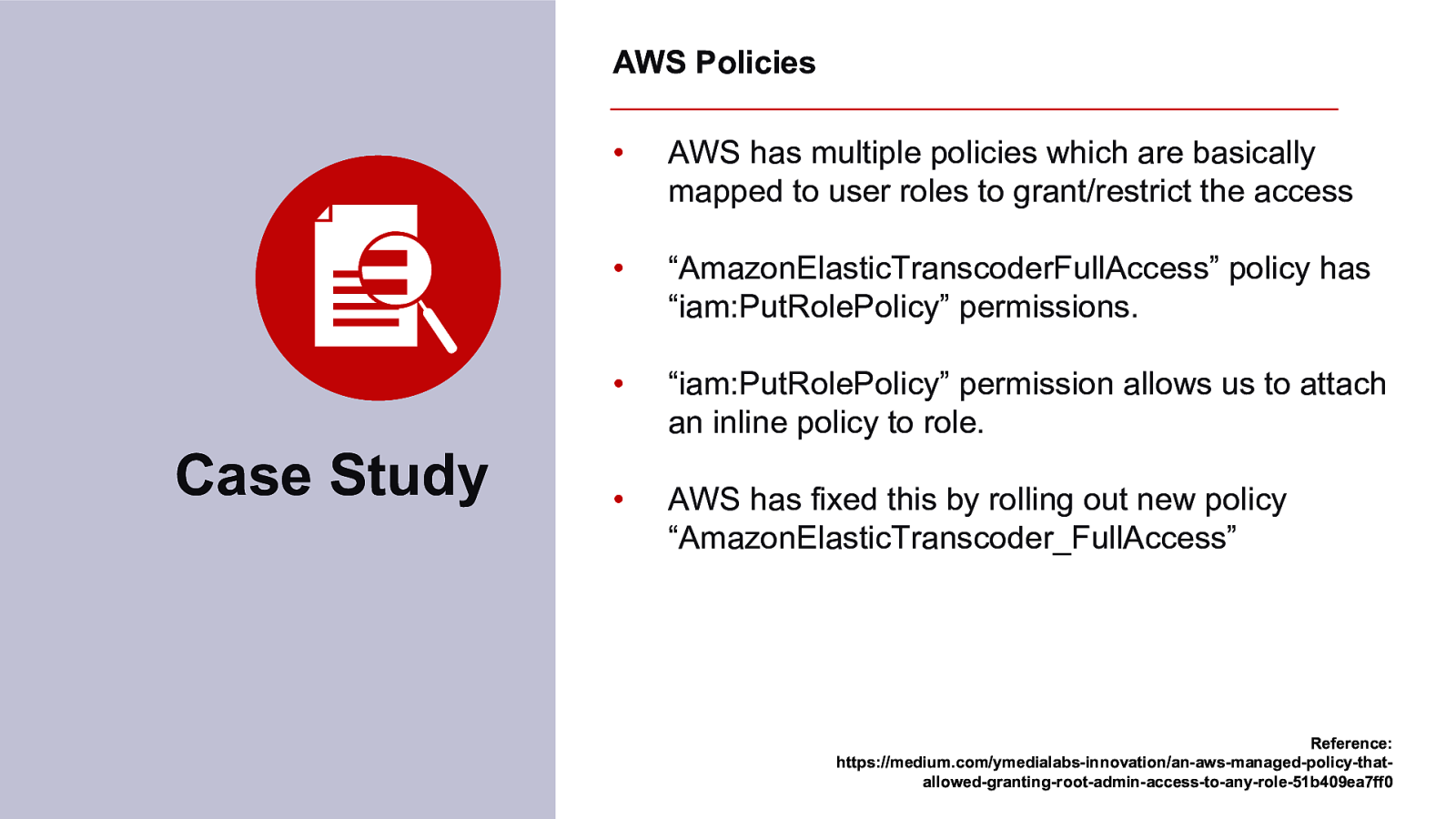
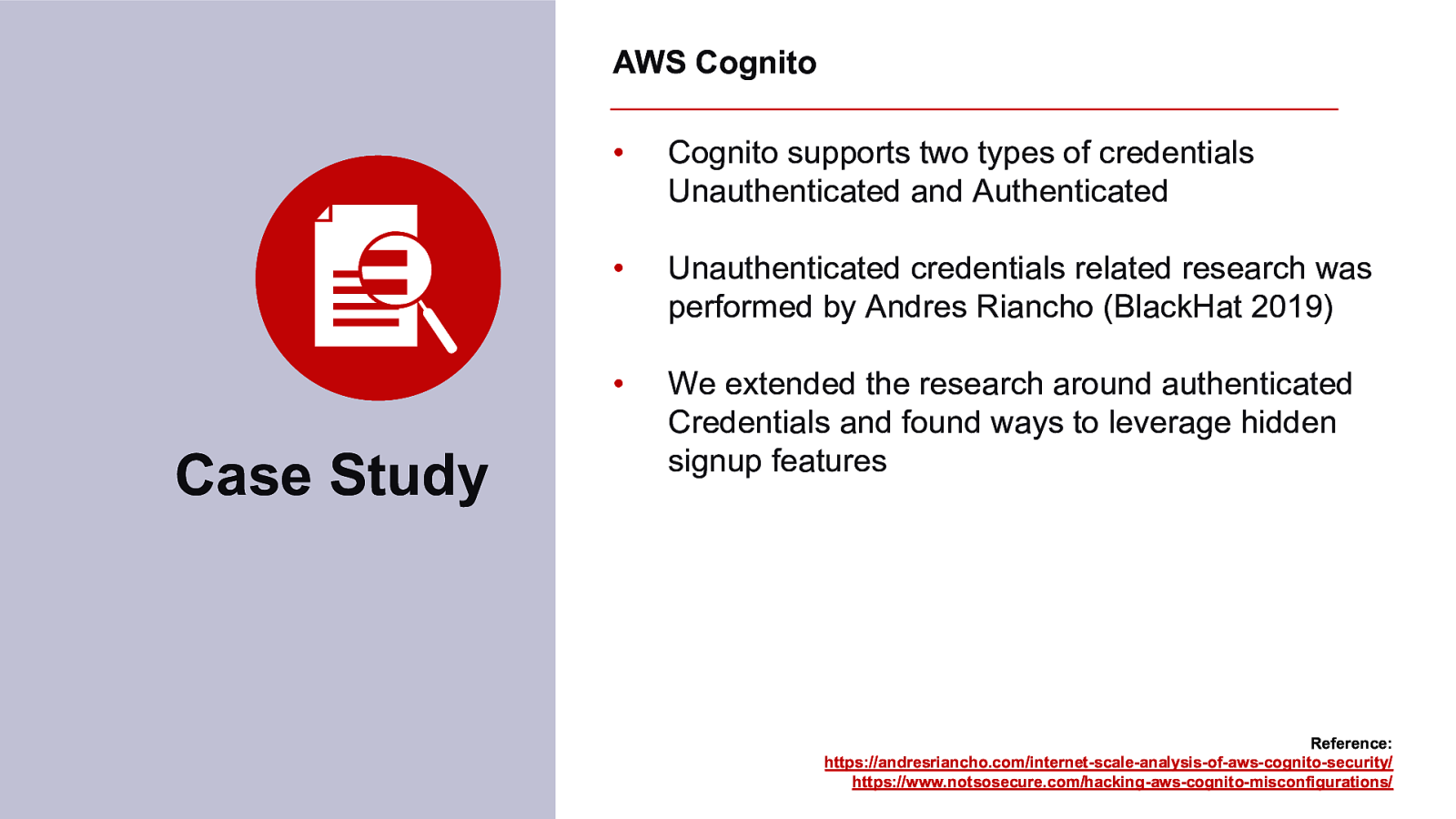
STEALING THE SILVER LINING FROM YOUR CLOUD
A presentation at Black Hat WebCast by Anant Shrivastava
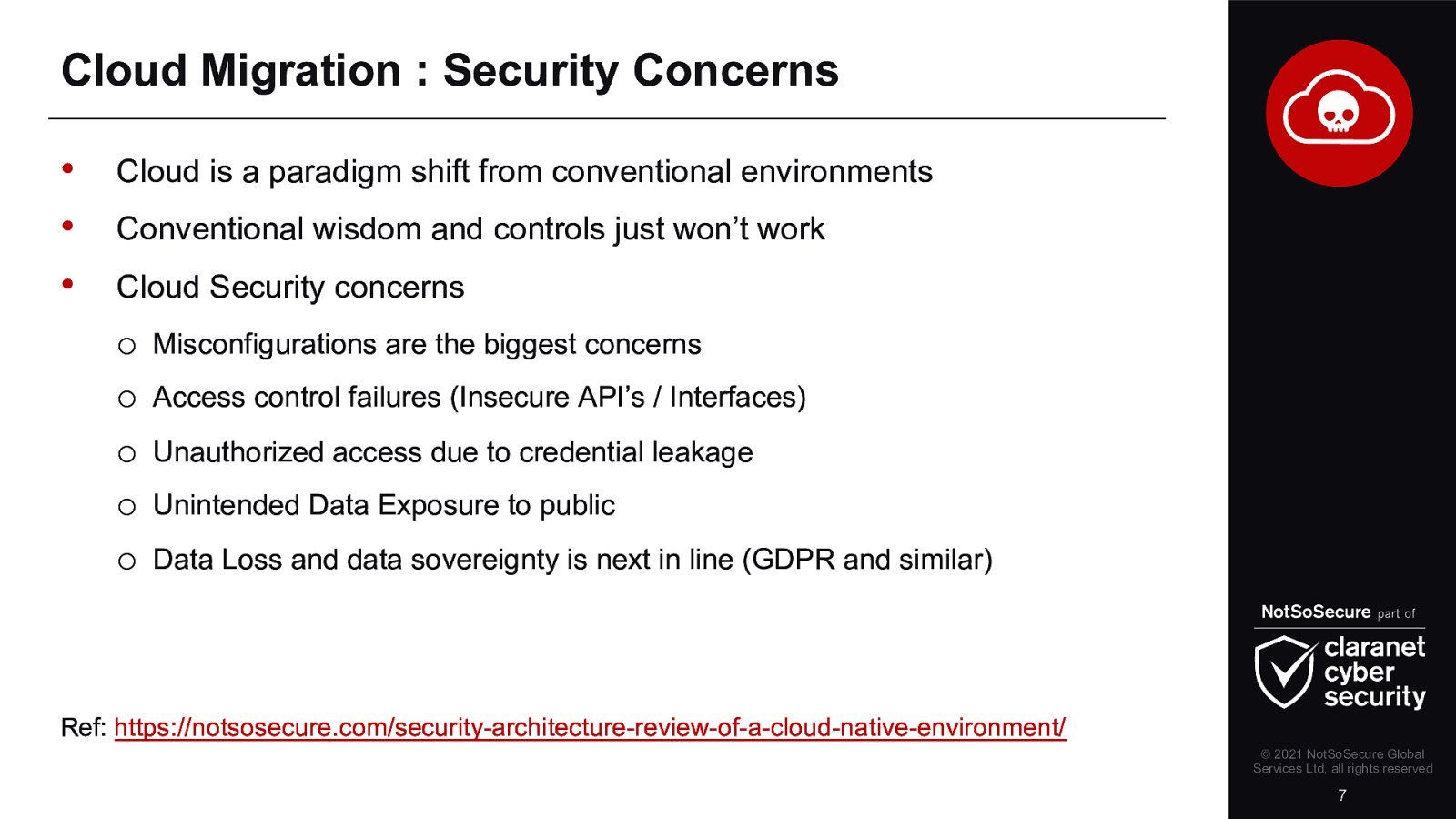
