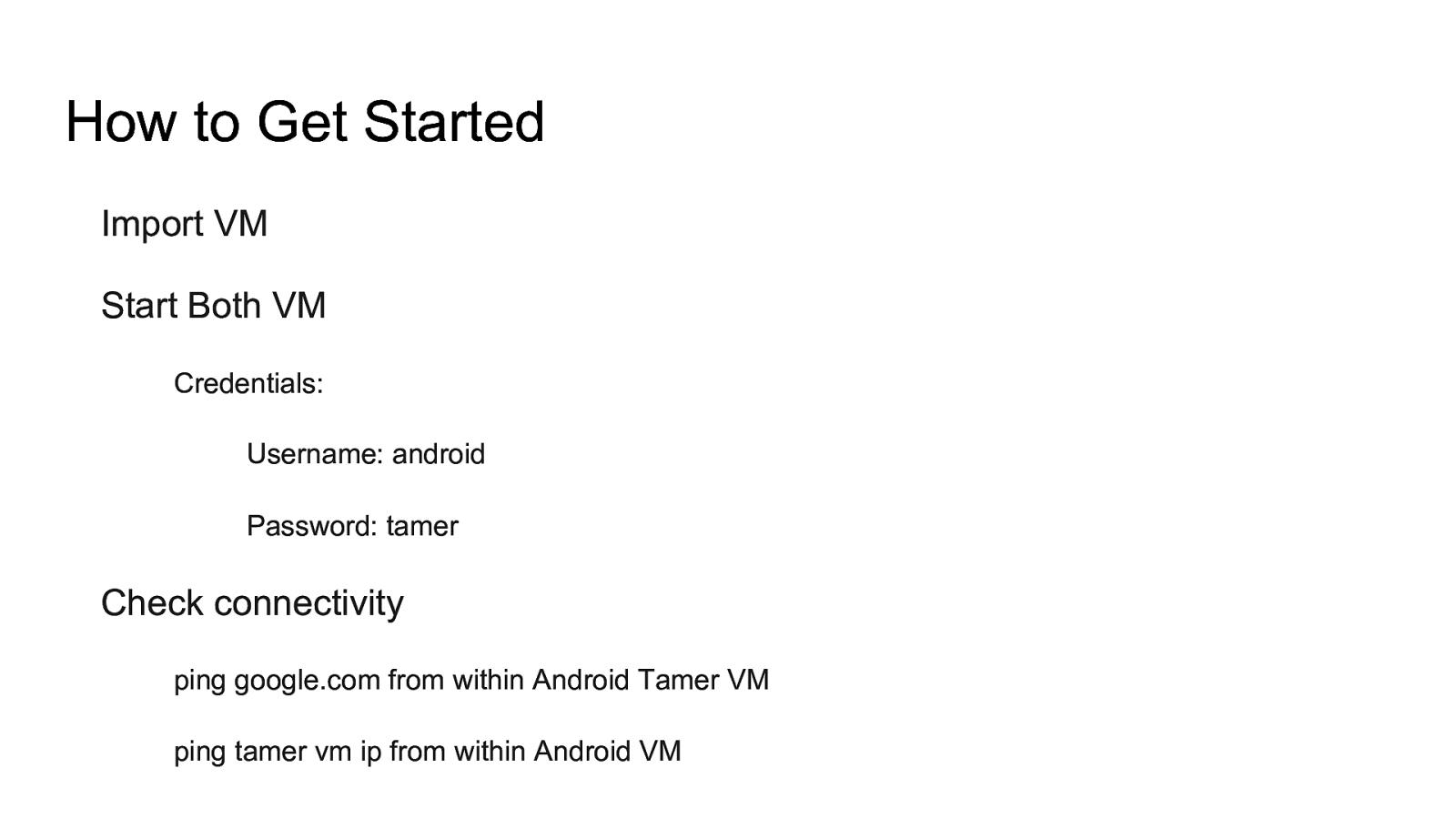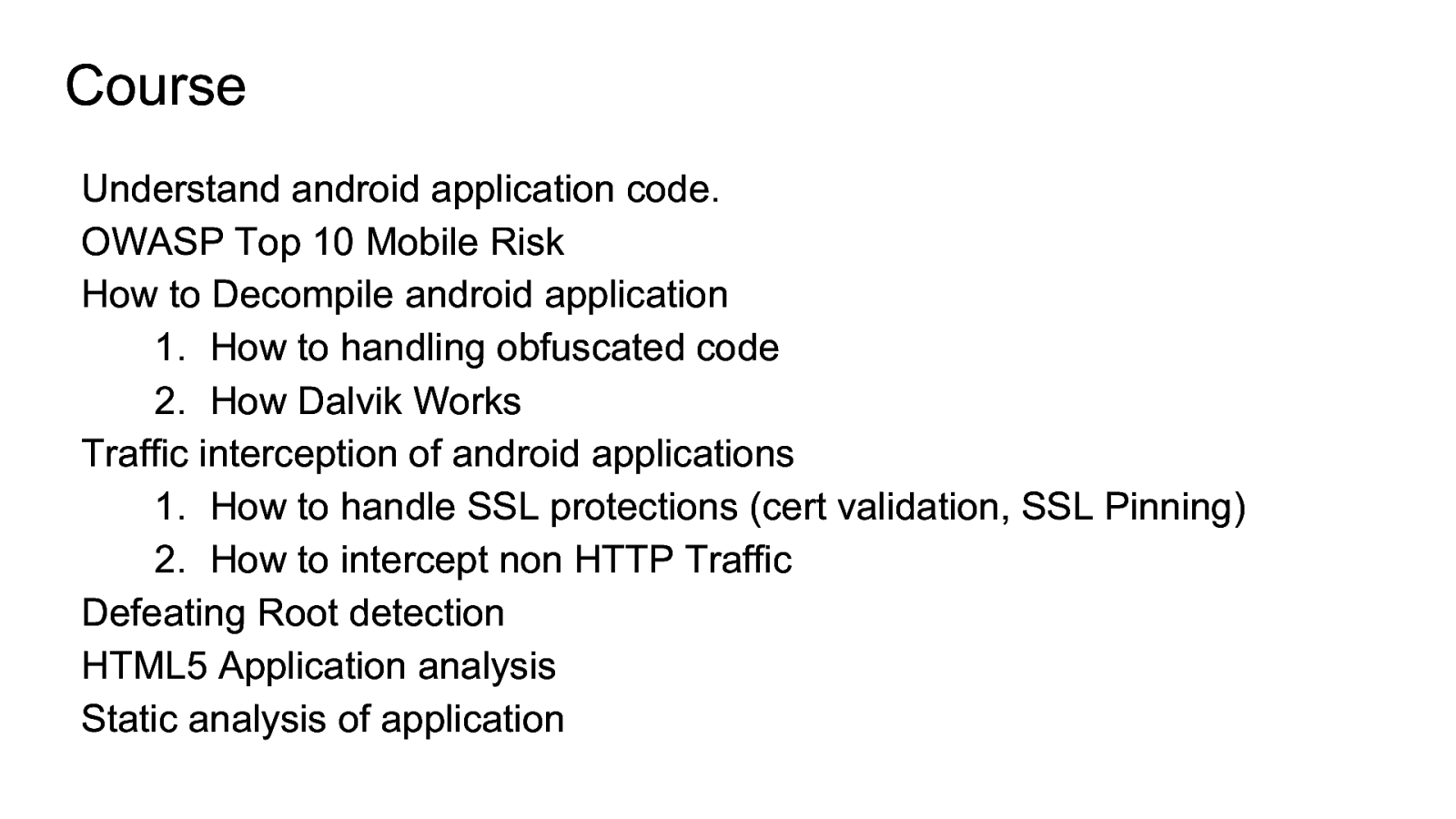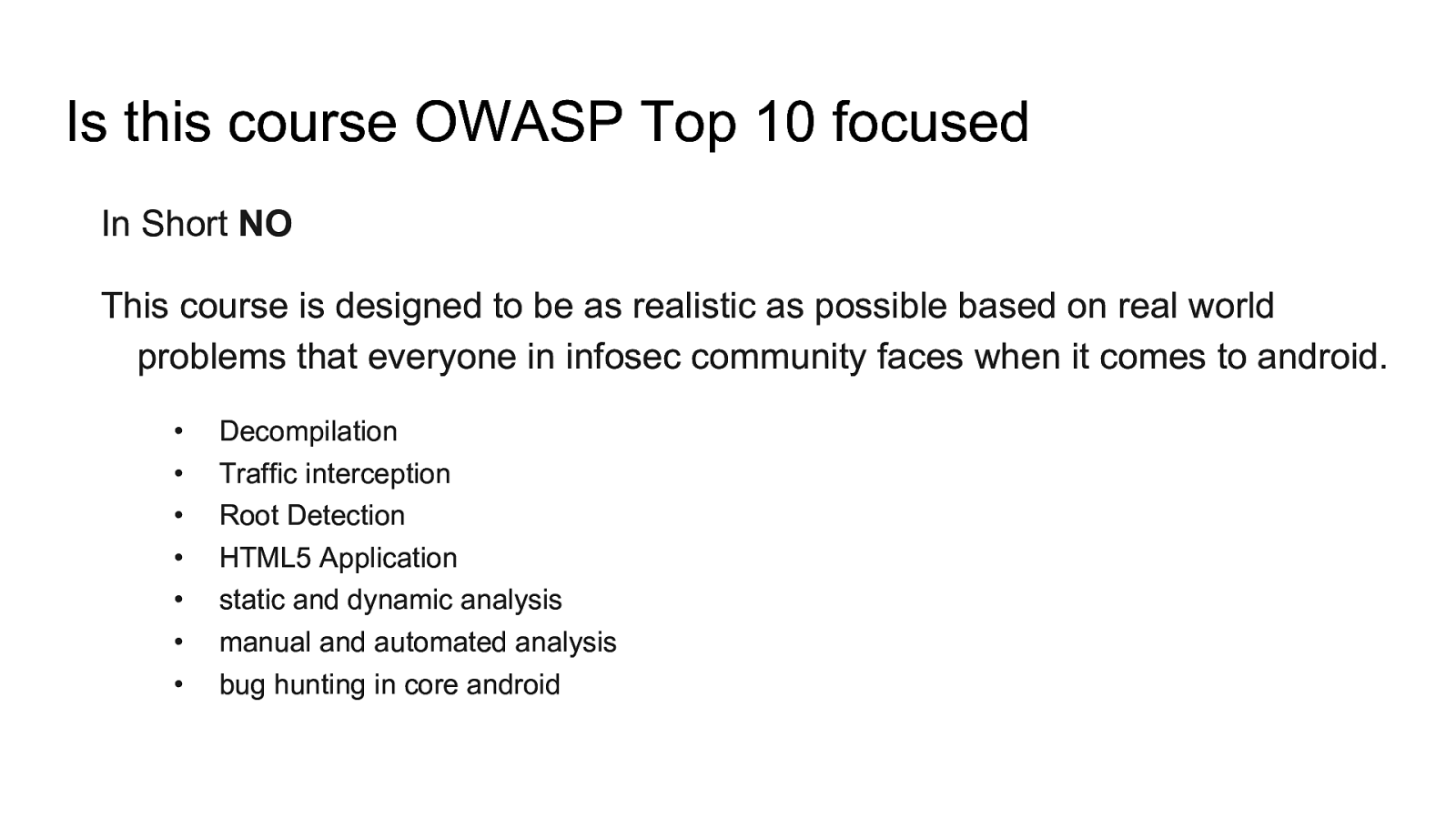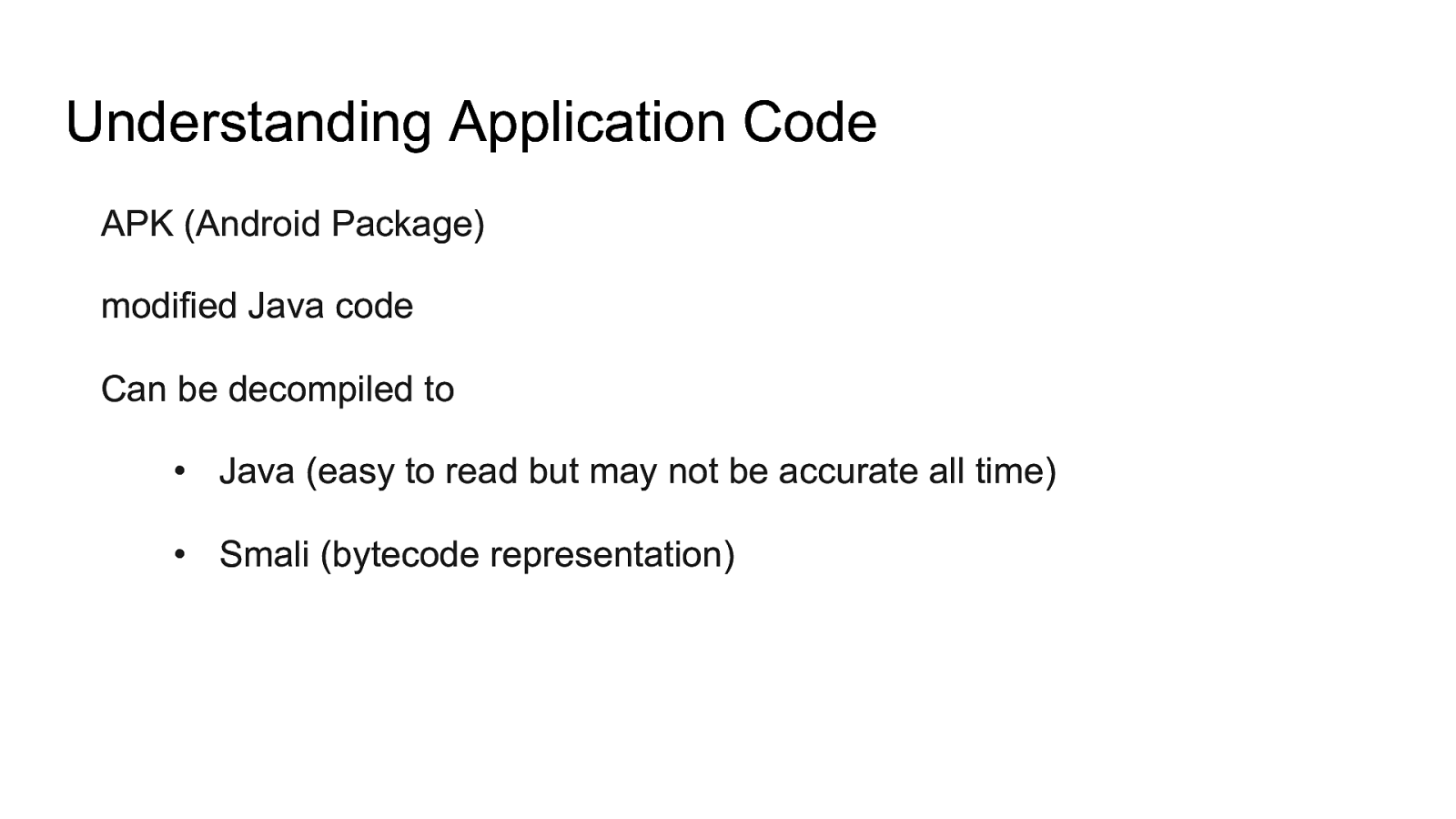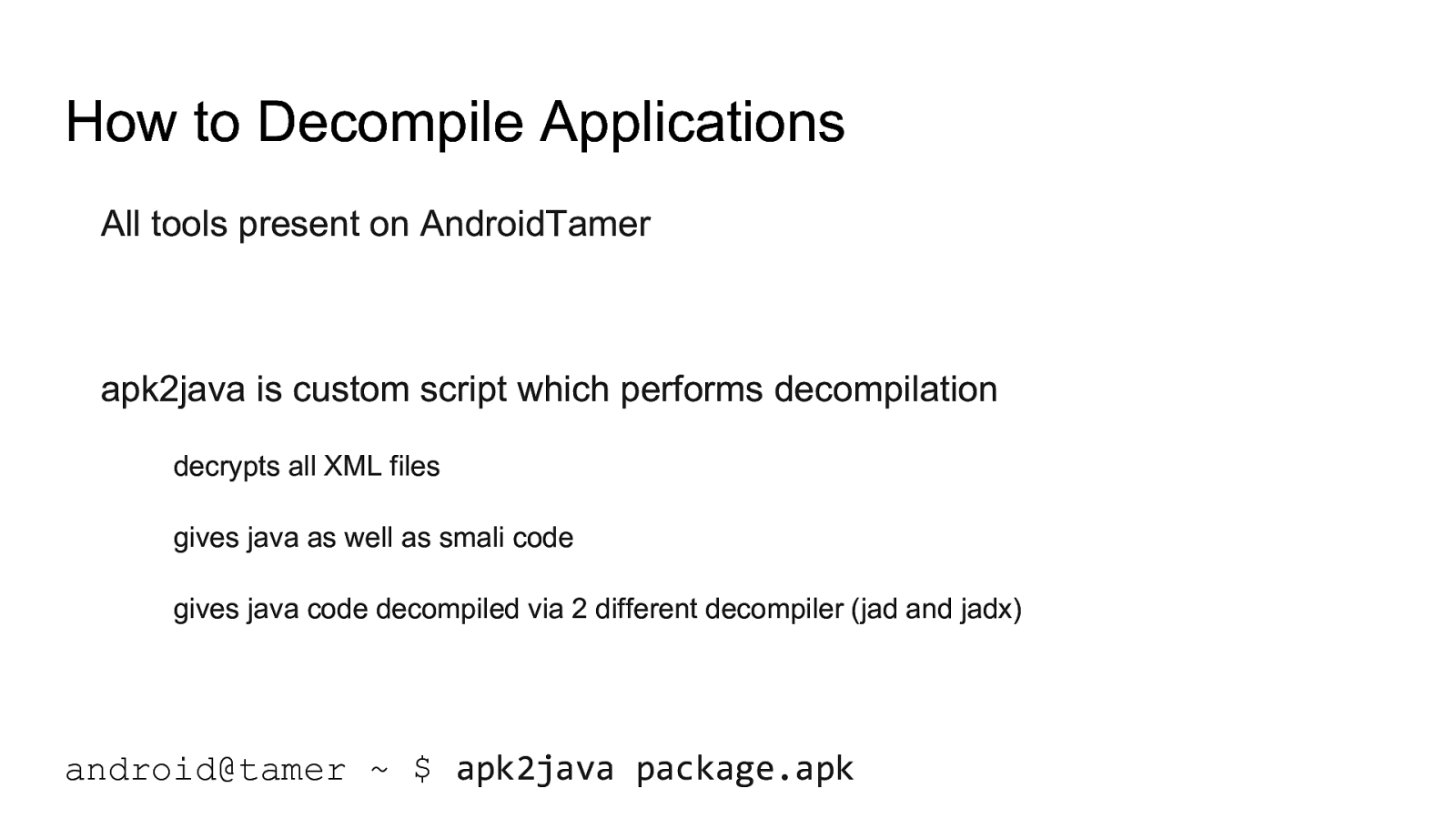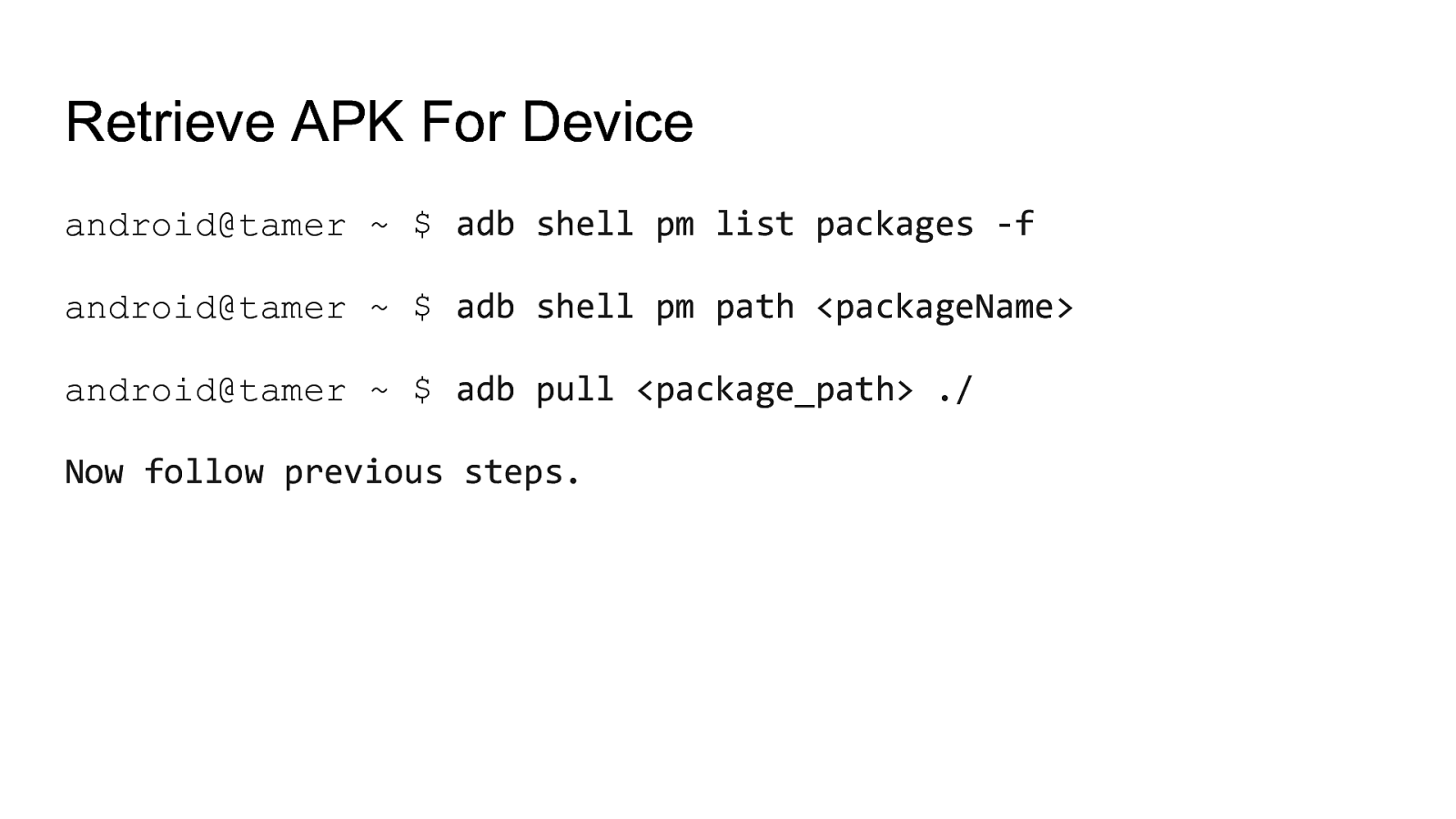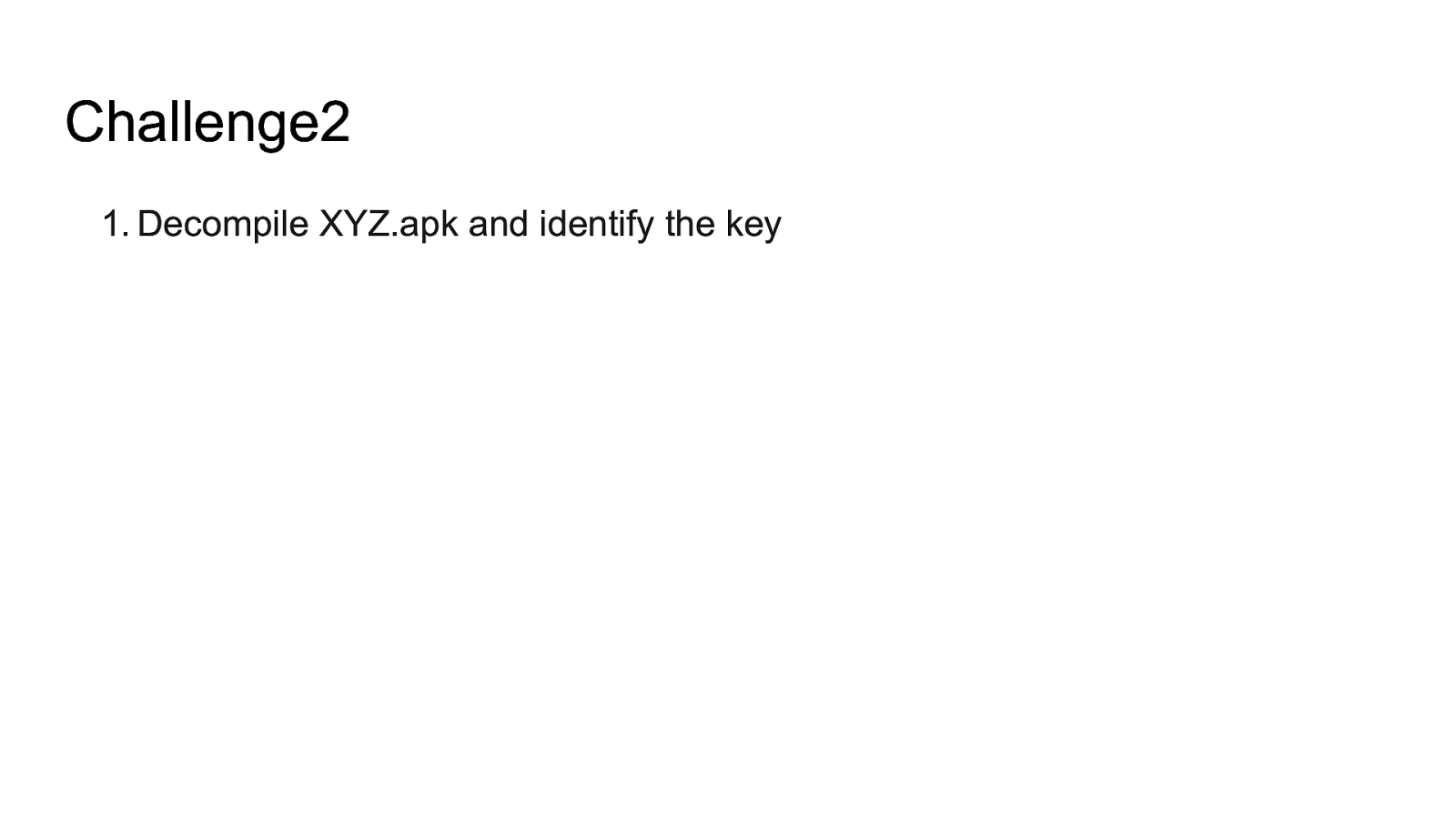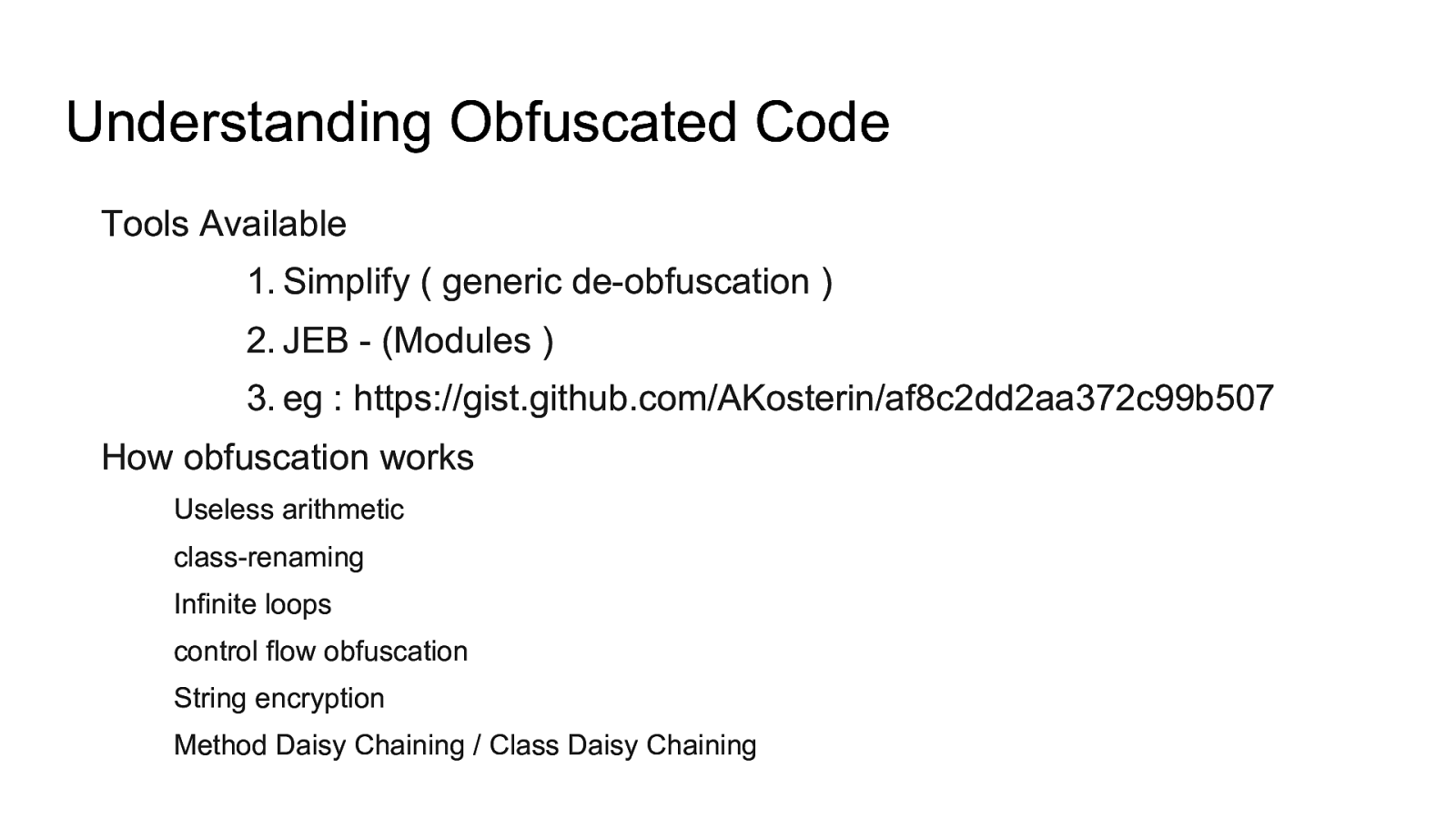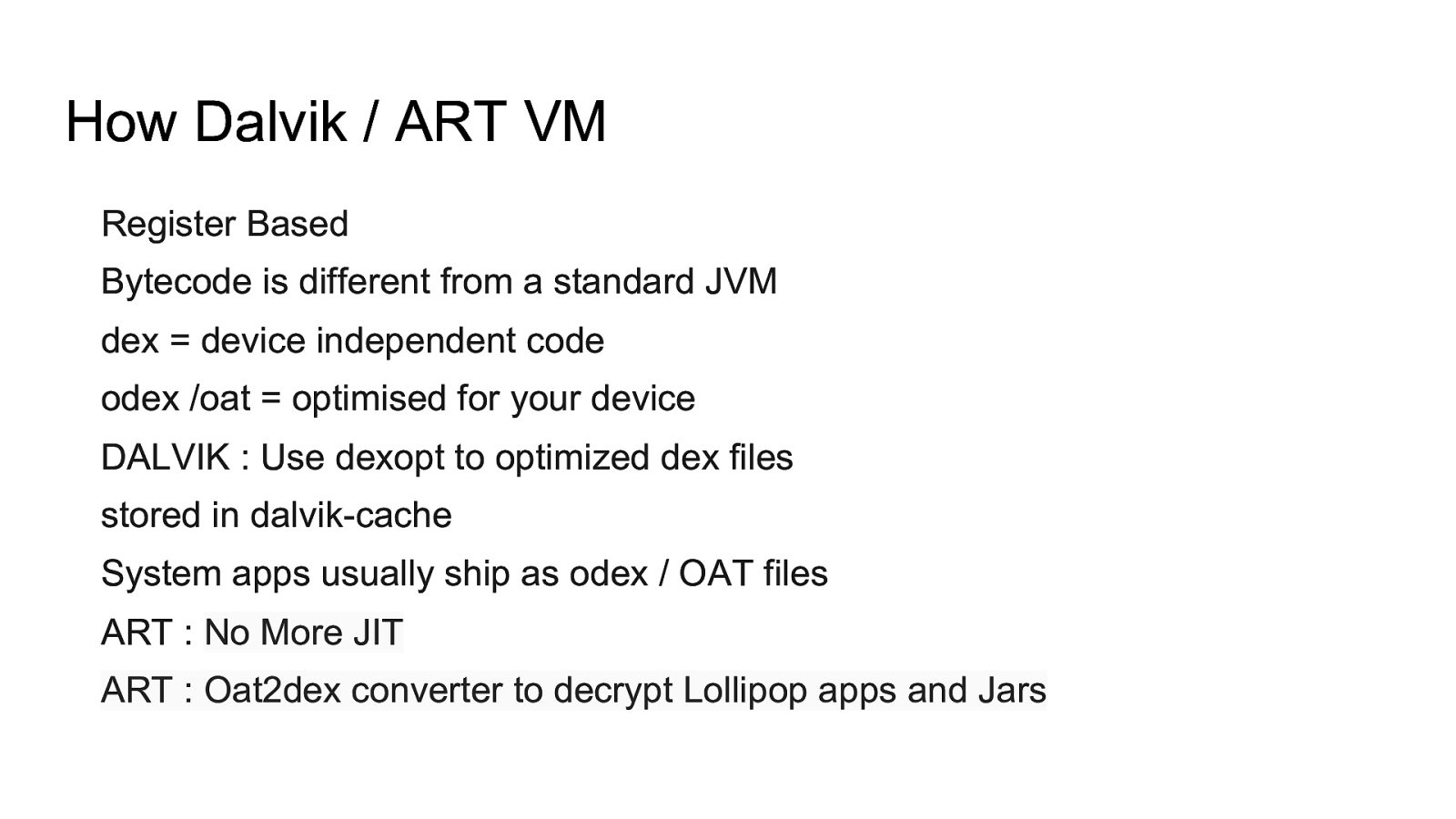