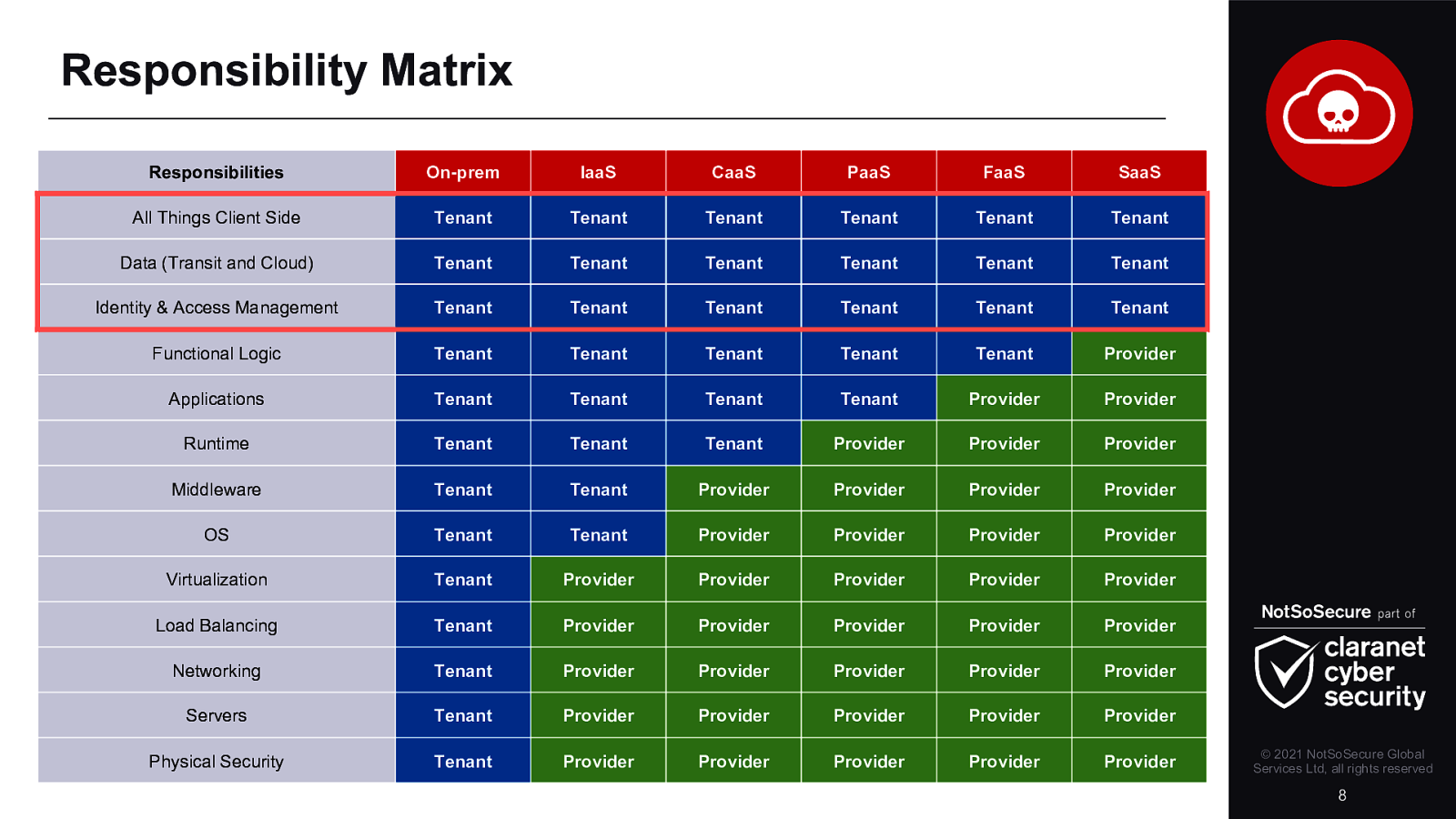
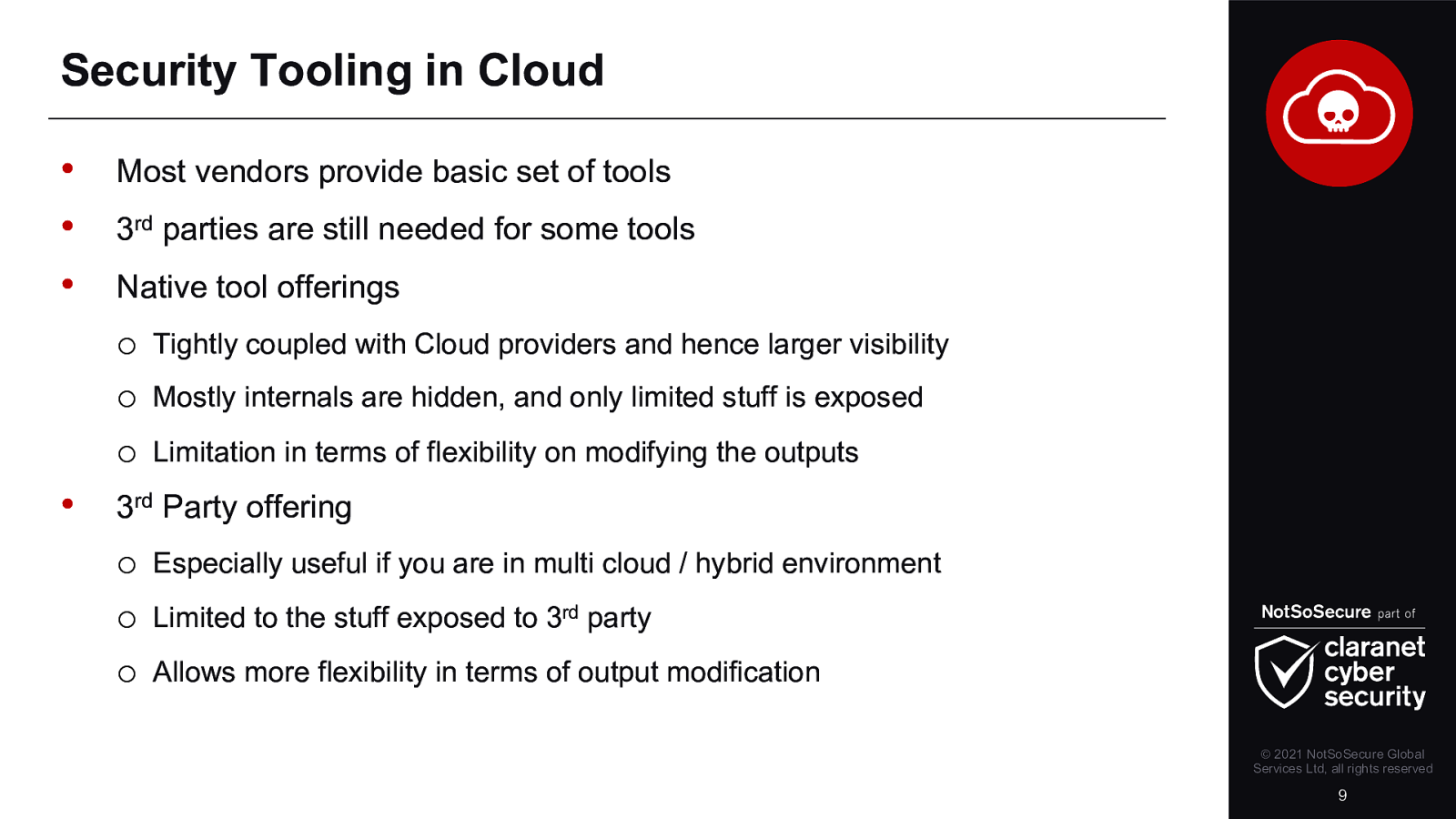
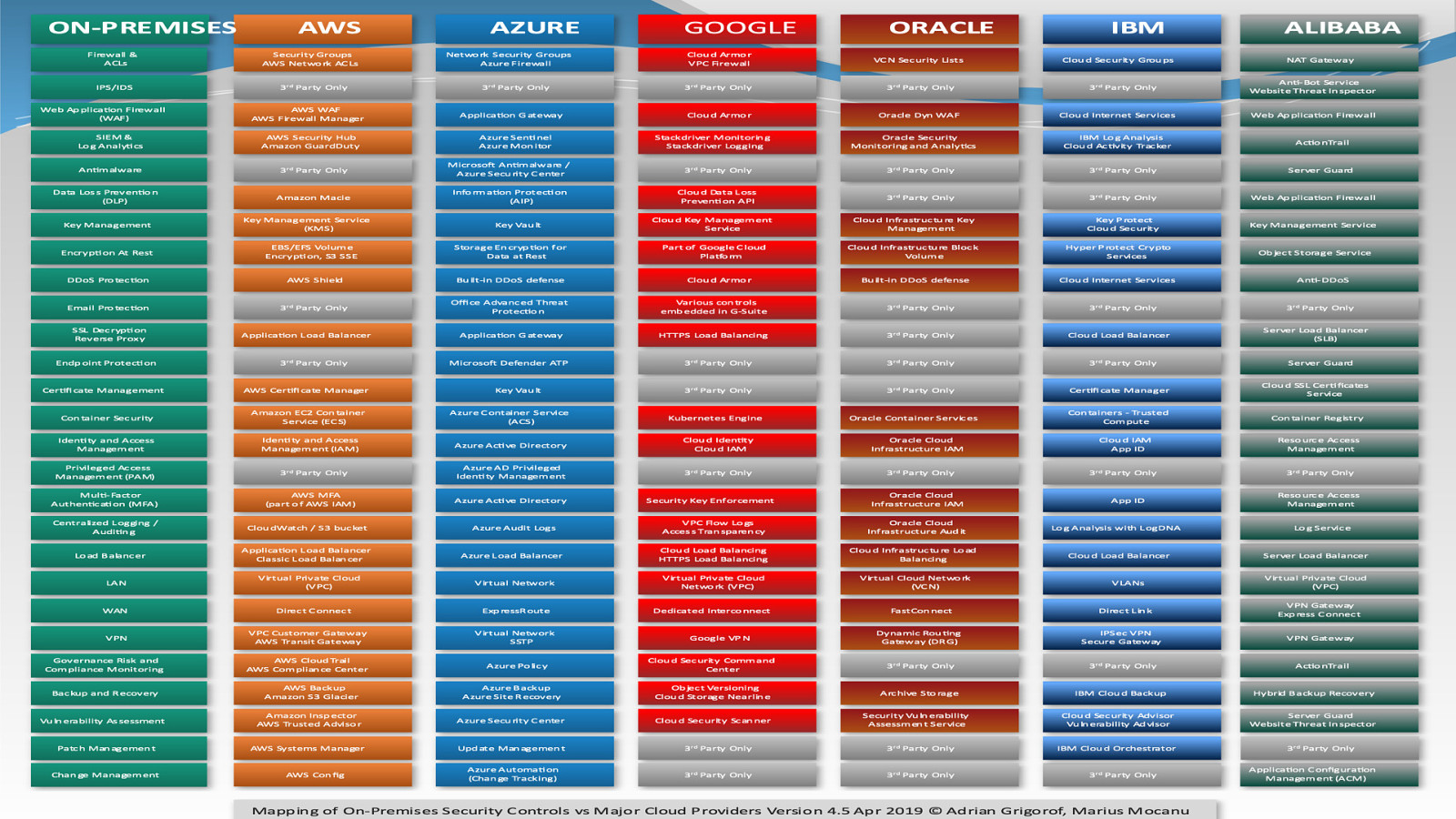
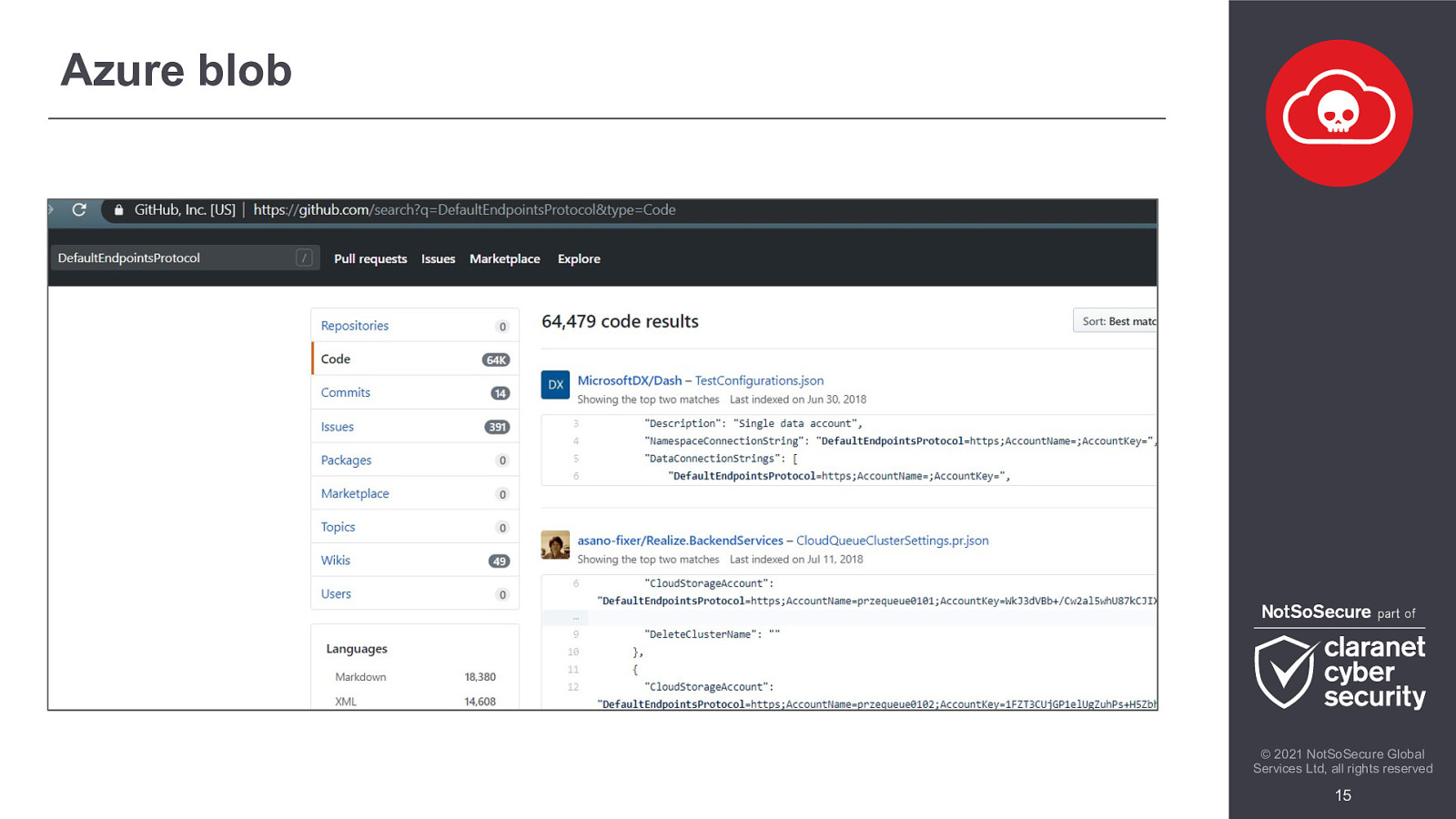
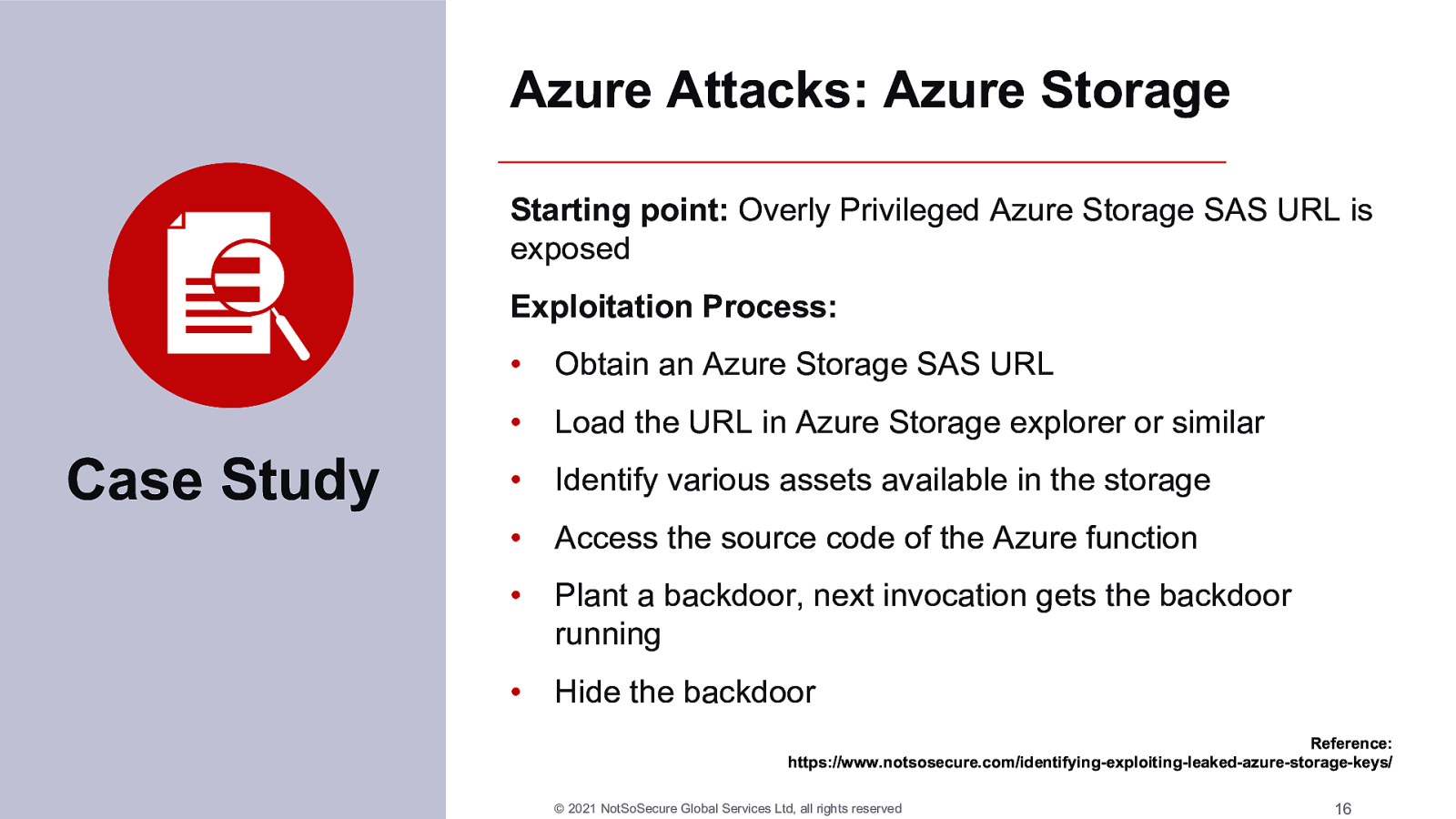