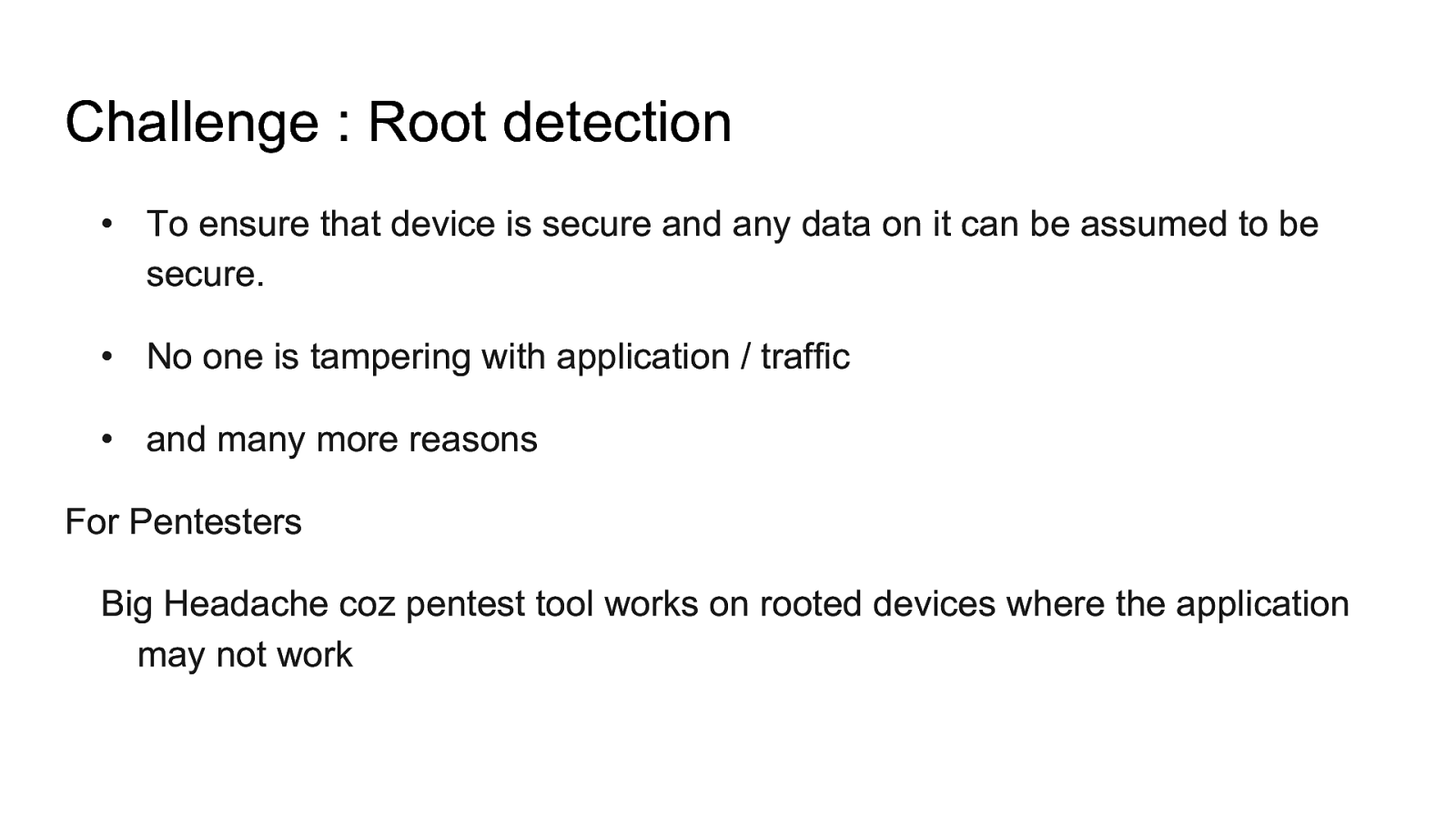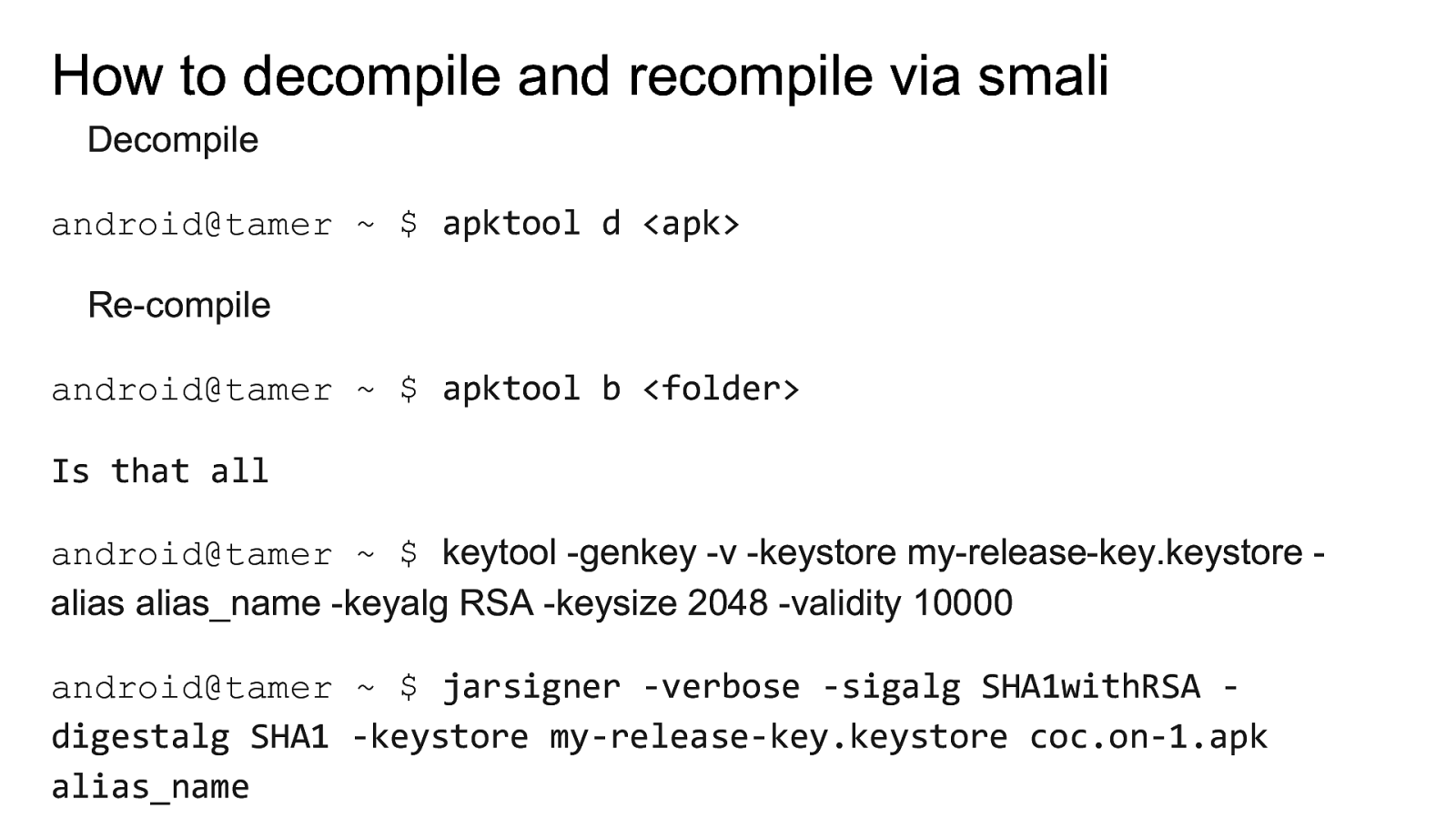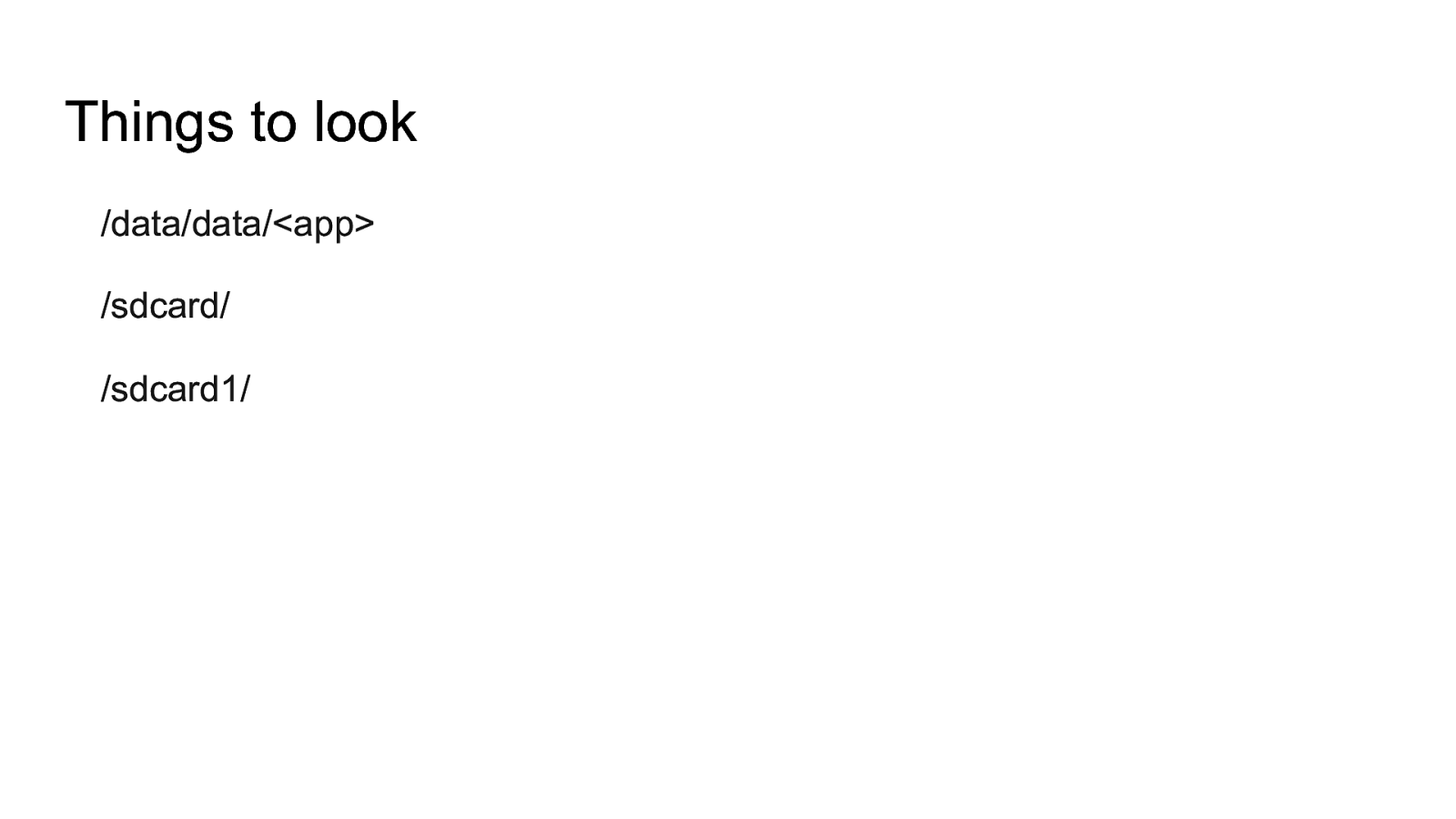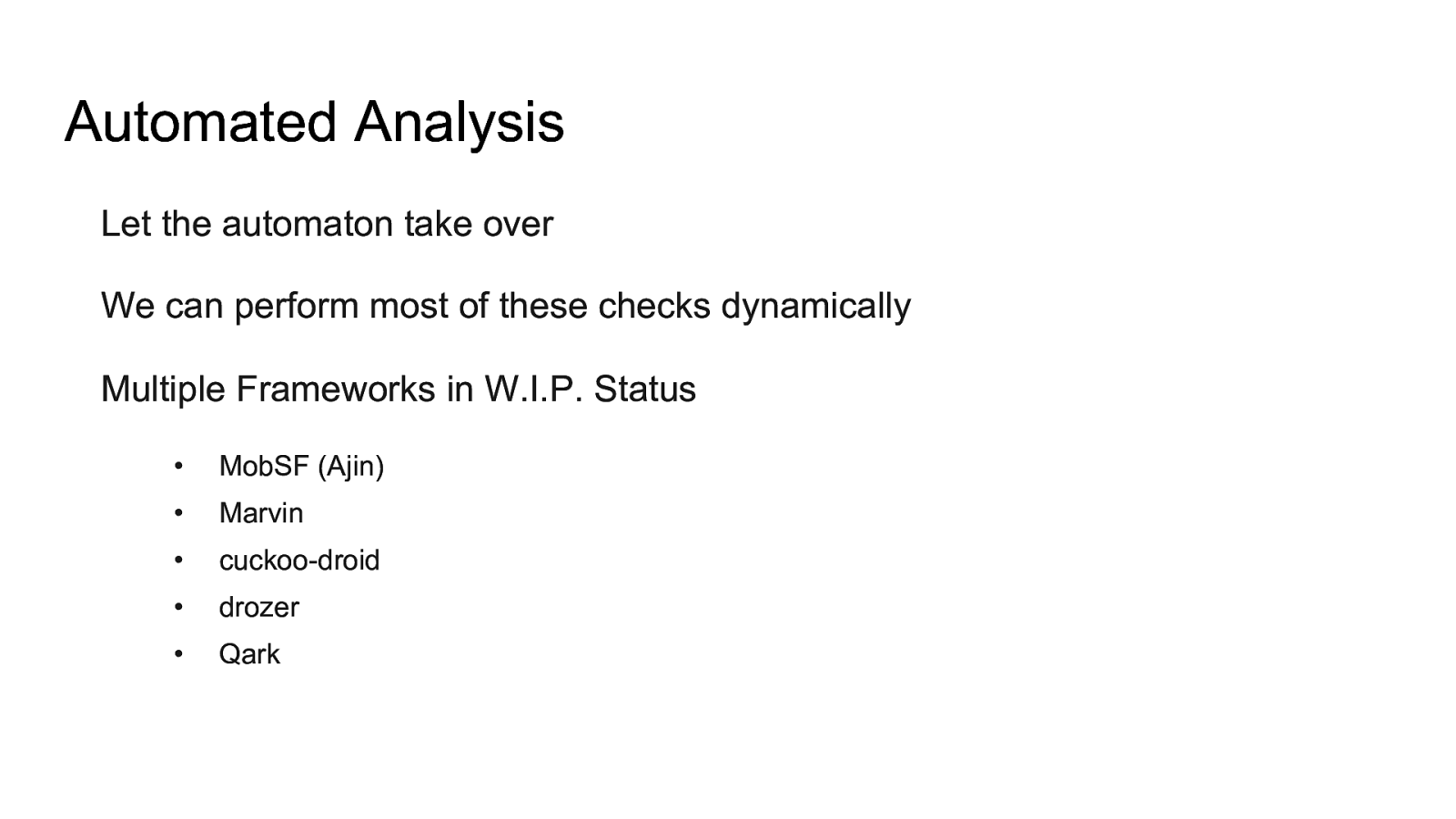Training: XTREME ANDROID EXPLOITATION LAB
A presentation at Nullcon 2017 in in Goa, India by Anant Shrivastava
Objective Xtreame Android Exploitation Lab is a 2 days fast paced hands-on session. The class is revamped to provide students with hands-on exposure which they can start applying immediately after the session. This training will teach you
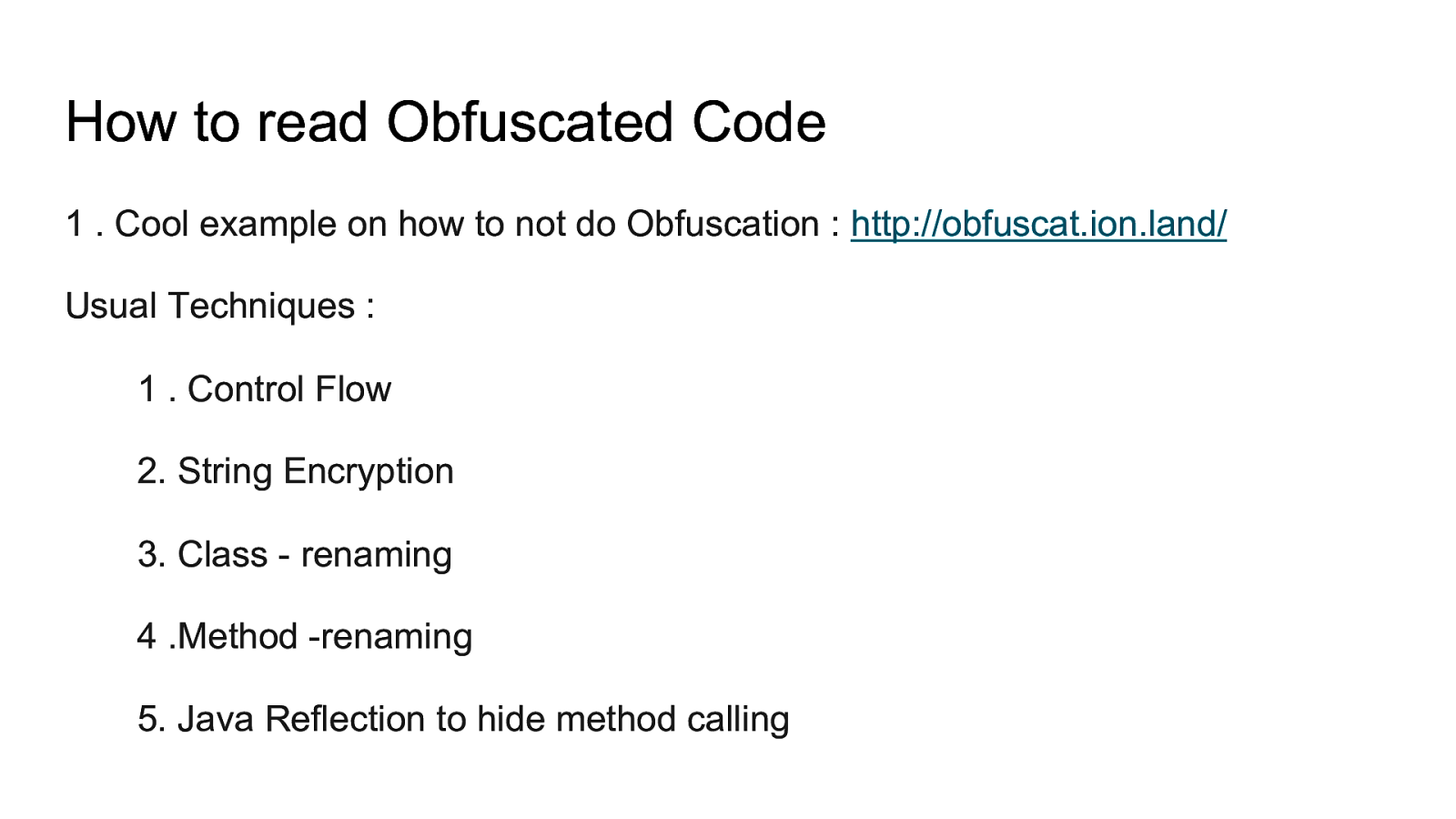
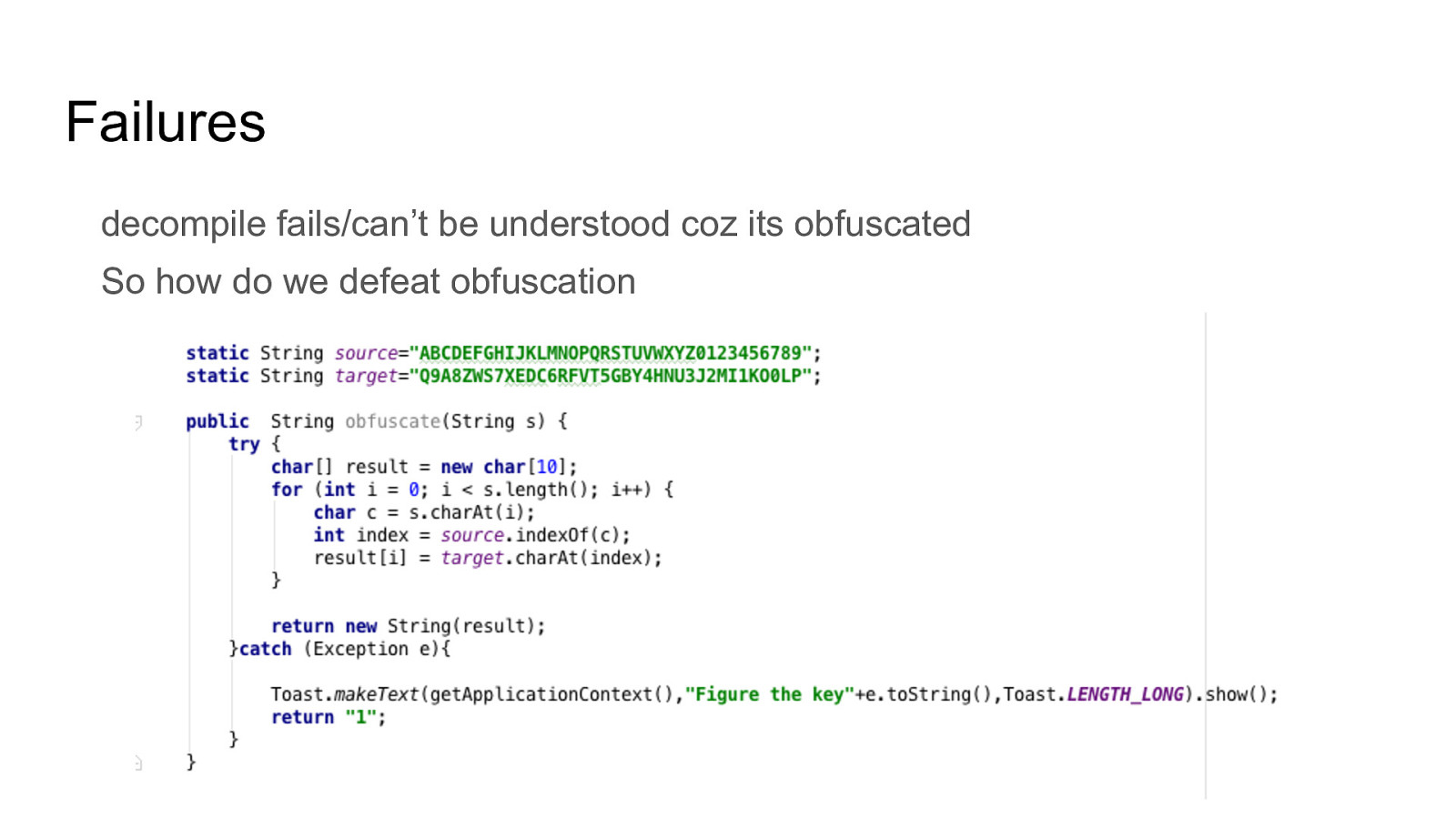
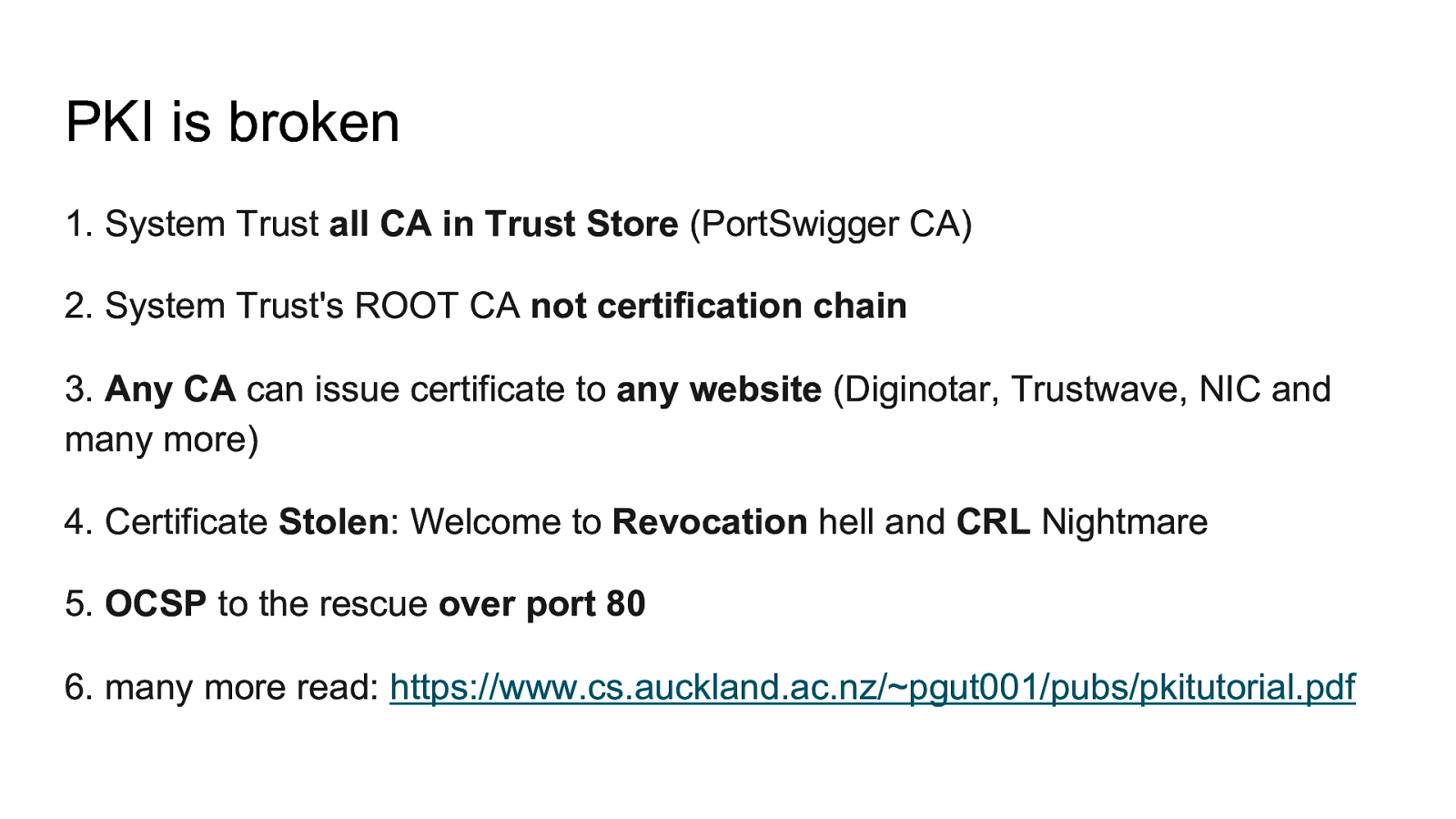
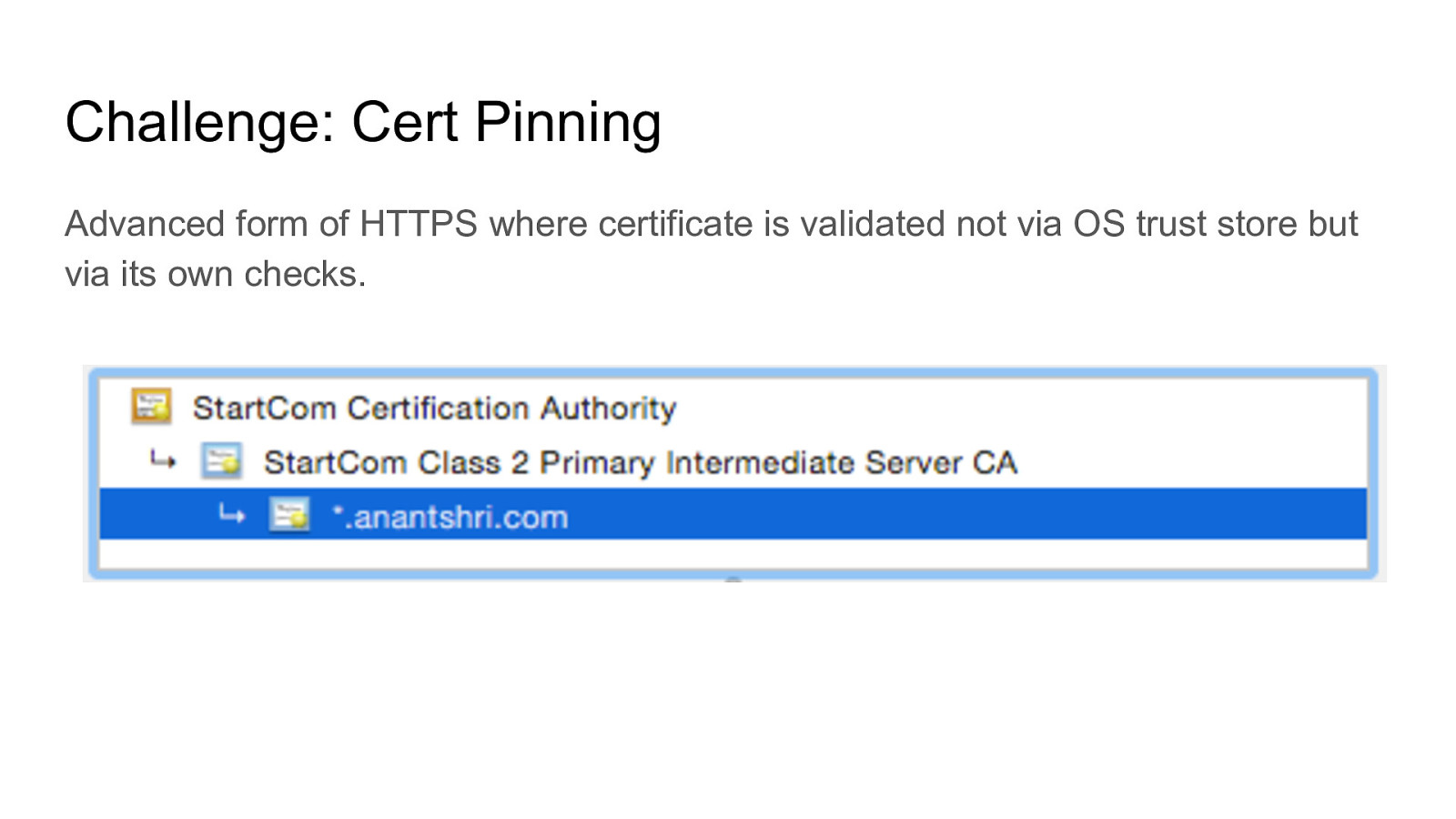
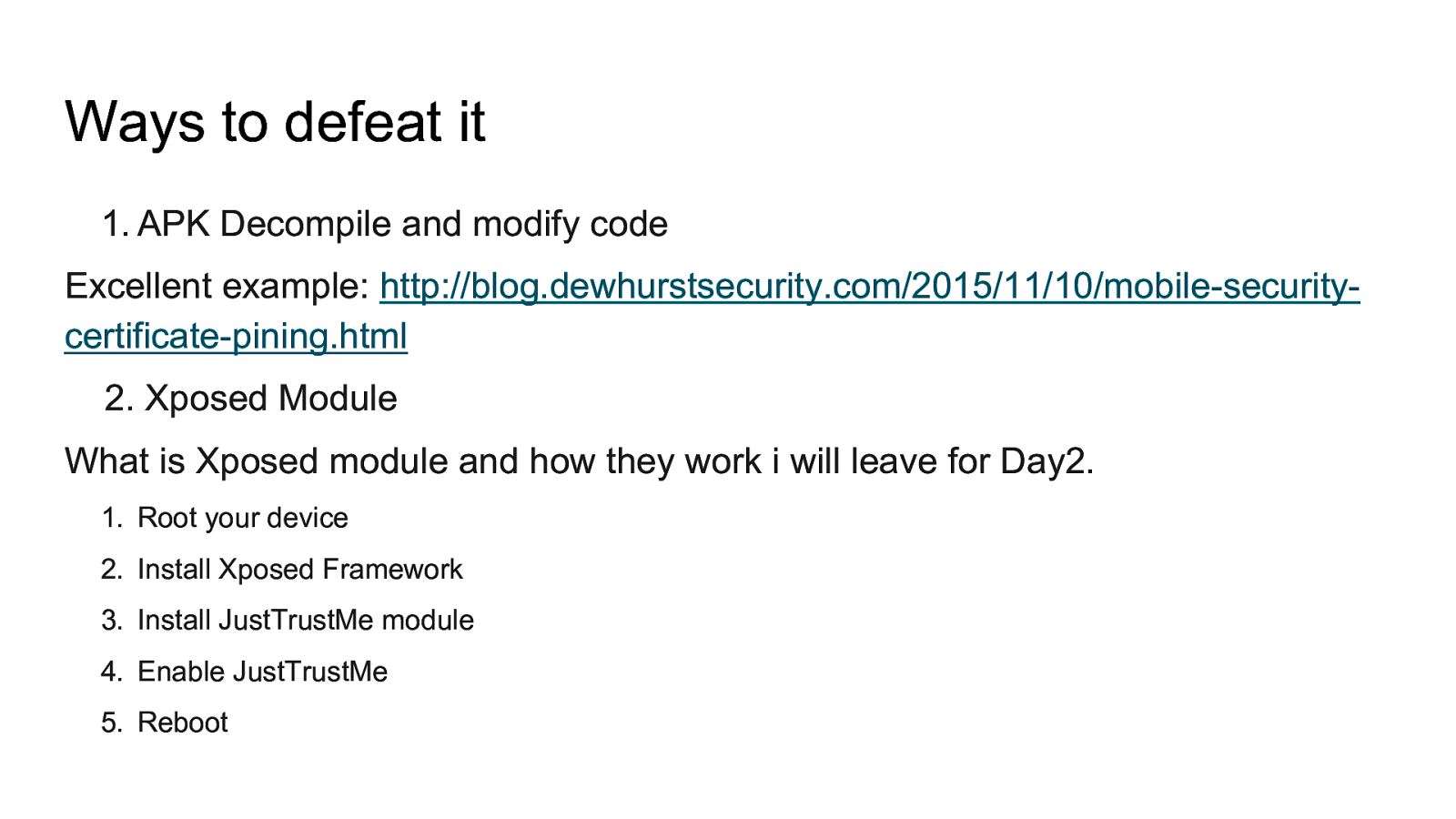
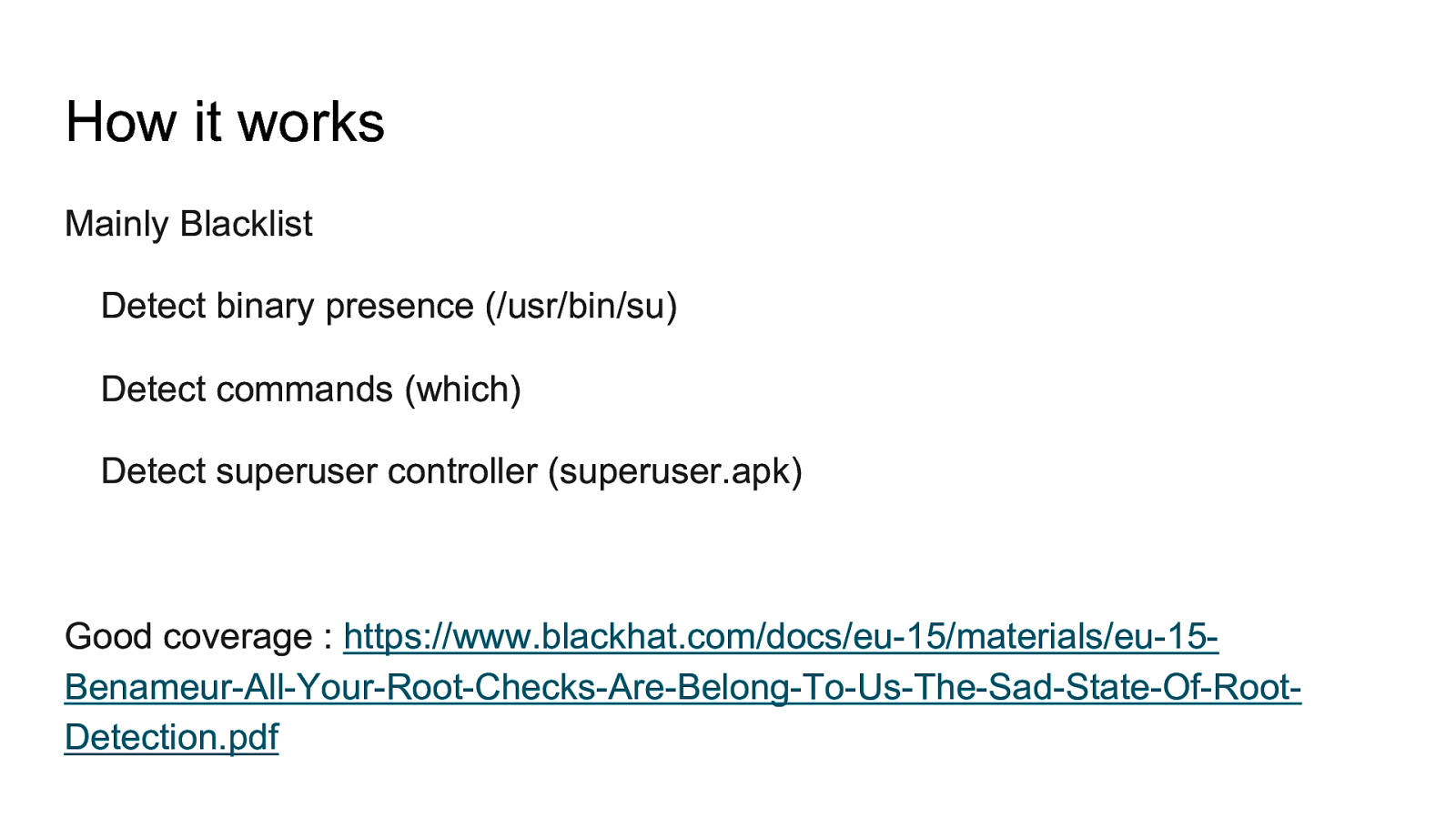