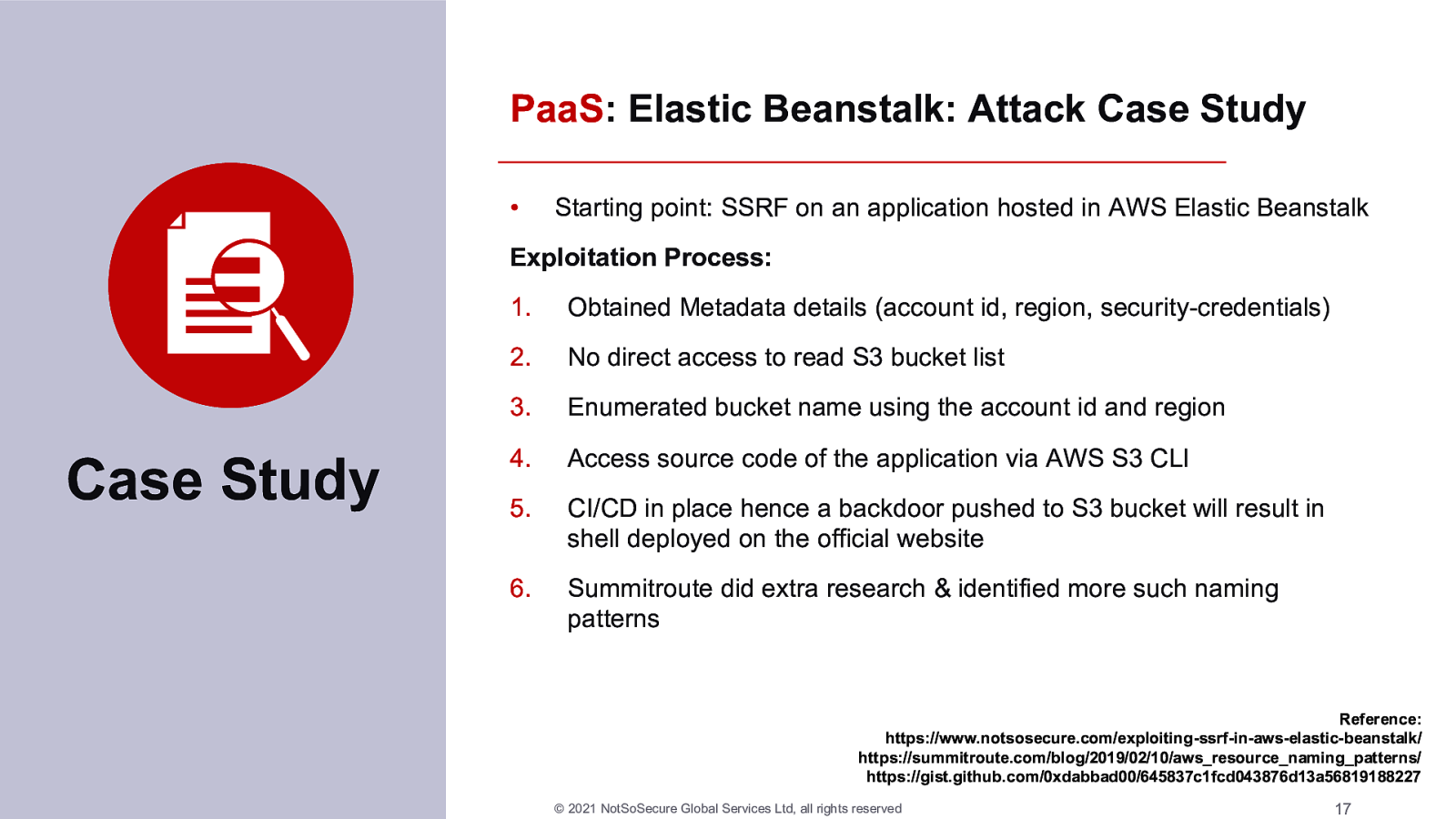
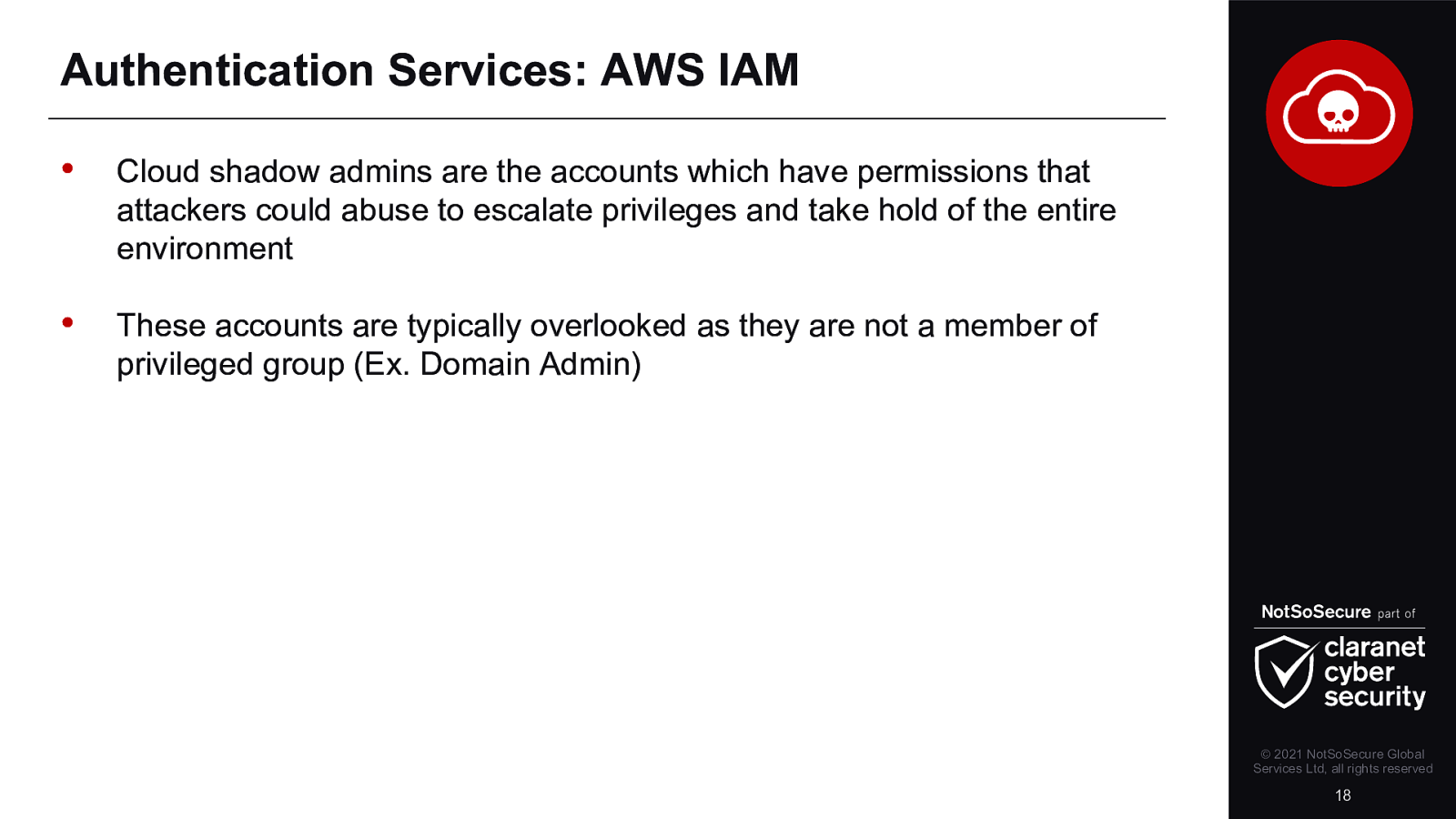
The last couple of years have seen a tremendous growth in cloud adoption. Every organisation has some cloud usage, using either a mixture of in-house and