How to decompile an android application and understand obfuscated code Intercept traffic from android application even with protections like HTTPS certificate validation and SSL Pinning How to defeat root detection Perform manual and automated static analysis Perform automated analysis using tools like drozer and Mobile Security Framework and more Perform application hooking and dynamic instrumentation using Xposed Framework including writing own custom xposed module. Analyze HTML5 Applications Fuzzing Android for memory corruption vulnerabilities Perform Remote Code Executions Write your own tools / scripts to automate analysis And much more. The entire lab is designed in a scenario based situation where we will perform the same attacks that an attacker can do to gain access. Multiple applications have been developed to mimic real life vulnerabilities and multiple real world applications will be analyzed and exploited.
Each attendee will be provided with complete testing environment preconfigured for application assessment. The environment will consist of Android Tamer distribution customized for NullCon Training and customized Android Emulator images pre-configured with security tools. Attendees will learn and understand how to make best use of Android Tamer for android application penetration testing, directly from its creator.
All attendees will also be provided access to a continuous learning portal which will allow them to continue learning newer security developments even after finishing the training session. The portal also provides options to collaborate amongst the present and current students and also to interact with the trainer.
At the end of the class, there will be a final CTF challenge where the attendees will have to identify security vulnerabilities and exploit them in a real world application.
Buzz and feedback
Here’s what was said about this presentation on social media.