public cloud or they are fully cloud based. This unprecedented adoption of technologies has opened gaping holes in an organisation’s security landscape. Whilst moving to the cloud is a sensible move because vendors are taking an increasingly larger responsibility in being more proactive towards security, it also opens organisations up to be more severely punished for their mistakes.
In this demo filled webinar, we will discuss various scenarios where cloud based technologies have given opportunities to attackers that have resulted in catastrophic repercussions for the company involved.
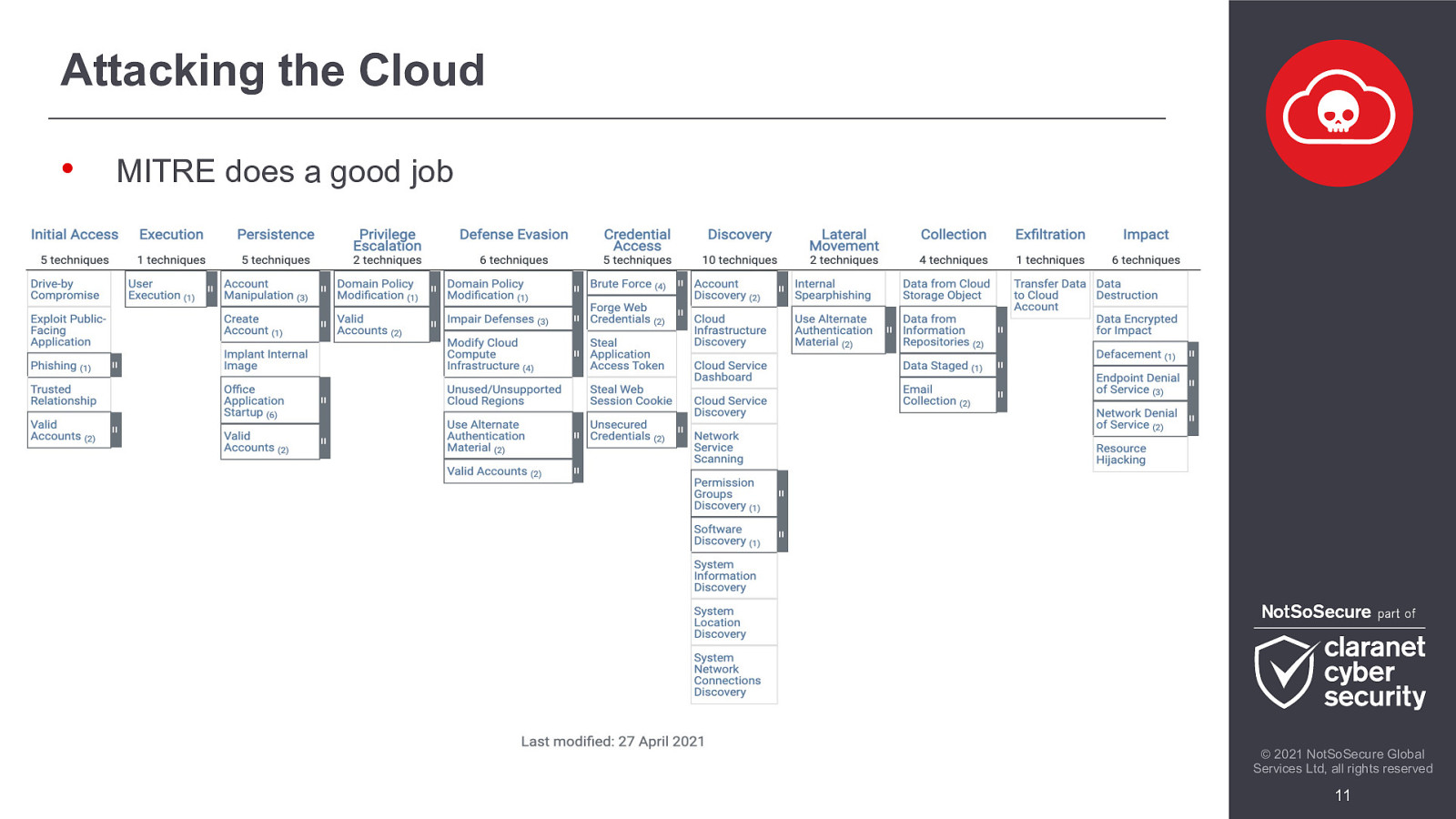
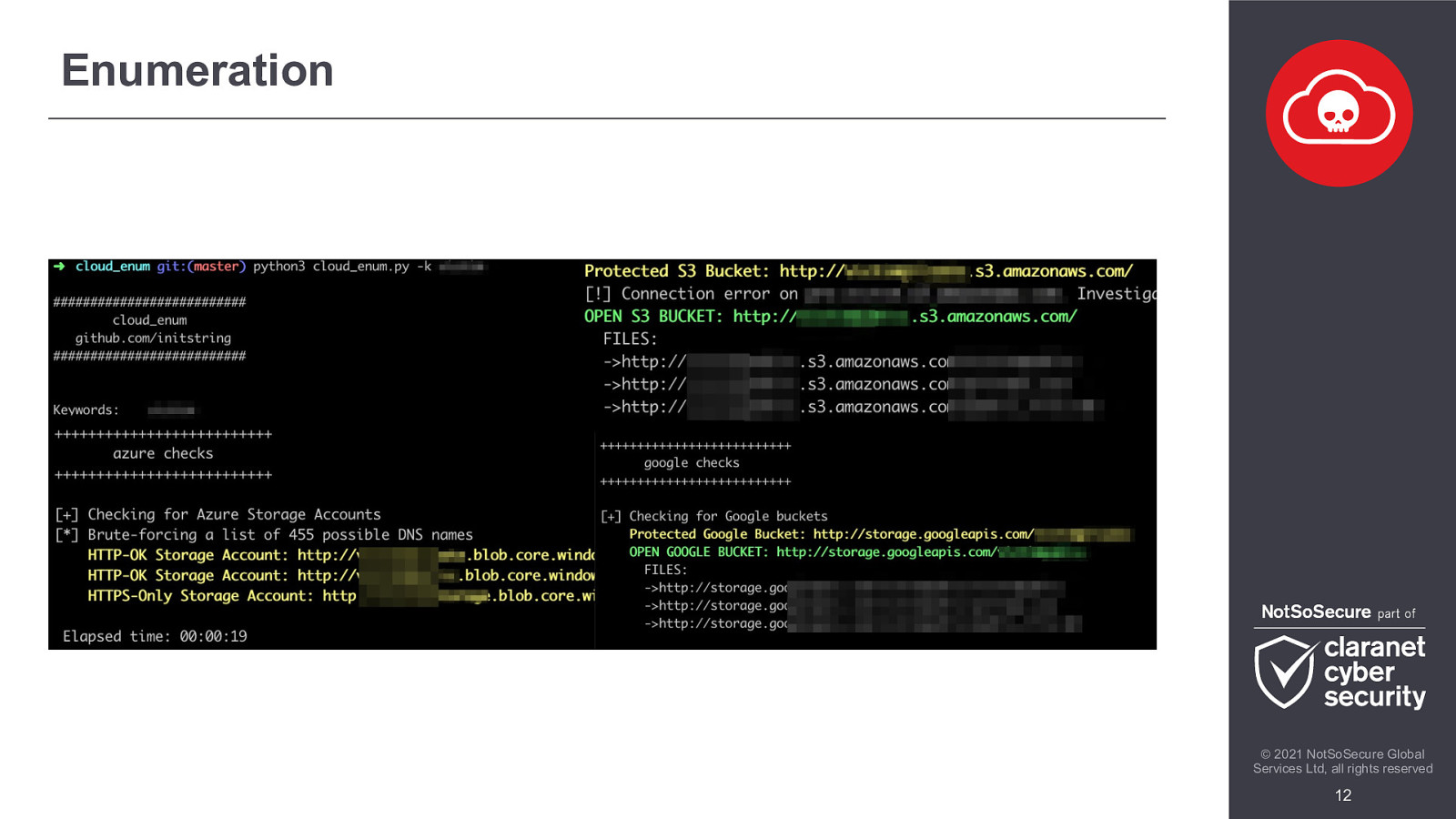
We will look at ways to exploit these cloud environments from an attackers point of view, covering various phases of attack from enumeration to exploitation, through the escalation of privileges and ending with a complete ownage of the cloud network.
Resources
The following resources were mentioned during the presentation or are useful additional information.
Buzz and feedback
Here’s what was said about this presentation on social media.